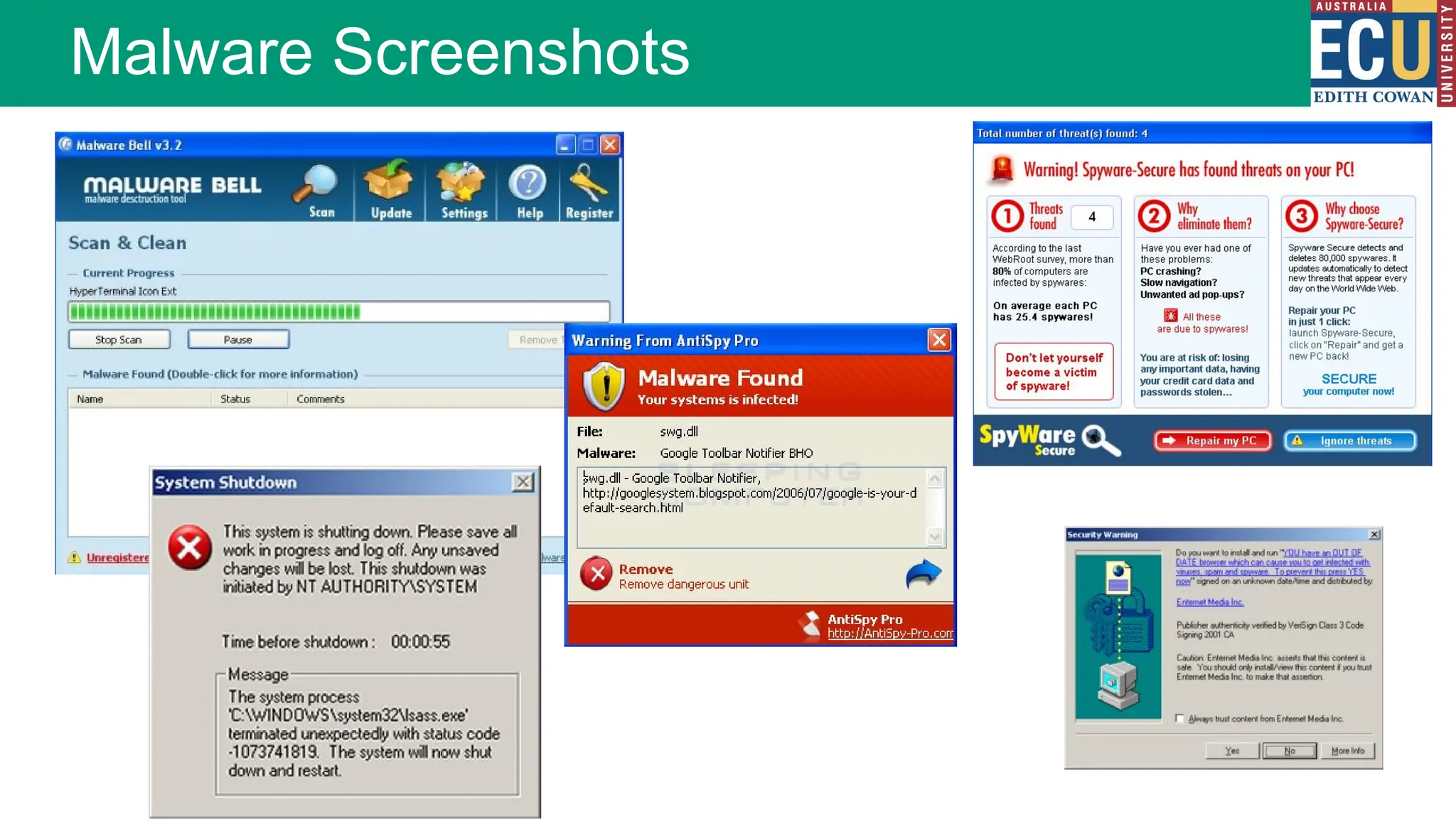
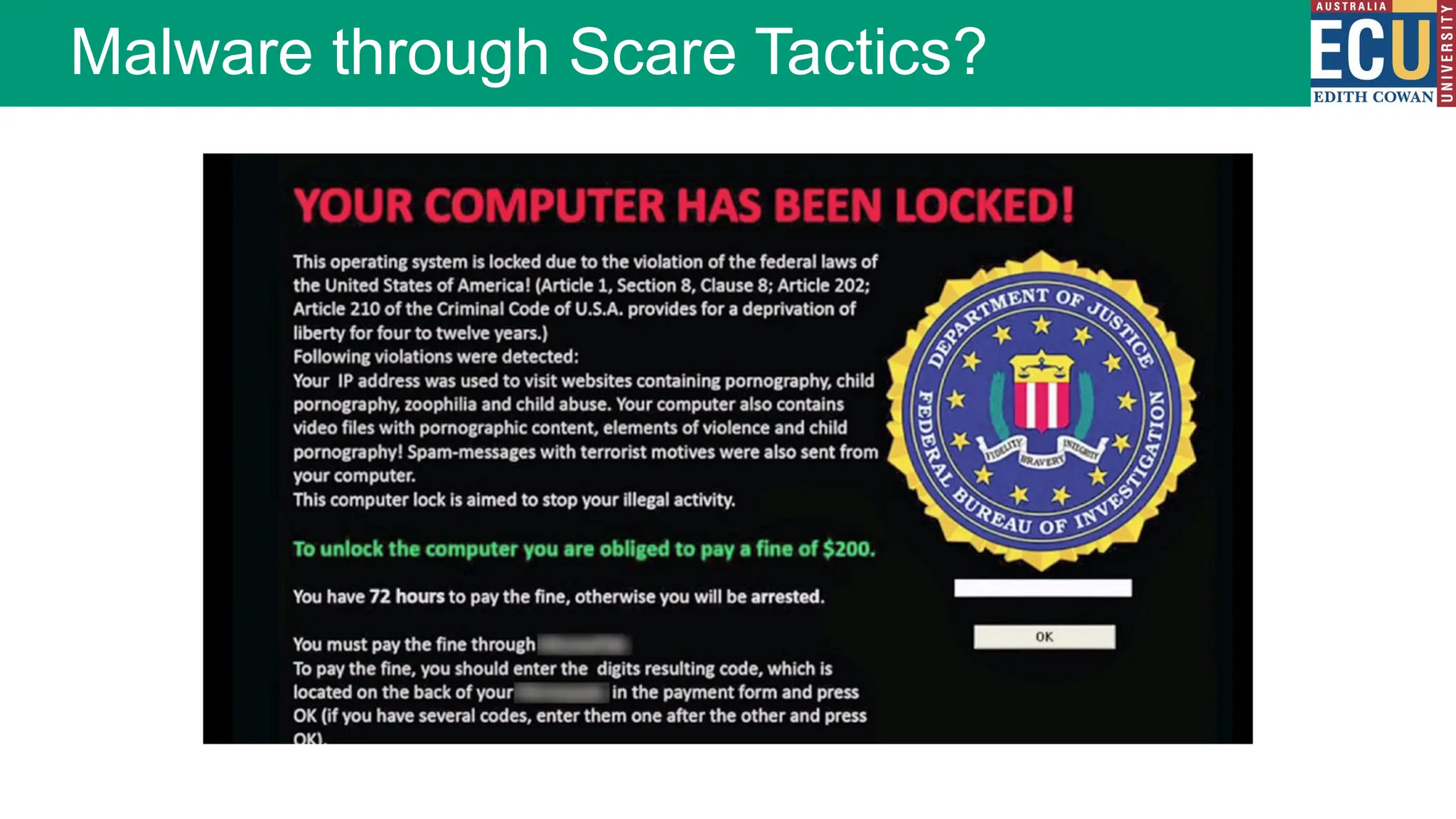
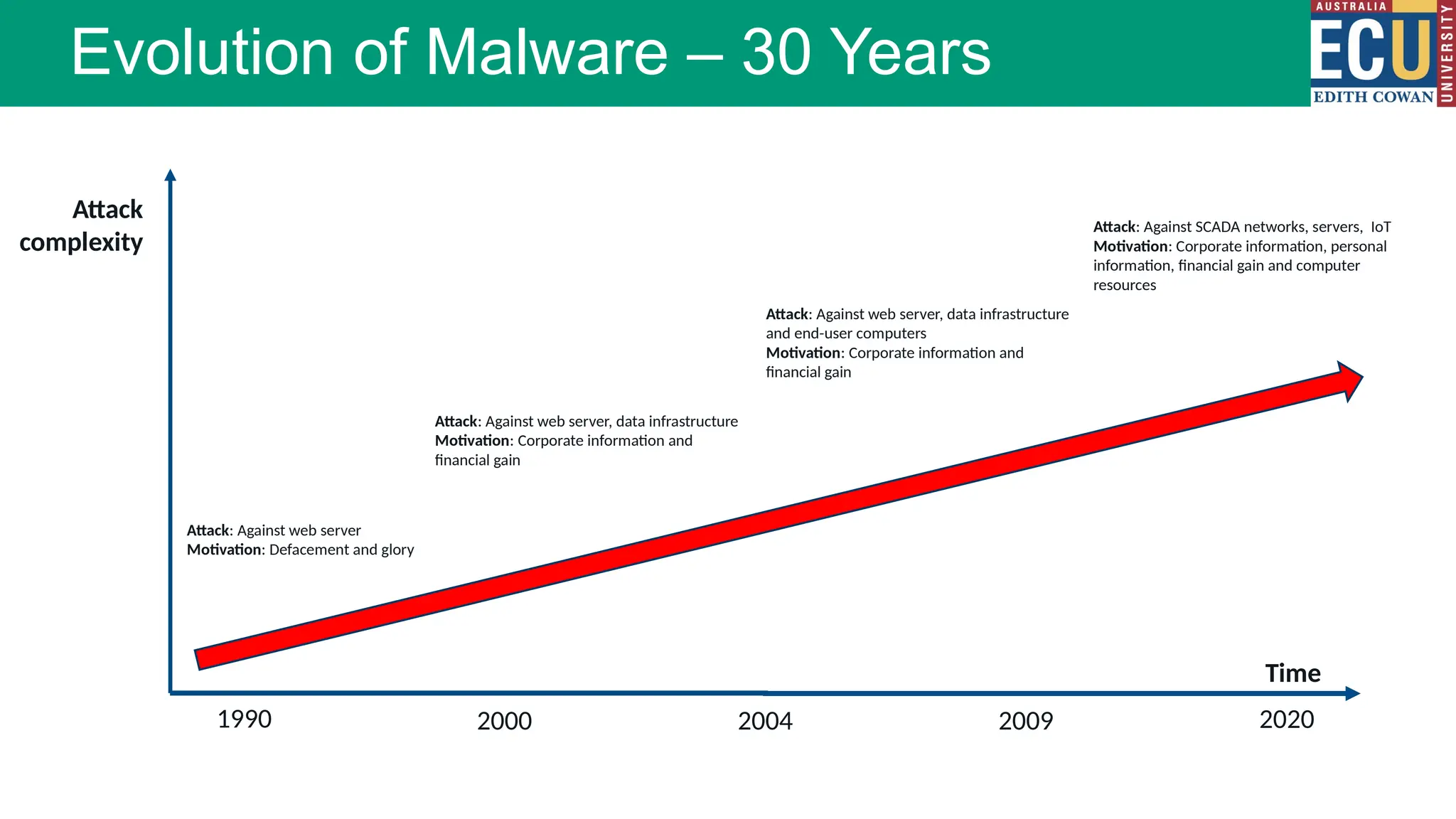
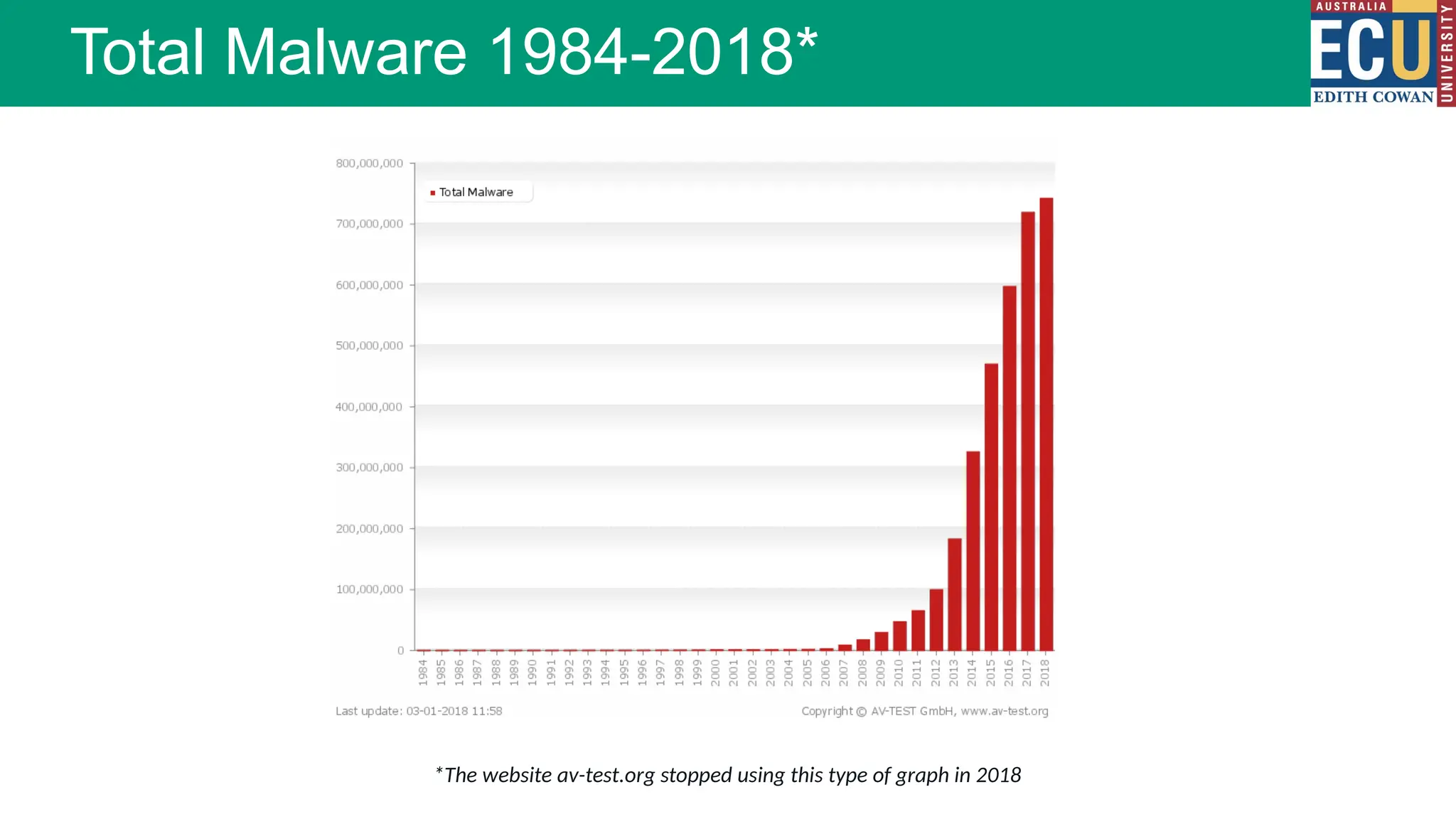
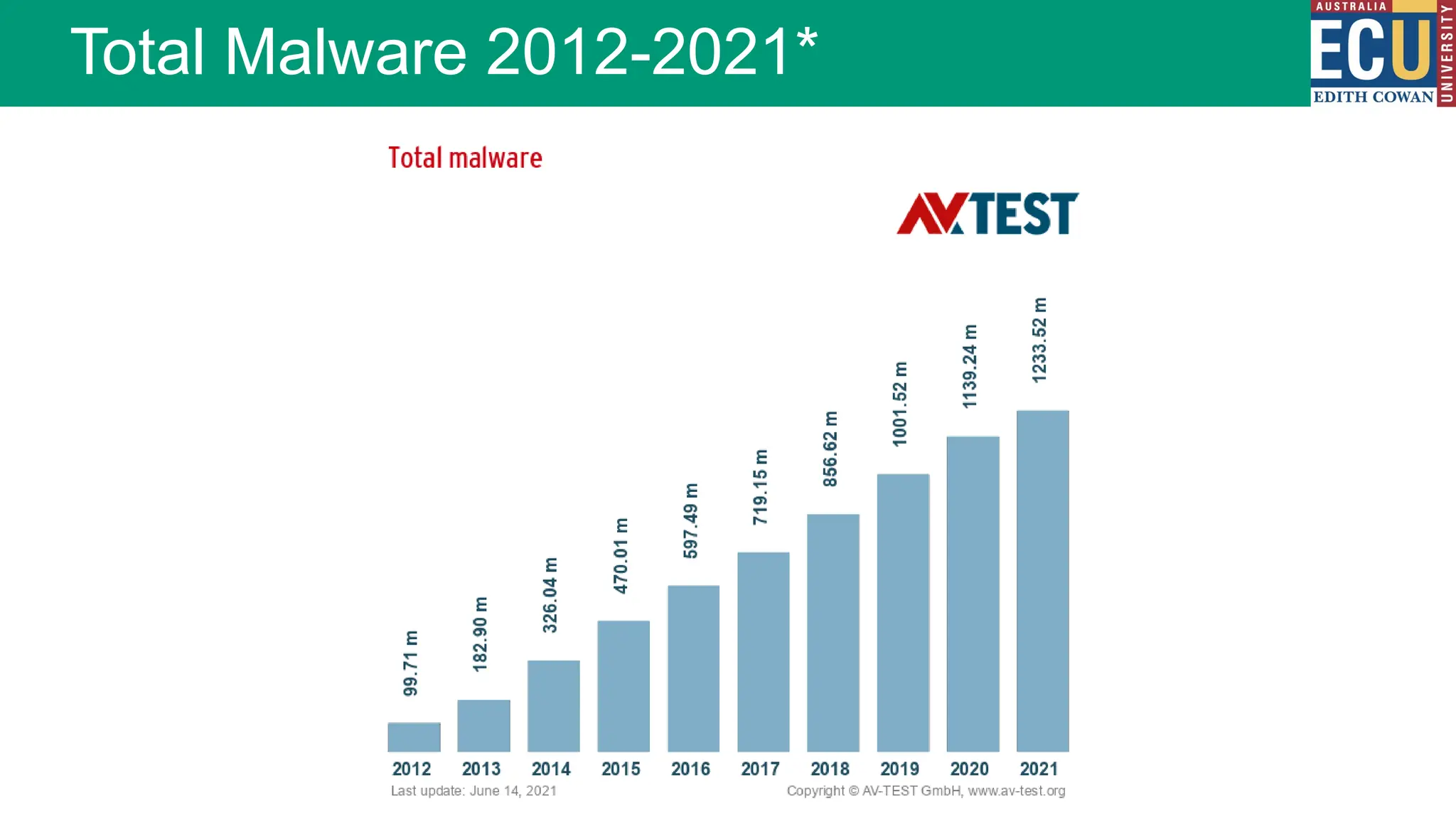
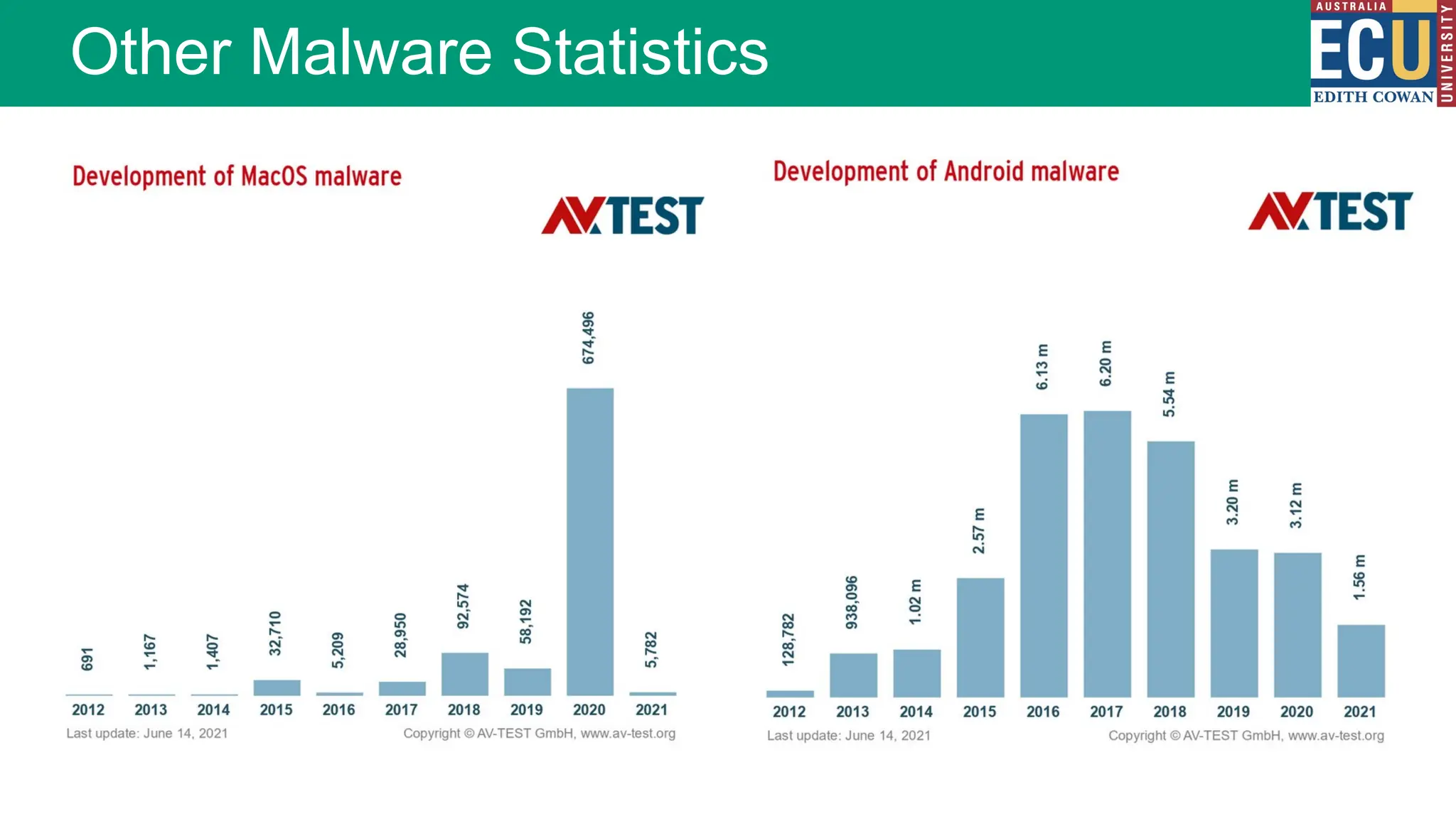
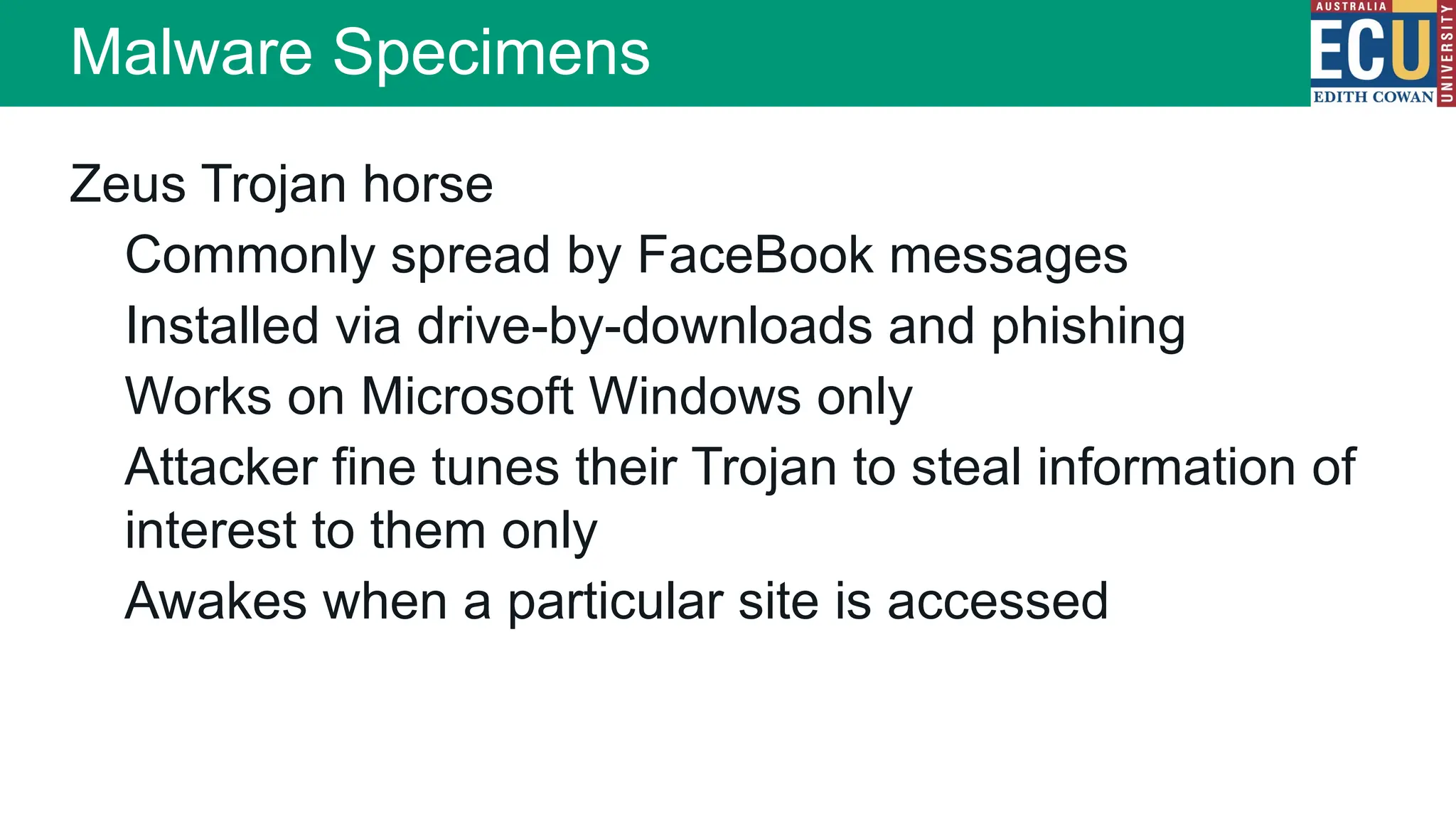
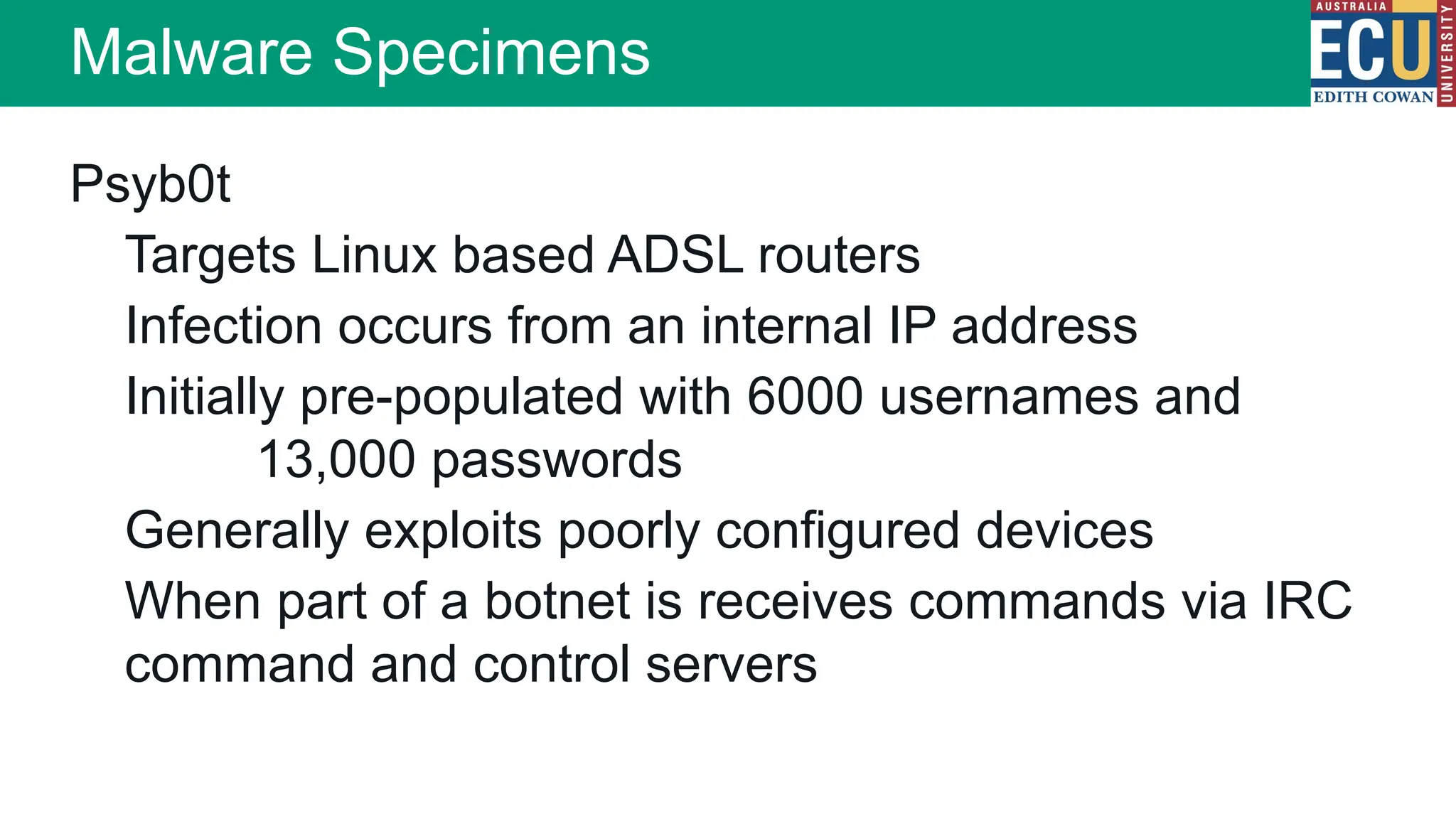
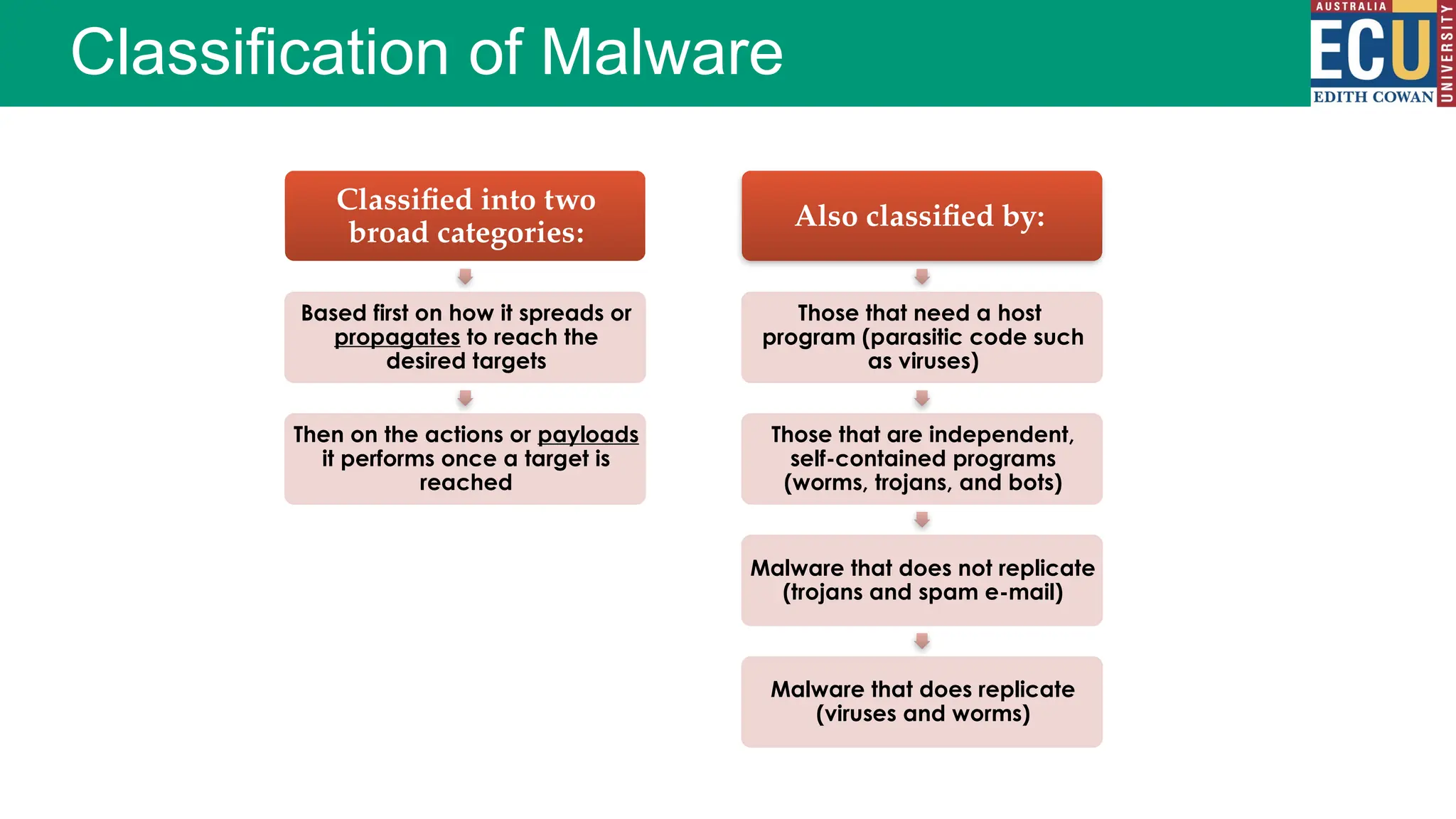
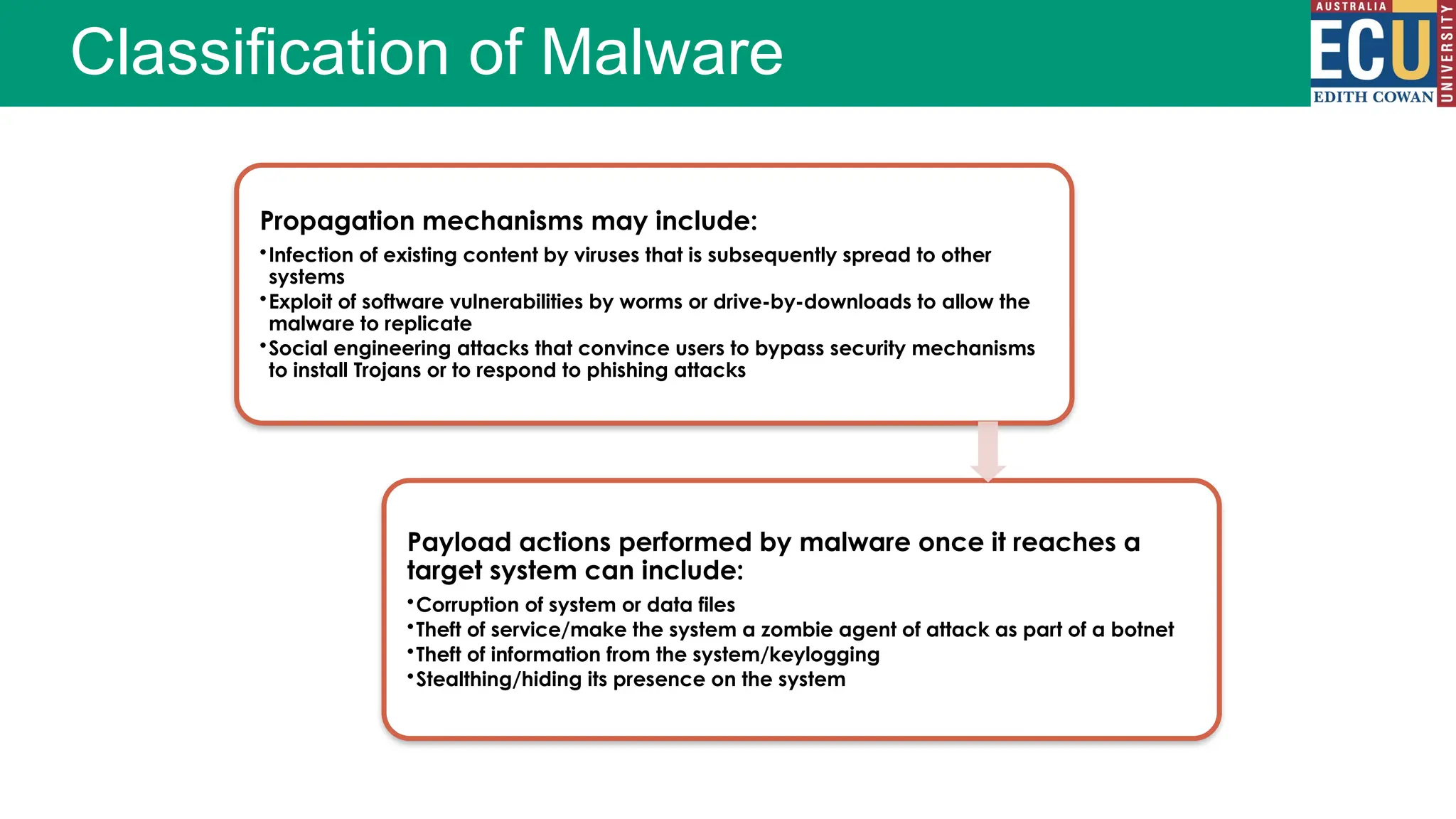
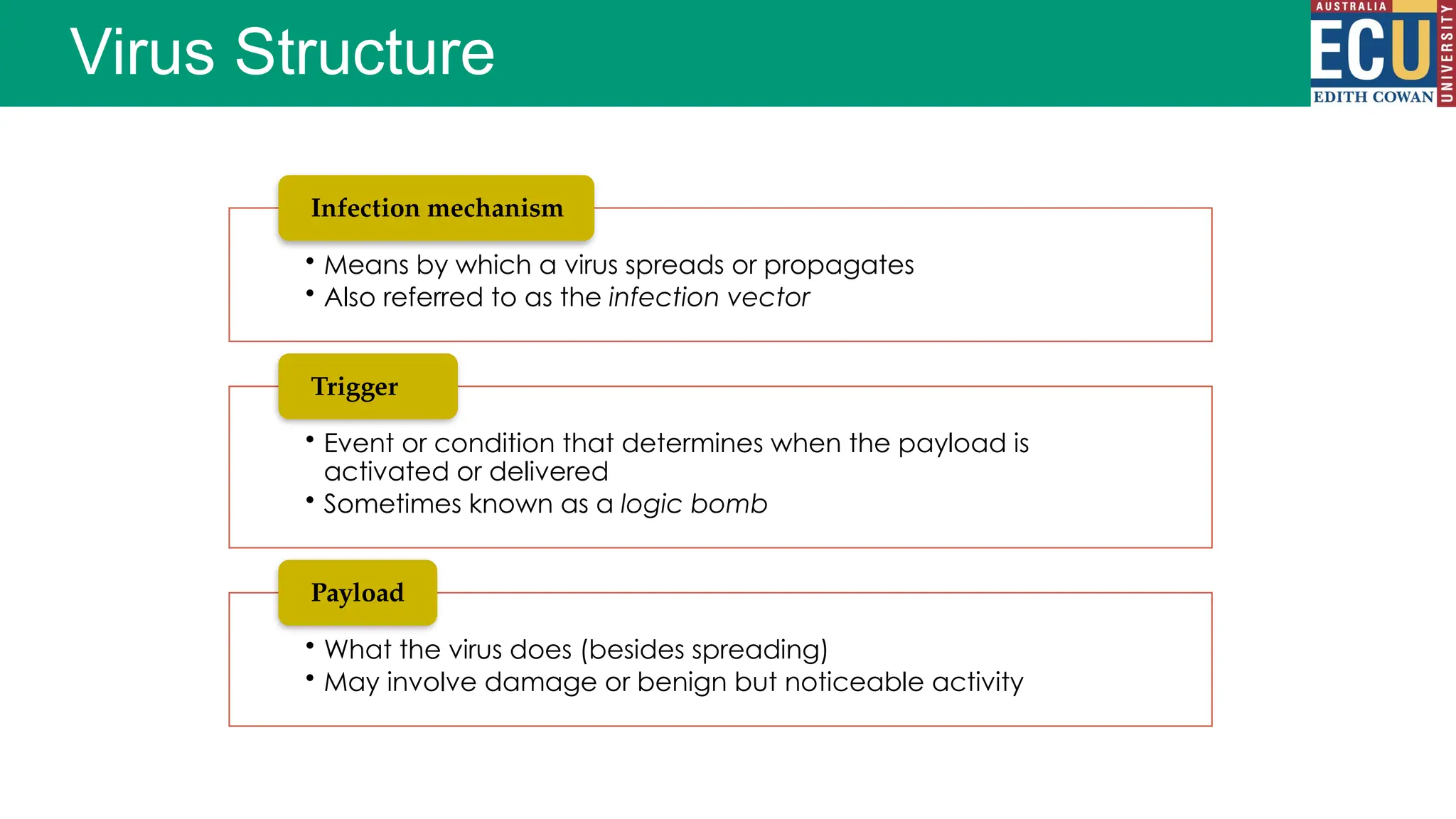
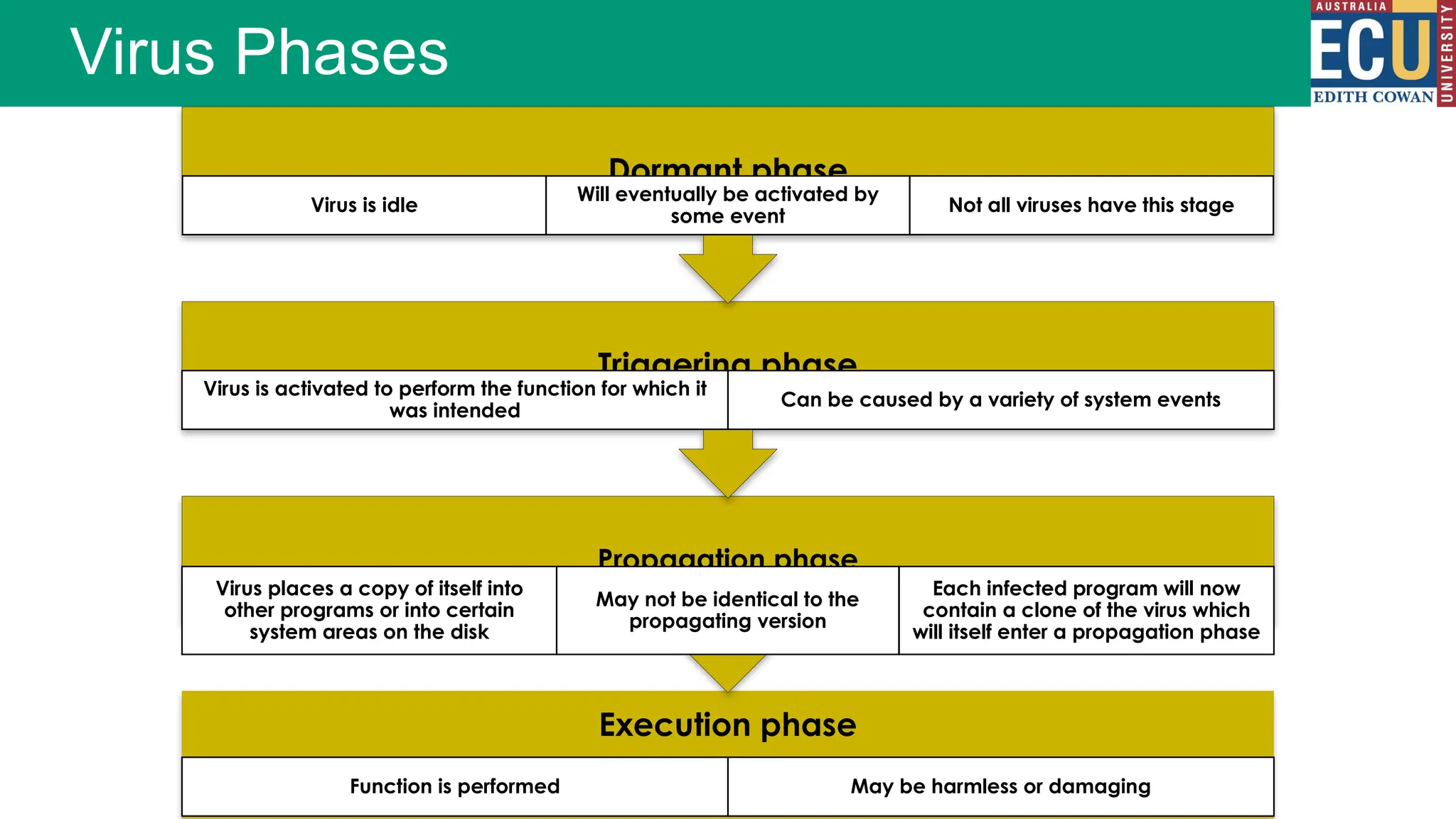
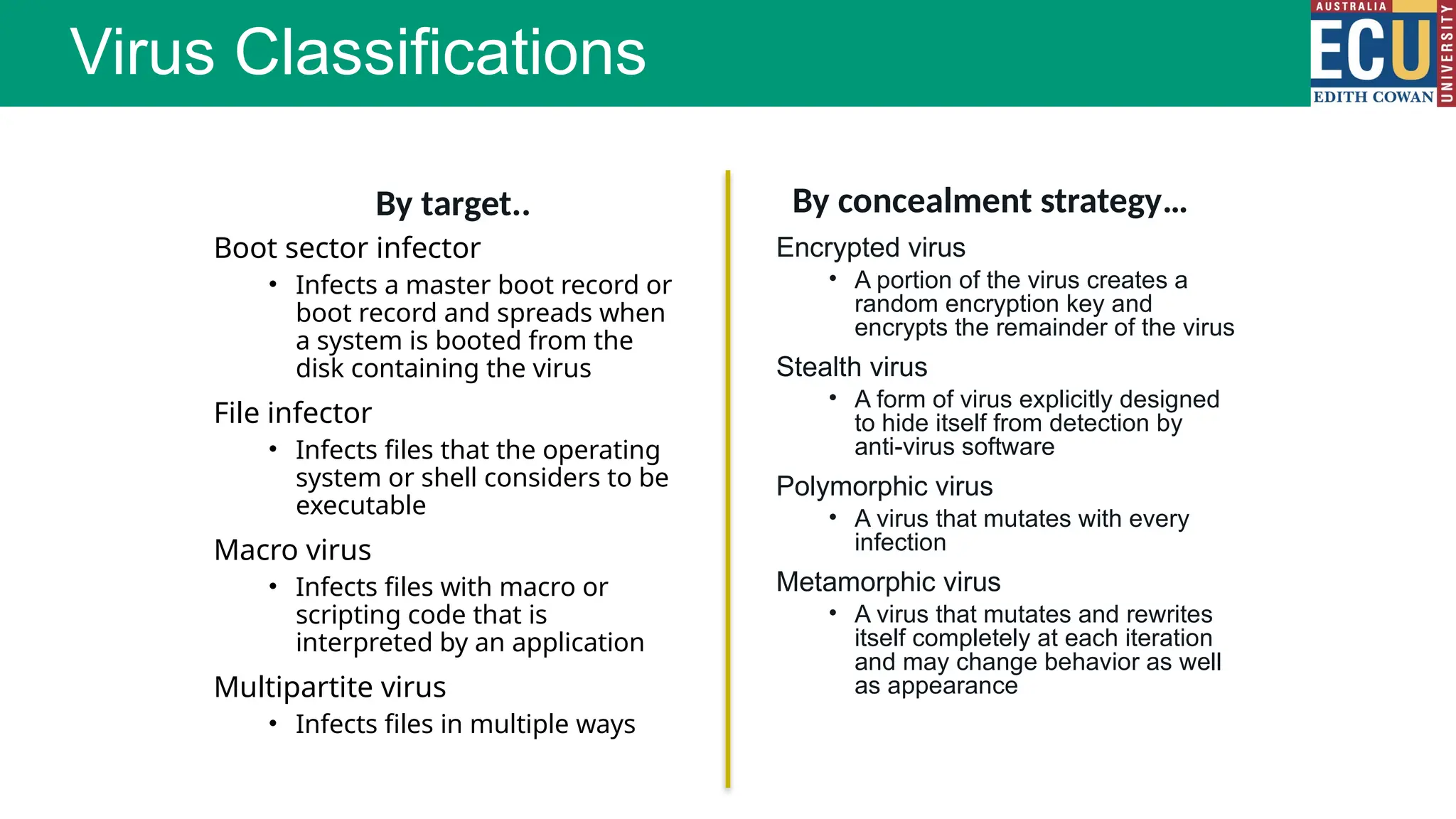
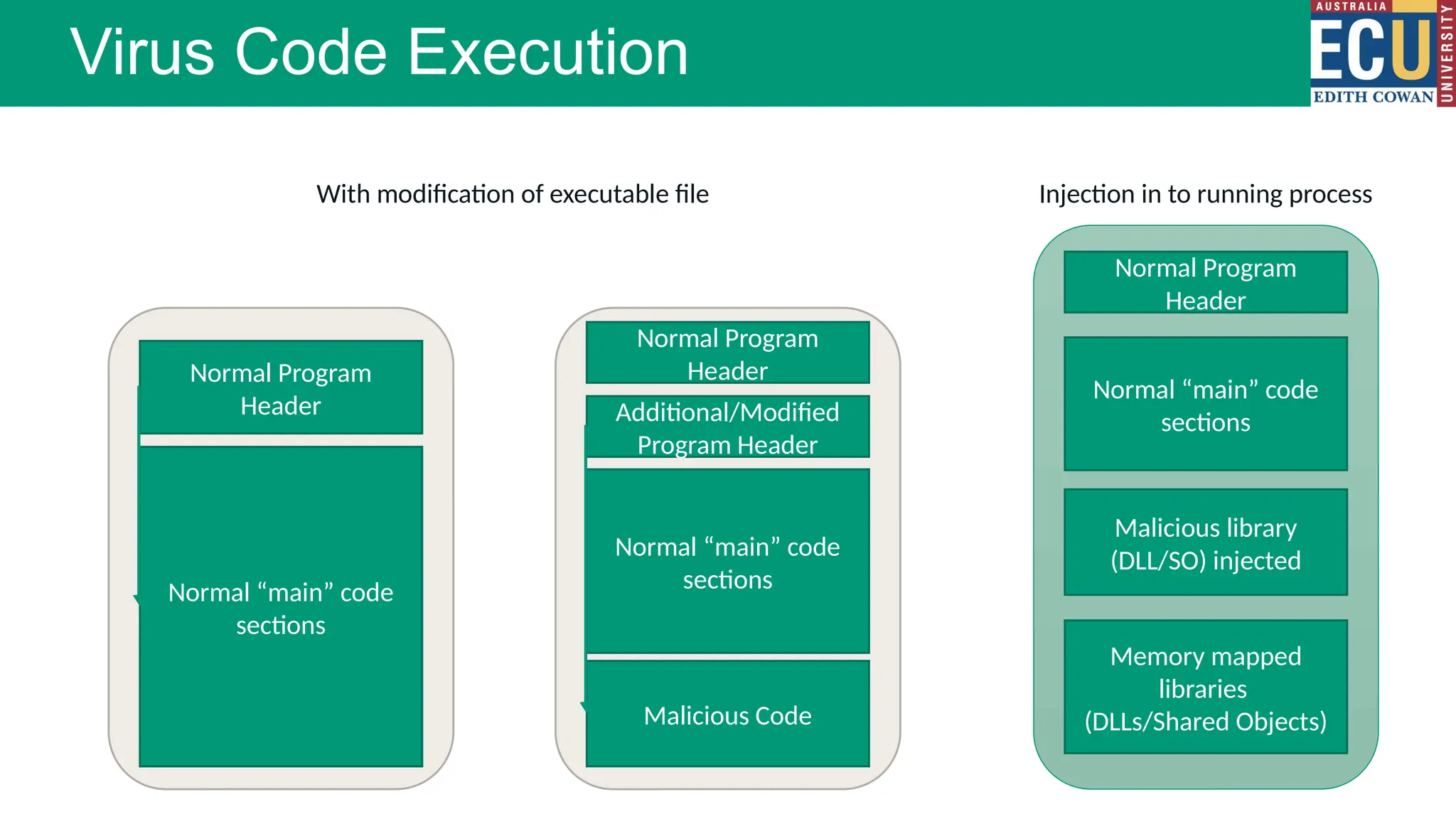
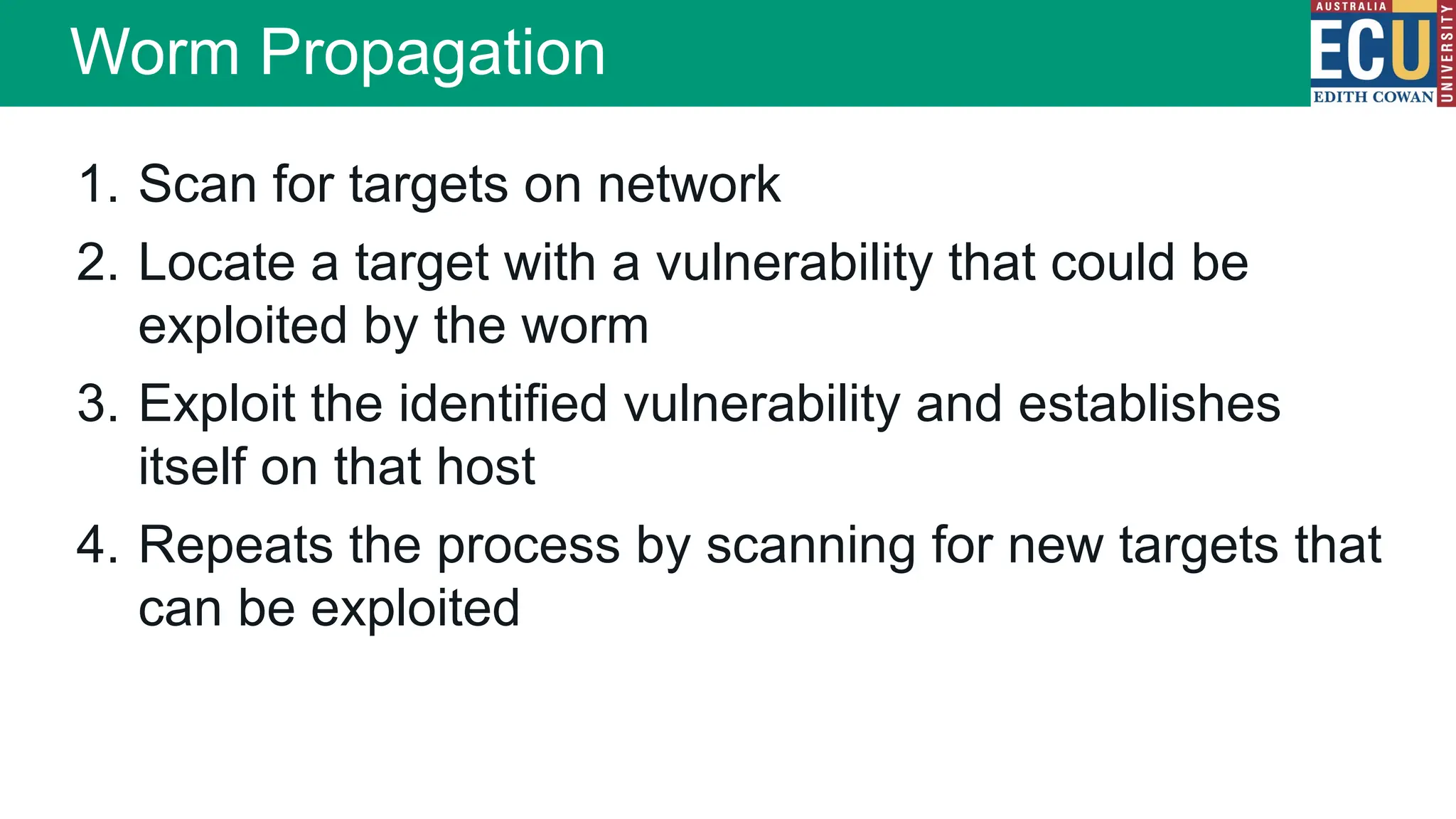
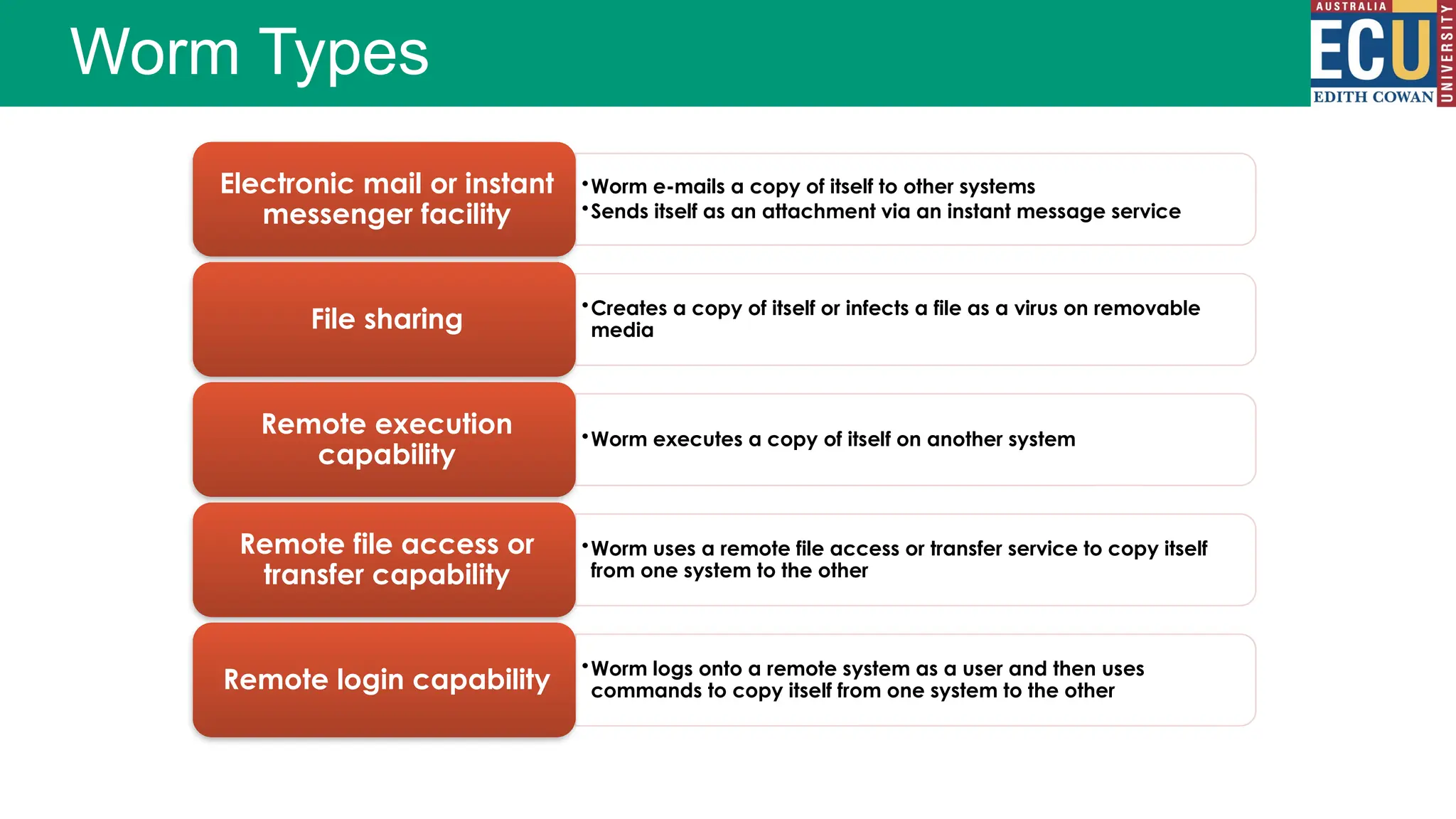
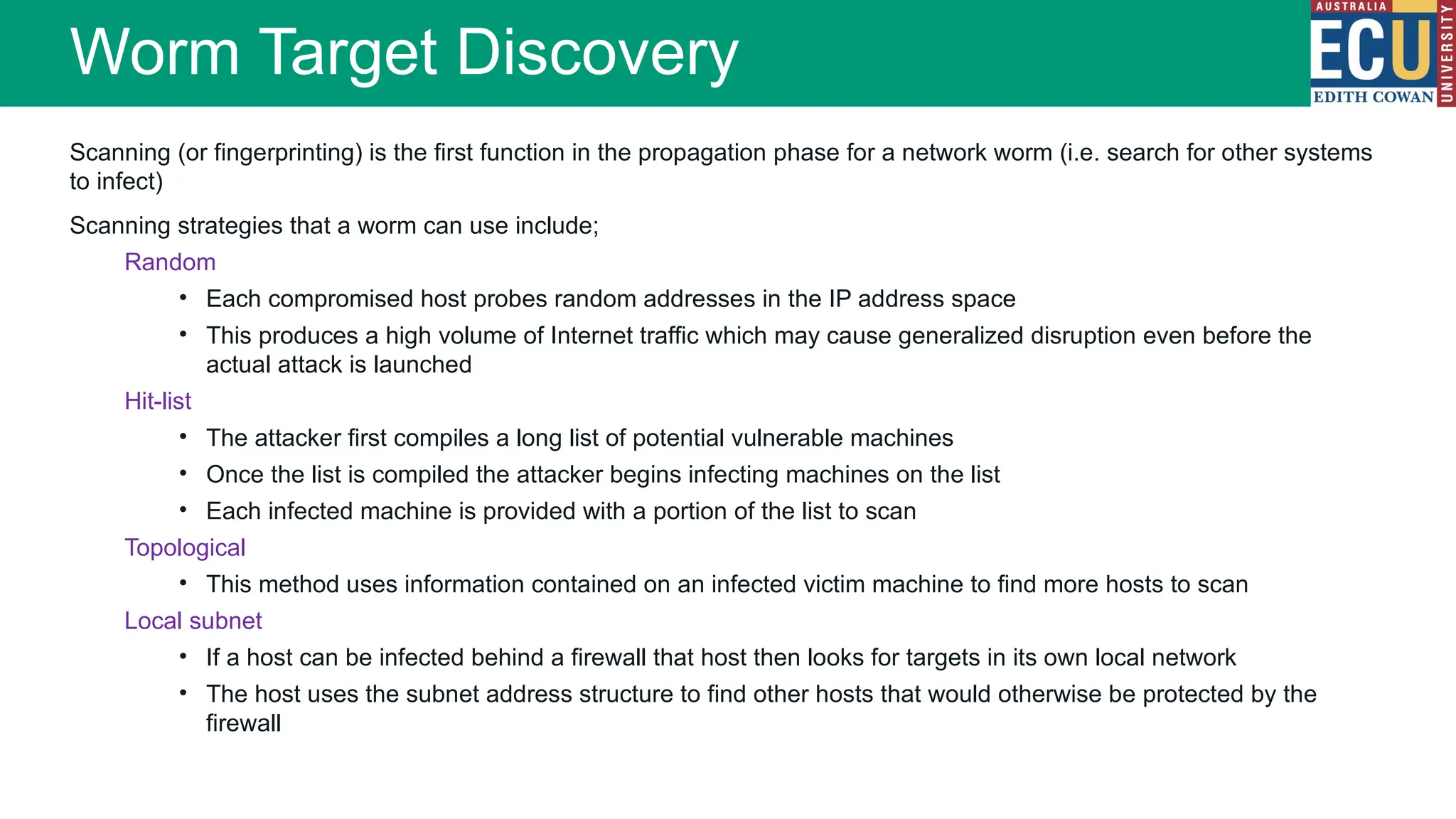
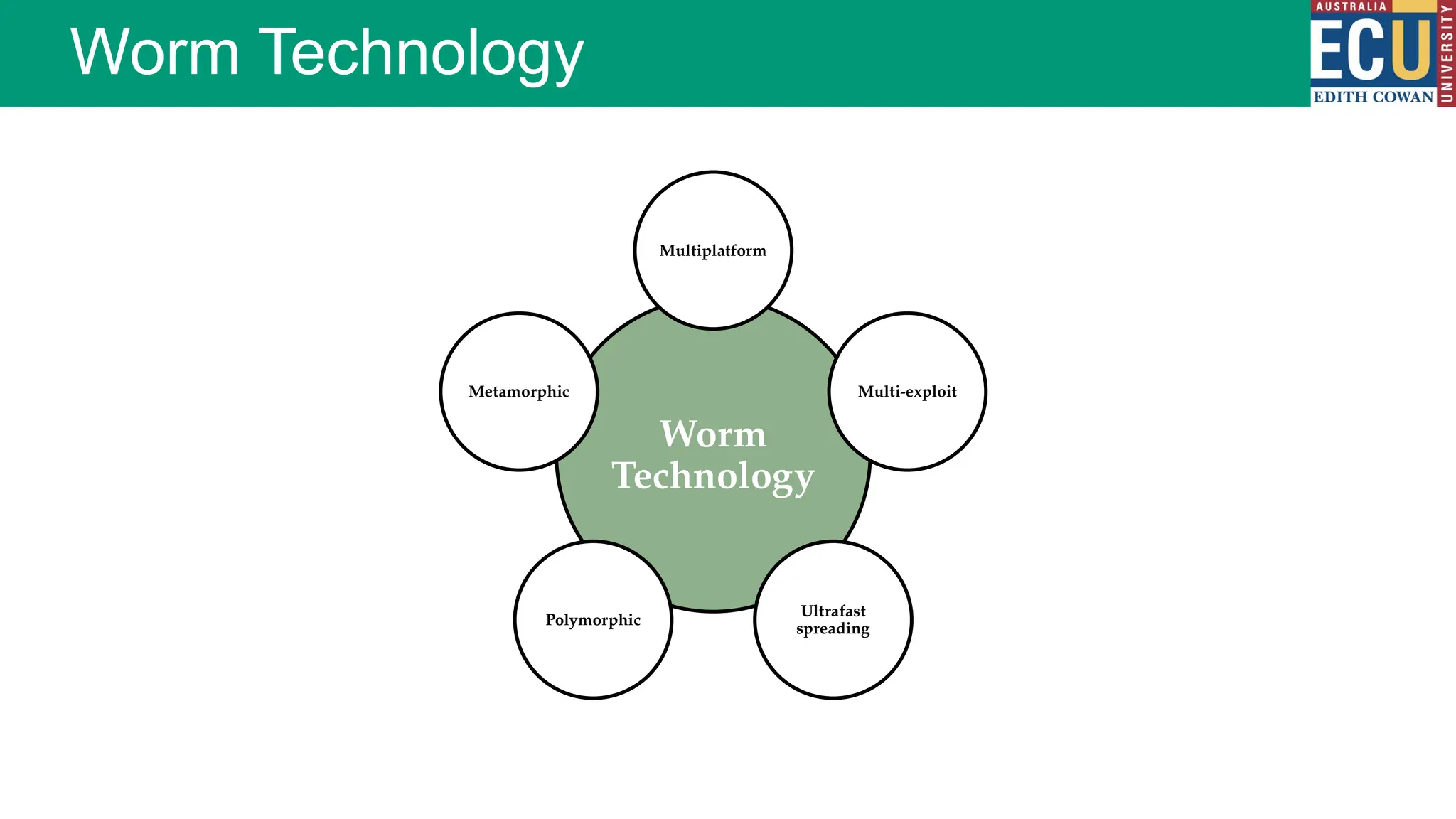
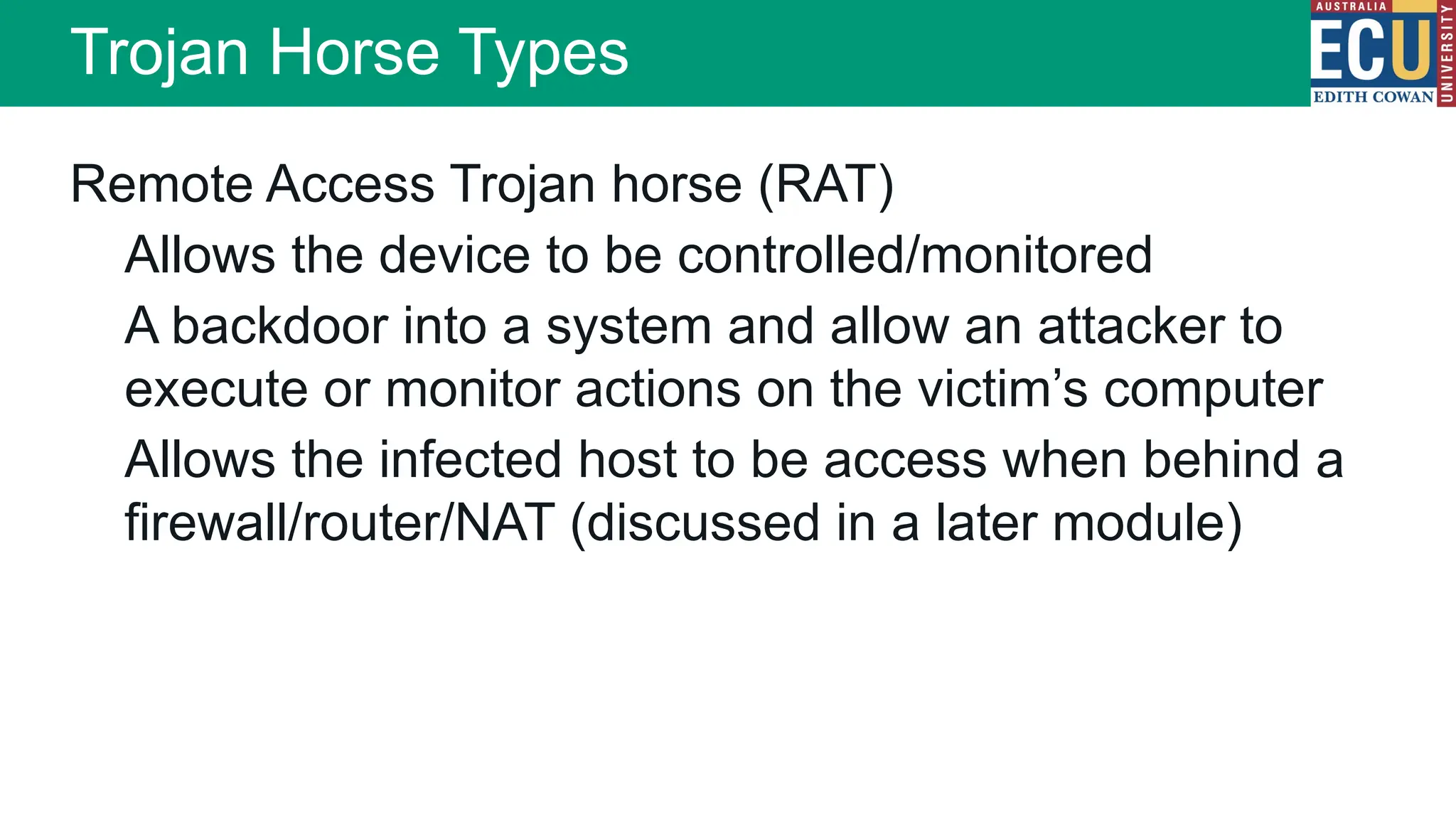
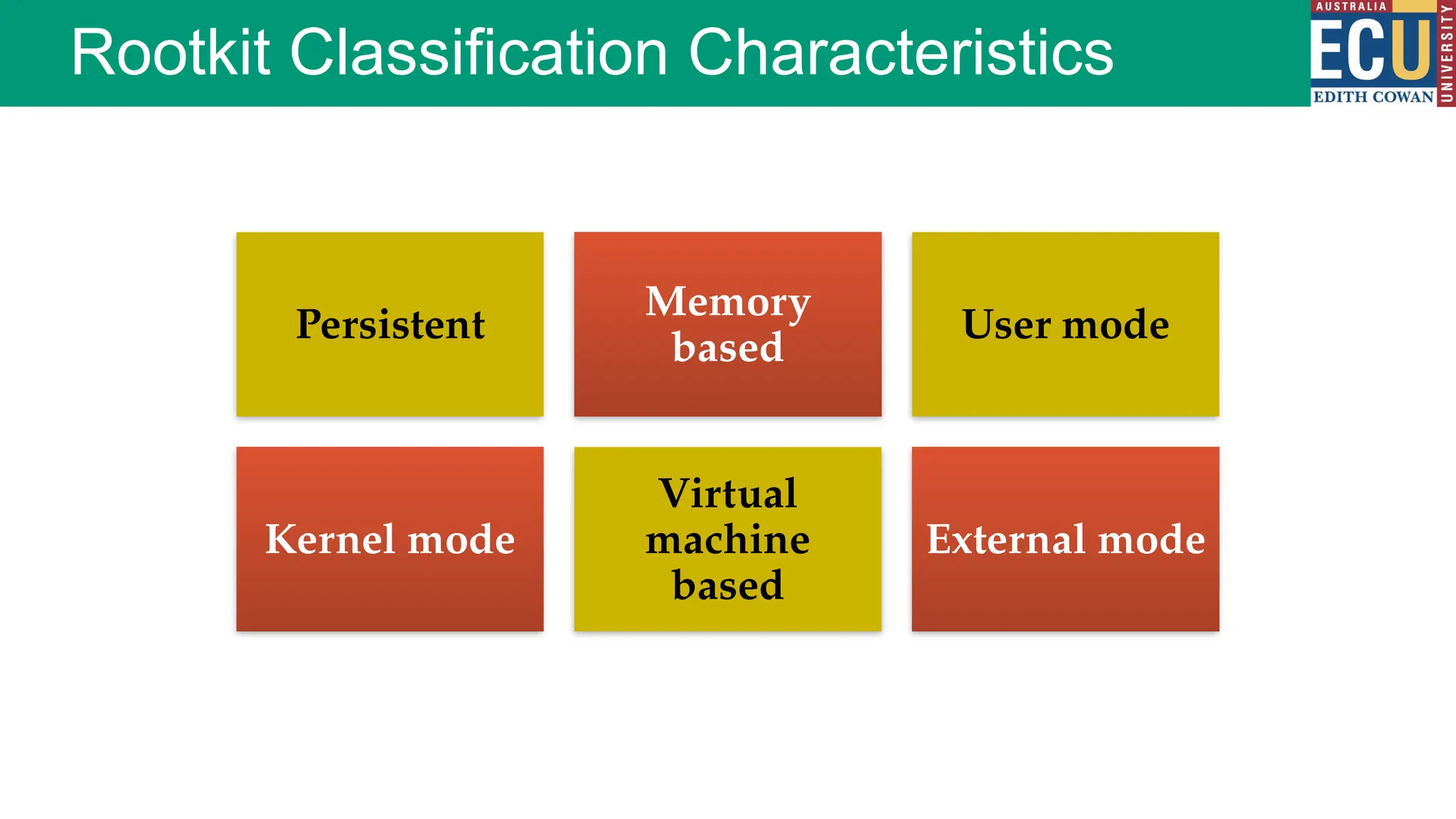
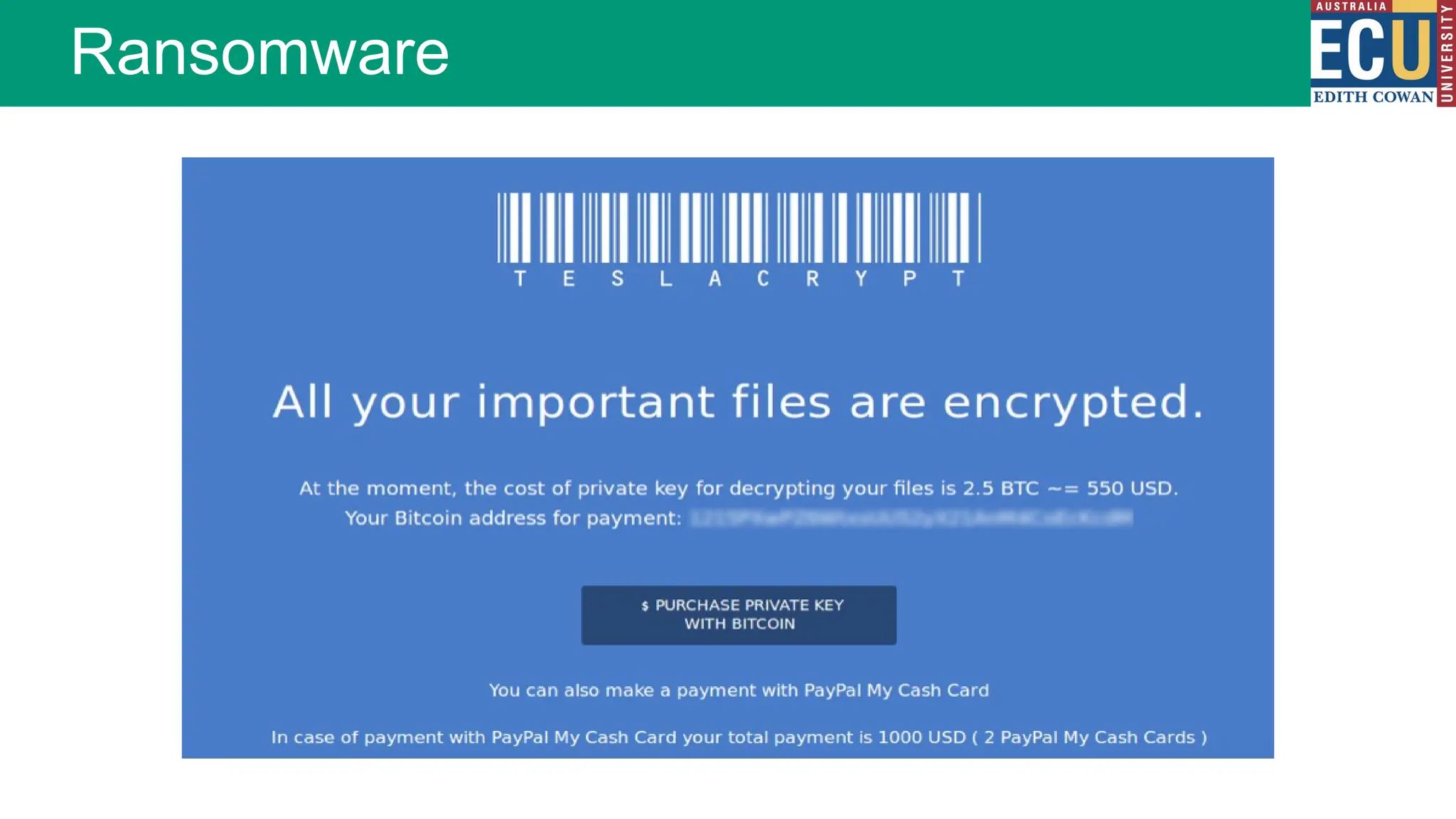
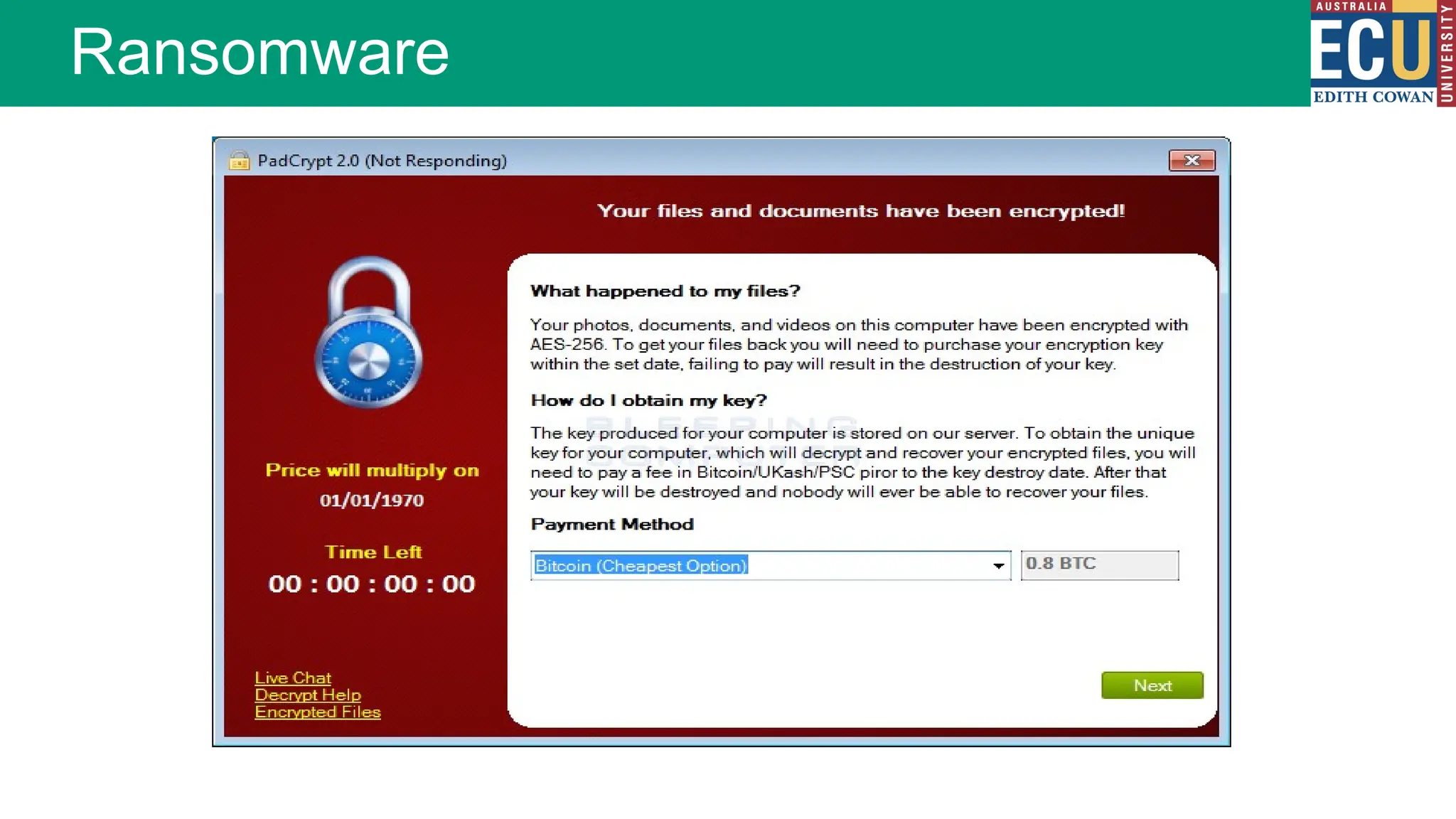
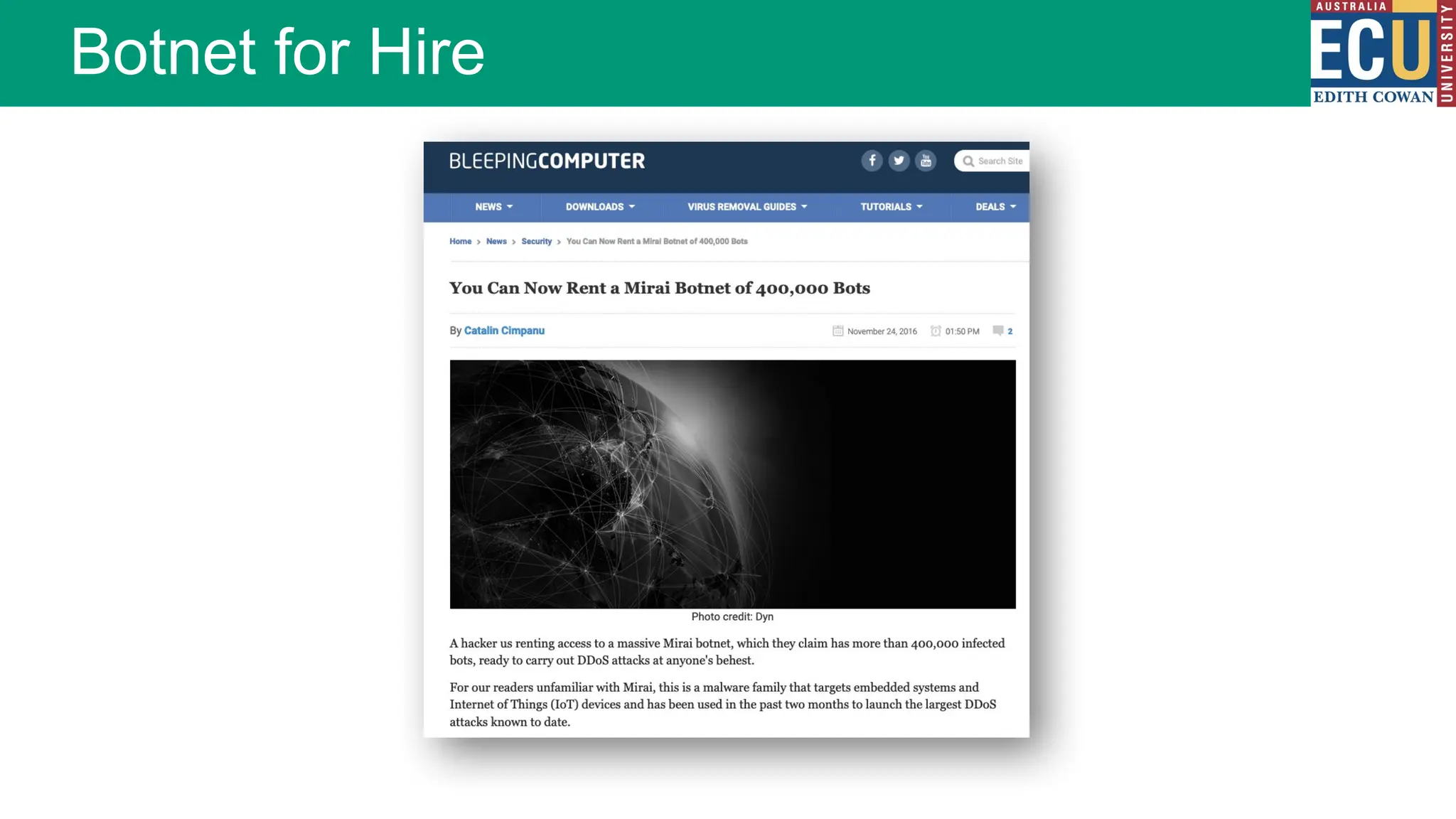
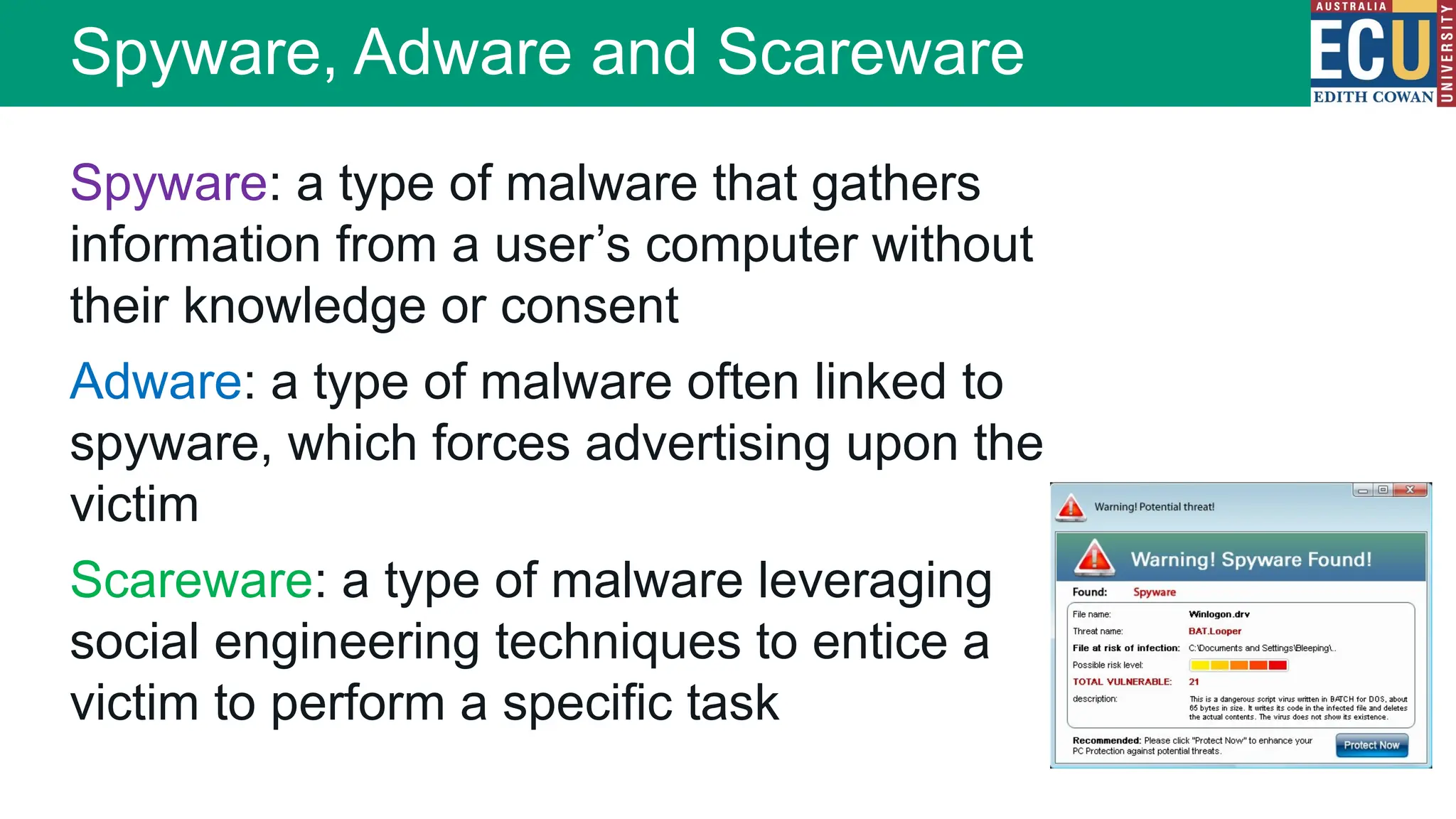
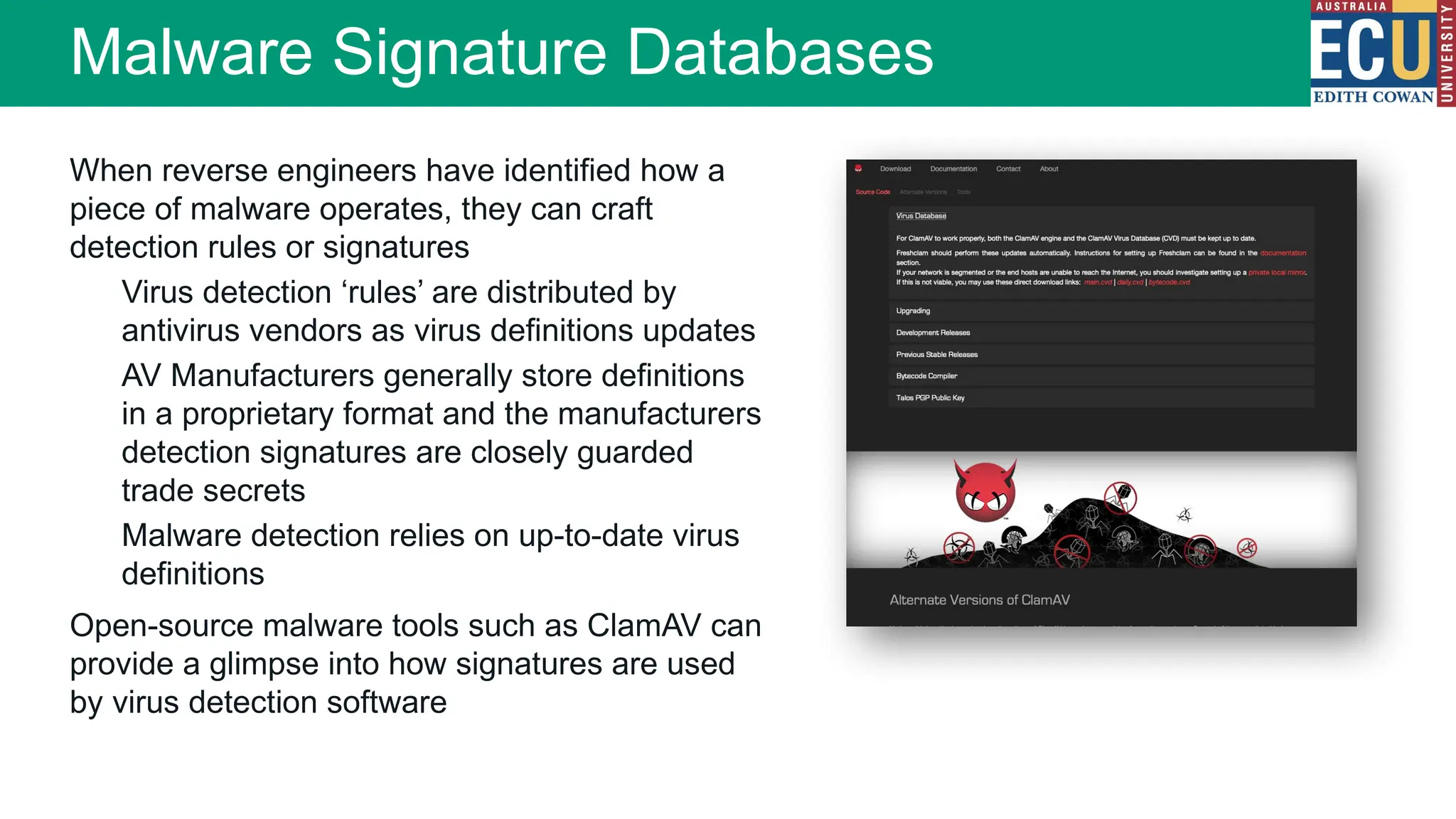
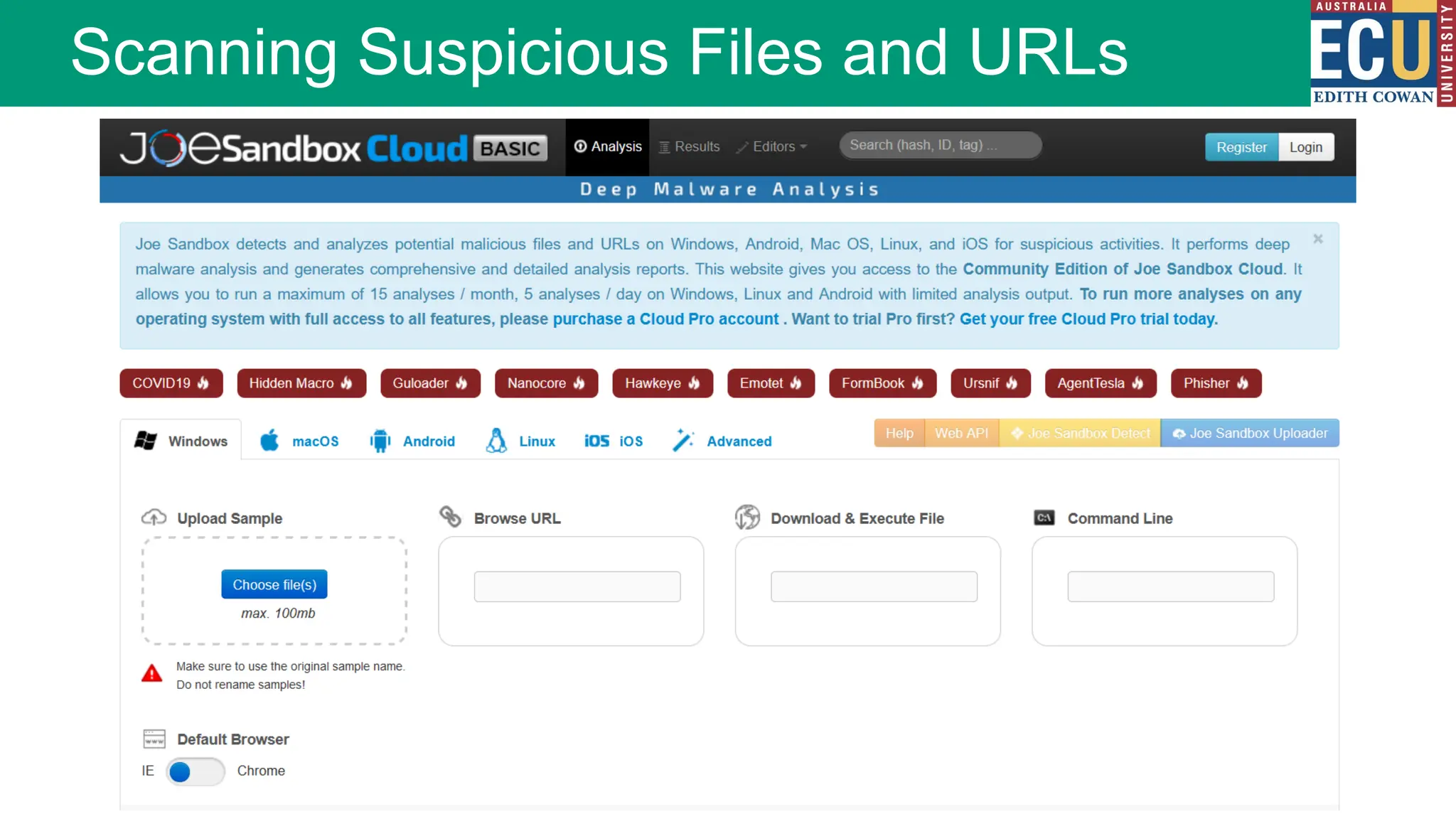
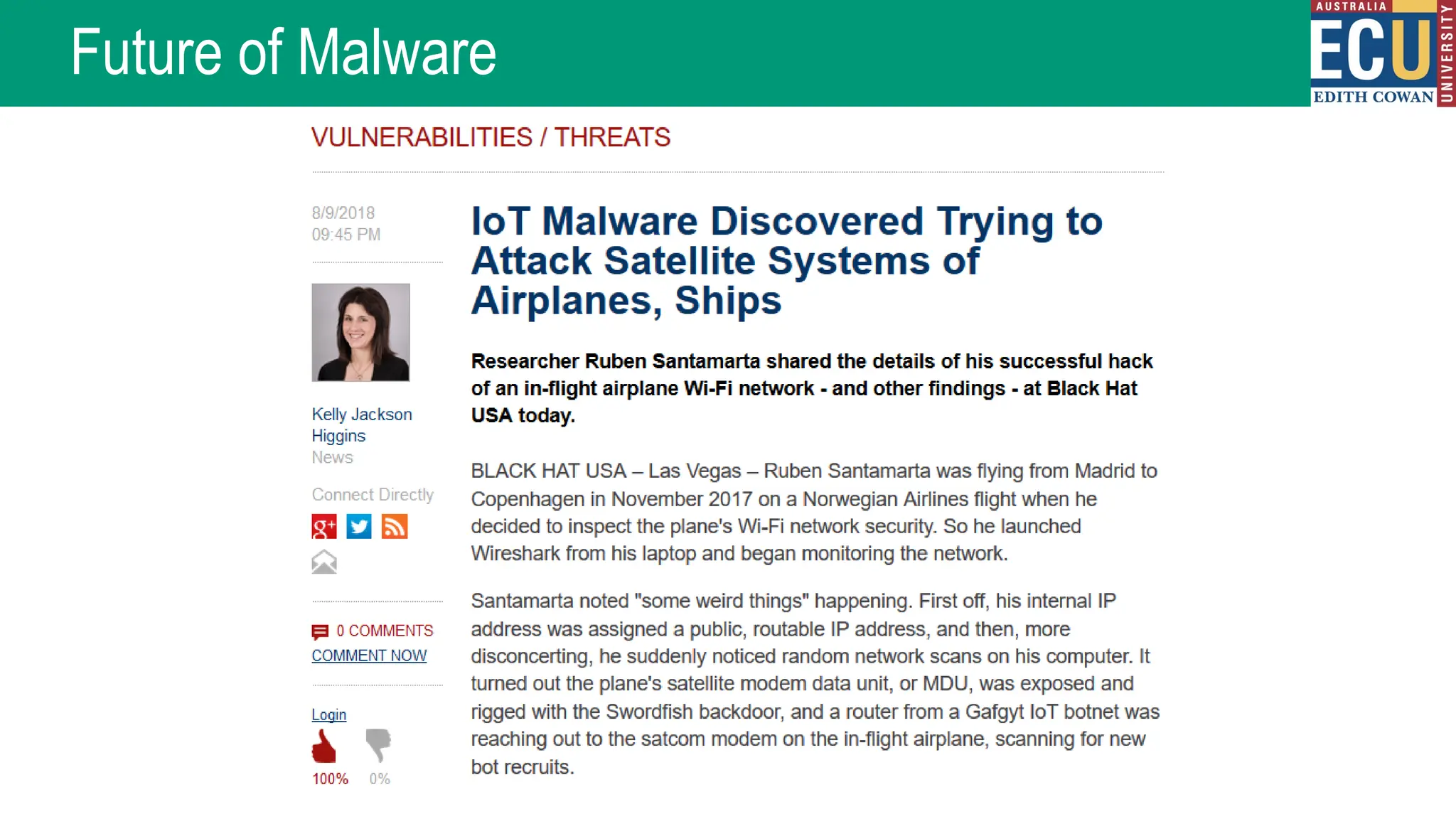
The document provides an extensive overview of malware, including its definitions, types, propagation methods, and impact on computer systems. It outlines various categories such as viruses, worms, trojan horses, and explains attack strategies like large-scale and targeted attacks, along with defense mechanisms. The information covers the evolution of malware, its effects on organizations, and strategies to detect and prevent malware infections.