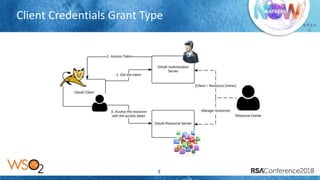
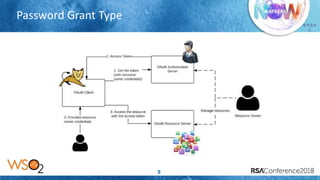
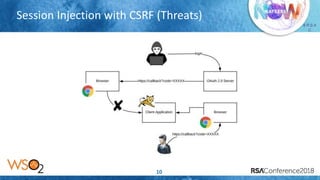
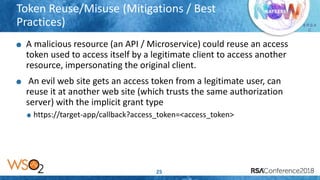
The document discusses OAuth 2.0 security threats including session injection with CSRF, token leakage, token reuse/misuse, and token export. It provides details on the threats, victims, and best practices for mitigation. These include using short-lived authorization codes, TLS, proof-key-for-code-exchange, limiting grant types by client, white-listing redirect URIs, token binding, and enforcing throttle limits to prevent token misuse. The presentation encourages attendees to review their OAuth 2.0 implementations against these threats and ensure authorization servers follow security best practices.