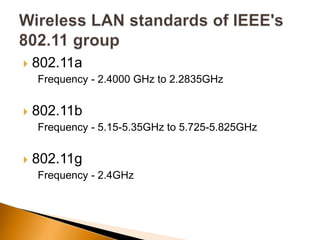
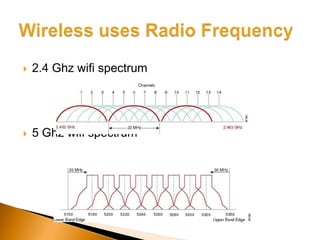
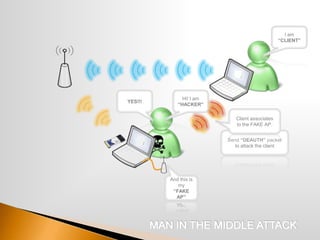
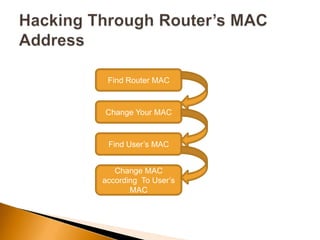
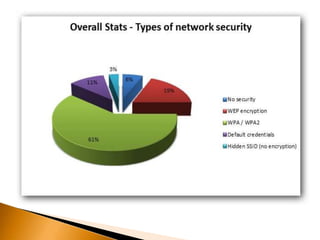
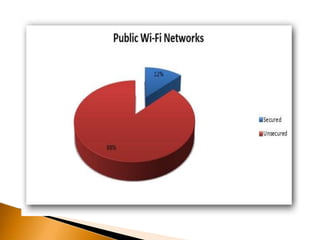
The document discusses the security challenges associated with wireless networking technology, emphasizing the importance of encryption protocols like WEP and WPA for protecting data. It outlines various methods used by hackers to breach wireless networks and provides recommendations for securing networks, such as disabling SSID broadcasting and regularly updating router settings. Although it acknowledges that no wireless network can be completely secure, it suggests practical steps to enhance security.