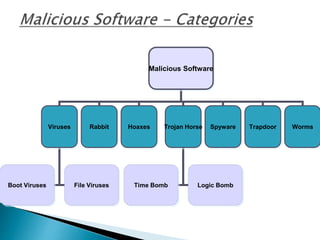
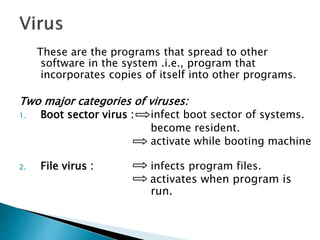
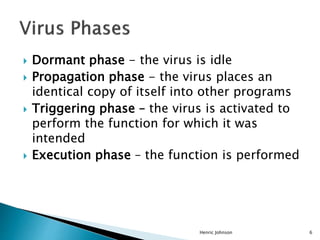
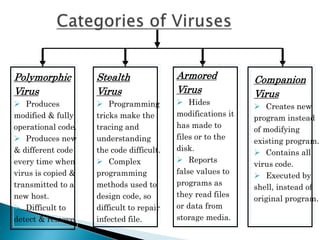
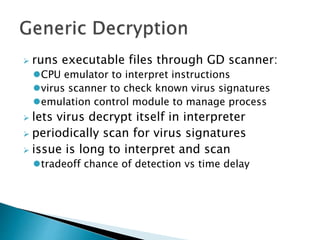
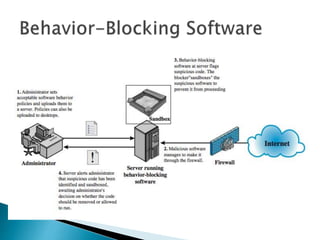
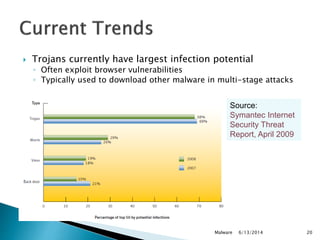
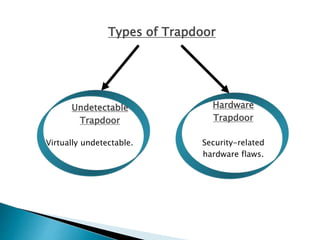
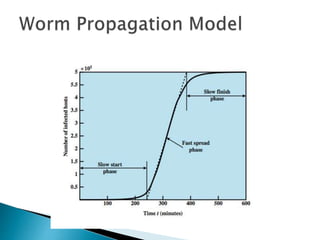
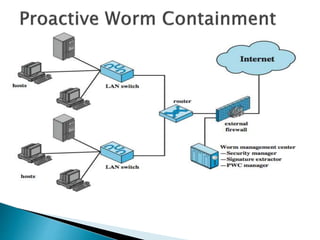
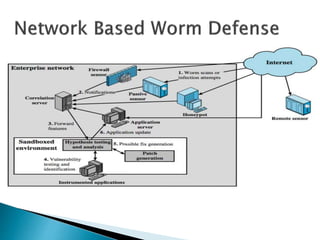
This document discusses different types of malicious software including viruses, trojan horses, worms, and spyware. It provides details on how each type spreads and the harm they can cause. Viruses spread by infecting other files or programs and can corrupt data or disrupt systems. Trojan horses disguise harmful programs as legitimate ones. Worms replicate across networks and can delete files or disrupt systems. The document outlines strategies for prevention, detection, and removal of malicious software.