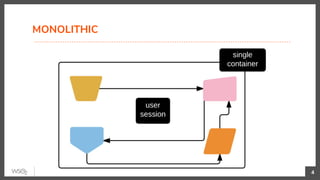
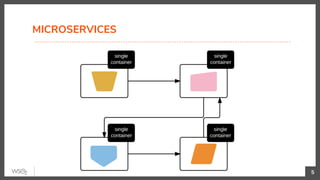
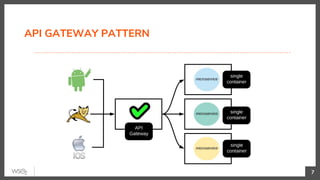
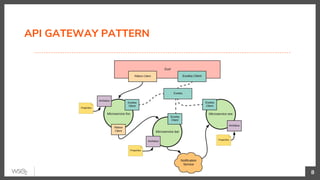
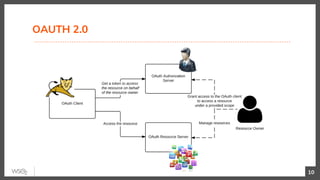
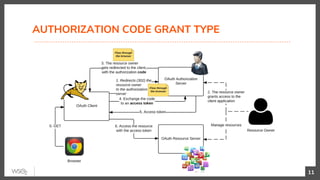
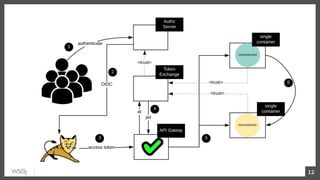
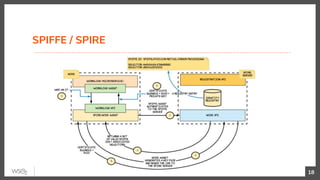
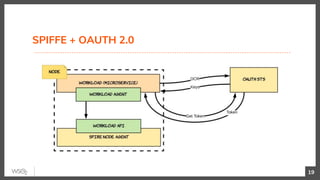
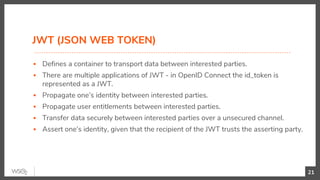
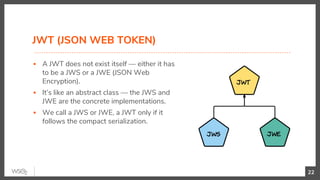
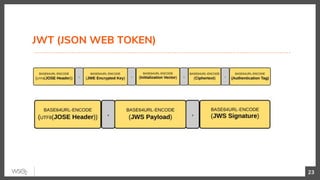
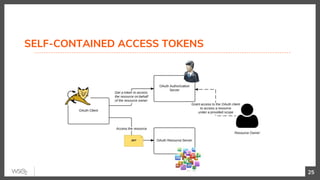
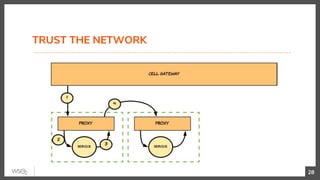
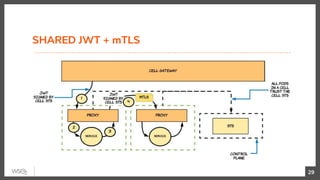
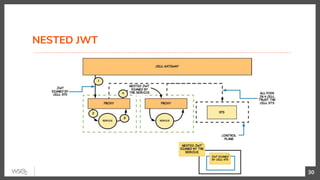
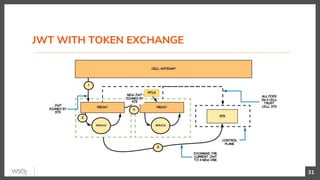
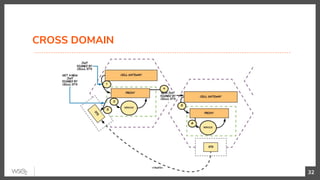
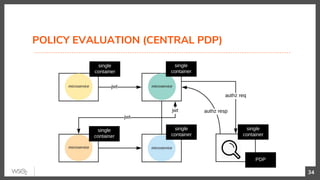
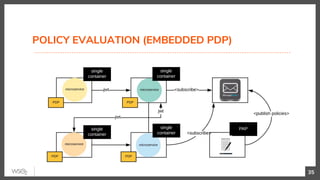
This document discusses security in microservices architectures. It begins by comparing monolithic and microservices approaches. It then covers edge security using API gateways and OAuth 2.0 authorization. Other topics include service-to-service security using TLS mutual authentication, JSON Web Tokens (JWTs), and SPIFFE/SPIRE for identity management. Patterns like JWTs, nested JWTs, and token exchange are presented for secure communication between services. The document also discusses access control and policy evaluation using approaches like embedded policy decision points and the Open Policy Agent (OPA) framework.