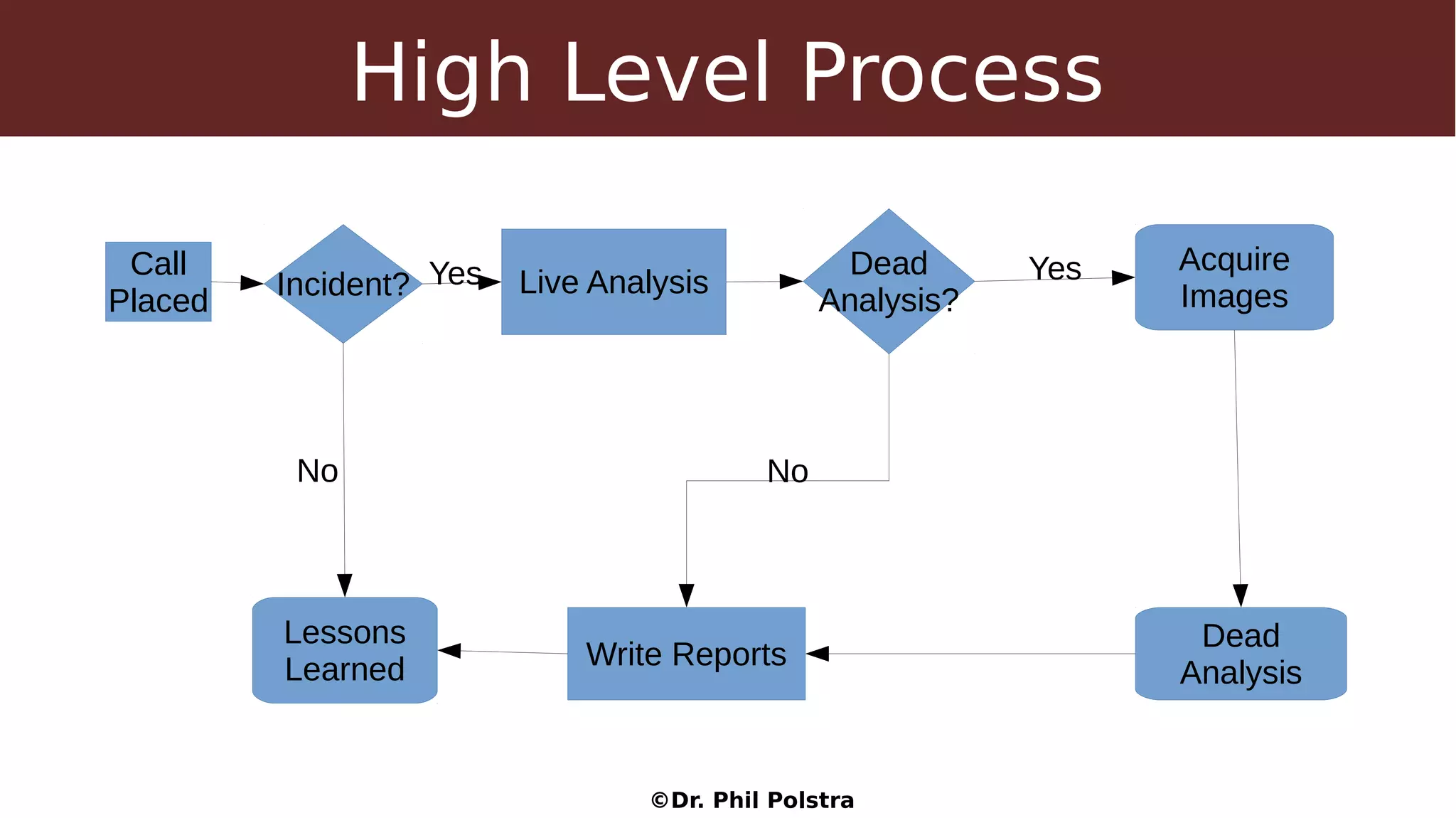
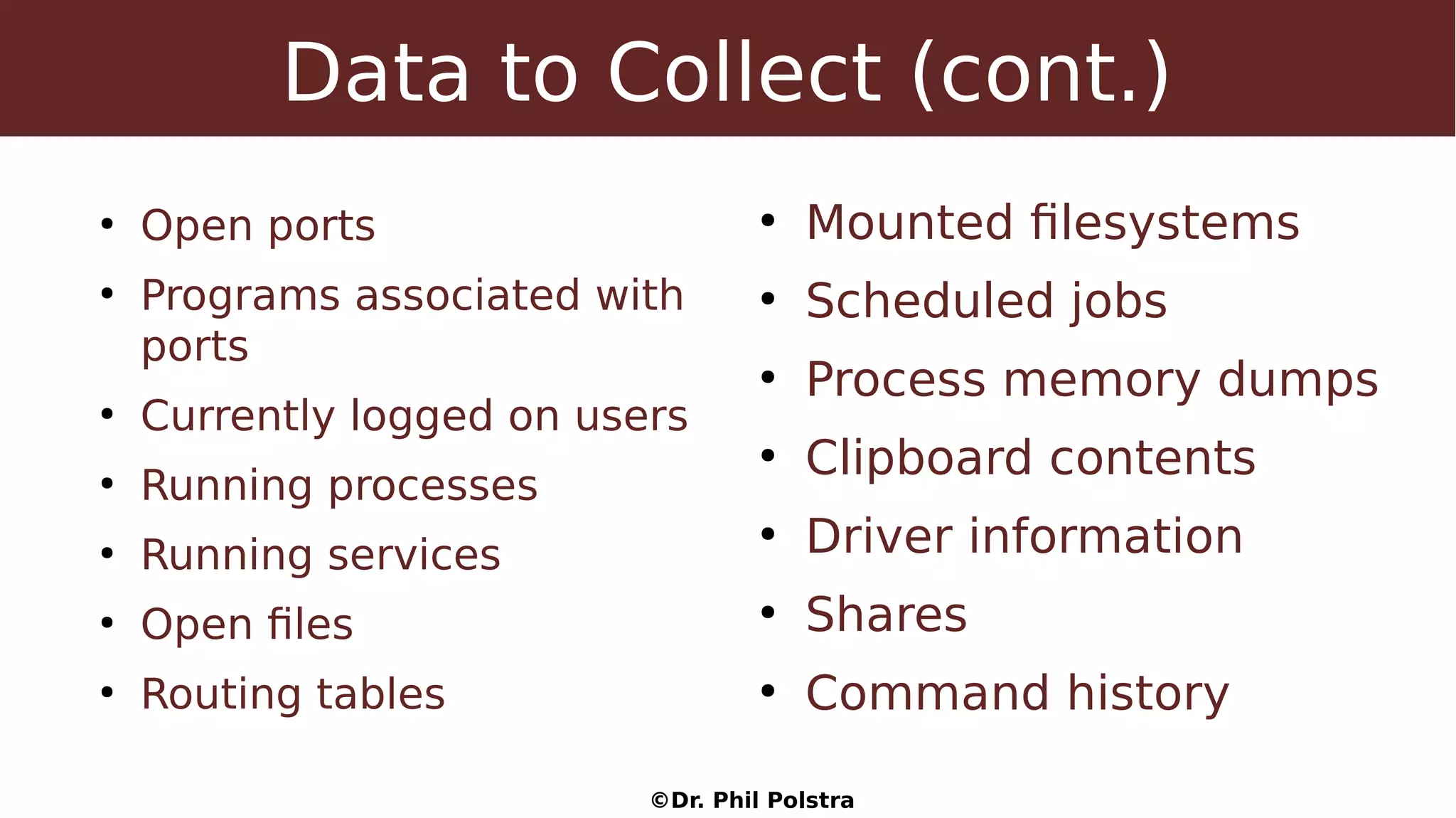
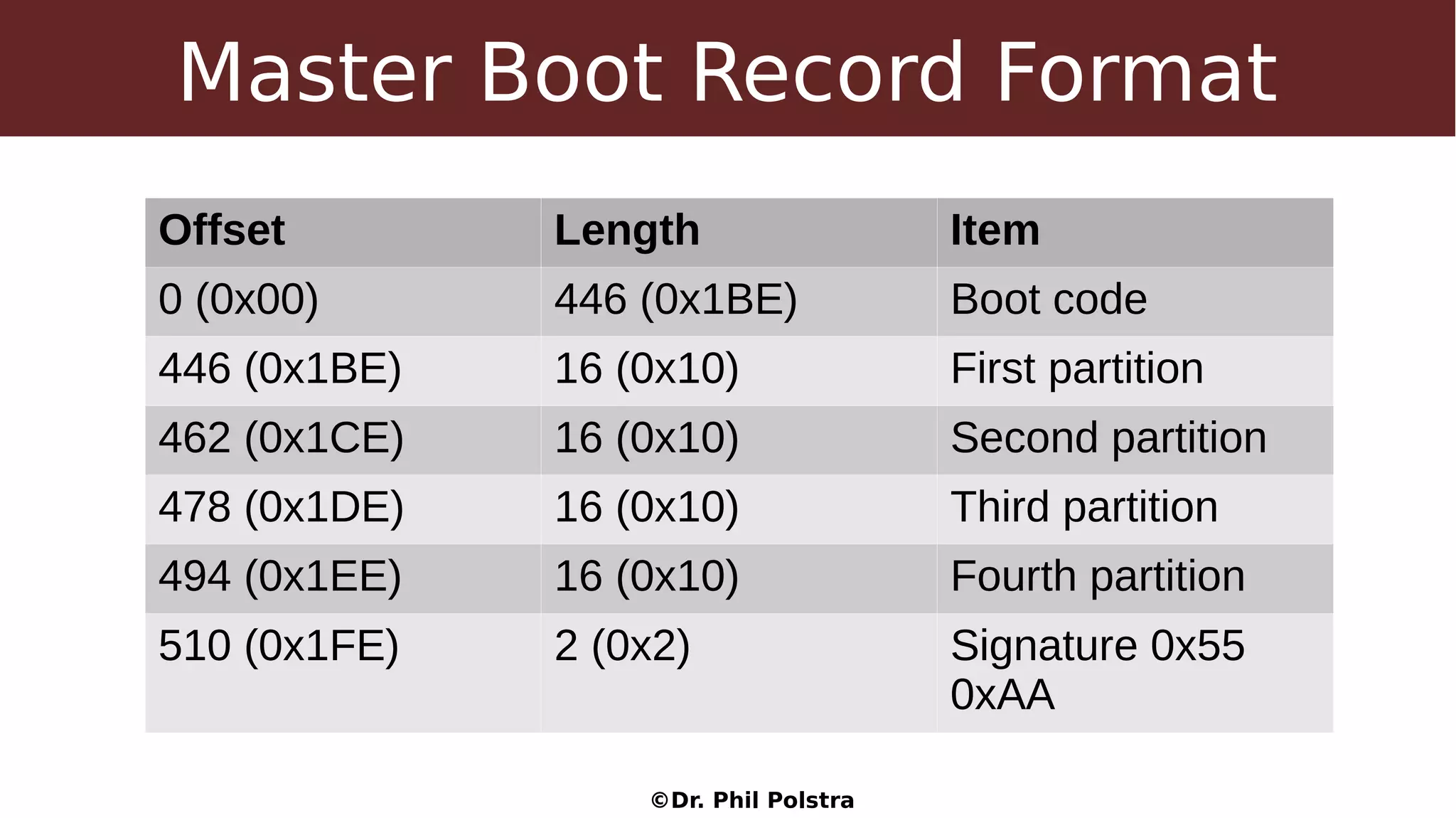
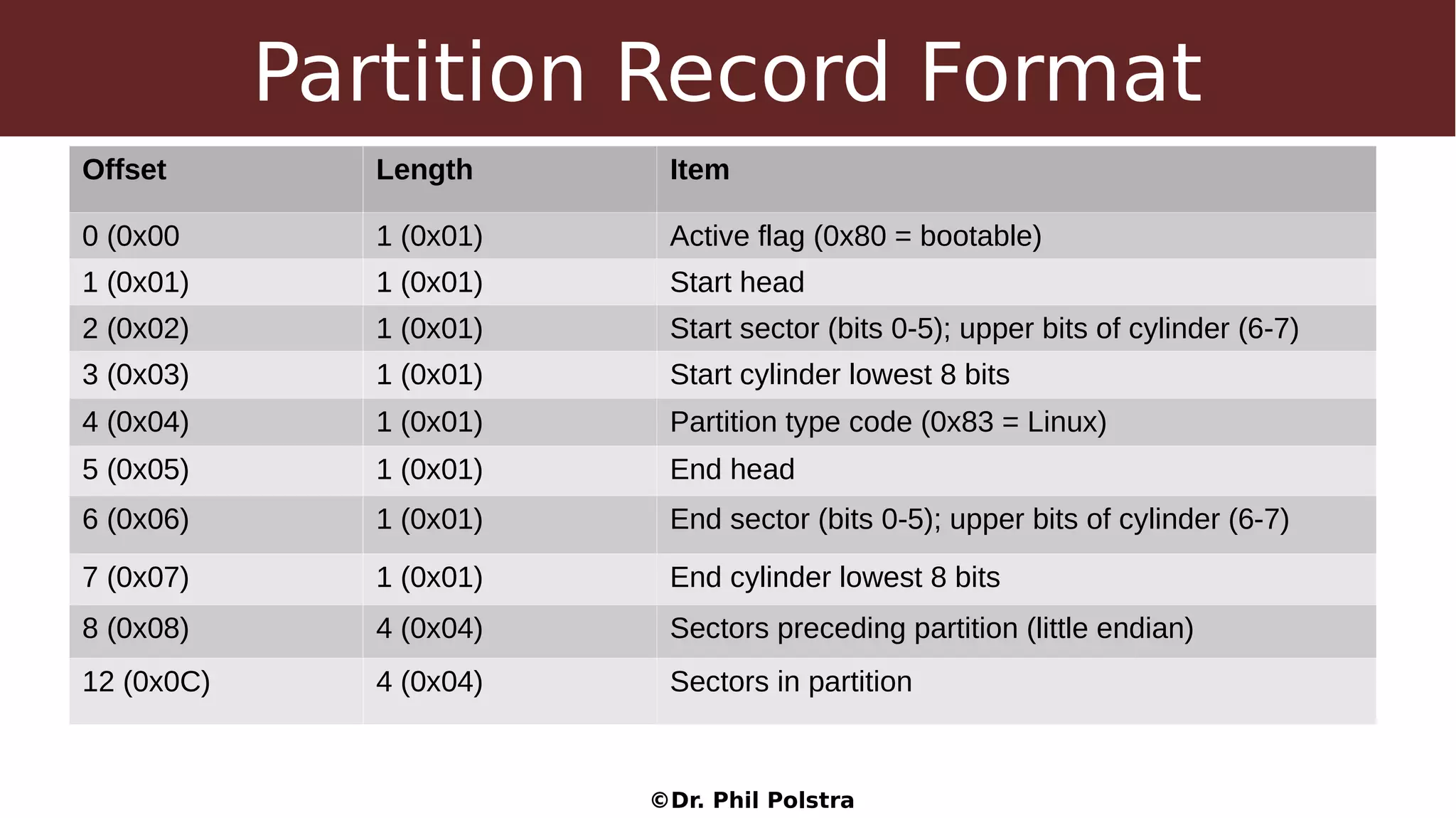
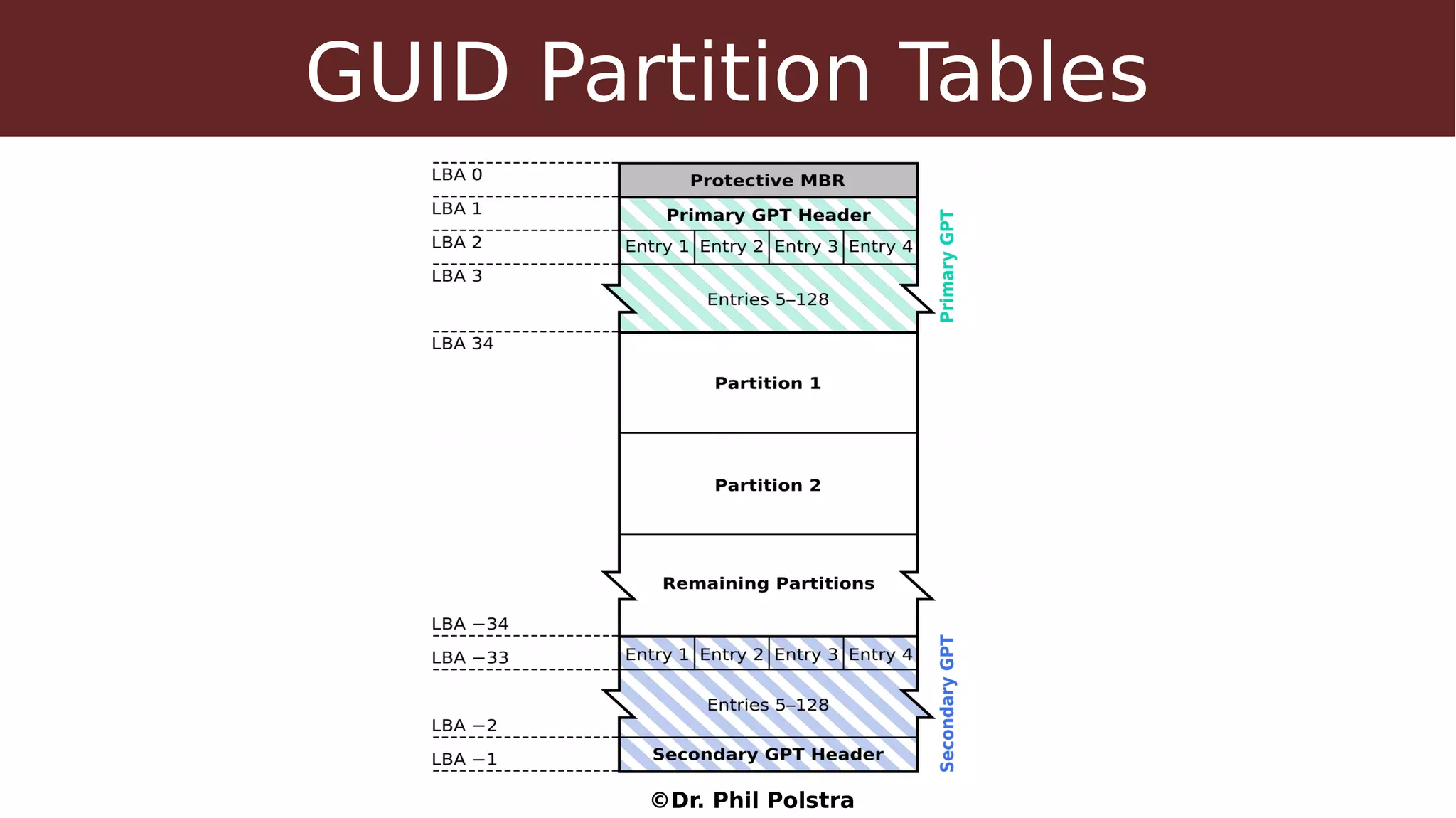
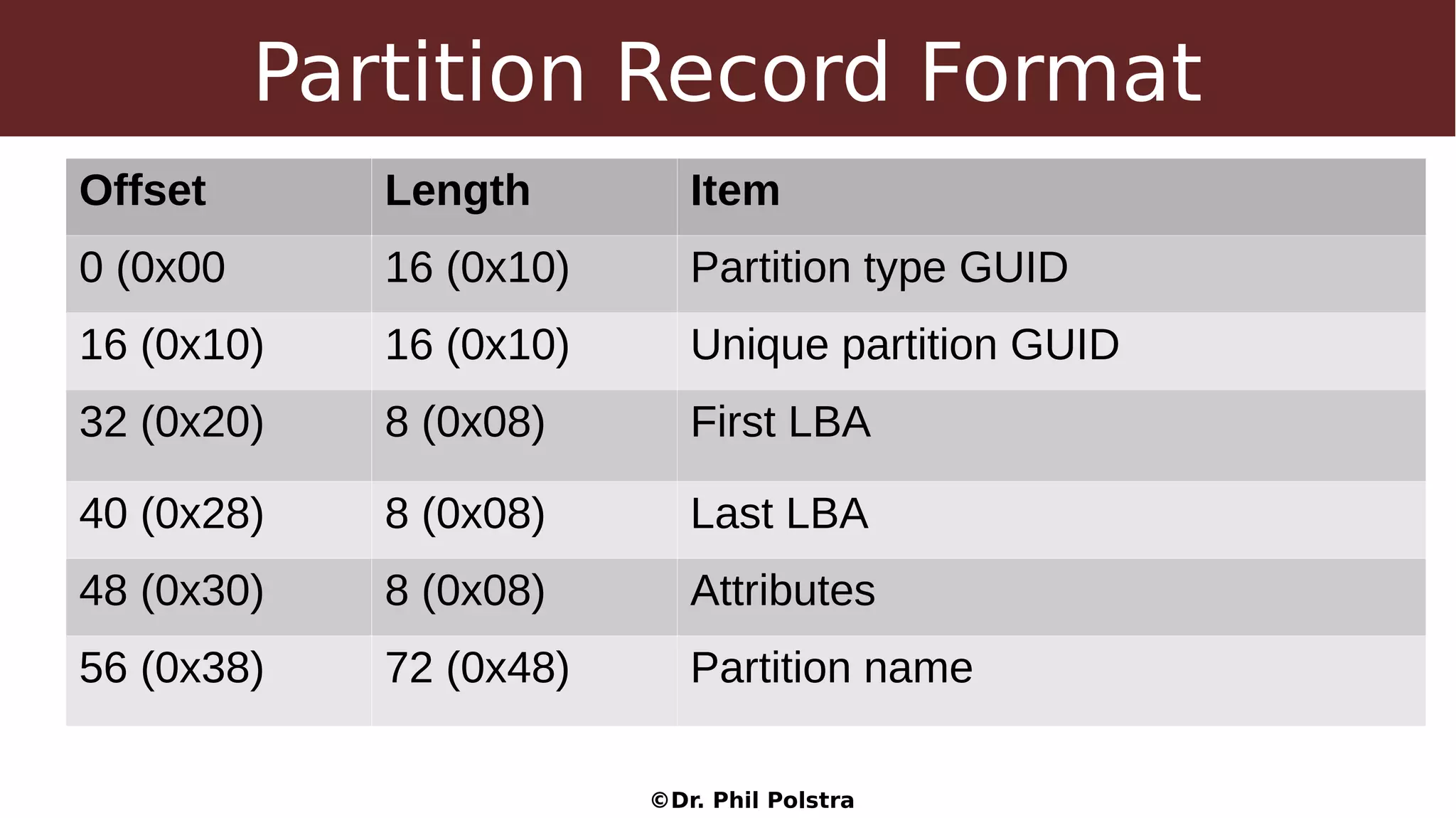
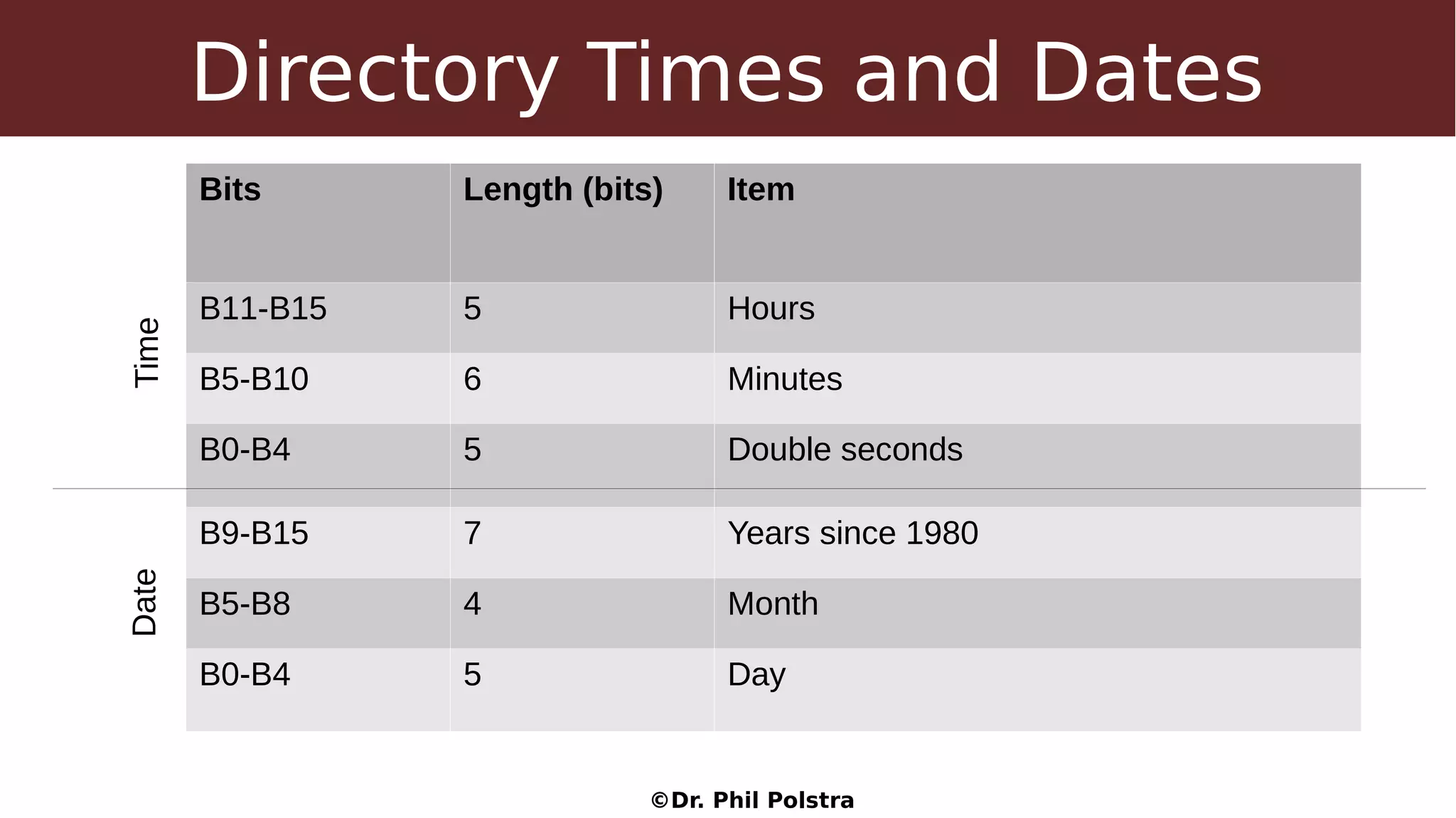
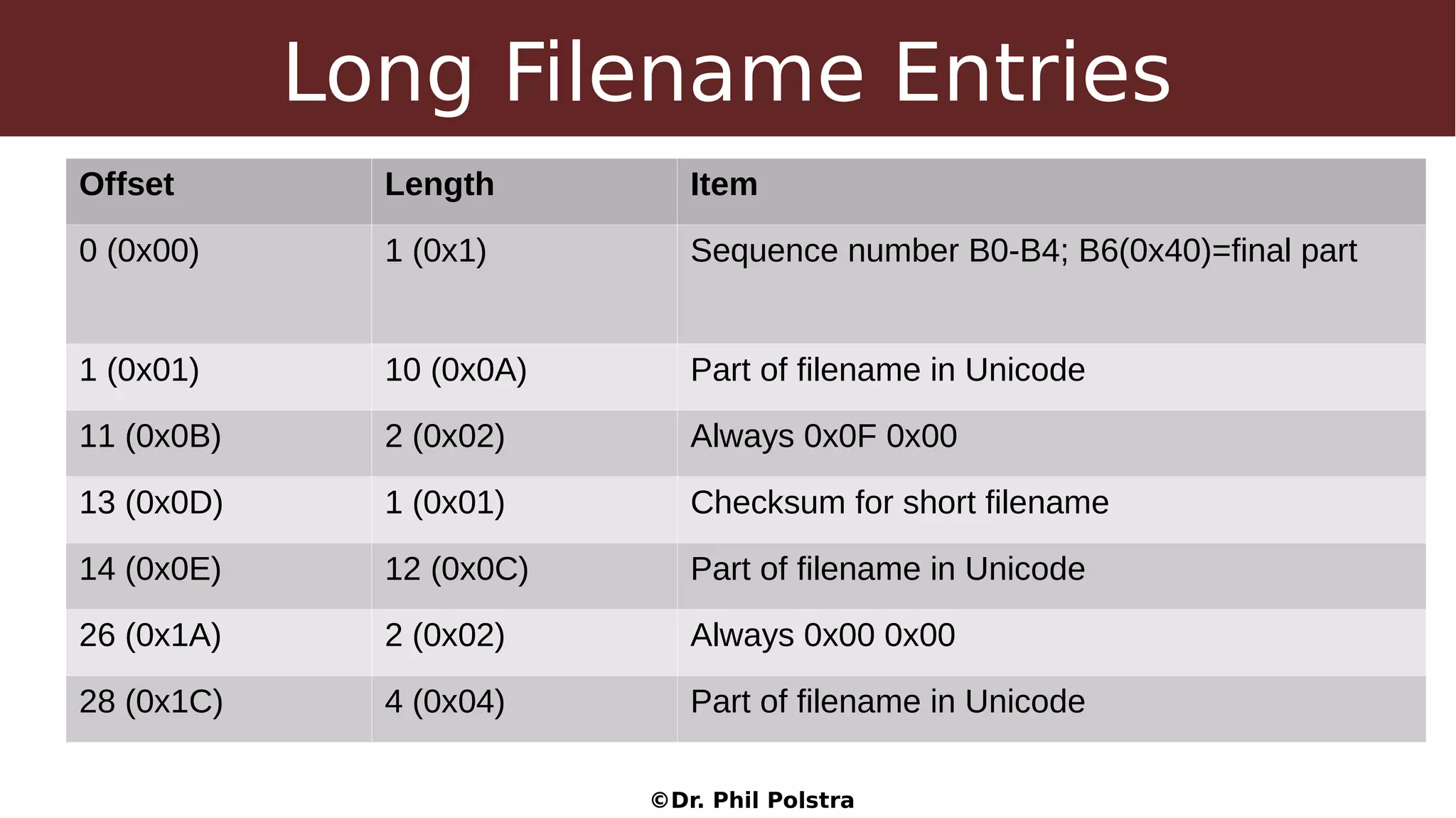
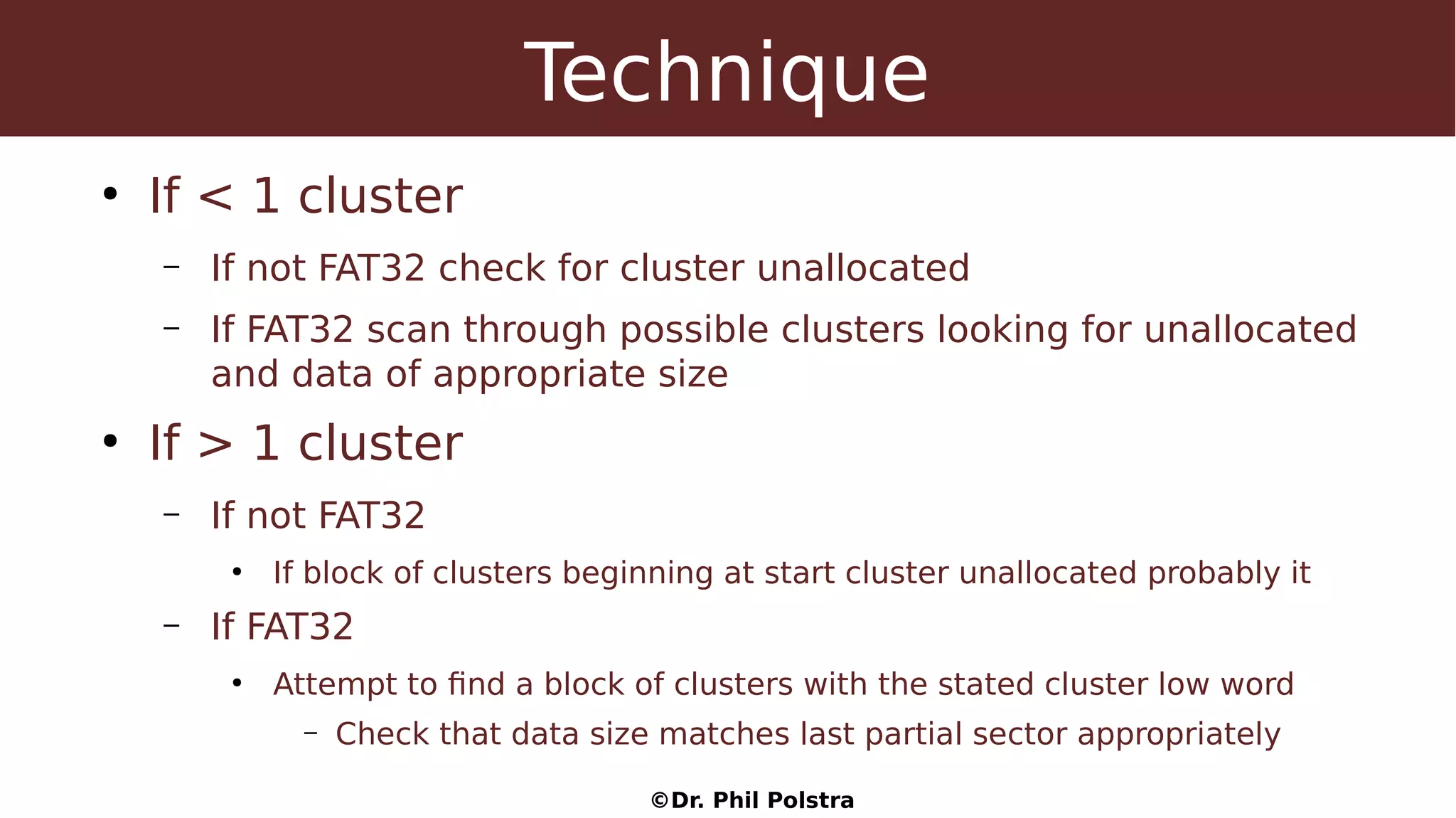
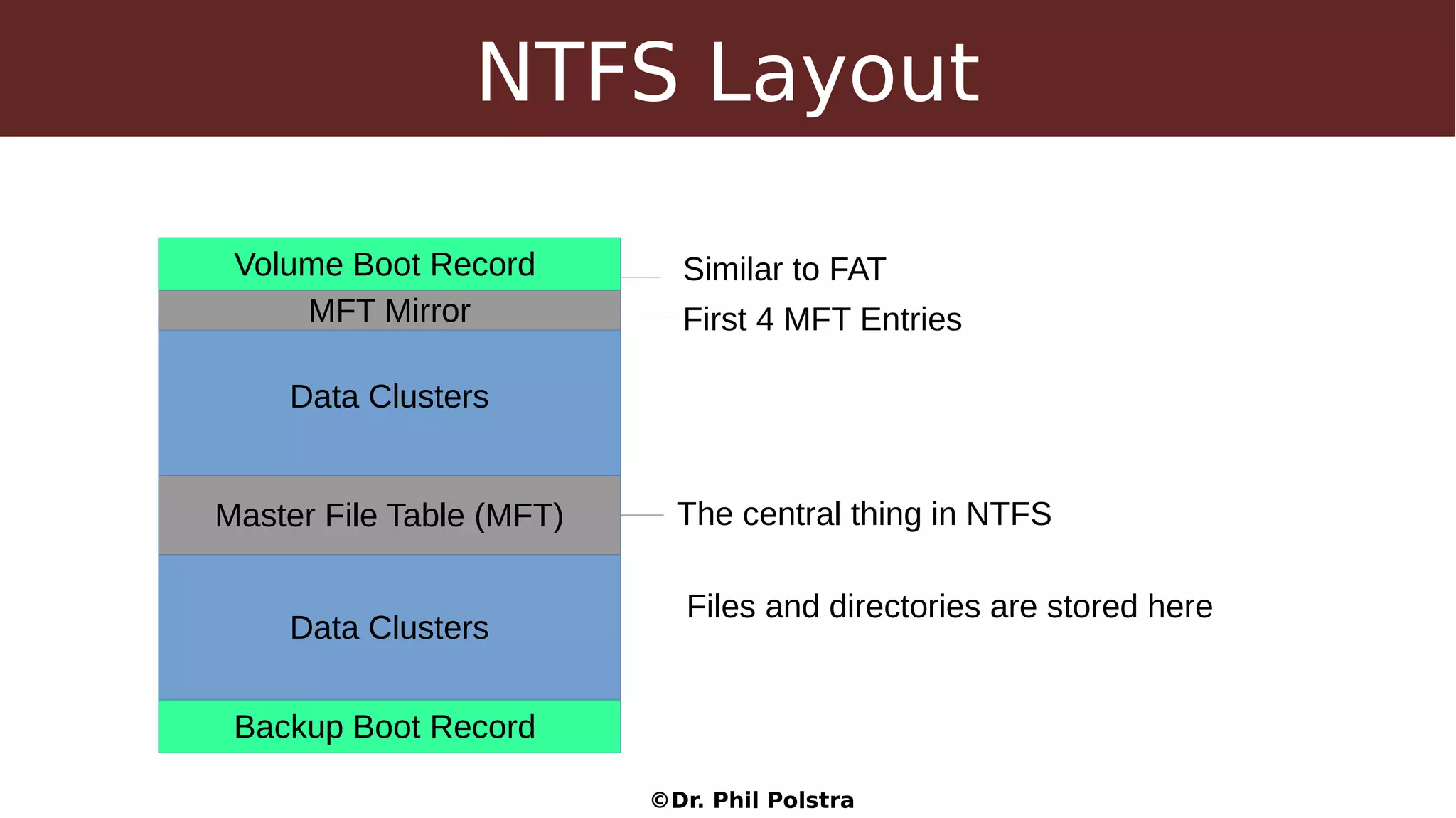
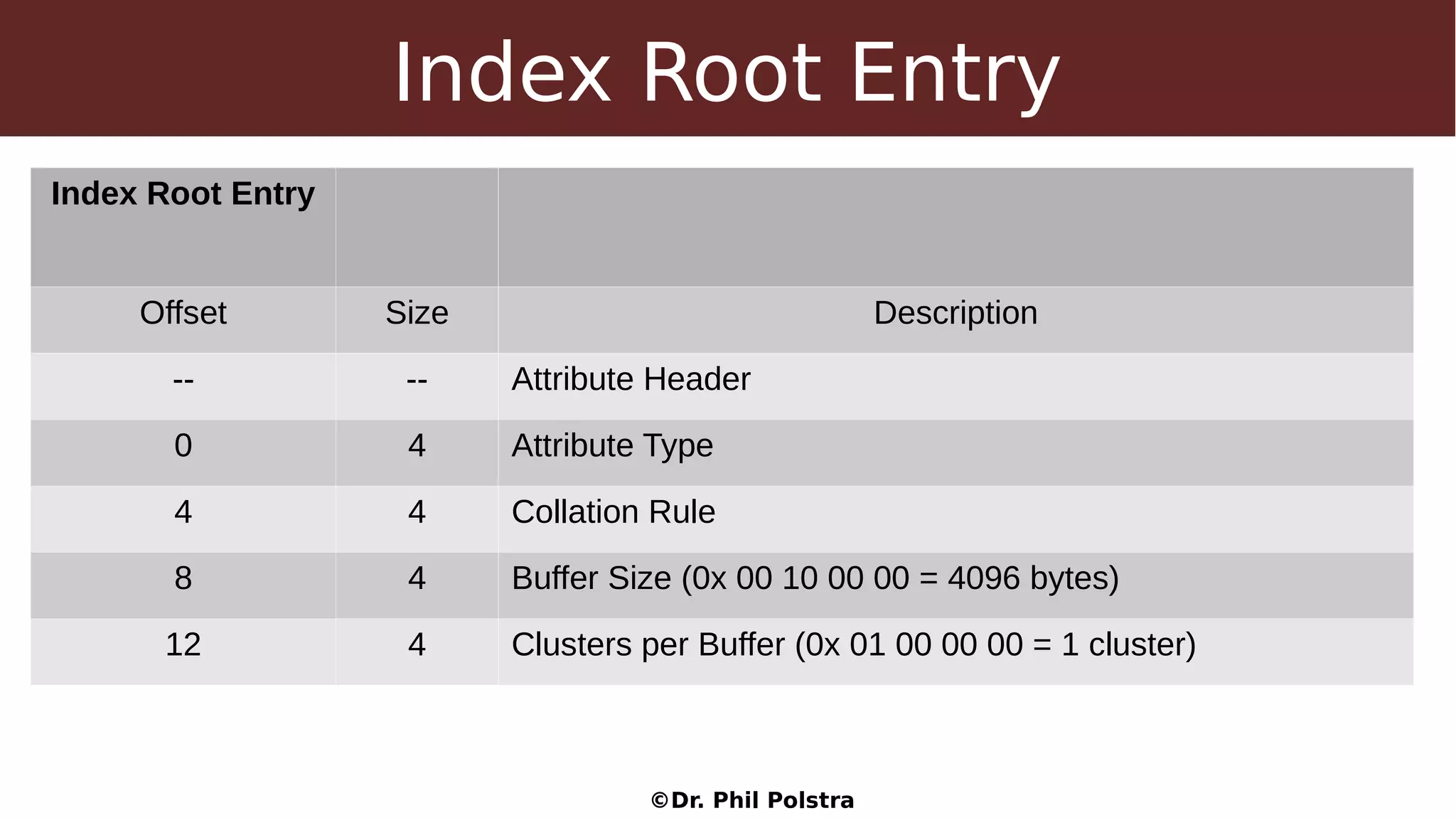
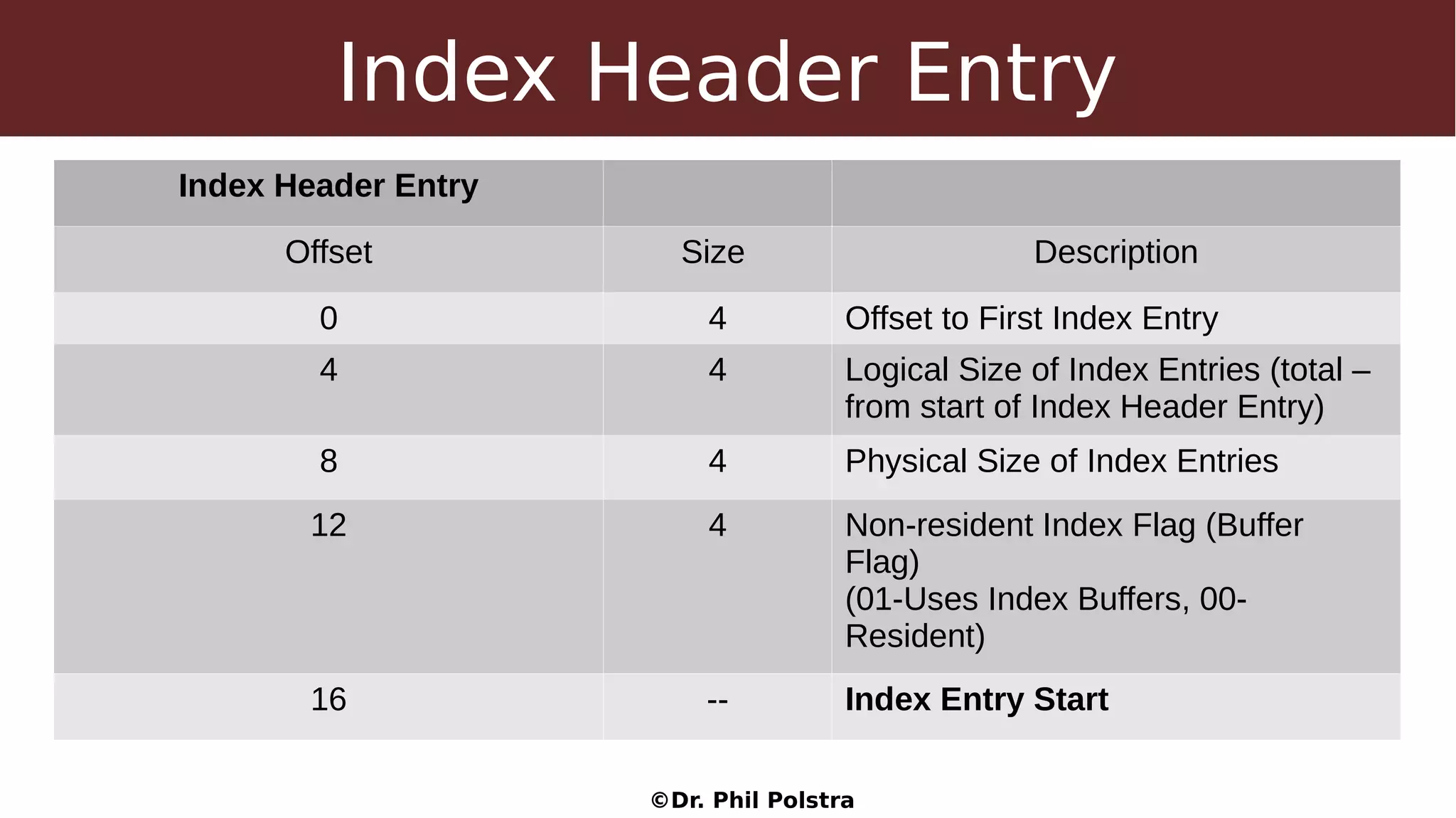
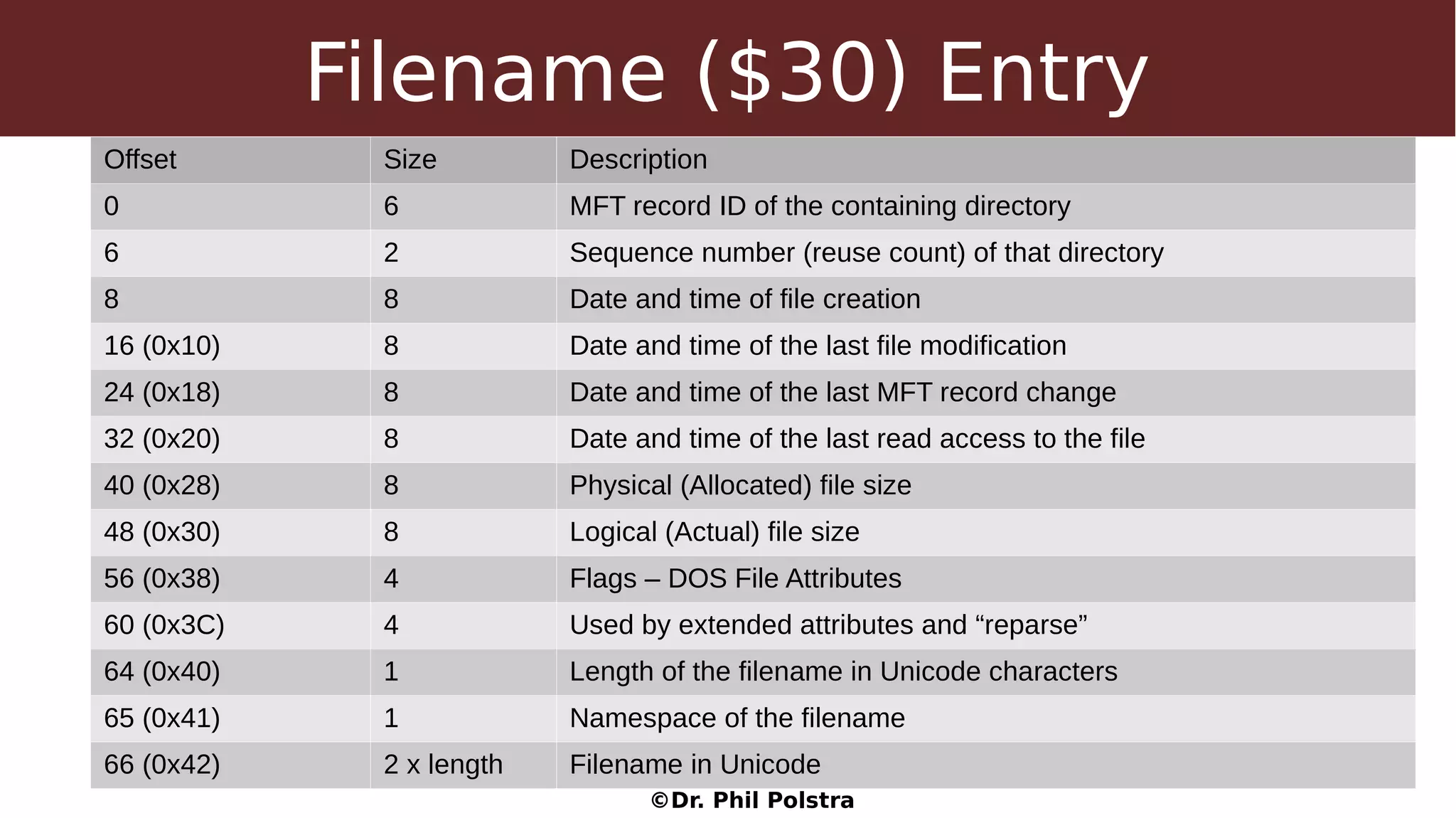
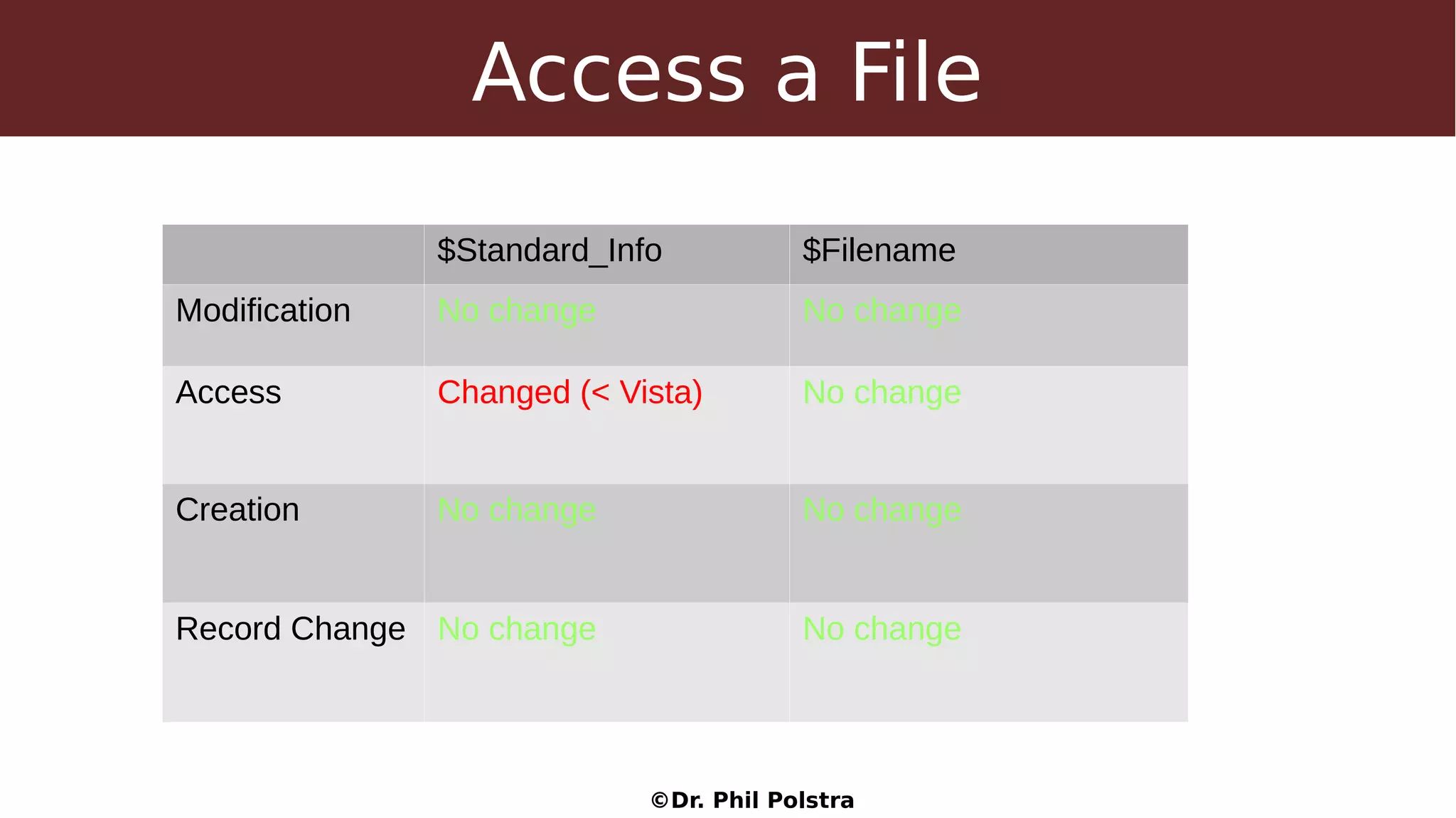
This document provides an overview of digital forensics concepts and processes. It defines forensics as the scientific collection of evidence suitable for use in court. It describes different types of forensics including physical and digital. The document outlines general forensic principles like maintaining evidence integrity and documenting work. It also describes the phases of an investigation including evidence preservation, searching, and event reconstruction.