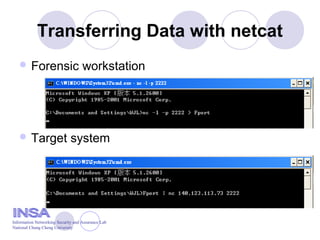
This document discusses techniques for collecting volatile data and performing a live response investigation on a Windows system. It provides a list of tools to create a response toolkit and obtain information such as running processes, open ports, logged on users, and network connections. The document recommends using these tools to review the event logs and registry for evidence, obtain passwords from the SAM database, and dump system memory for a more in-depth investigation.