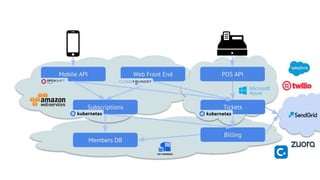
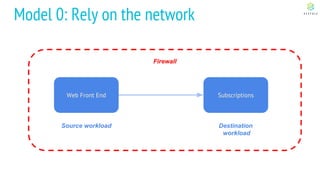
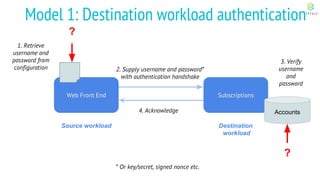
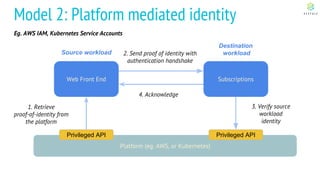
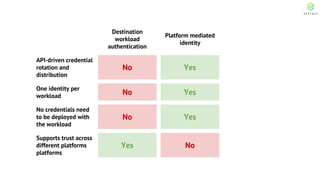
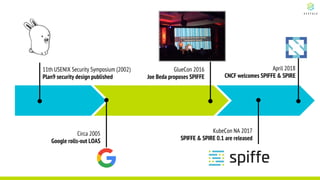
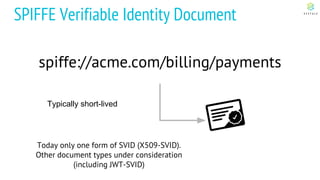
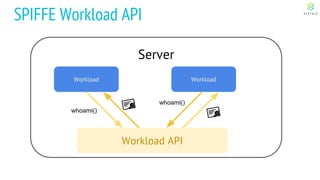
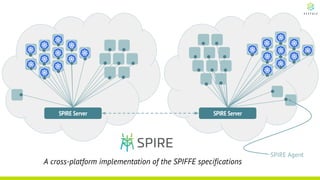
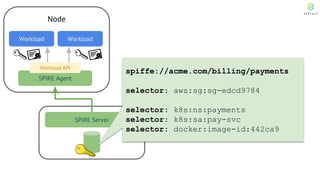
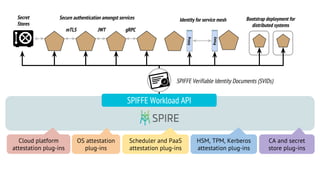
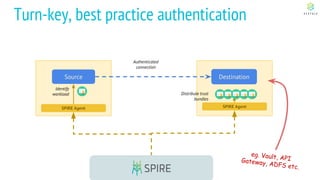
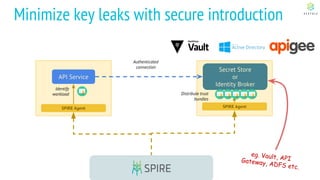
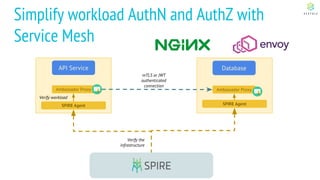
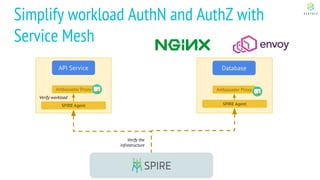
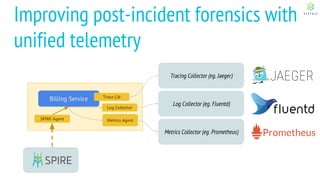
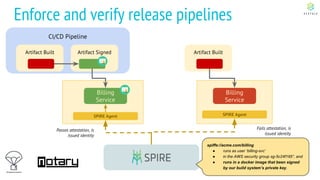
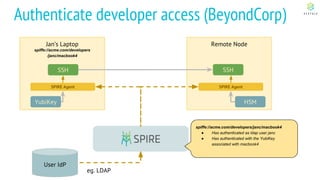
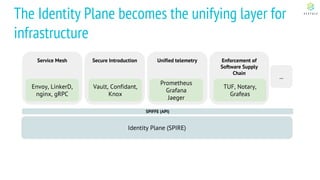
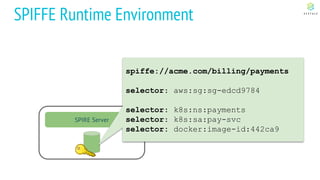
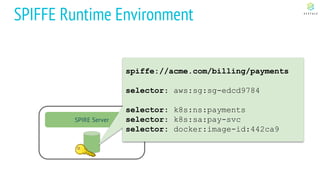
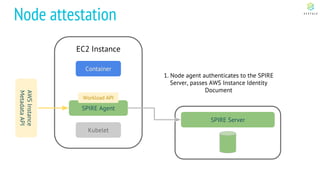
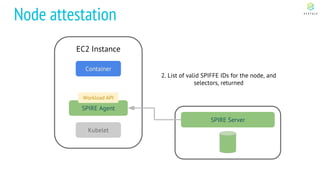
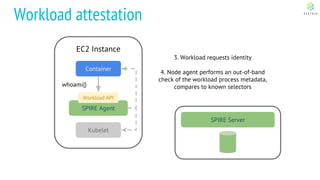
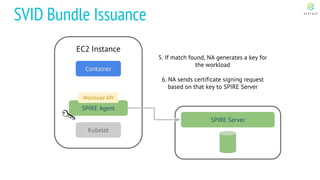
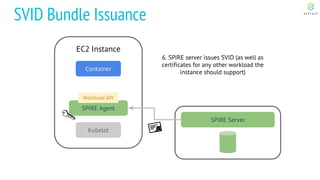
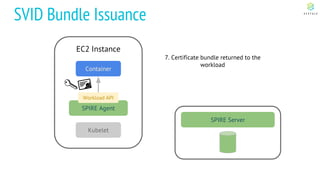
This document discusses Cloud Native Identity Management using SPIFFE (Secure Production Identity Framework for Everyone) and SPIRE (SPIFFE Runtime Environment). It provides an overview of SPIFFE and SPIRE, including how they address identity management challenges in cloud-native environments. It then summarizes how SPIRE implements the SPIFFE specifications through a node attestation and workload attestation process where a SPIRE agent authenticates to a server, retrieves selectors to verify workloads, and issues signed identity documents when a workload matches the selectors.