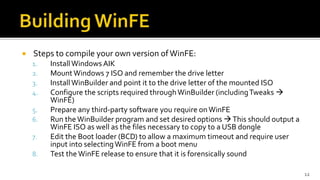
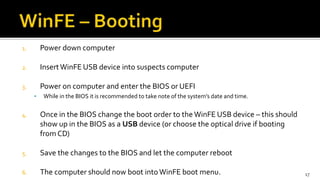
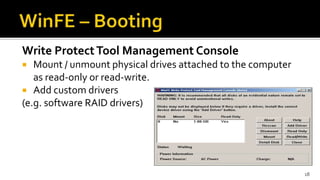
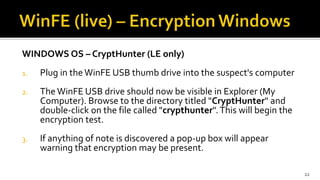
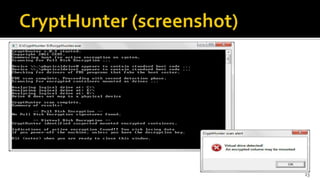
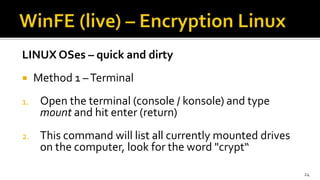
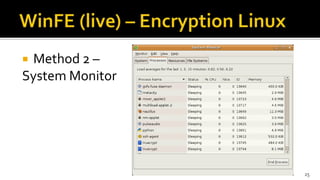
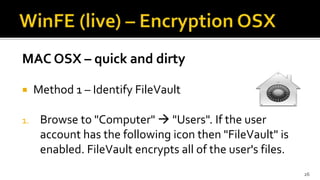
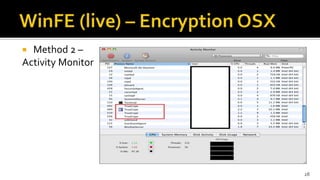
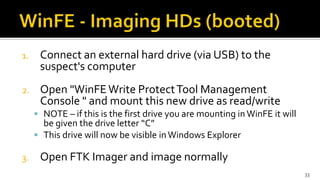
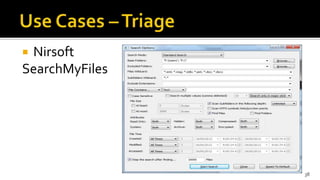
The document discusses the benefits and process of building WinFE, a Windows forensic environment that can be run from RAM or a USB drive. Key points include that WinFE allows booting on x86 devices regardless of operating system, runs Windows compatible tools, and is highly customizable. The document provides detailed instructions on compiling WinFE using the Windows AIK and WinBuilder utility, including how to add drivers, copy files to USB, and use various forensic tools for encryption detection, imaging RAM and drives, and triage.