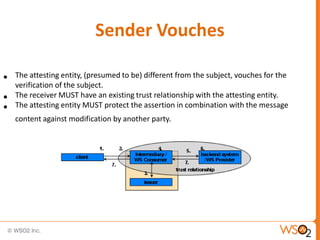
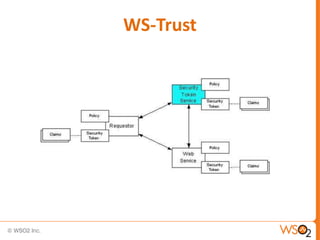
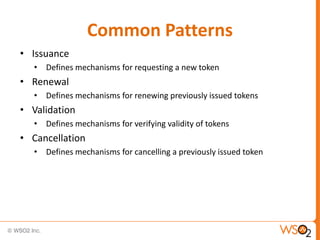
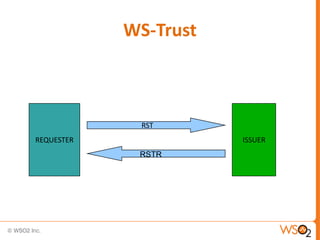
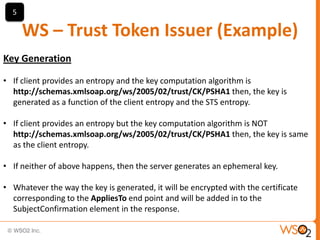
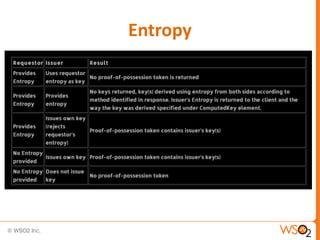
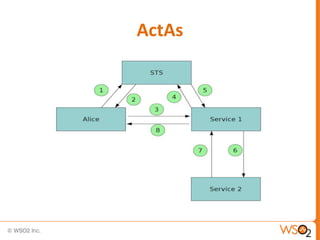
SAML enables portable identities by defining standards for assertions, protocols and bindings. It allows identities established in one trust domain to be asserted in another domain. SAML assertions include authentication, authorization and attribute statements. SAML tokens can be included in SOAP message headers according to the WS-Security standard. They can be included directly or referenced remotely. WS-Trust is a standard that defines mechanisms for establishing, brokering and assessing trust relationships as well as issuing and exchanging security tokens like SAML tokens. Common patterns in WS-Trust include issuance, renewal, validation and cancellation of tokens.