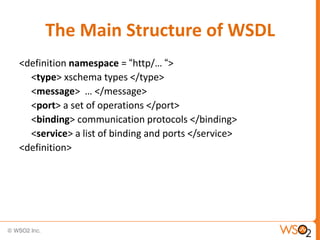
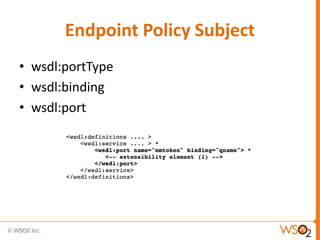
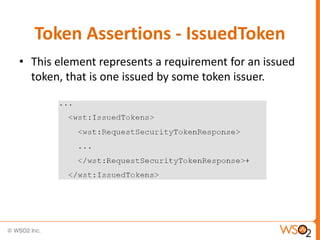
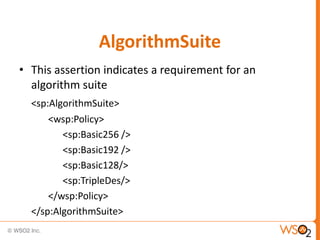
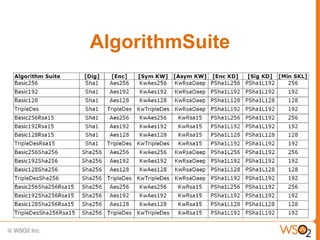
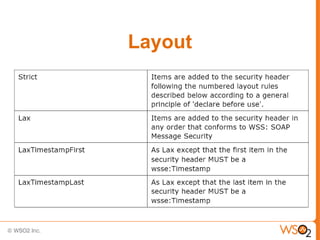
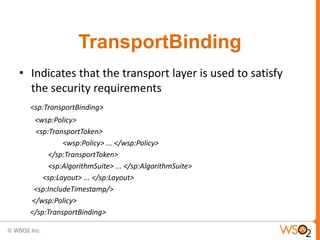
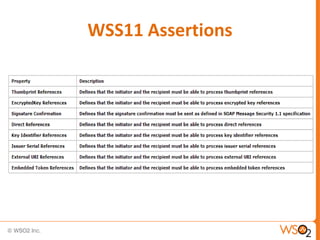
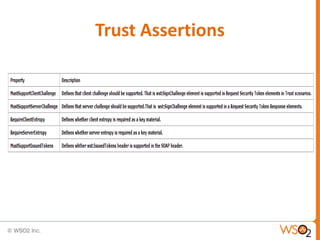
This document provides an overview of WS-Security Policy, which defines a framework for expressing security requirements for web services using policies. It discusses how WS-Security Policy builds on WS-Policy to allow endpoints to express security requirements through policy assertions. These include protection assertions to specify signed or encrypted parts, token assertions to specify required token types, and binding assertions to define how messages are secured. The document also covers how policies can be associated with WSDL definitions and how policy compatibility and intersections are defined.




![WS-Policy Framework
• WS-Policy, defines a framework for describing policy
assertions.
• WS-PolicyAttachment, describes how policies are
attached to resource [e.g. WSDL]
• WS-PolicyAssertions, describes a common set of
assertions that are applicable across different
domains.](https://image.slidesharecdn.com/ws-securitypolicy-131128012528-phpapp01/85/WS-SecurityPolicy-5-320.jpg)




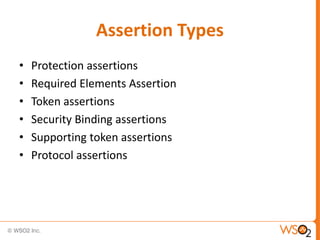


















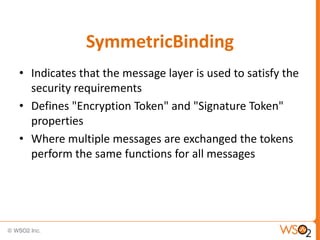







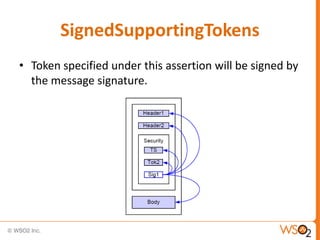
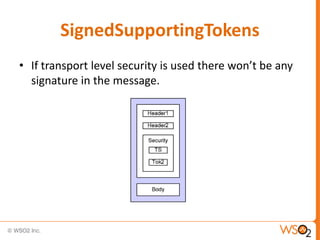


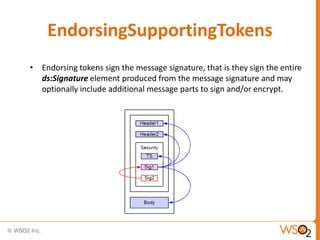
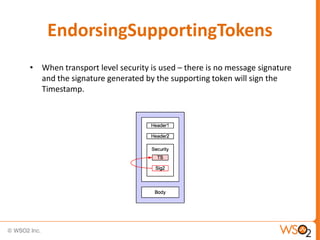



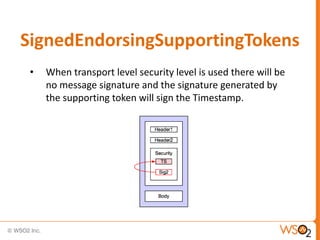



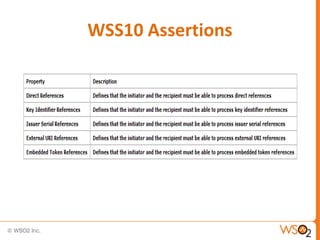
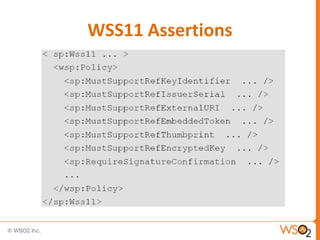

![Associating a Policy
• Define the policy within the WSDL [ in the WSDL it
self or pointed to from the WSDL]
• Stand alone policy which points back to the web
service or services associated with it – Arbitrary
Resource Attachment](https://image.slidesharecdn.com/ws-securitypolicy-131128012528-phpapp01/85/WS-SecurityPolicy-60-320.jpg)