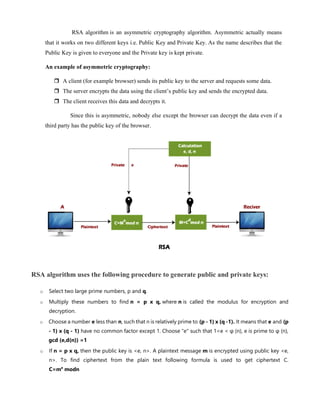
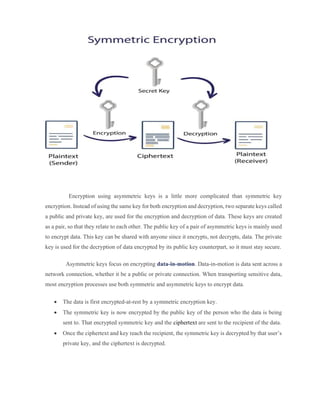
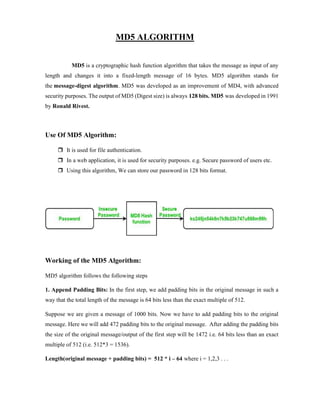
The document discusses the RSA algorithm for cryptography. It begins by explaining that RSA was created by Ron Rivest, Adi Shamir, and Leonard Adleman in 1977. It uses logarithmic functions to encrypt and decrypt data in a way that is difficult to break, even with powerful computers. RSA can encrypt generic data to enable secure sharing and can verify digital signatures. It works using a public key that encrypts data and a private key that decrypts it. The document then provides examples of how RSA encryption works step-by-step using prime numbers to generate keys. It discusses the security of RSA and how increasing the key size makes it more difficult to break through brute force attacks or factorization. Proper key management is













![// getInstance() method is called with algorithm SHA-1
MessageDigest md = MessageDigest.getInstance("SHA-1");
// digest() method is called
// to calculate message digest of the input string
// returned as array of byte
byte[] messageDigest = md.digest(input.getBytes());
// Convert byte array into signum representation
BigInteger no = new BigInteger(1, messageDigest);
// Convert message digest into hex value
String hashtext = no.toString(16);
// Add preceding 0s to make it 32 bit
while (hashtext.length() < 32) {
hashtext = "0" + hashtext;
}
// return the HashText
return hashtext;
}
// For specifying wrong message digest algorithms
catch (NoSuchAlgorithmException e) {
throw new RuntimeException(e);
}
}
// Driver code
public static void main(String args[]) throws
NoSuchAlgorithmException
{
System.out.println("HashCode Generated by SHA-1 for: ");
String s1 = "GeeksForGeeks";
System.out.println("n" + s1 + " : " + encryptThisString(s1));
String s2 = "hello world";
System.out.println("n" + s2 + " : " + encryptThisString(s2));
}
}](https://image.slidesharecdn.com/cryptography2-230209180450-15c17e1d/85/CRYPTOGRAPHY-2-pdf-16-320.jpg)


![After applying the function now we perform an operation on each block. For performing
operations we need
add modulo 232
M[i] – 32 bit message.
K[i] – 32-bit constant.
<<<n – Left shift by n bits.
Now take input as initialize MD buffer i.e. J, K, L, M. Output of K will be fed in L, L will
be fed into M, and M will be fed into J. After doing this now we perform some operations to find
the output for J.
In the first step, Outputs of K, L, and M are taken and then the function F is applied to
them. We will add modulo 232
bits for the output of this with J.
In the second step, we add the M[i] bit message with the output of the first step.
Then add 32 bits constant i.e. K[i] to the output of the second step.
At last, we do left shift operation by n (can be any value of n) and addition modulo by 232
.
After all steps, the result of J will be fed into K. Now same steps will be used for all functions G, H,
and I. After performing all 64 operations we will get our message digest.
Output:
After all, rounds have been performed, the buffer J, K, L, and M contains the MD5 output starting
with the lower bit J and ending with Higher bits M.
Code:
# importing the required libraries
import hashlib
inputstring = "This is a message sent by a computer user."
# encoding the message using the library function
output = hashlib.md5(inputstring.encode())
# printing the hash function
print("Hash of the input string:")
print(output.hexdigest())](https://image.slidesharecdn.com/cryptography2-230209180450-15c17e1d/85/CRYPTOGRAPHY-2-pdf-20-320.jpg)




![SSL Handshake
(1) Client Hello (algorithms,…)
(2) Server Hello (alg. selection, …)
(3) Server Certificate
(4) ClientKeyRequest
(5) ChangeCipherSuite
(6) ChangeCipherSuite
(7) Finished
(8) Finished
Simplified Protocol Detail
Participants: Alice/A (client) and Bob/B (server)
Crypto Elements : Random R, Certificate C, k+
i Public Key (of i)
Crypto Functions : Hash function H(x), Encryption E(k, d), Decryption D(k, d),
Keyed MAC HMAC(k, d)
1. Alice → Bob RA
2. Bob → Alice RB, CB
Alice pick pre-master secret S
Alice calculate master secret K = H(S, RA, RB)
3. Alice → Bob E(k+B, S), HMAC(K,! CLNT! + [#1, #2])
Bob recover pre-master secret S = D(k−B , E(k+B, S))
Bob calculate master secret K = H(S, RA, RB)
4. Bob → Alice HMAC(K,! SRV R! + [#1, #2])](https://image.slidesharecdn.com/cryptography2-230209180450-15c17e1d/85/CRYPTOGRAPHY-2-pdf-25-320.jpg)
