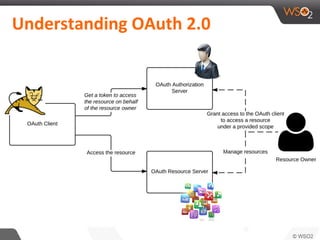
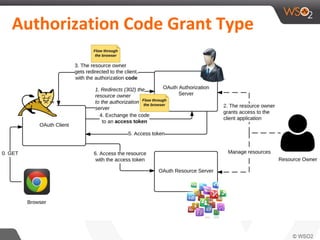
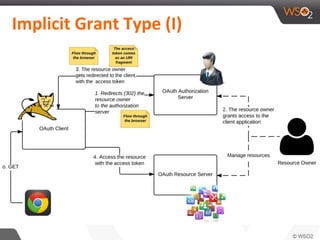
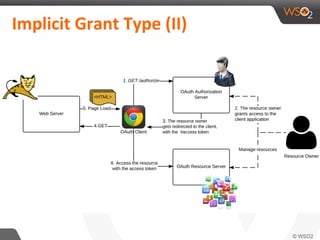
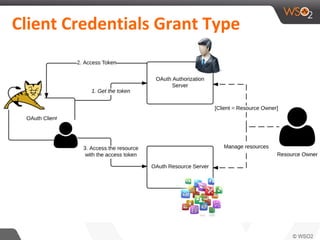
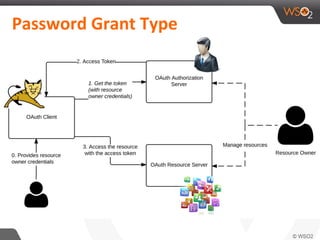
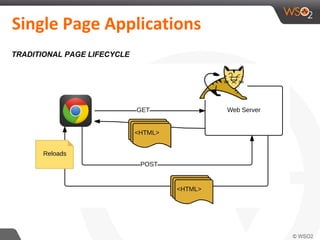
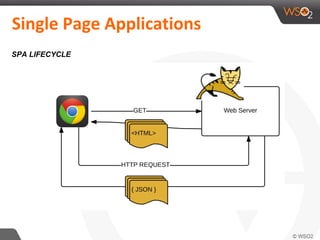
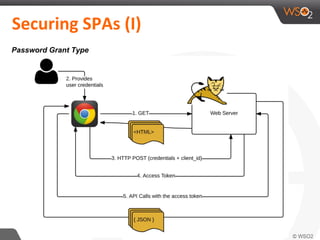
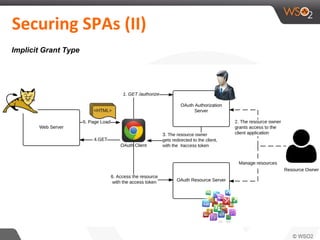
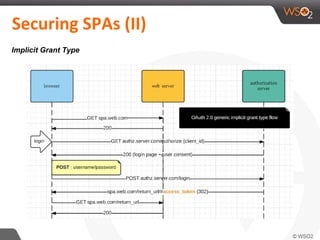
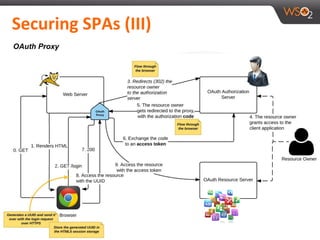
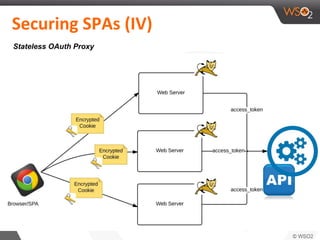
This document discusses securing single-page applications (SPAs) with OAuth 2.0. It describes how SPAs work by loading a single HTML page and dynamically updating content without page reloads. It outlines two issues with using OAuth in SPAs: client authentication and exposing access tokens to users. It proposes using the implicit grant type to address these by enabling single sign-on without exposing credentials to the SPA. It also describes using an OAuth proxy to further improve security by encrypting tokens in cookies and routing all API calls through the proxy.