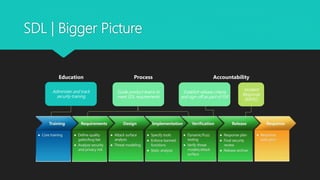
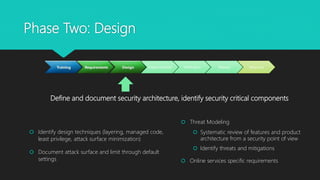
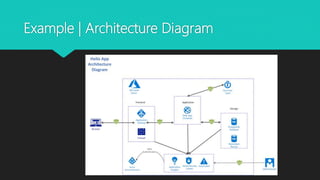
The document outlines Microsoft's Security Development Lifecycle (SDL), detailing its history, phases, and implementation practices aimed at integrating security into software development processes. Key components include threat modeling, security training, and the establishment of design, implementation, and verification protocols to ensure secure software releases. Resources and tools for SDL and threat modeling are provided to support developers and teams in improving security measures.