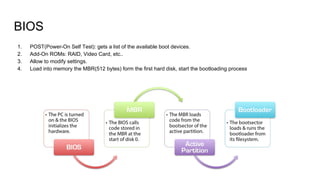
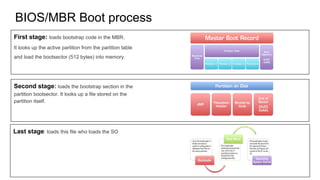
BIOS and UEFI are types of firmware that control the boot process. BIOS uses the MBR partition table and boots by loading the MBR, then the partition bootsector. UEFI uses the GPT partition table and ESP partition, and its boot manager loads UEFI drivers and bootloaders. Secure Boot is an UEFI extension that verifies signatures of boot components for security.




![UEFI BOOT MANAGER
[root@system directory]# efibootmgr -v
BootCurrent: 0002
Timeout: 3 seconds
BootOrder: 0003,0002,0000,0004
Boot0000* CD/DVD Drive BIOS(3,0,00)
Boot0001* Hard Drive HD(2,0,00)
Boot0002* Fedora HD(1,800,61800,6d98f360-cb3e-4727-8fed-5ce0c040365d)File(EFIfedoragrubx64.efi)
Boot0003* opensuse HD(1,800,61800,6d98f360-cb3e-4727-8fed-5ce0c040365d)File(EFIopensusegrubx64.efi)
Boot0004* Hard Drive BIOS(2,0,00)P0: ST1500DM003-9YN16G
Disk boot targets can be defined but also non-disk targets as PXE server.
Disk boot targets:
● BIOS compatibility boot entries: 0000,0004. Autogenerated by the firmware.
● “Fall backpath” native UEFI entries: 0001. The firmware will look through each ESP partition in the
disk, in the order they exist, and look for EFIBOOTBOOT{machine type short-name}.EFI: BOOT64.EFI
(x86-64)BOOTIA32.EFI (x86-32)](https://image.slidesharecdn.com/bootprocess-161213173259/85/Boot-process-BIOS-vs-UEFI-7-320.jpg)


