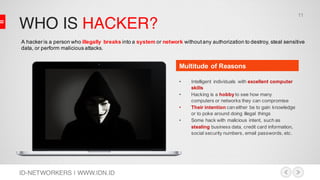
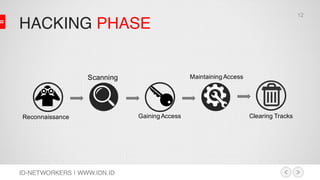
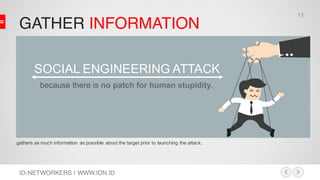
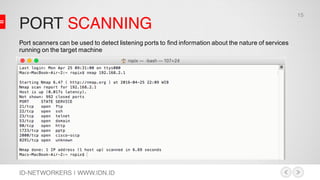
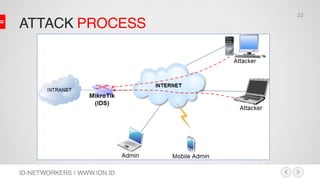
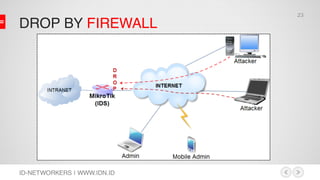
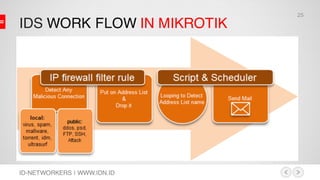
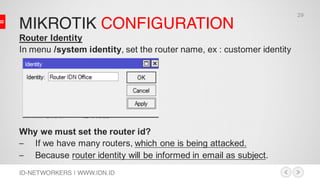
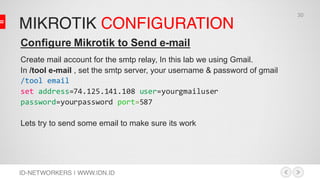
This document discusses network security and MikroTik routers. It provides background on the author and his experience. It then summarizes threats to internet security like hacking, cybercrime, and effects on businesses. It outlines the phases of hacking like reconnaissance, scanning, gaining access, and maintaining access. Finally, it demonstrates how to configure a MikroTik router for intrusion detection, including setting up email alerts.


















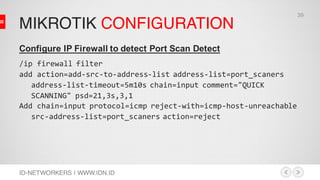
![MIKROTIK CONFIGURATION
ID-NETWORKERS | WWW.IDN.ID
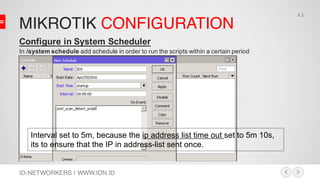
Configure MikroTik to Run the Script
Scripts can be written directly to console or can be stored in Script
repository
• Example script that directly run in console:
[admin@MikroTik]>:put (45+23+1)
• Script repository ( /system script) can be run by running other
script, on event scheduler or netwatch
40](https://image.slidesharecdn.com/bsipresentation-160507070255/85/MikroTik-Security-40-320.jpg)
![MIKROTIK CONFIGURATION
ID-NETWORKERS | WWW.IDN.ID
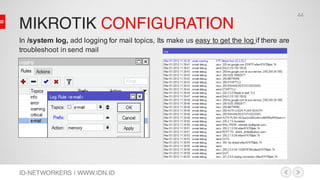
Configure in Script Repository (/system script)
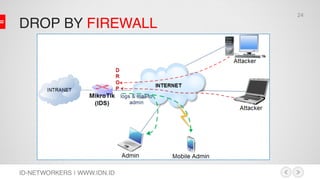
:foreach a in=[/ip firewall address-list find list=port_scaners] do={:global
ip [/ip firewall address-list get $a address];
:log warning ("Scan Attack from:" .$ip);
:local sysname [/system identity get name];
:local date [/system clock get date];
:local time [/system clock get time];
/tool e-mail send from="Router $sysname<mikrotik.ids@gmail.com>"
to="indomedia.monitoring@yahoo.com" start-tls=yes server=74.125.127.108
port=587 user=mikrotik.ids password=t3ddyb3ar subject="Scan Attack!" body="
Dear Admin, n nWe have note that on $date at $time. There is scanning attack
to $sysname from IP $ip, and has been blocked by firewall. nSee
http://whois.sc/$ip for detail IP attacker information. n n Thanks & Regard
nIDS Machine":log warning "IP intruder telah diblock dan Email report telah
dikirim."}
Find match address list
Get the IP address
Log it on machine
Get router id, date & time
send the report
41](https://image.slidesharecdn.com/bsipresentation-160507070255/85/MikroTik-Security-41-320.jpg)