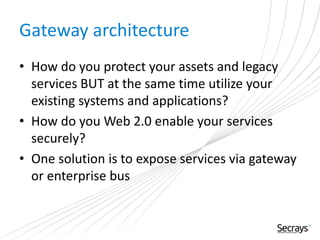
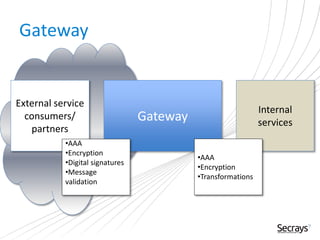
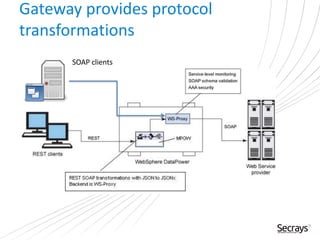
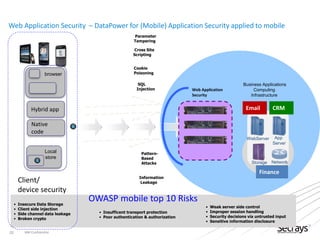
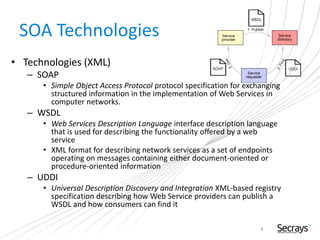
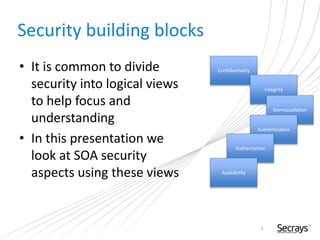
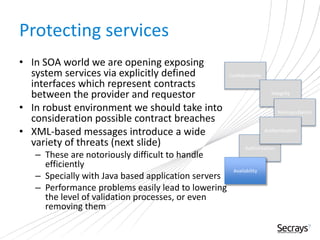
This document discusses security considerations for service-oriented architectures (SOAs). It begins by defining SOA and some common SOA technologies like SOAP, WSDL, and UDDI. It then covers important security concepts like confidentiality, integrity, non-repudiation, authentication, authorization, and availability. Specific security standards and approaches are discussed for each concept, such as encryption for confidentiality and digital signatures for integrity and non-repudiation. Authentication methods like digital certificates and SAML are also described. The document advocates for defining clear security policies and separating policy enforcement from decision making. It concludes by discussing threats to XML and debates between using REST vs SOAP/WS-Security approaches.





![To REST or not?
• REST simplicity is appealing
– Implementing a SOAP/SAML
authentication/authorization scheme is not
necessarily a trivial exercise
• With Web 2.0 REST w/JSON has become a de
facto standard
• The bottom line is that REST just does not
have the same security standards as you
have within SOAP with WS-Security
– RESTful services are point-to-point solutions
• Large organizations will have legacy SOAP
– Should they turn to REST?
{
"firstName": "John",
"lastName": "Smith",
"age": 25,
"address": {
"streetAddress": "21 2nd Street",
"city": "New York",
"state": "NY",
"postalCode": 10021
},
"phoneNumbers": [
{
"type": "home",
"number": "212 555-1234"
},
{
"type": "fax",
"number": "646 555-4567"
}
]
}](https://image.slidesharecdn.com/soasecuritysecrays-150319085449-conversion-gate01/85/SOA-Security-18-320.jpg)