This document discusses database system security and outlines several key areas to focus on:
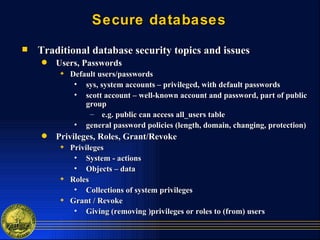
1. Secure the database itself by managing users, passwords, privileges and roles.
2. Secure the database management system (DBMS) by patching known vulnerabilities and controlling access to system files and directories.
3. Secure applications that interface with the database to prevent attacks like SQL injection.
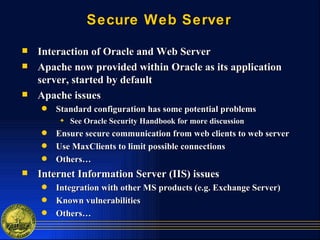
It also briefly outlines the importance of securing the operating system, web server, and network environment that interact with the database system. A lab exercise is proposed to examine security in these different areas of an Oracle database deployment.