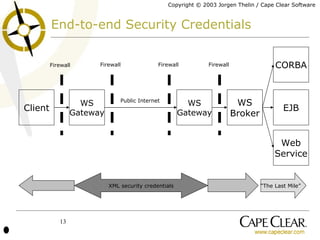
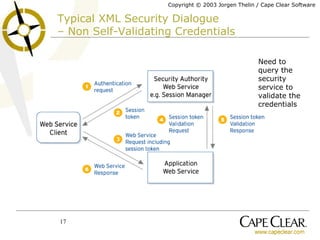
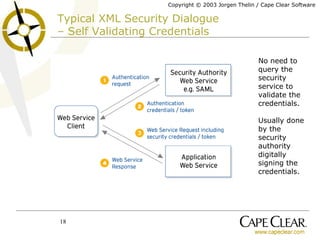
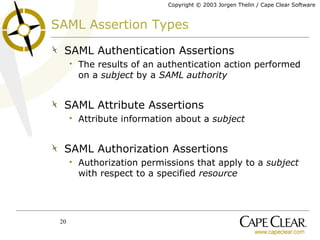
The document discusses the importance of identity, security, and XML web services for enterprise applications, emphasizing the role of security credentials and standards like SAML. It outlines how web service implementations must be identity-aware to manage authentication and authorization effectively, while also highlighting the need for standardized interfaces and interoperability within security frameworks. The piece concludes that while progress has been made in standardization, true interoperability in web services security remains a work in progress.




![A Definition of Identity Definition from Cambridge Dictionaries Online: Identity [ noun ] Who a person is, or the qualities of a person or group which make them different from others http://dictionary.cambridge.org/define.asp?key=identity*1+0](https://image.slidesharecdn.com/wsidentity-1227239137870017-8/85/Identity-Security-and-XML-Web-Services-5-320.jpg)