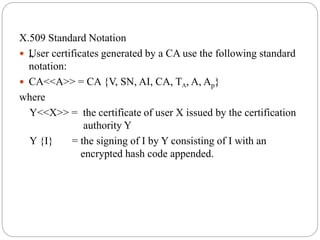
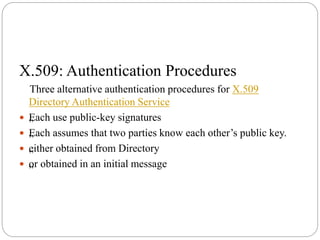
The document provides an overview of the x.509 directory authentication service, part of x.500 directory services, which defines a framework for authentication using public-key cryptography and digital signatures. It details the characteristics and structure of x.509 certificates, the role of certification authorities (CAs), including trust issues and the practicality of using multiple CAs for large user communities. Additionally, it describes alternative authentication procedures that assume prior knowledge of public keys between parties.