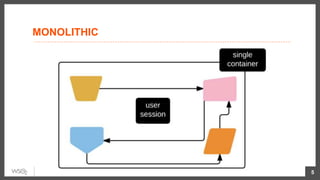
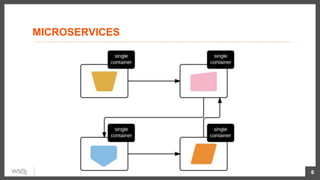
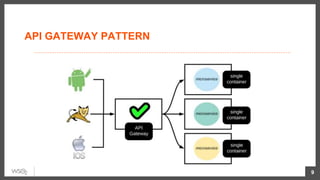
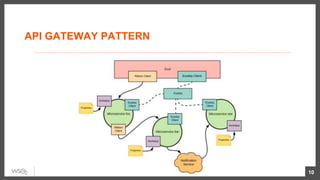
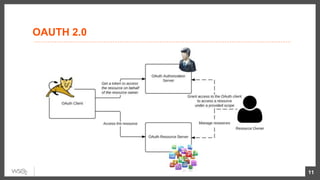
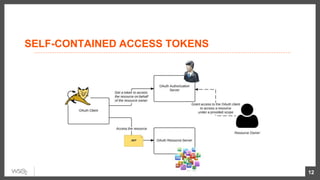
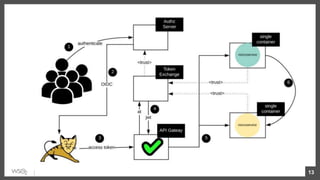
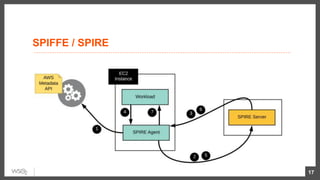
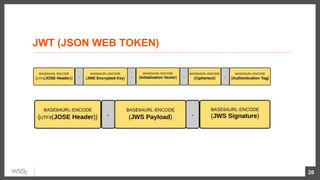
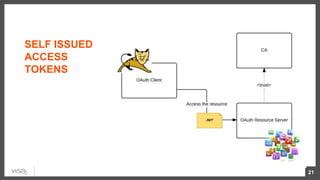
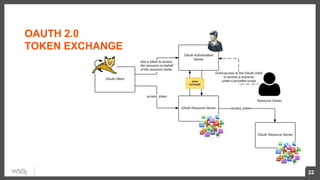
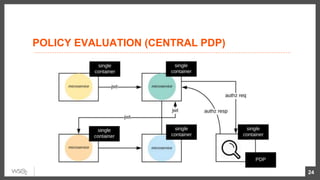
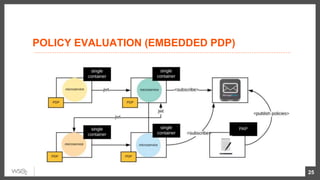
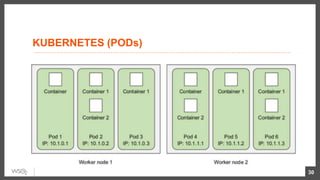
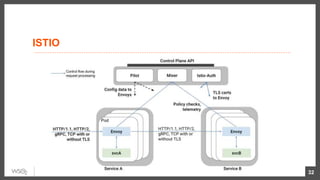
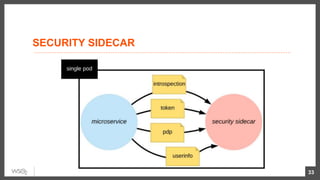
This document discusses security considerations for microservices architectures. It covers edge security using API gateways, service-to-service authentication using TLS and JWT, access control using centralized and embedded policy decision points, deployment models like Docker and Kubernetes, and the use of sidecars and service meshes like Istio for security. Key challenges with microservices include a broader attack surface, performance issues, and complexity in deployment and observability across services.