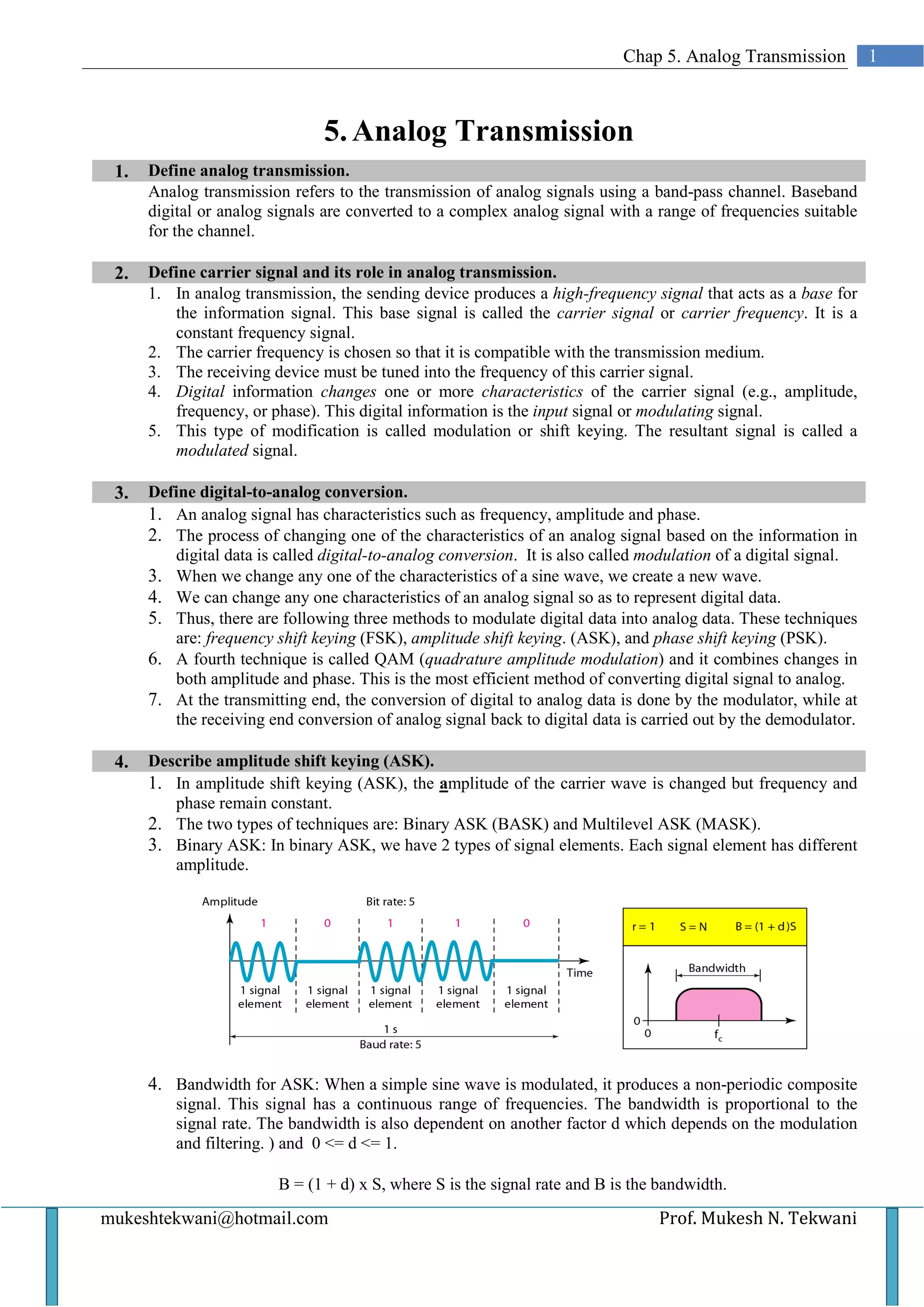
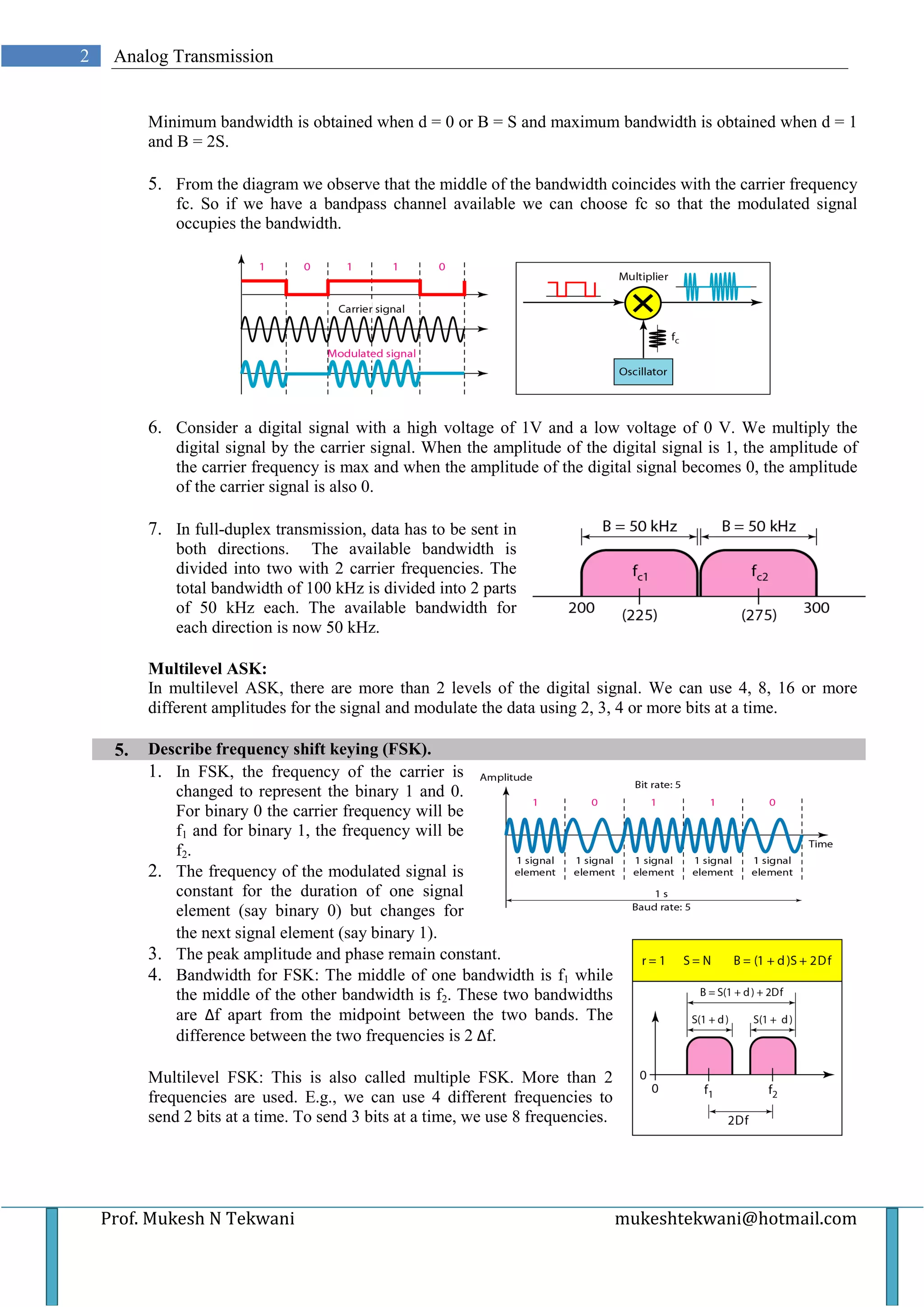
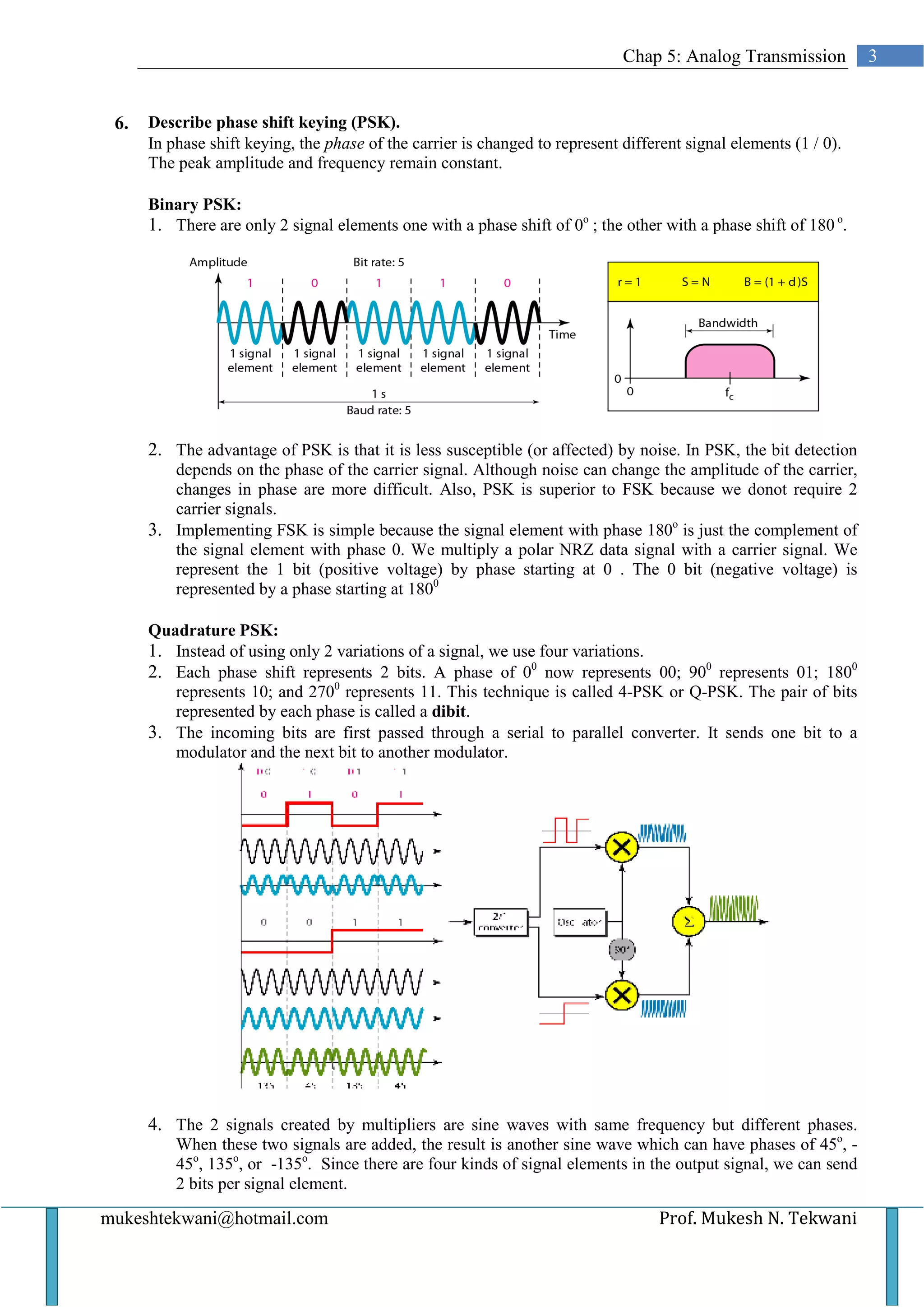
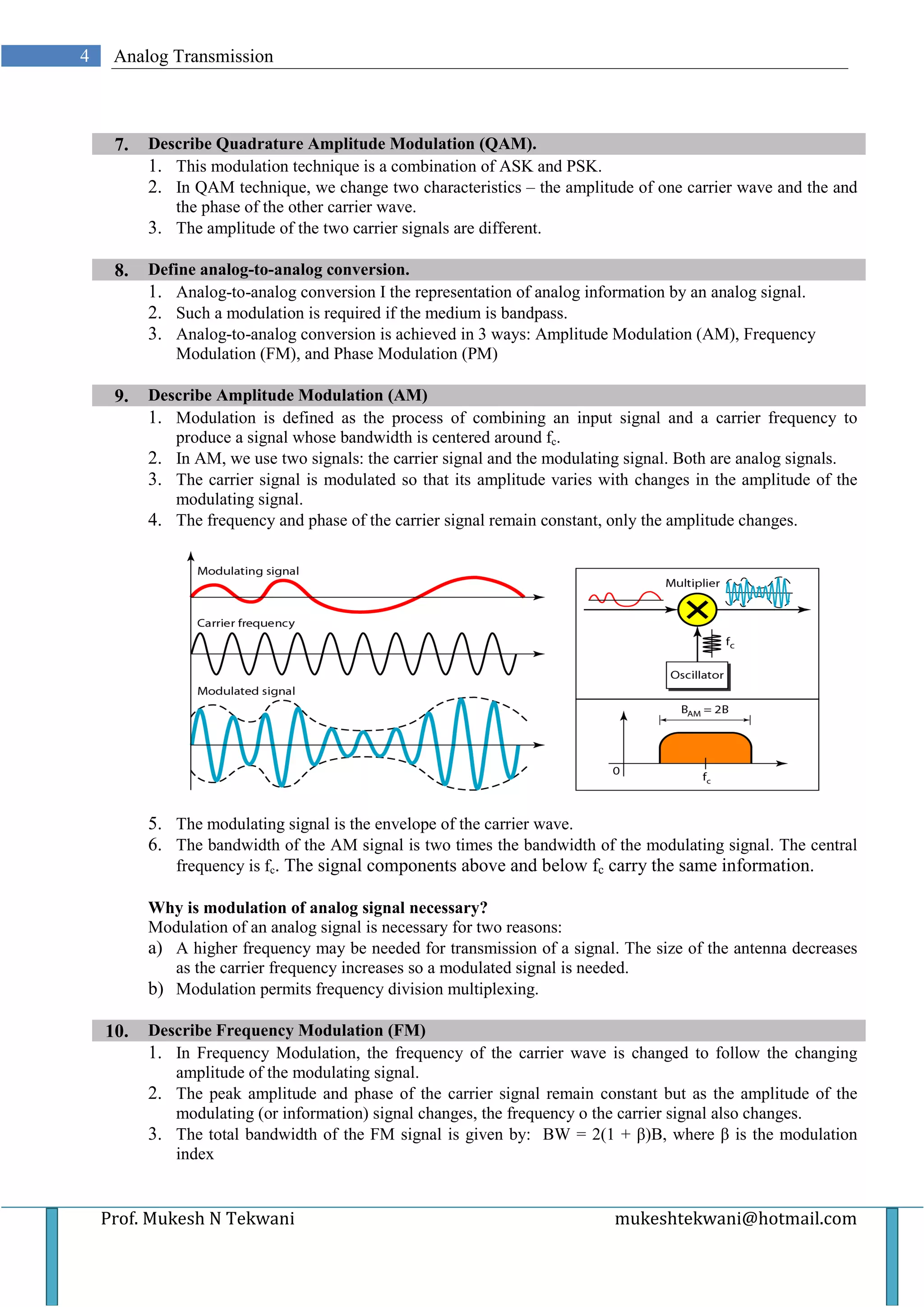
This document discusses various types of analog transmission techniques. It defines analog transmission as the transmission of analog signals using a band-pass channel, where baseband signals are converted to complex analog signals with frequencies suitable for the channel. It describes different modulation techniques used in analog transmission including amplitude shift keying (ASK), frequency shift keying (FSK), phase shift keying (PSK), and quadrature amplitude modulation (QAM). It also discusses analog-to-analog conversion techniques such as amplitude modulation (AM), frequency modulation (FM), and phase modulation (PM).