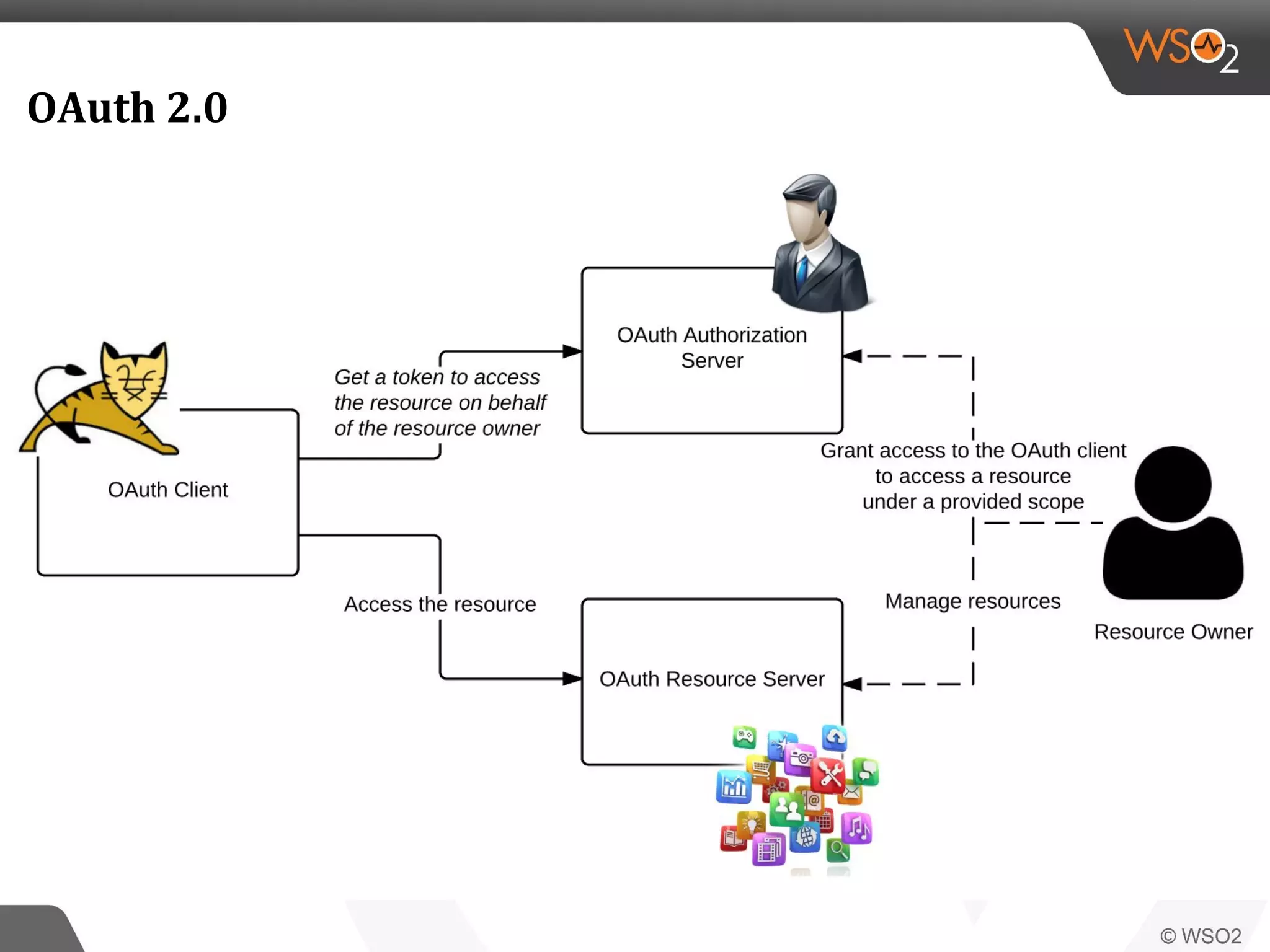
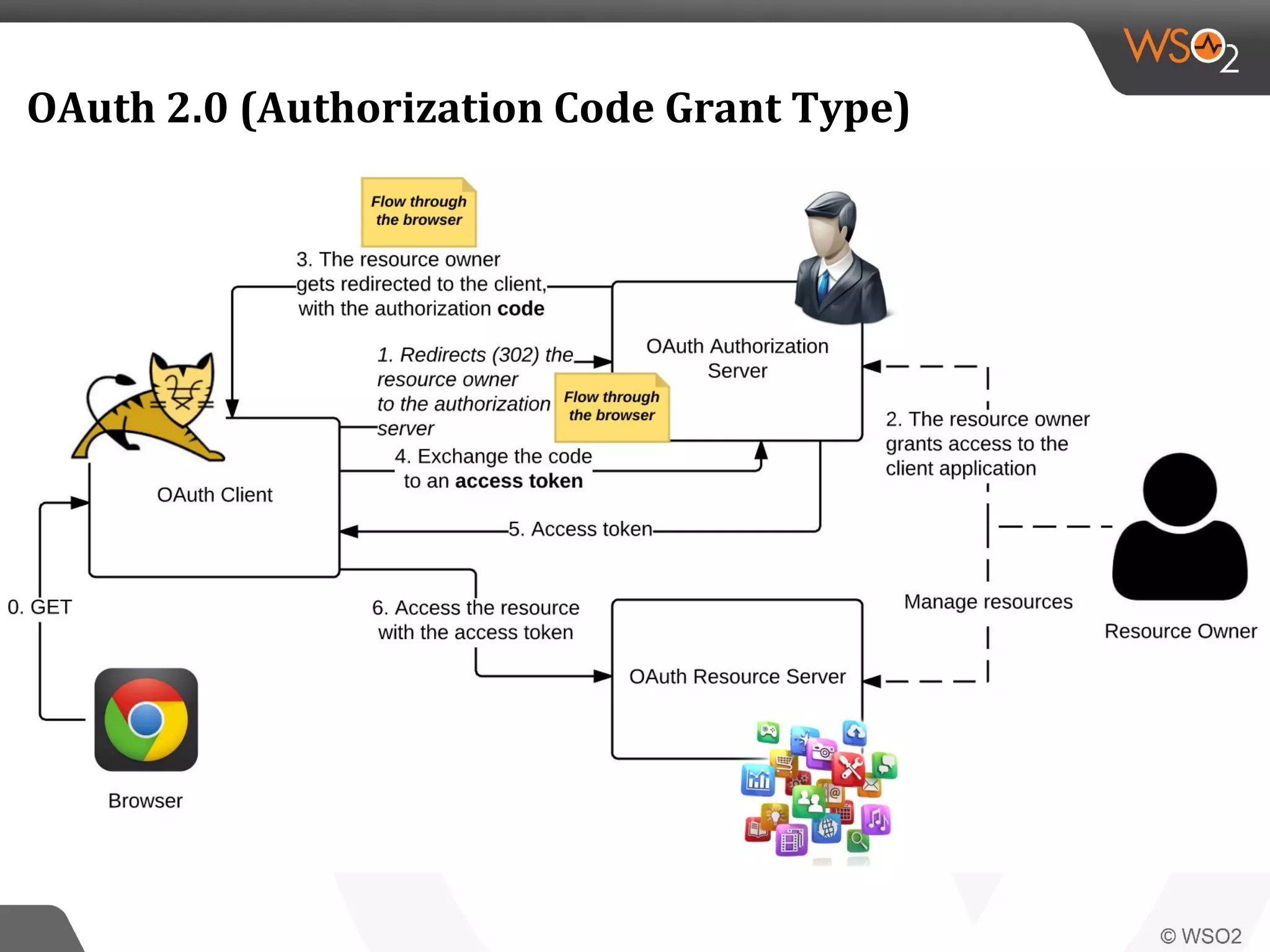
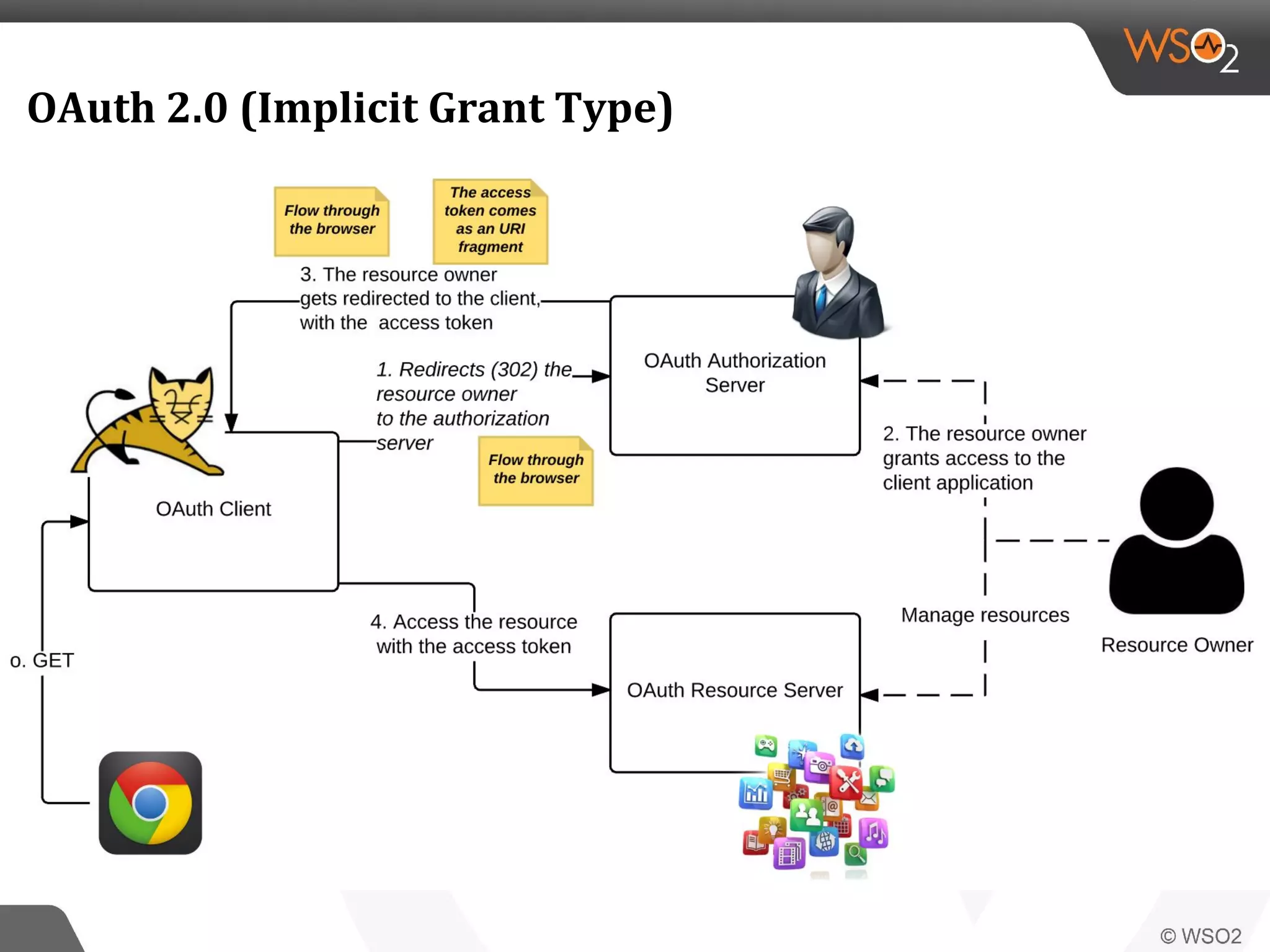
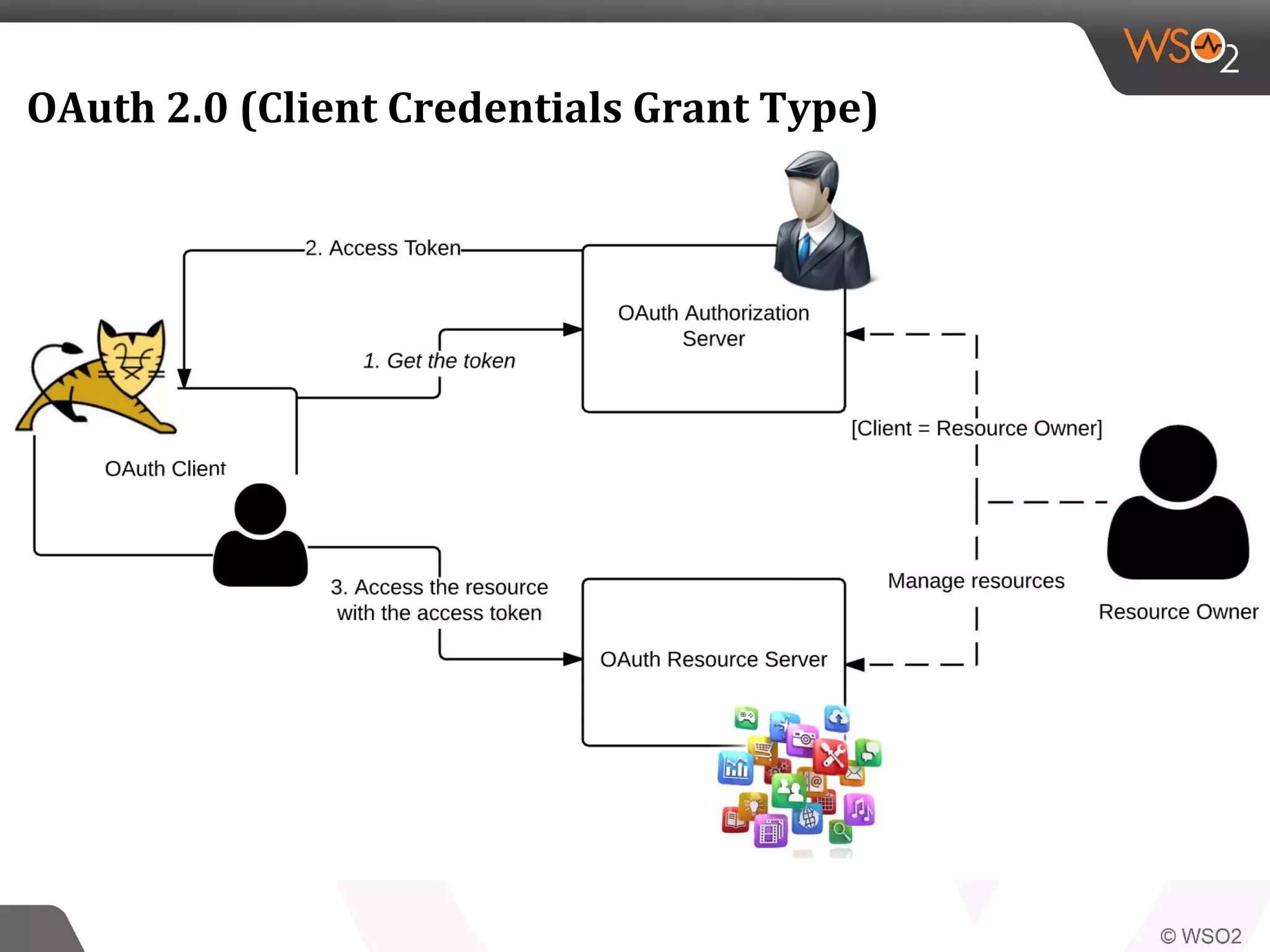
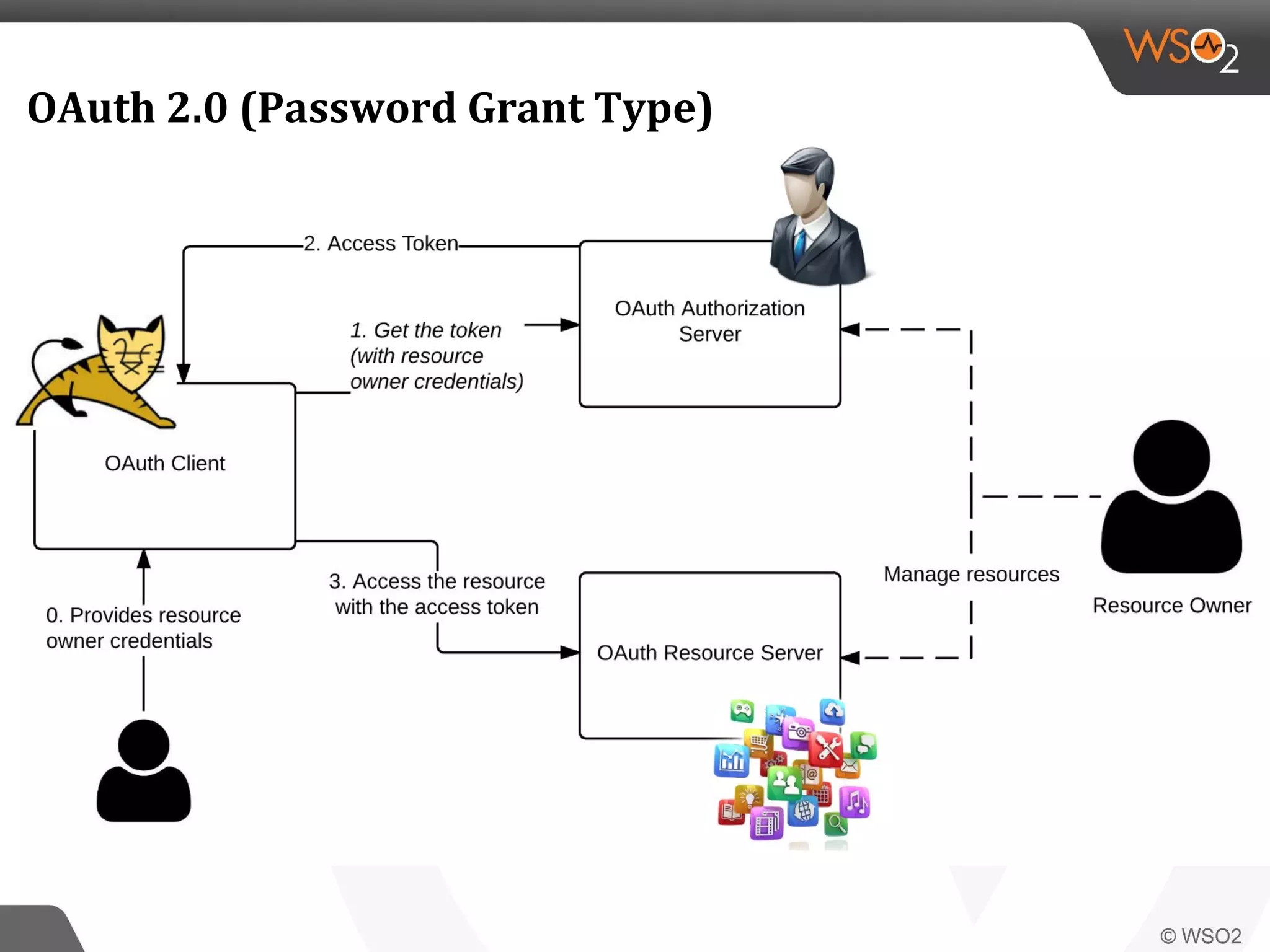
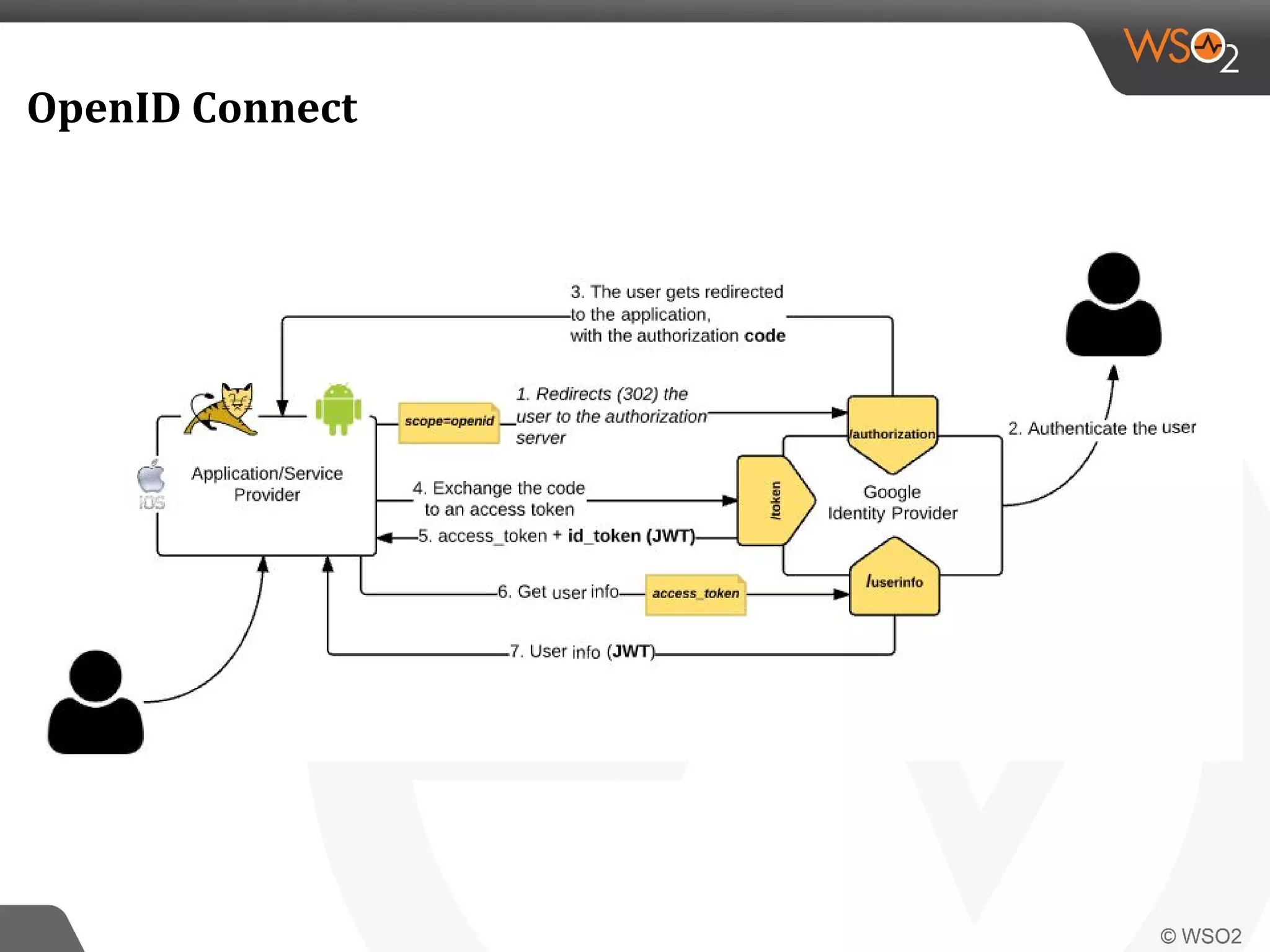
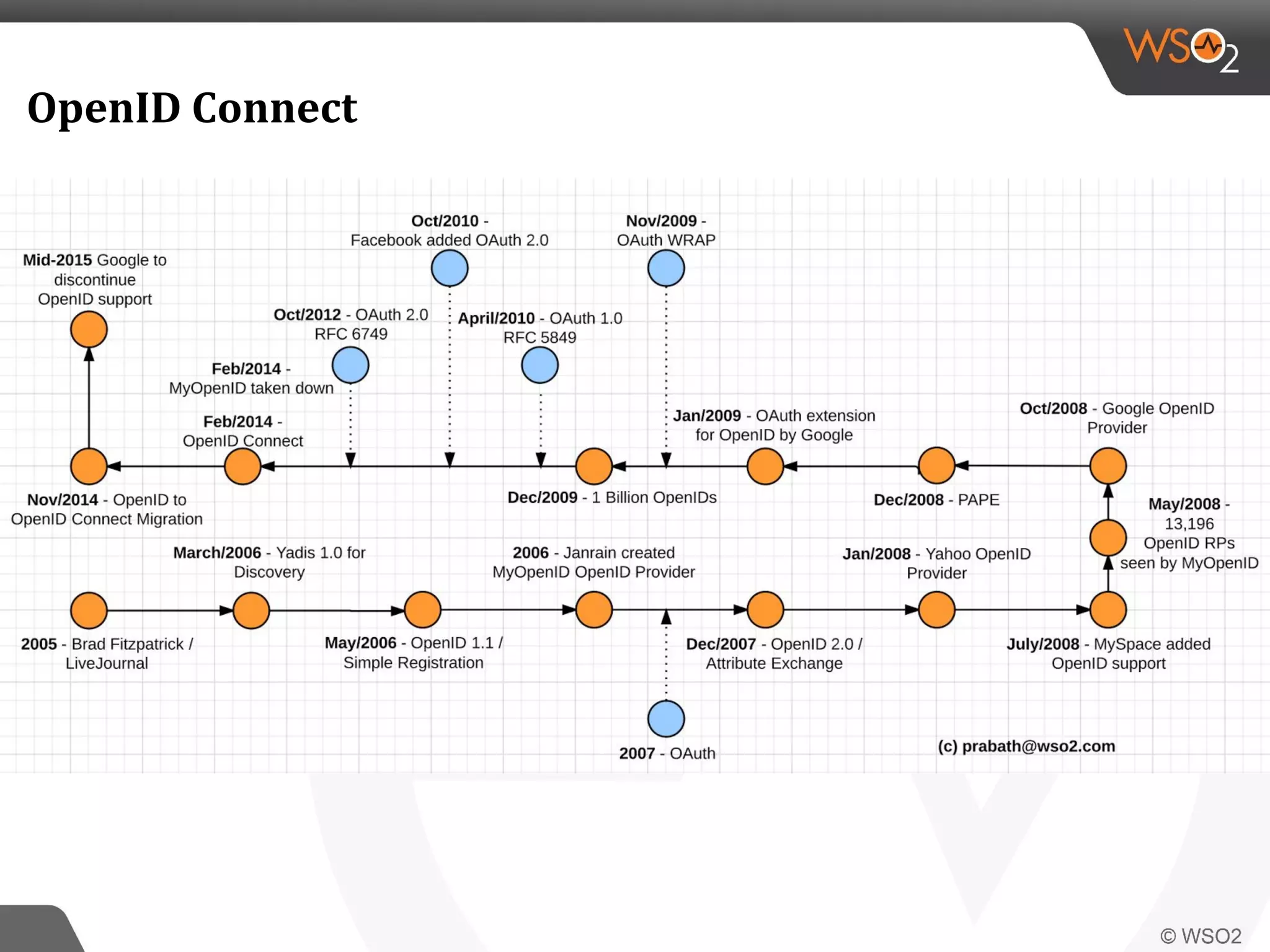
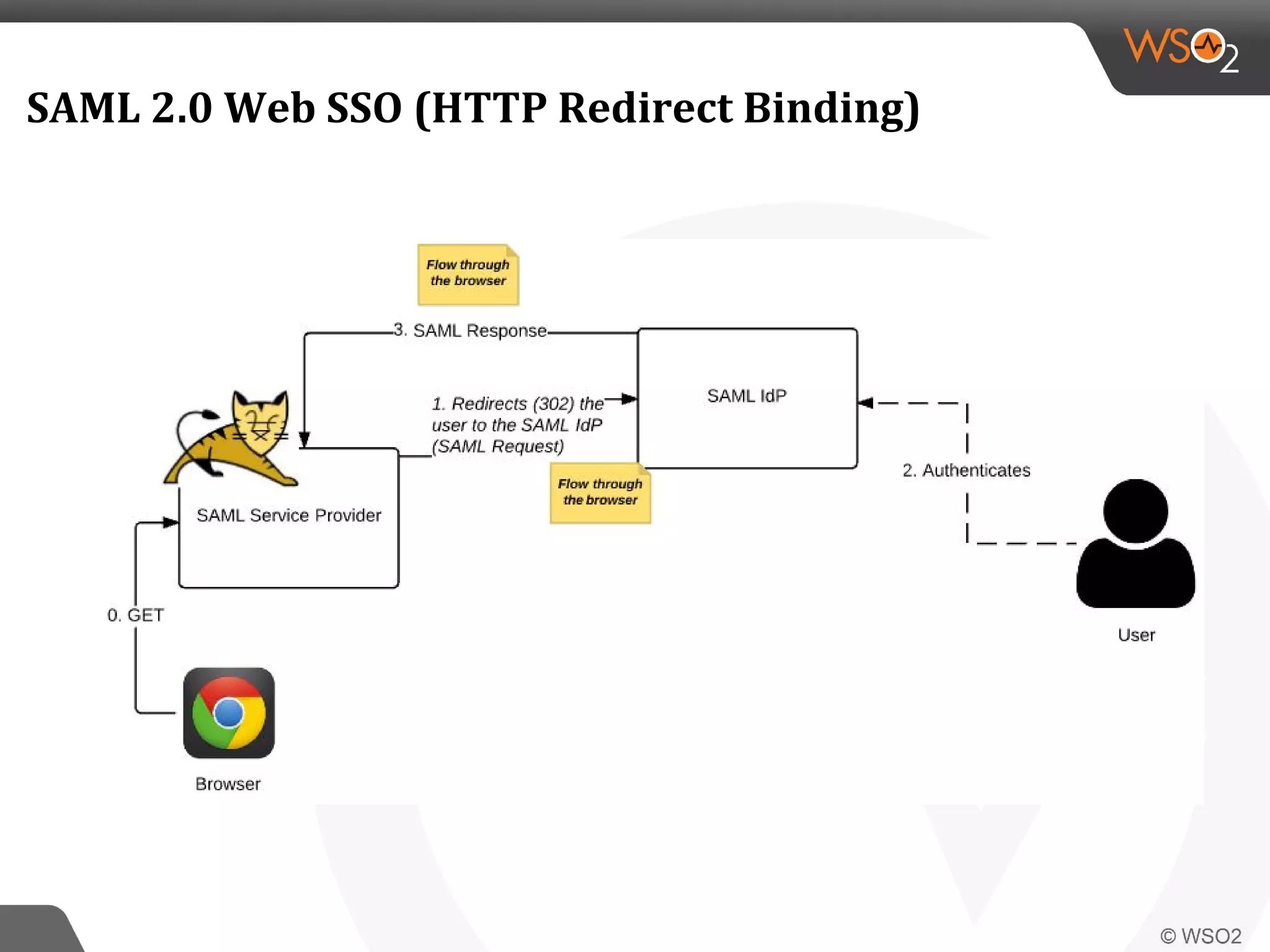
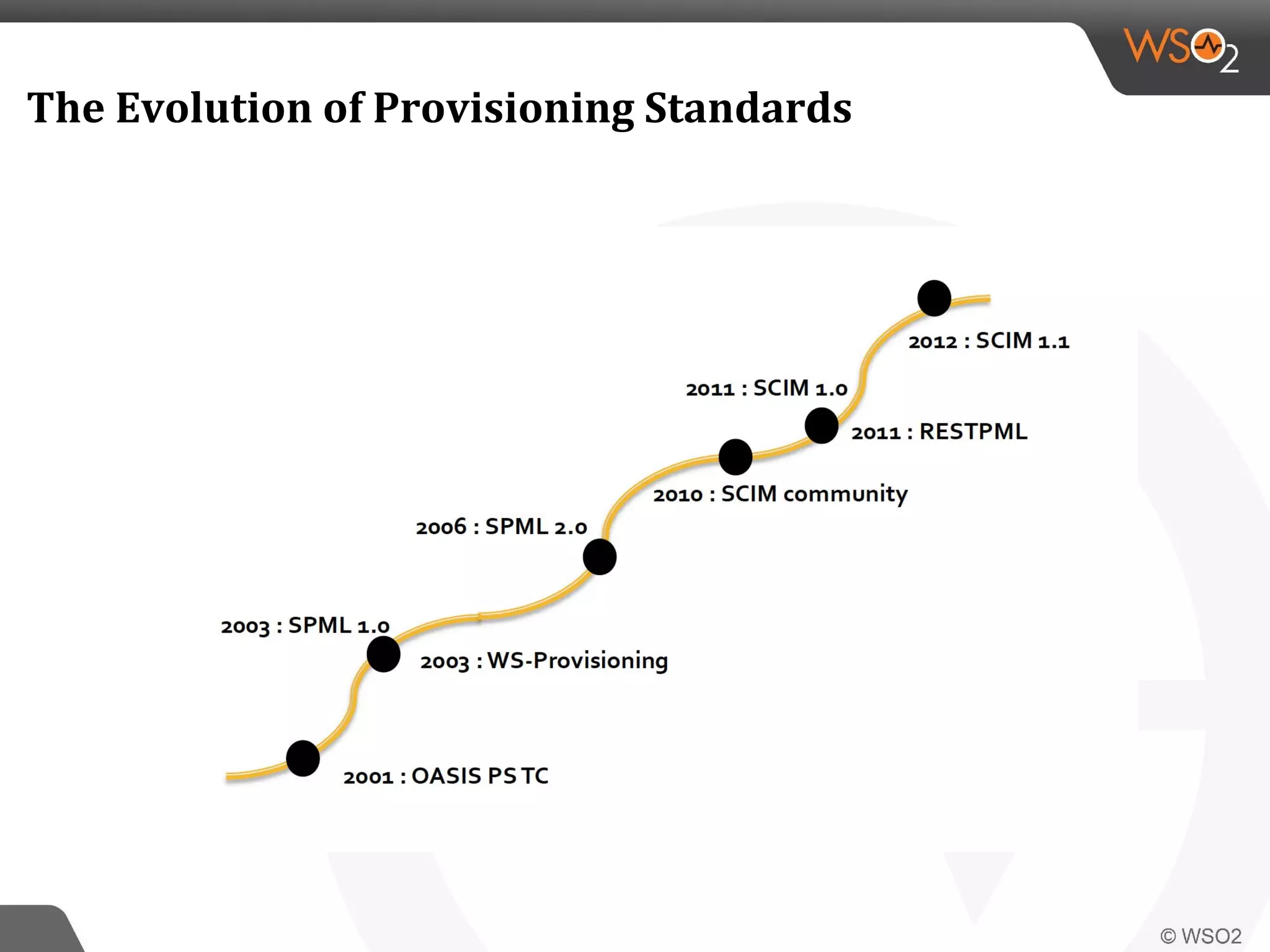
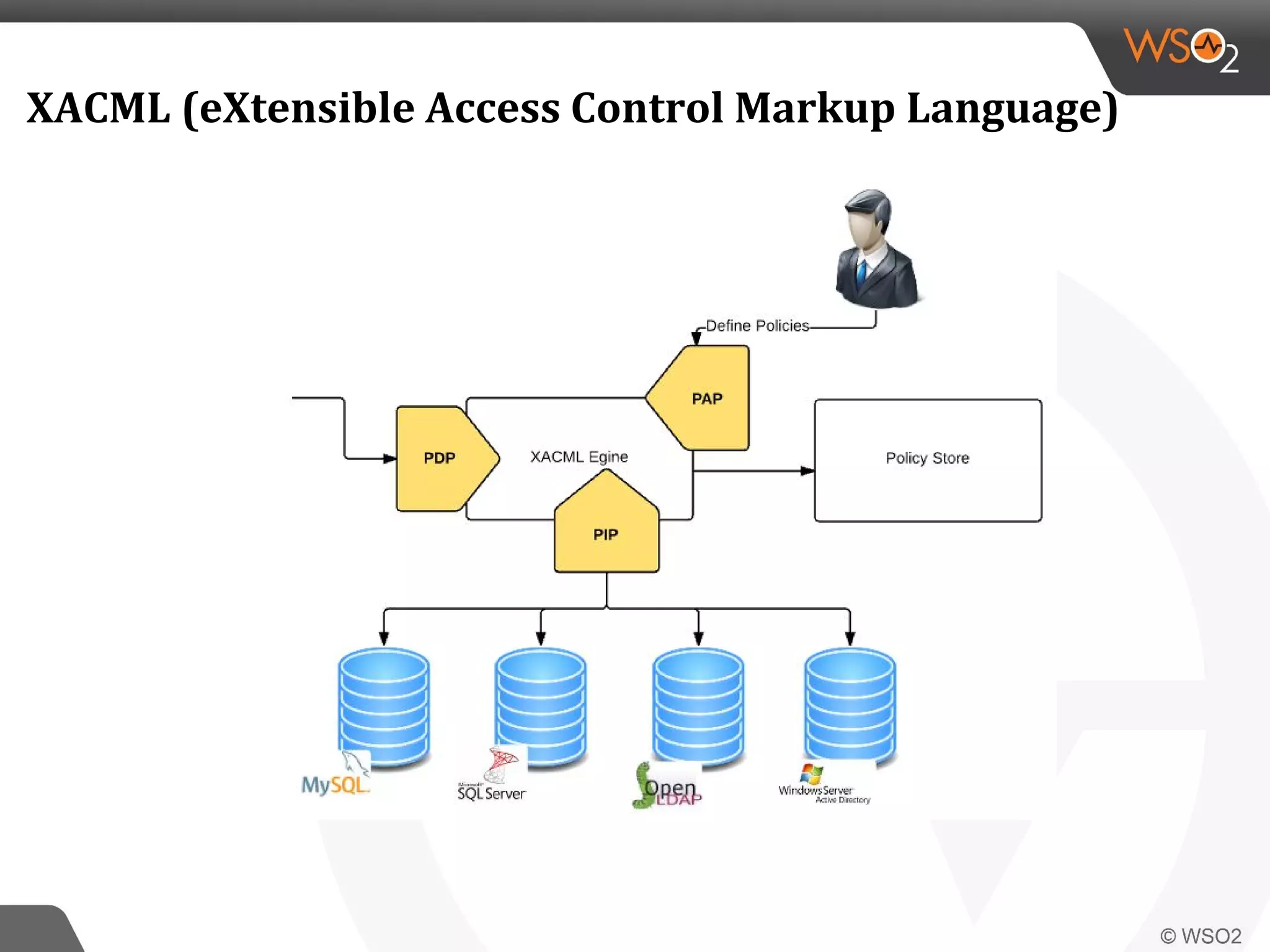
WSO2 produces open source identity and access management software. Through Google Summer of Code, WSO2 has mentored 11 projects implementing key identity standards like UMA, SAML, and OAuth. These standards, developed by organizations like OASIS and IETF, provide frameworks for identity federation, SSO, provisioning, and access control. Formats include SAML for SSO, SCIM for provisioning using REST, and XACML for fine-grained authorization control. WSO2 contributes implementations of these standards to help users manage identity and access securely across domains.