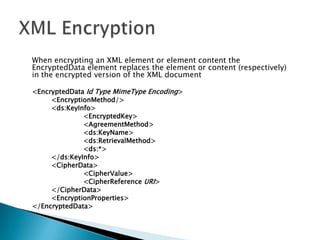
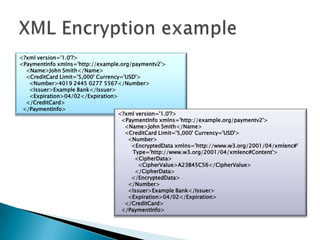
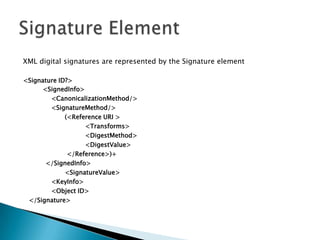
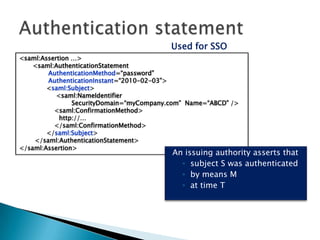
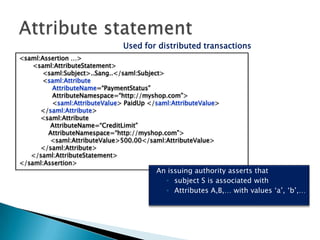
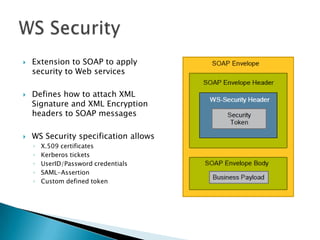
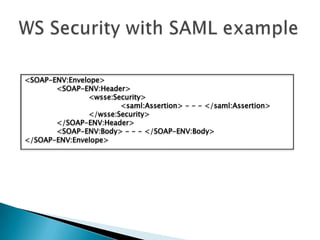
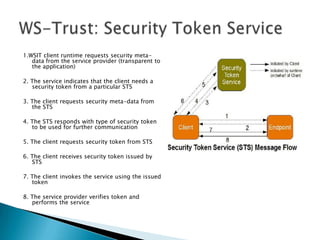
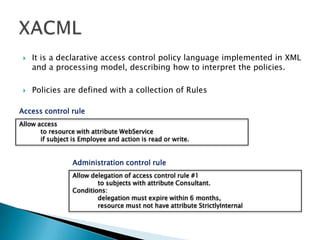
This document discusses several standards for web service security including XML encryption, XML digital signatures, SAML, WS-Security, WS-Trust, WS-SecureConversation, and XACML. It provides examples of how XML encryption can encrypt elements in an XML document, how XML signatures bind a sender's identity to a document, and how SAML can be used for single sign-on, distributing attributes, and authorization. It also summarizes the purpose and key aspects of standards like WS-Security, WS-Trust, and XACML.