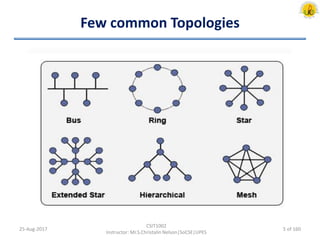
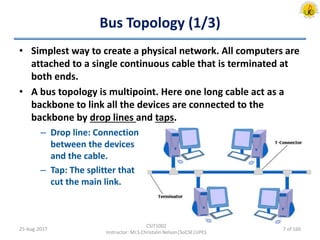
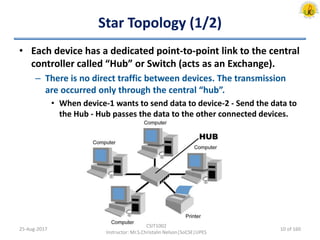
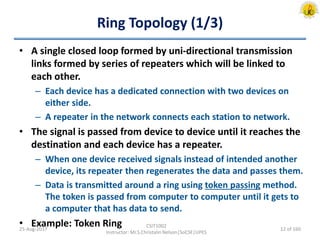
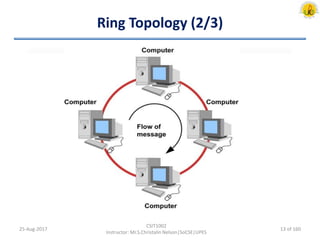
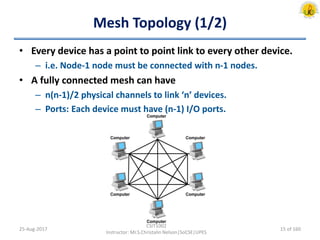
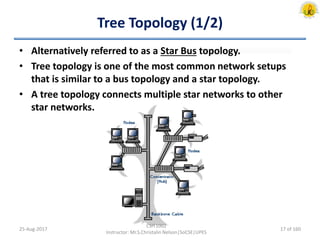
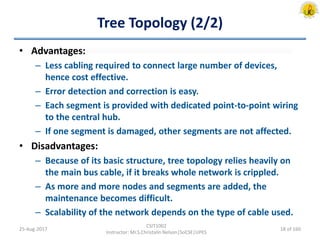
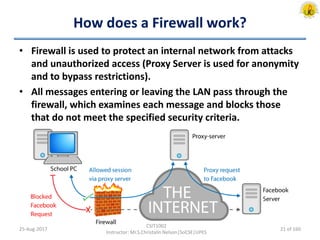
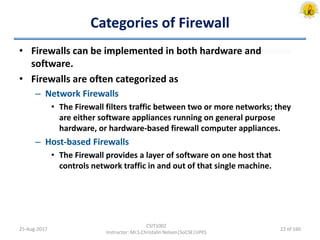
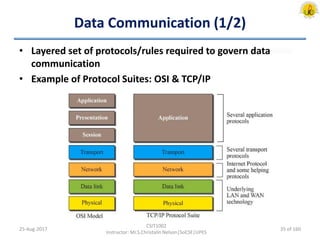
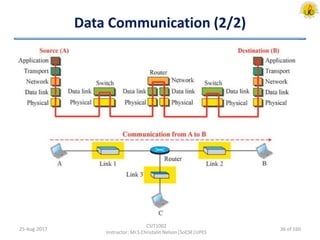
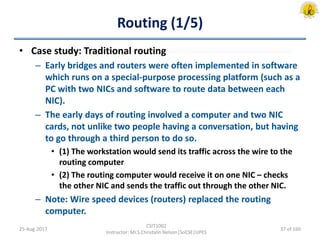
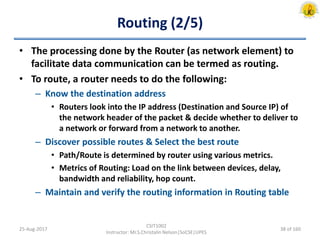
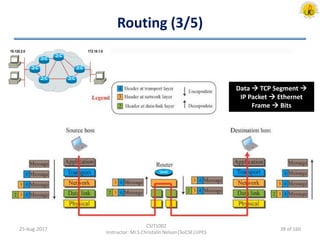
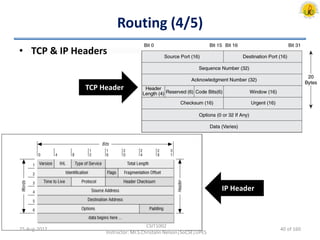
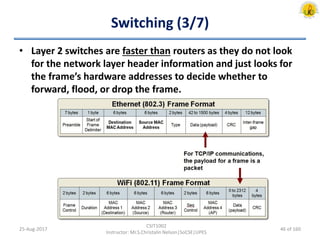
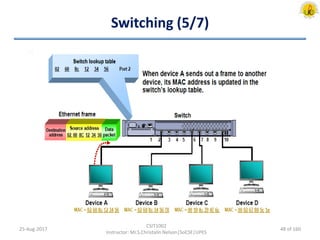
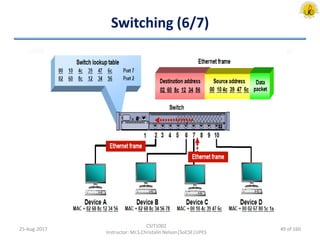
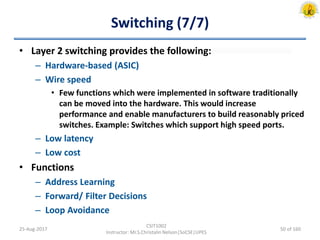
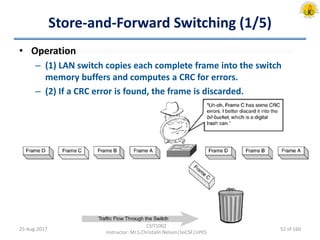
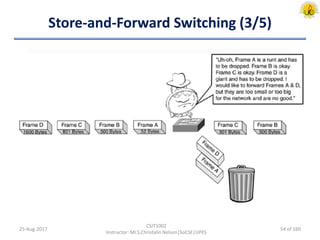
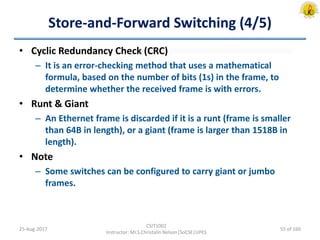
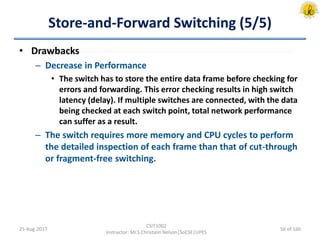
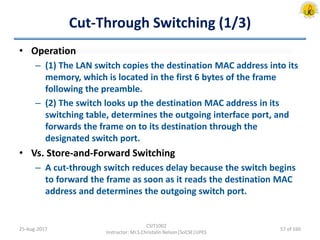
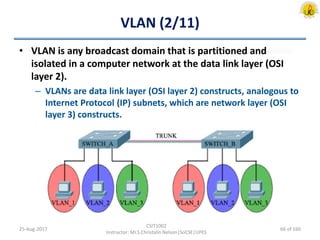
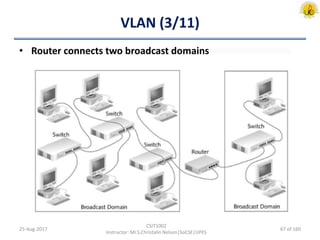
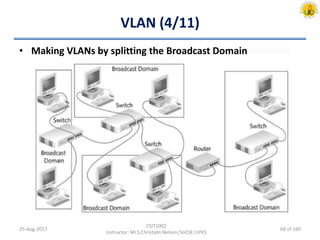
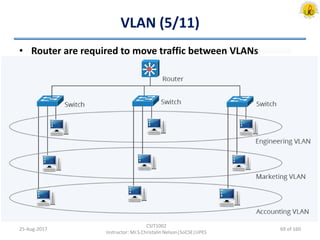
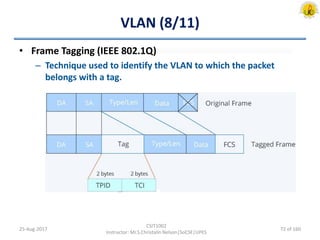
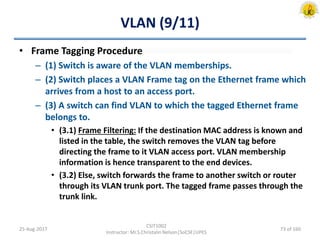
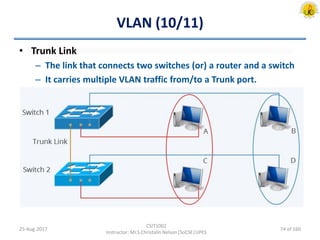
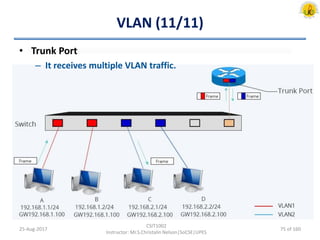
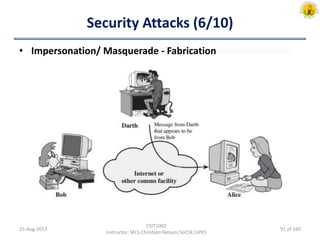
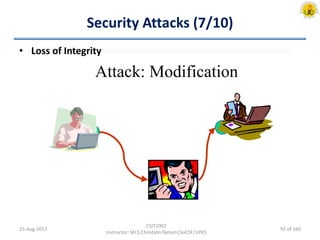
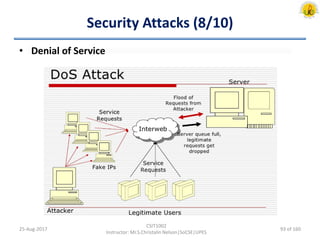
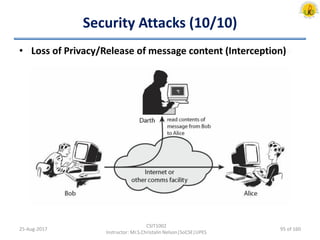
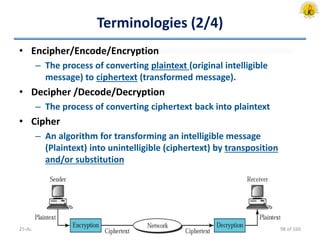
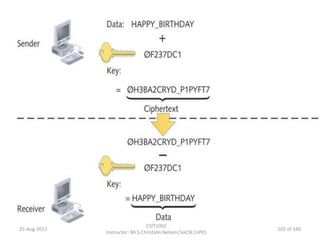
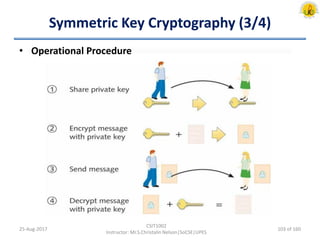
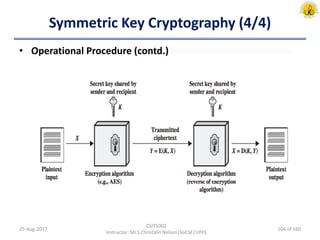
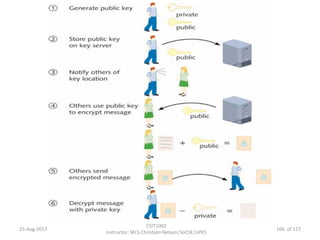
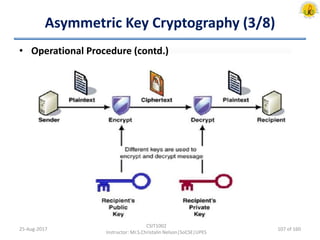
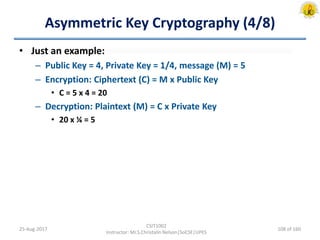
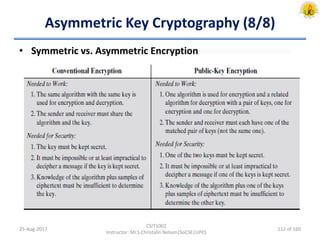
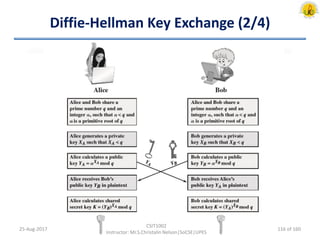
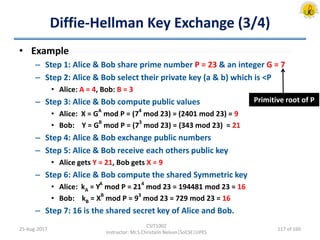
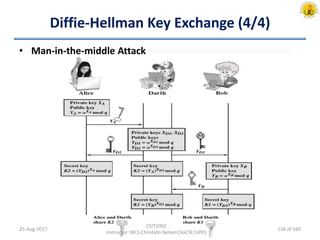
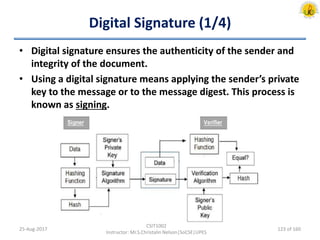
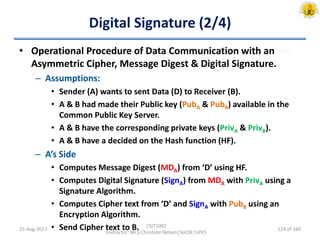
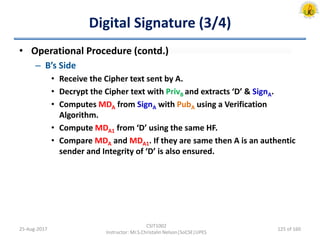
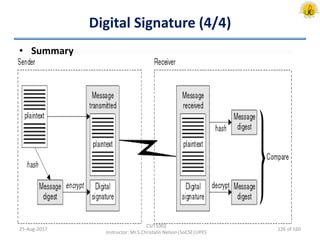
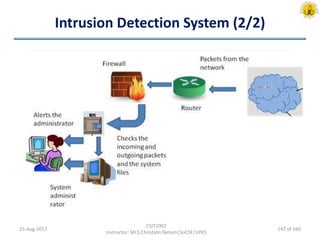
The document outlines an overview of network and security concepts, detailing various network topologies such as bus, star, ring, mesh, and tree, along with their advantages and disadvantages. It also discusses the function and types of firewalls, including packet filter firewalls, stateful firewalls, application layer firewalls, and proxy firewalls, which protect networks from intrusions by filtering traffic based on defined rules. Additionally, it describes security zones like the internet, intranet, DMZ, production network, and management network, highlighting their roles in controlling access and securing data communication.