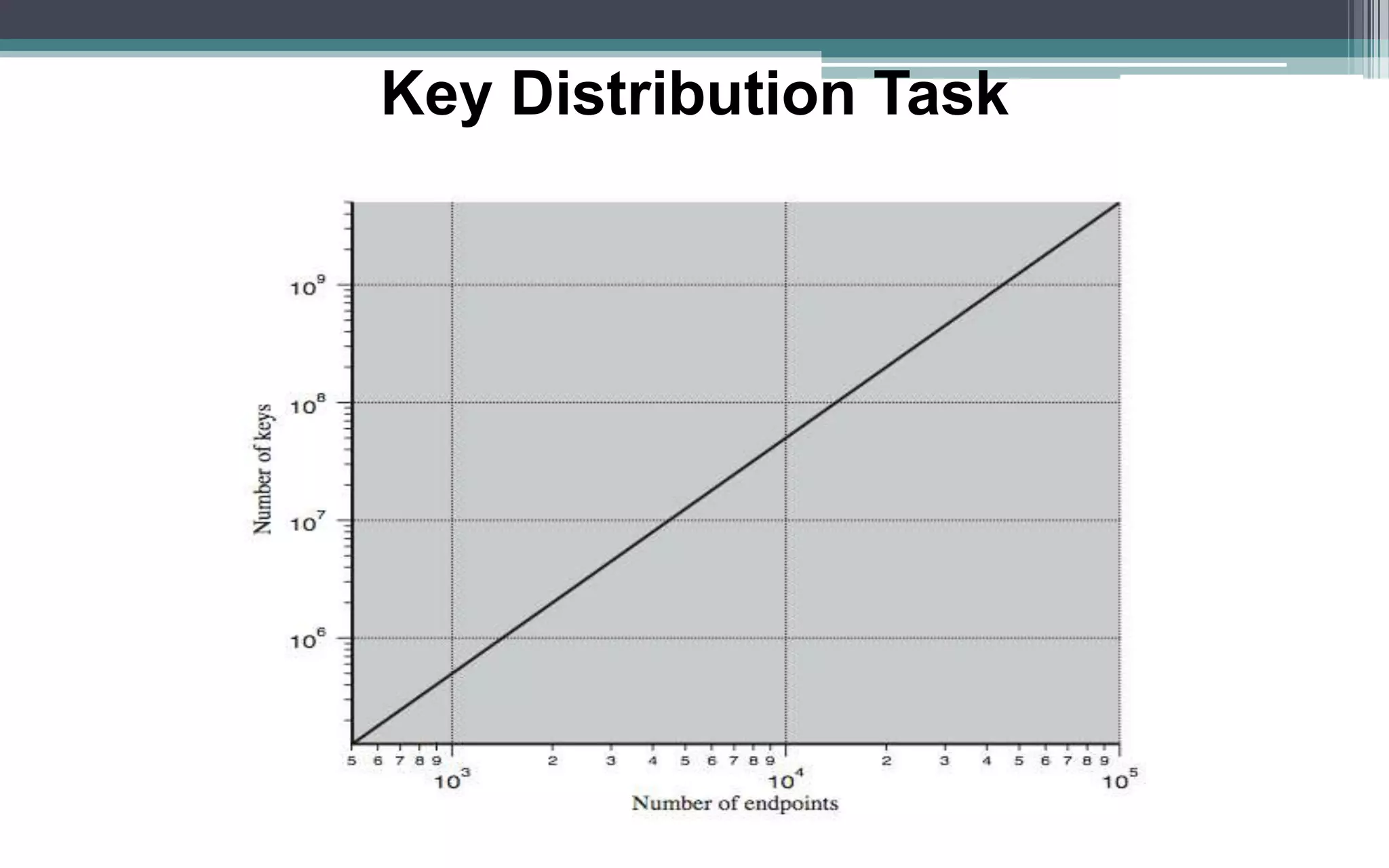
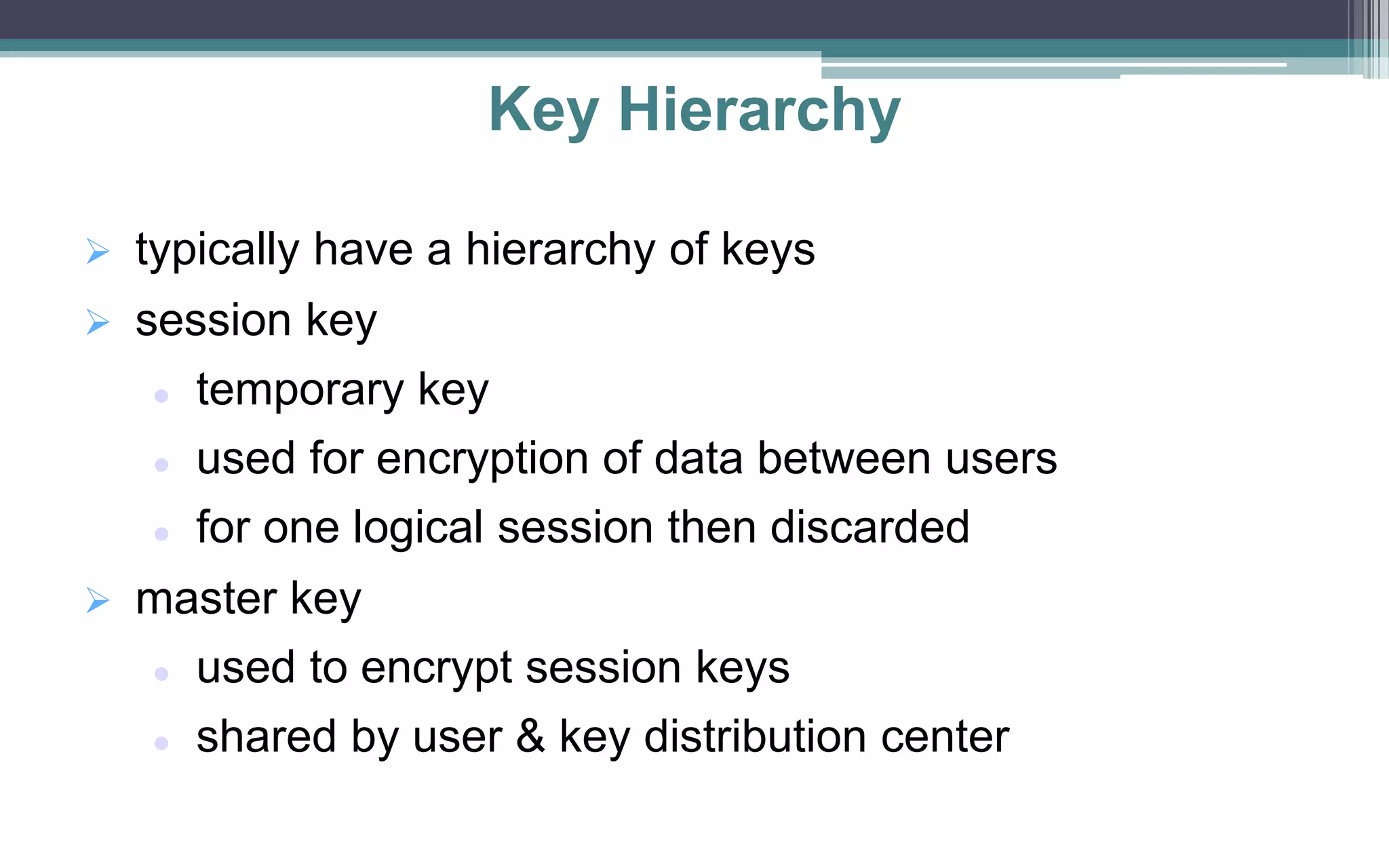
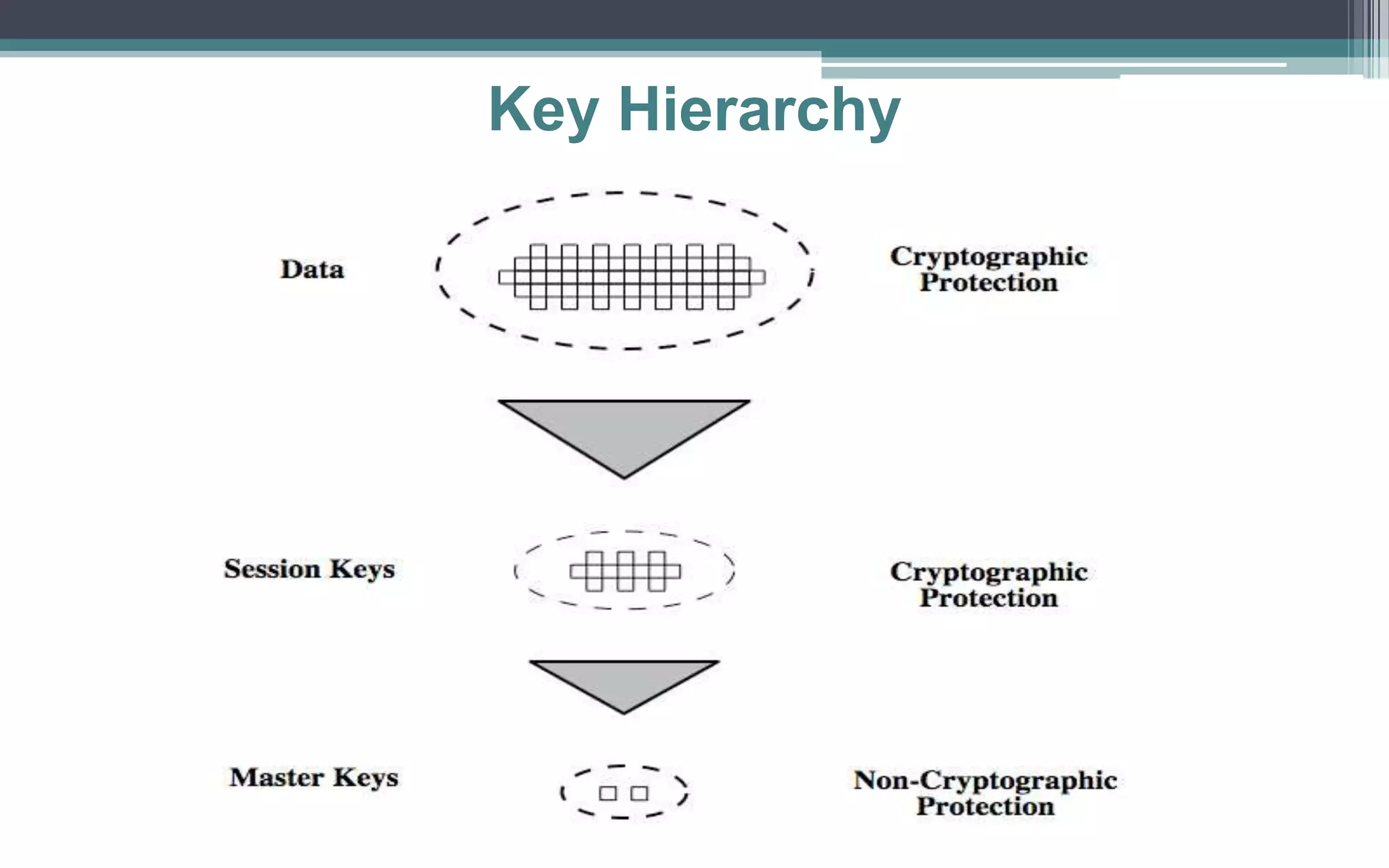
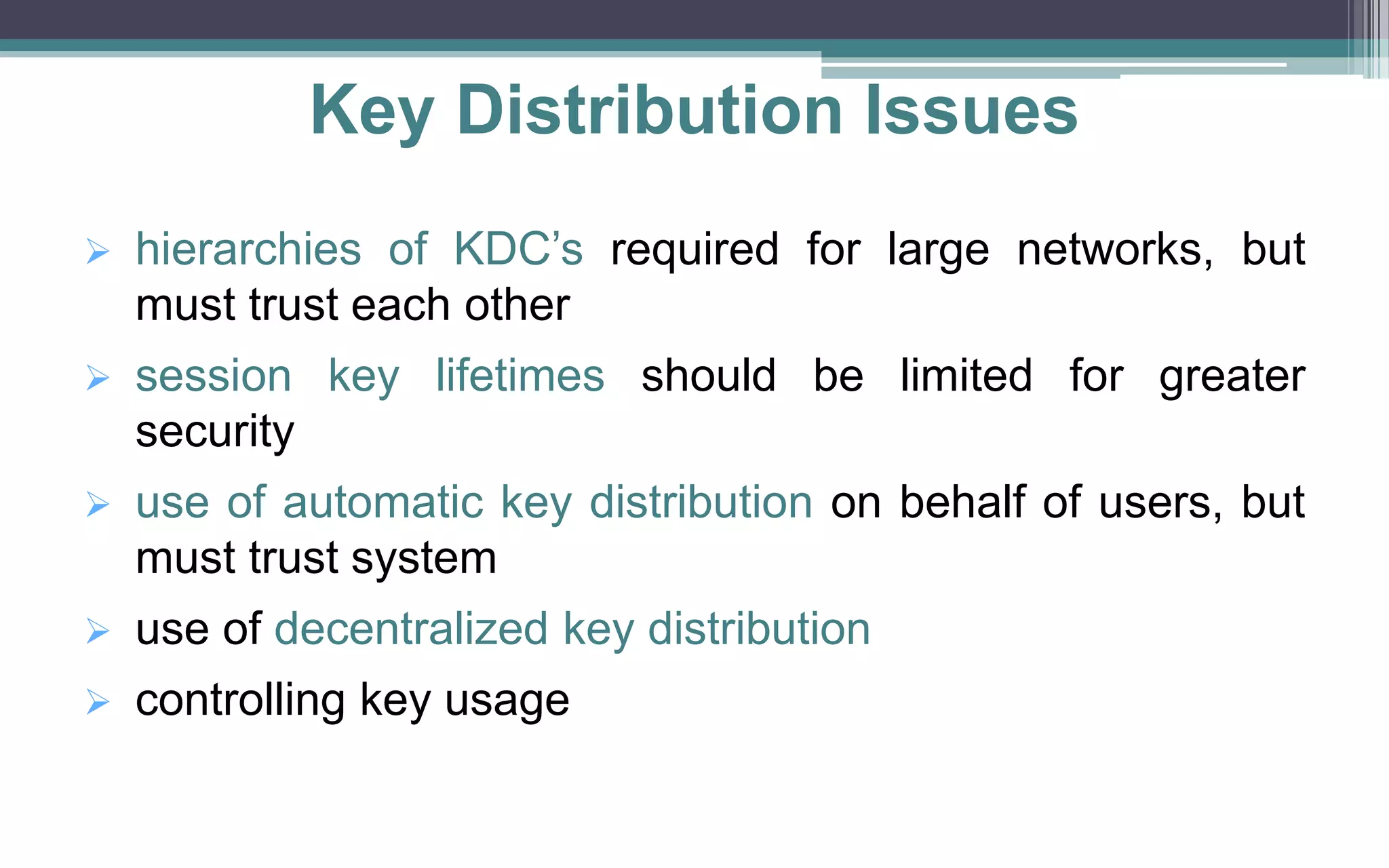
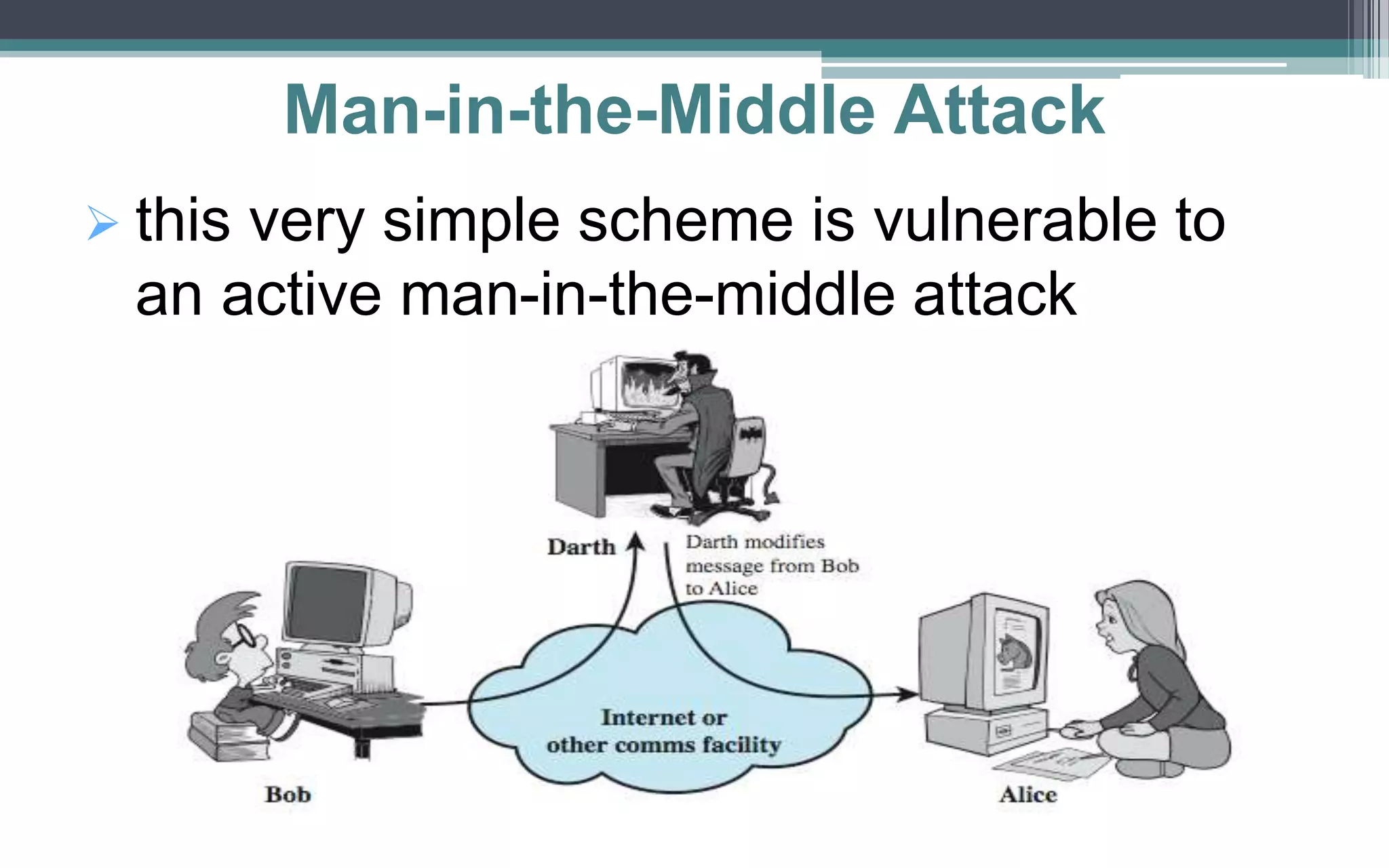
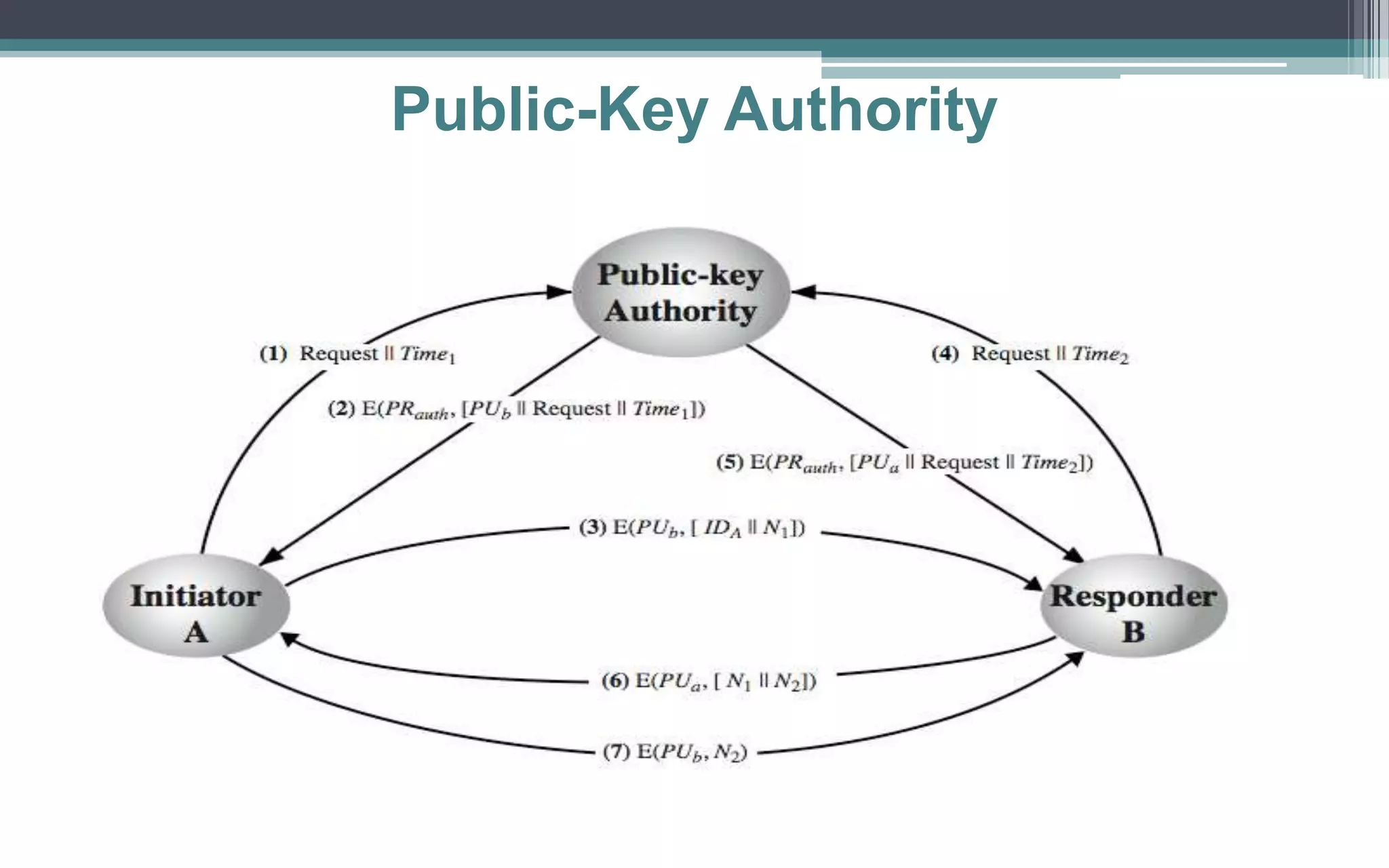
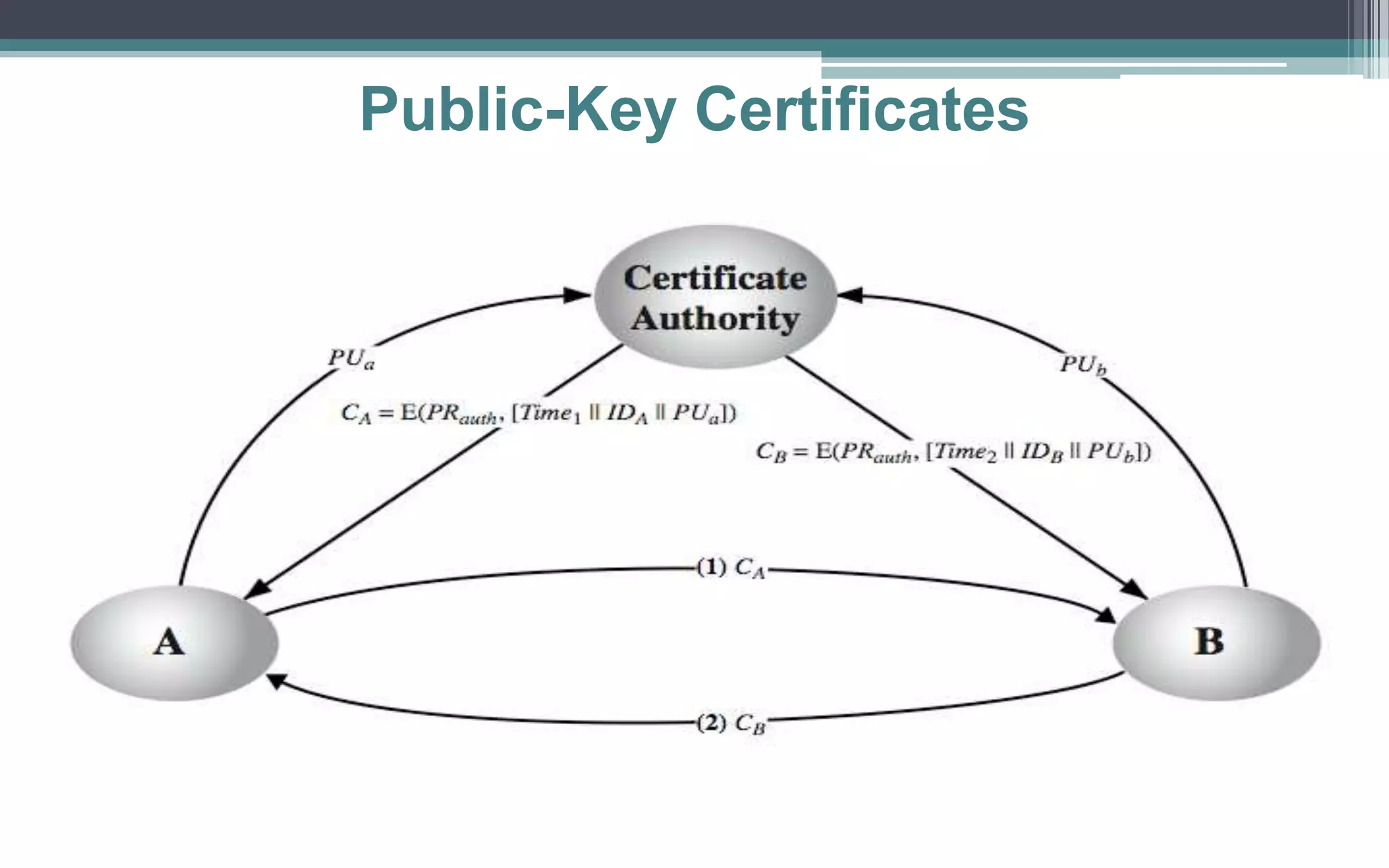
Key management and distribution are complex due to cryptographic, protocol, and management issues. Symmetric schemes require parties to share a secret key, while public key schemes require parties to acquire valid public keys. This document discusses several methods for distributing keys, including using symmetric encryption, public key encryption, public announcements, directories, authorities, and certificates signed by certificate authorities.