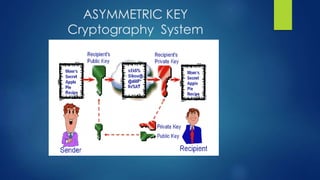
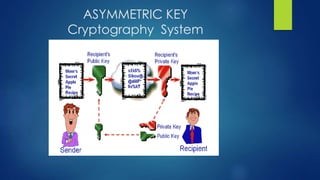
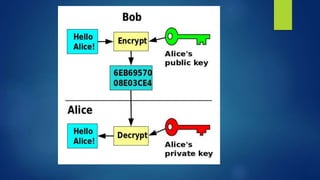
Public key algorithms like RSA and ElGamal allow for secure encryption without a shared private key. RSA uses a public and private key pair generated from large prime numbers such that a message encrypted with the public key can only be decrypted by the corresponding private key. It is widely used due to its security being based on the difficulty of factoring large numbers, though it is less efficient than symmetric algorithms due to involving modular exponentiation. ElGamal also uses a public/private key approach and its security relies on the discrete logarithm problem.