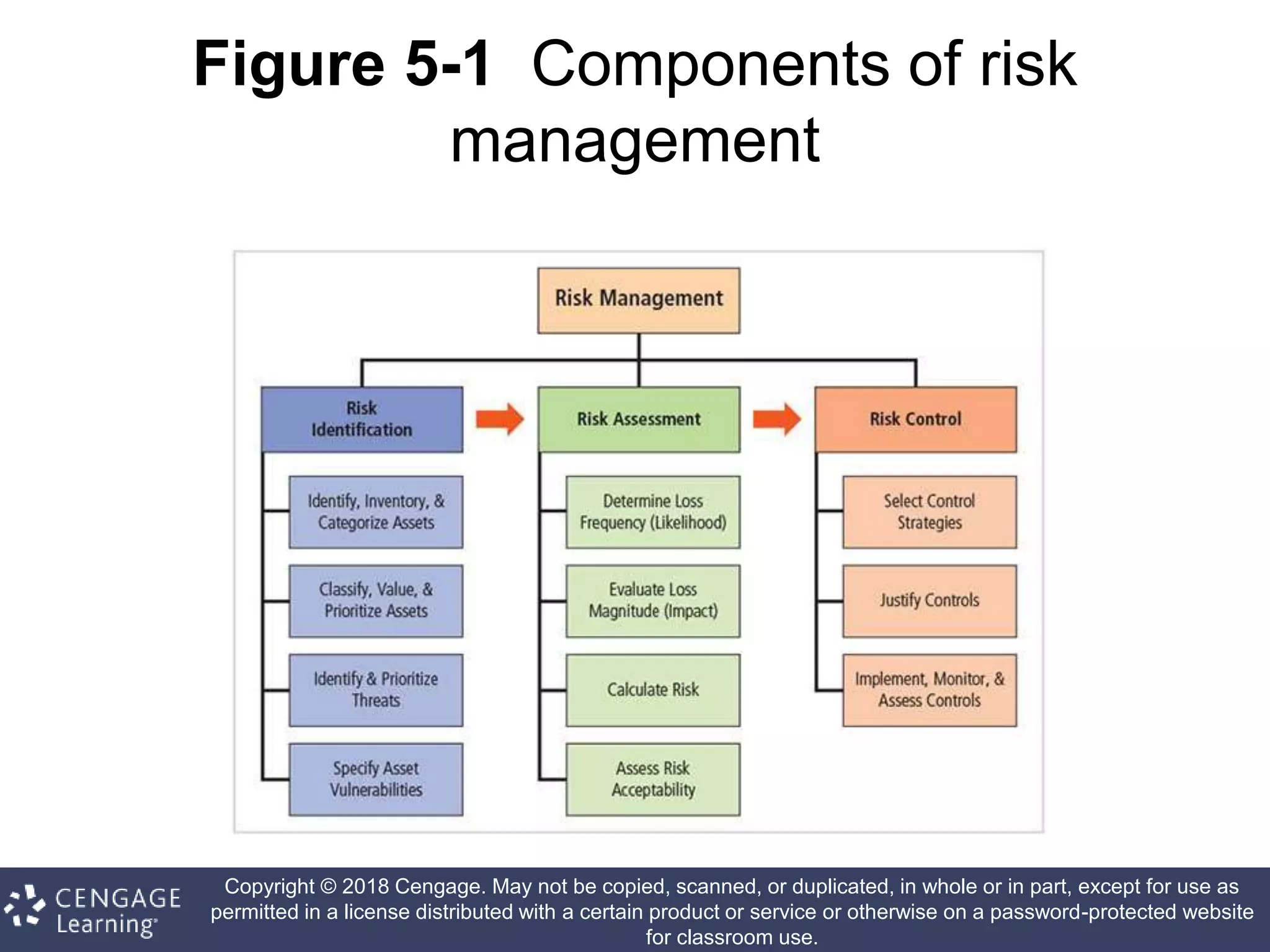
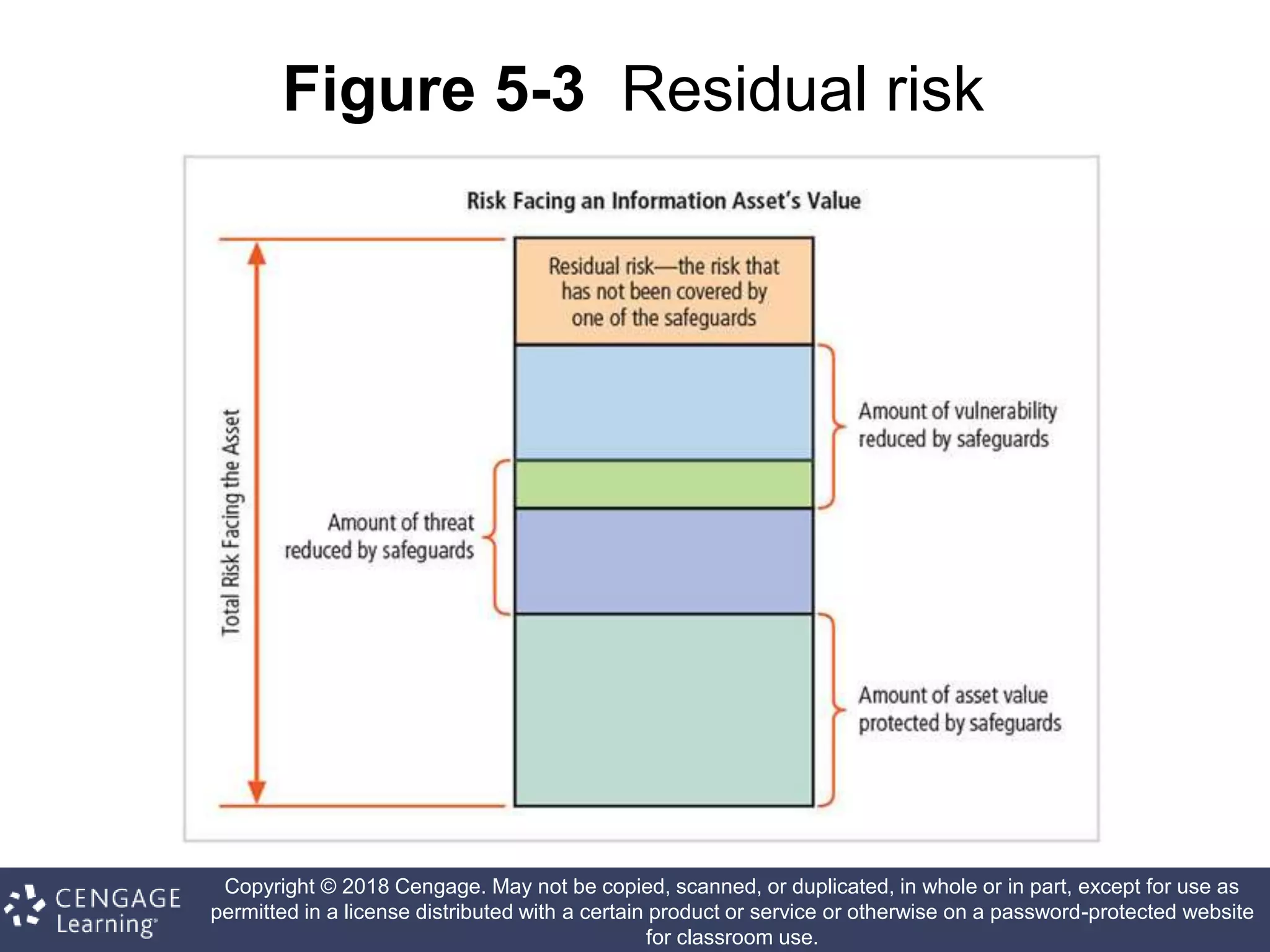
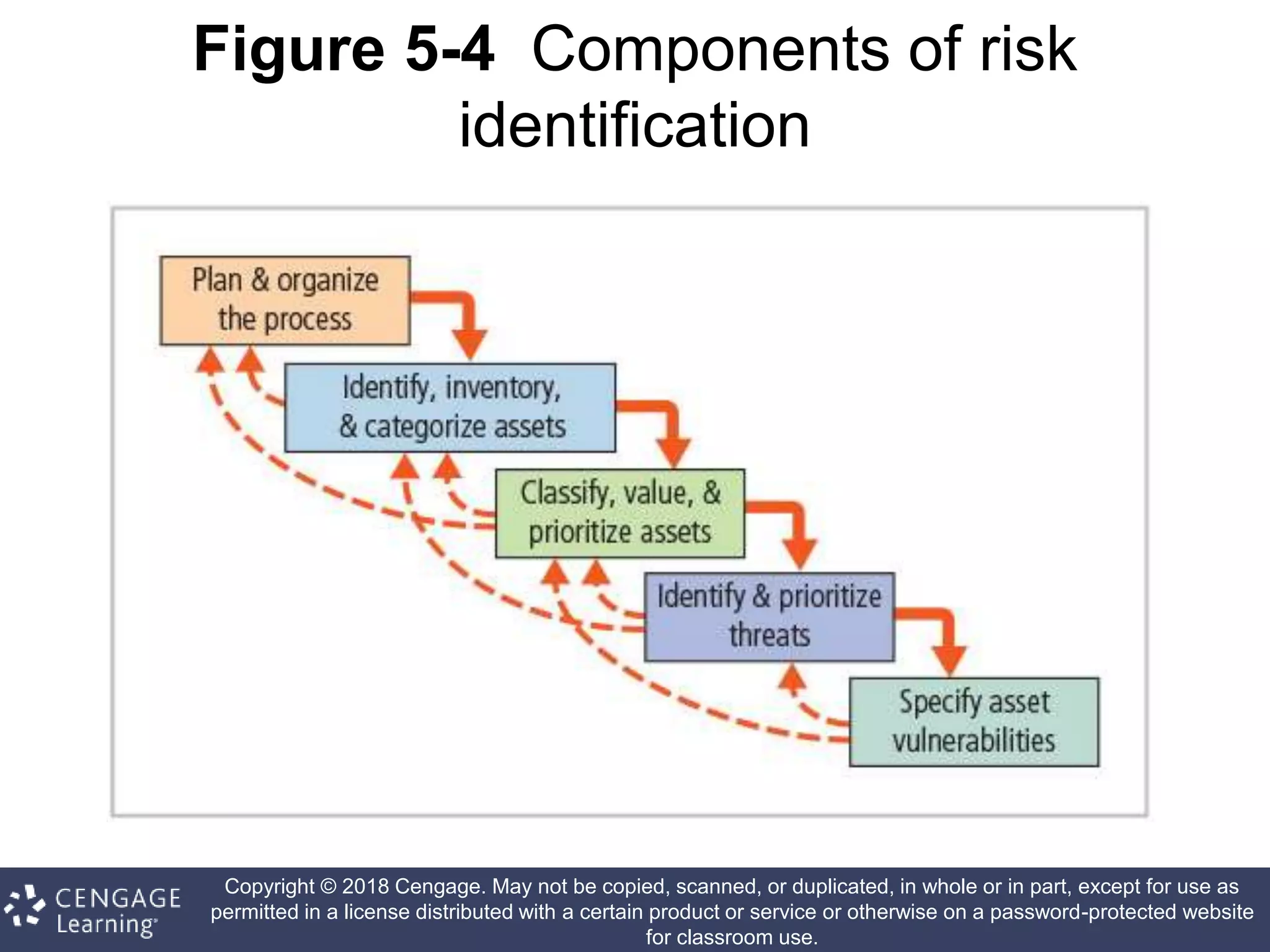
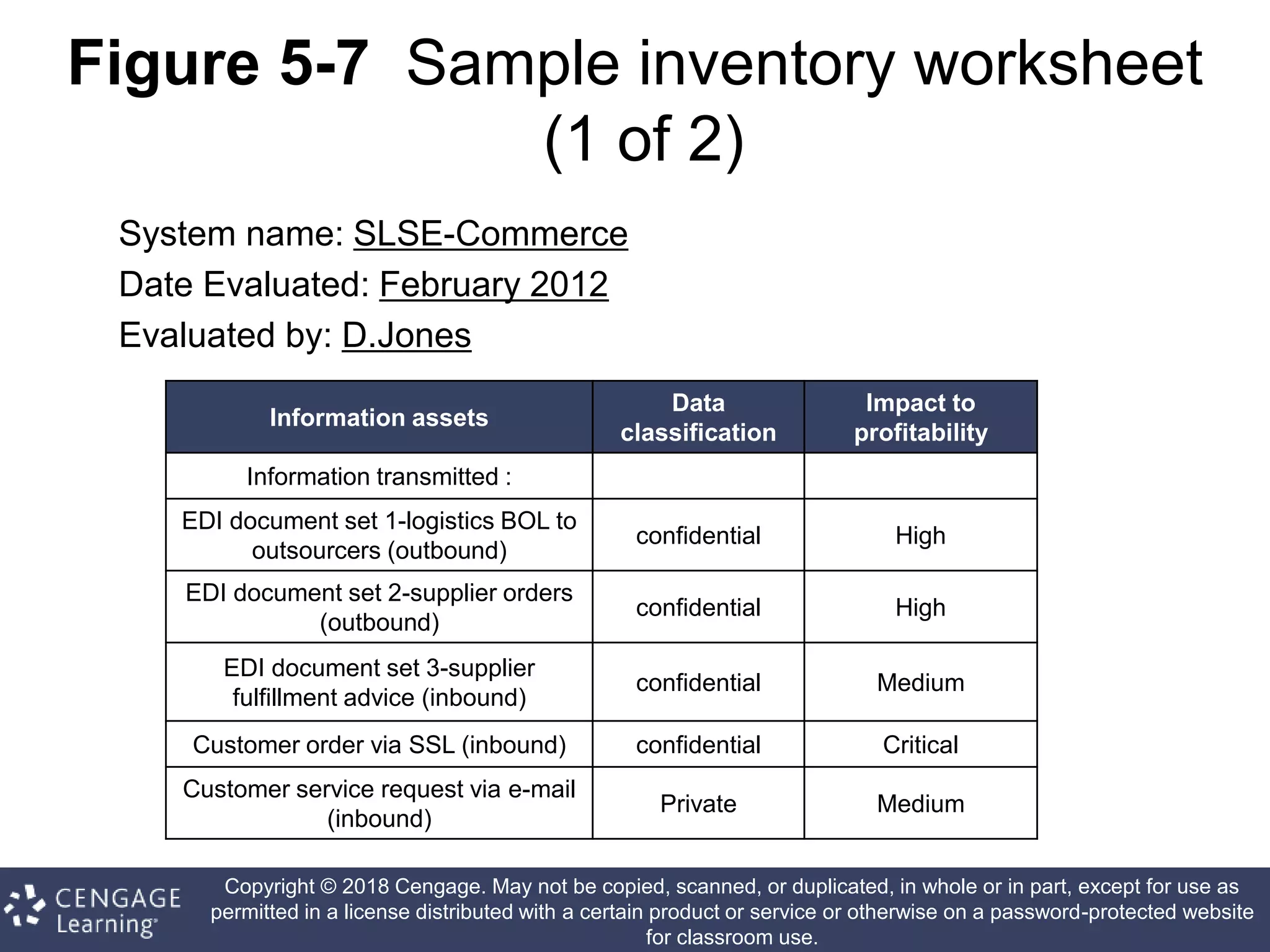
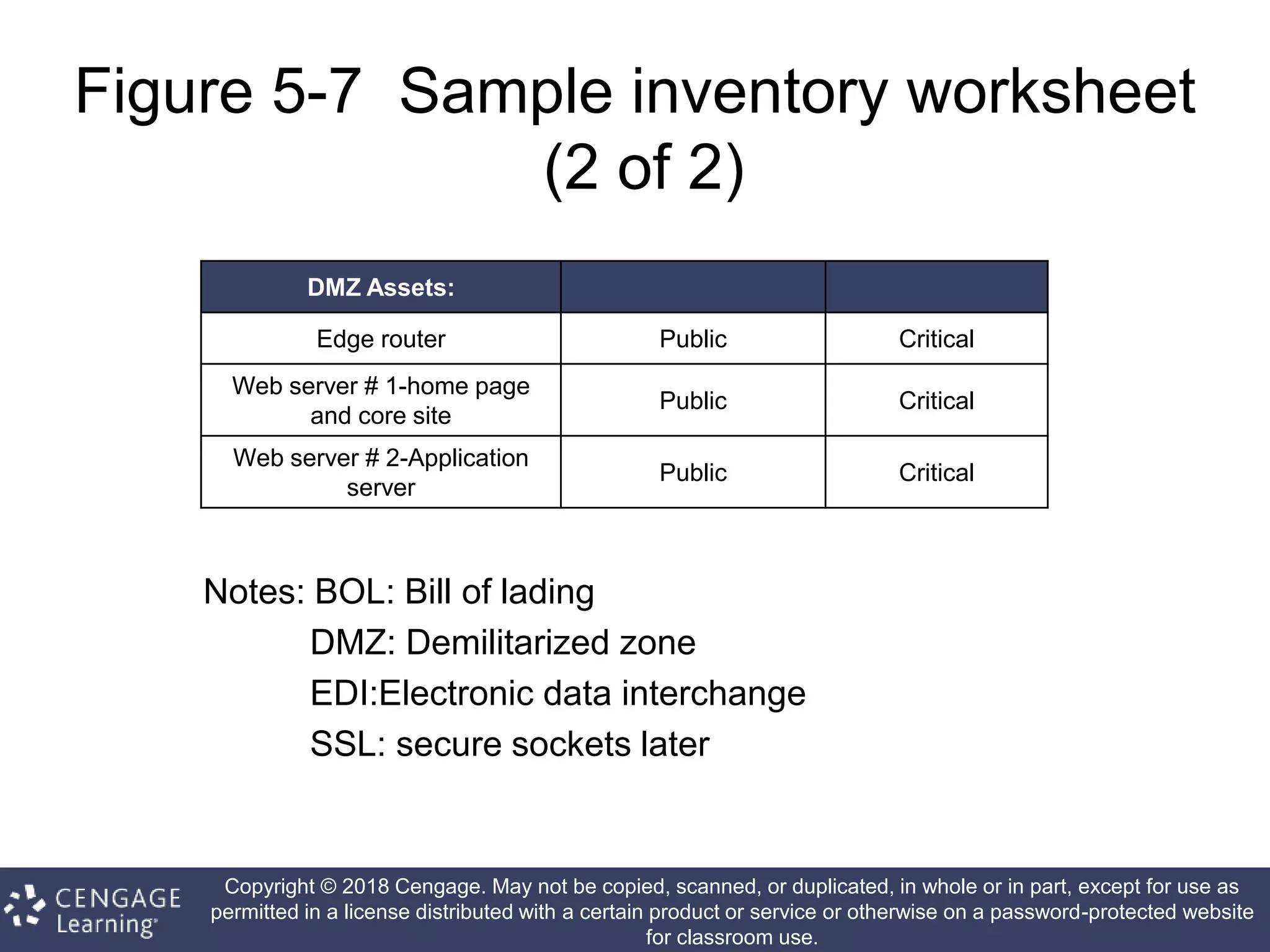
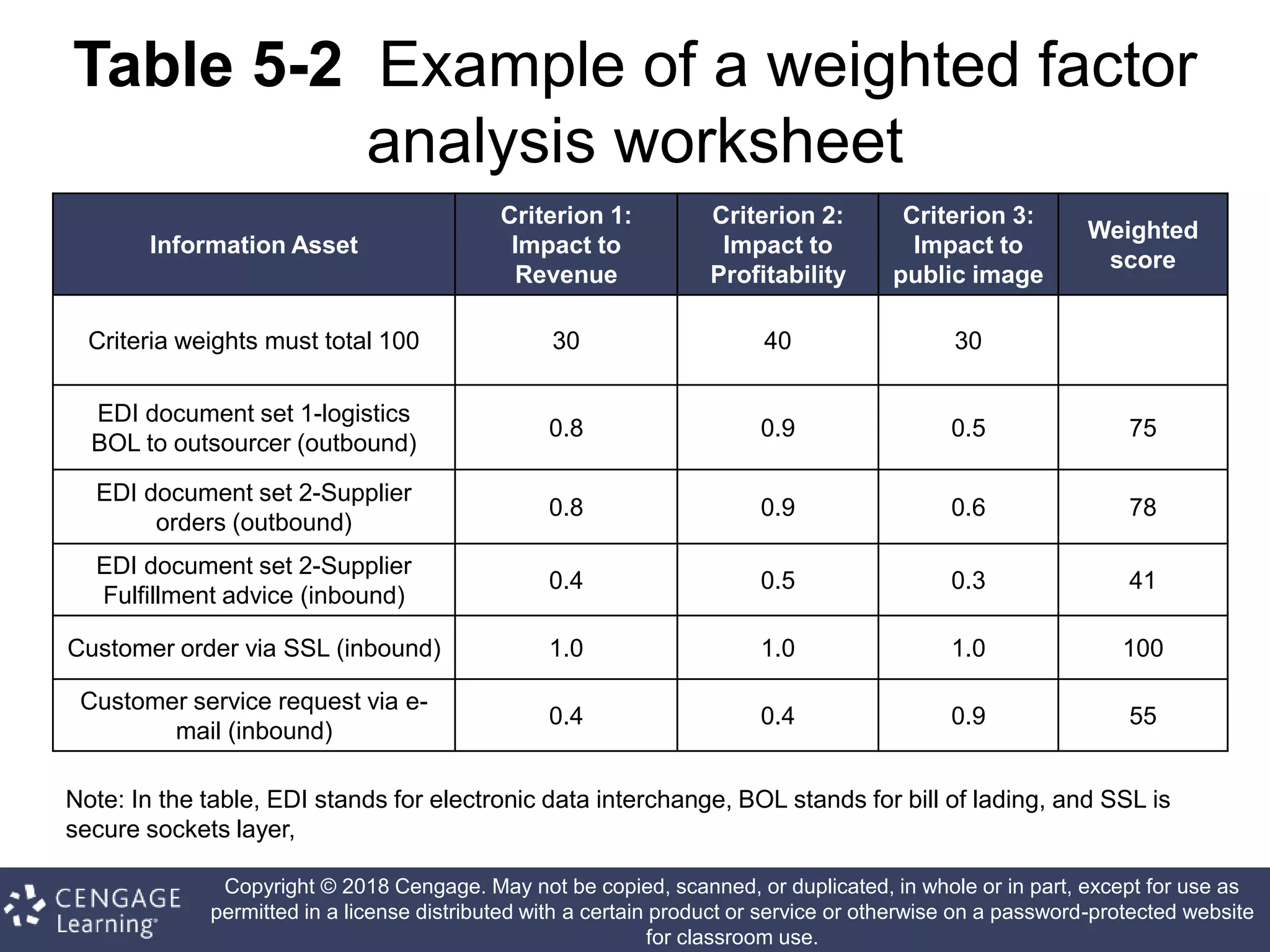
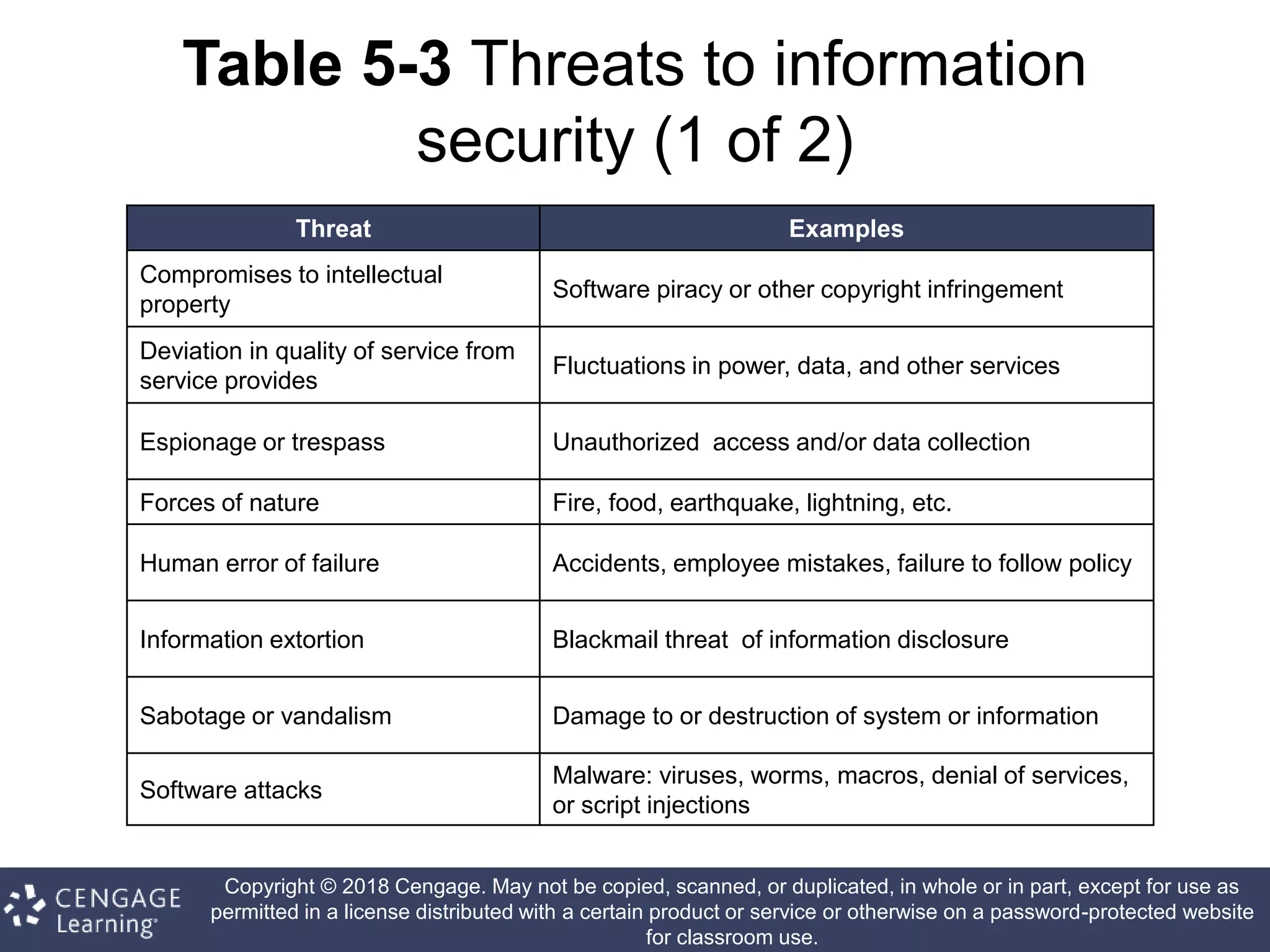
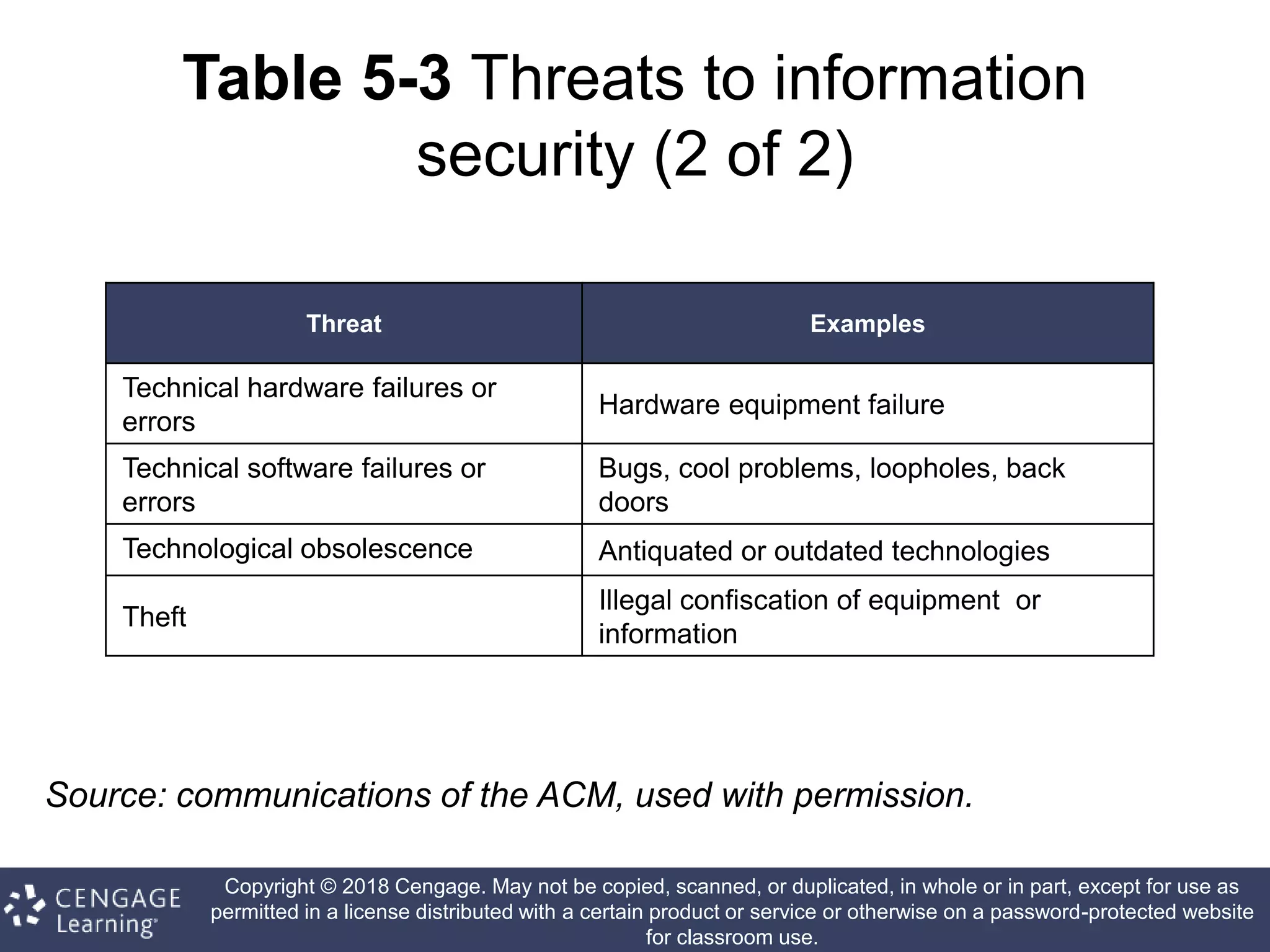
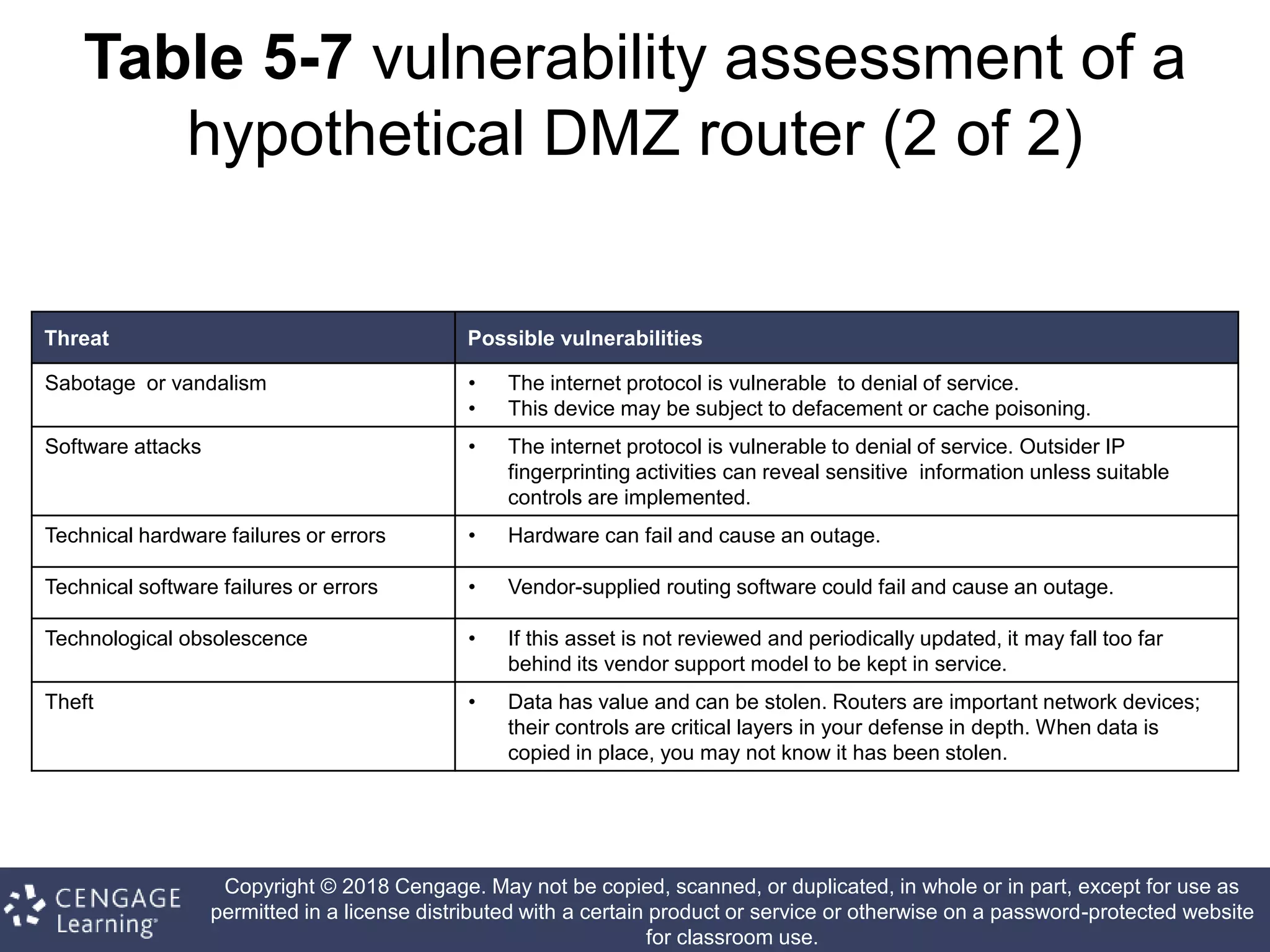
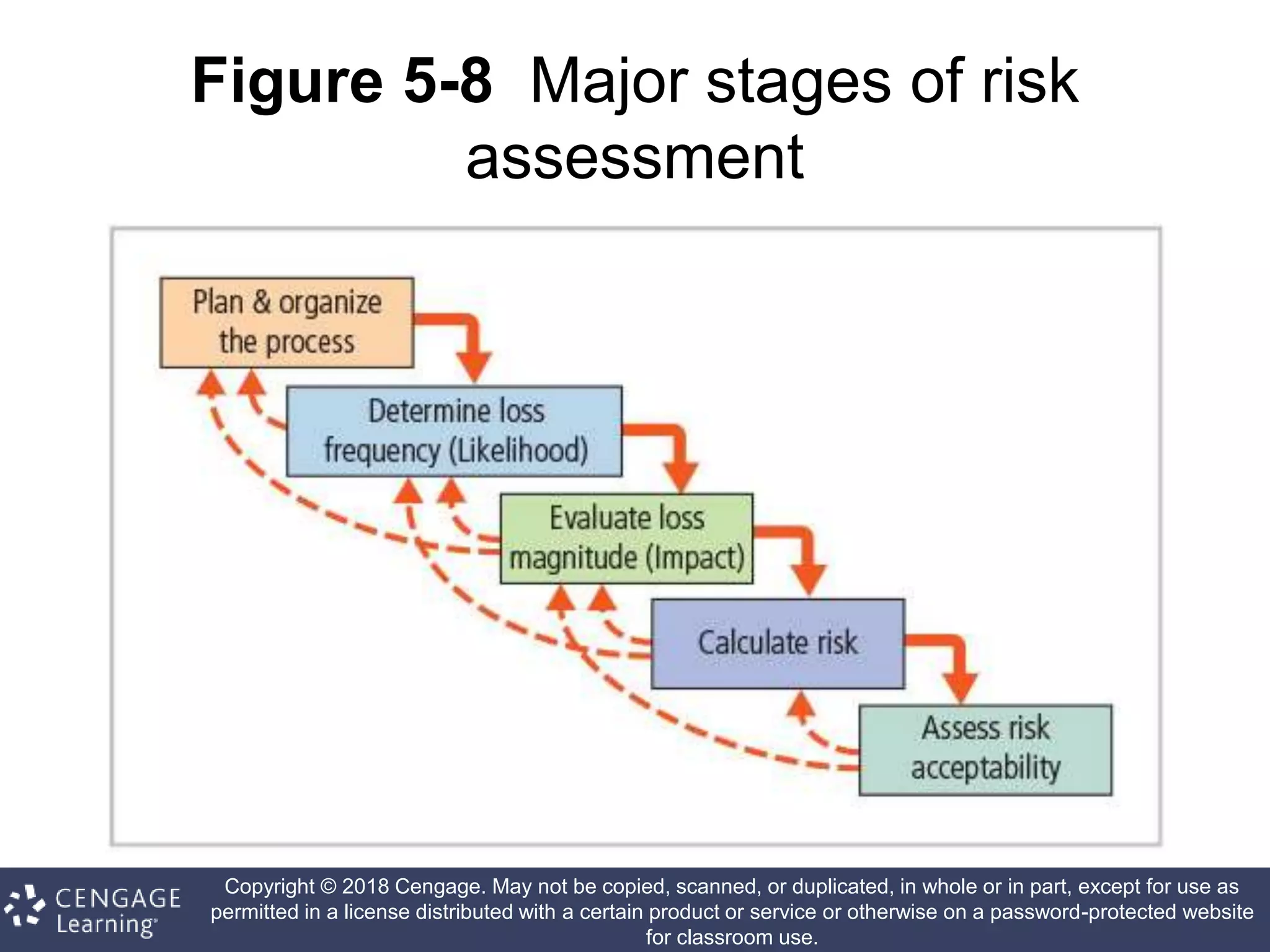
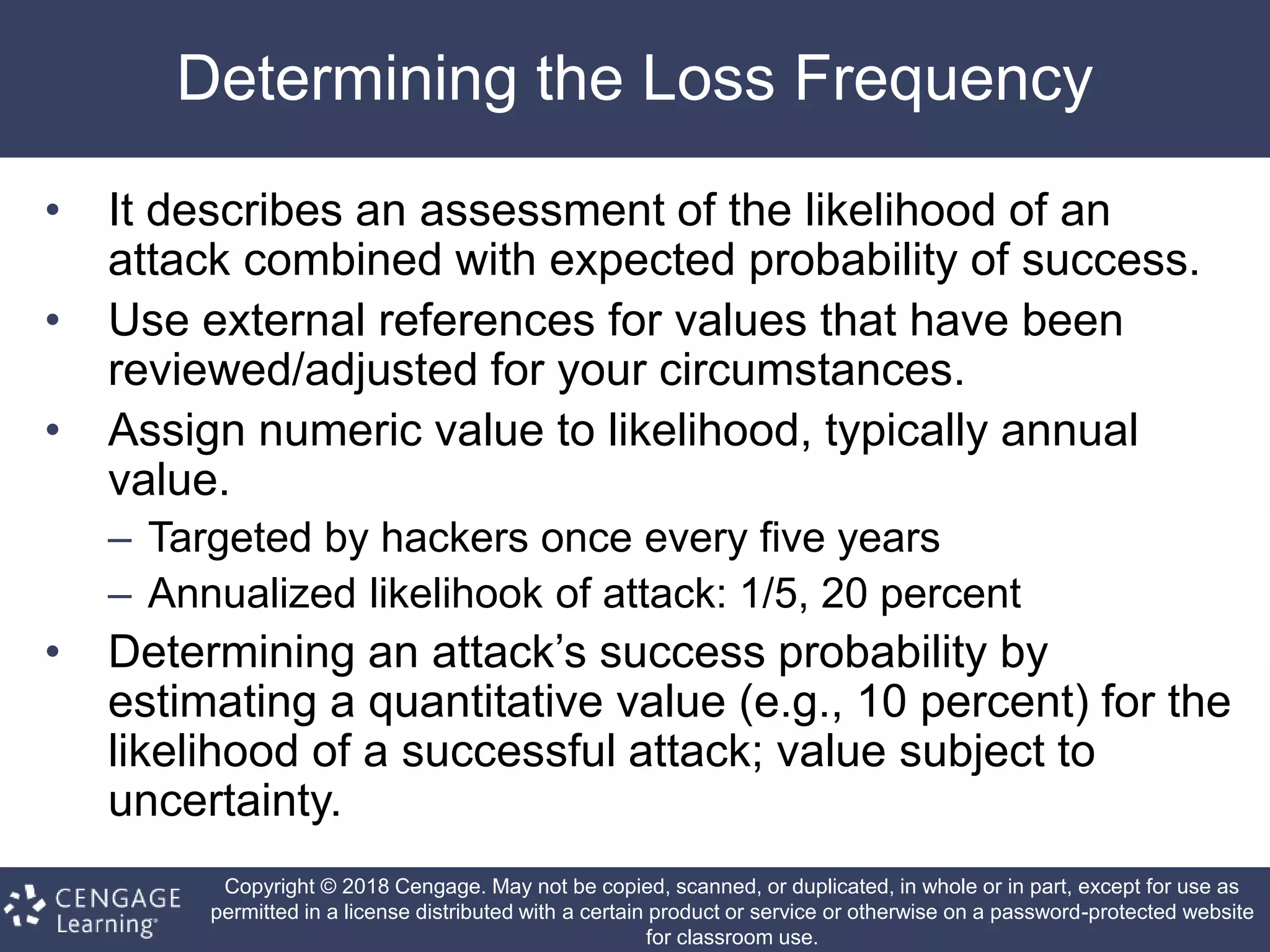
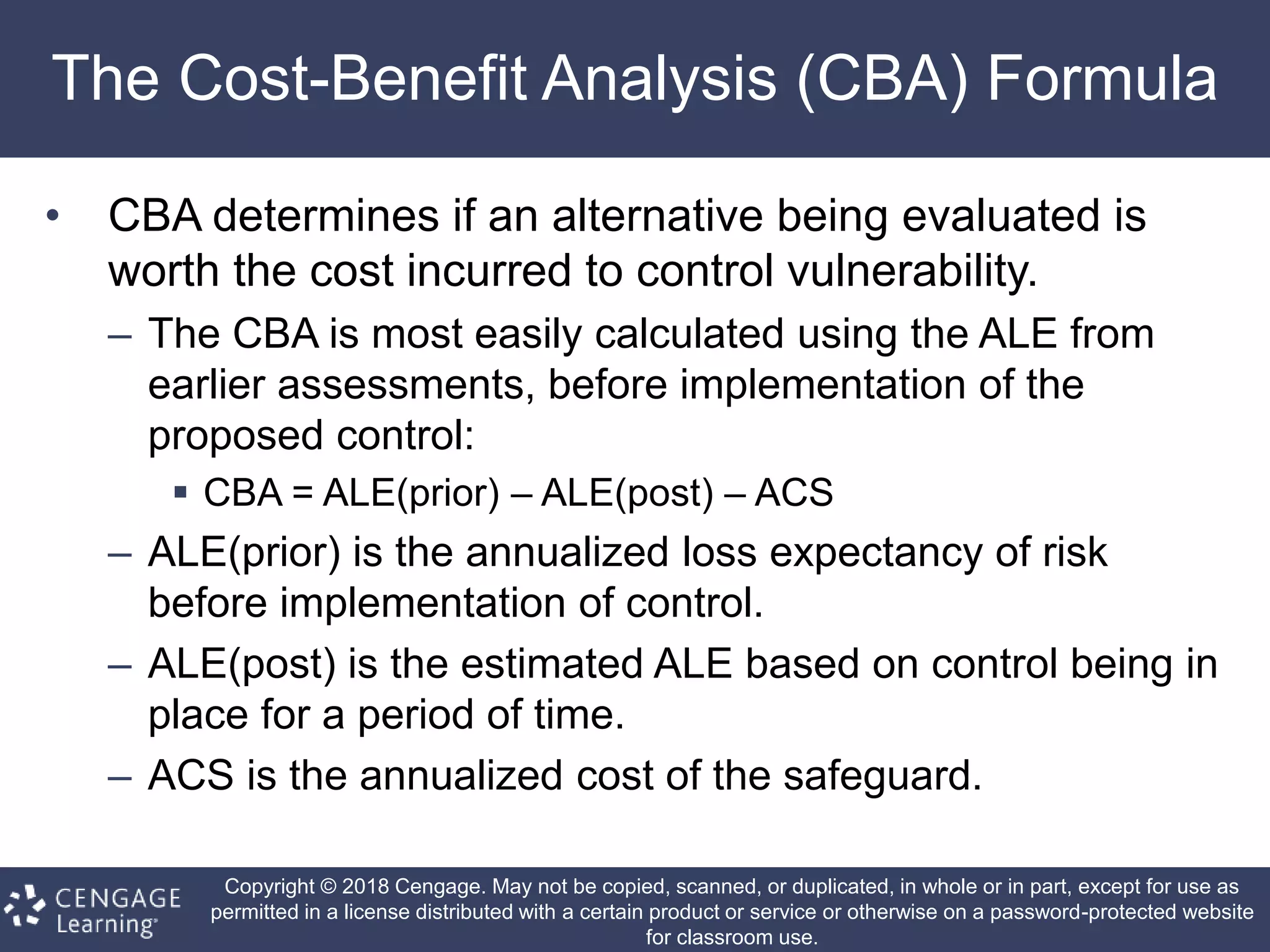
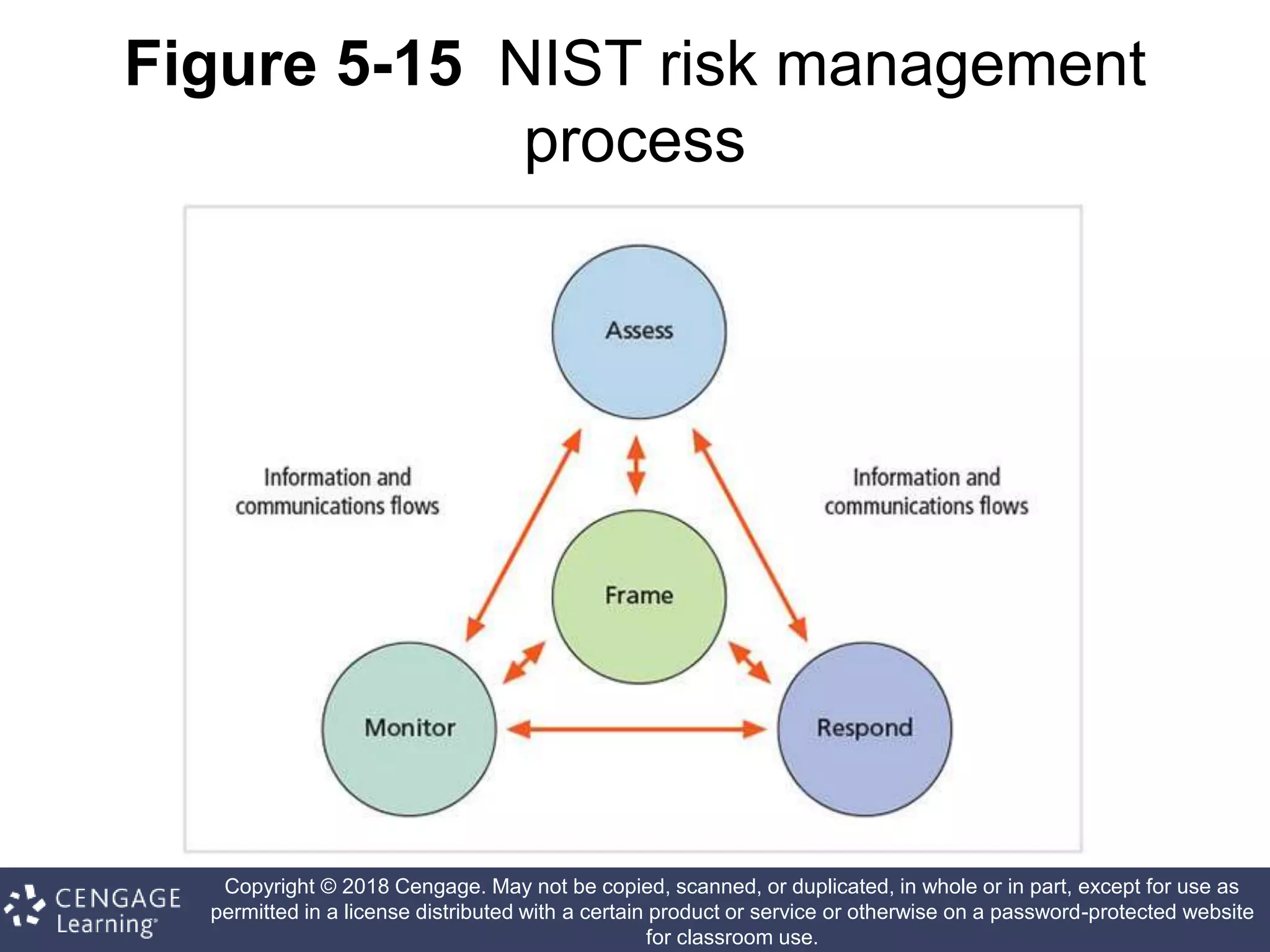
This document discusses risk management in information security. It defines key terms like risk identification, risk assessment, and risk control. It explains that risk management involves identifying risks, assessing their magnitude, and taking steps to reduce risks to an acceptable level. It also discusses how organizations identify their information assets and evaluate risks to those assets in order to implement appropriate risk controls.