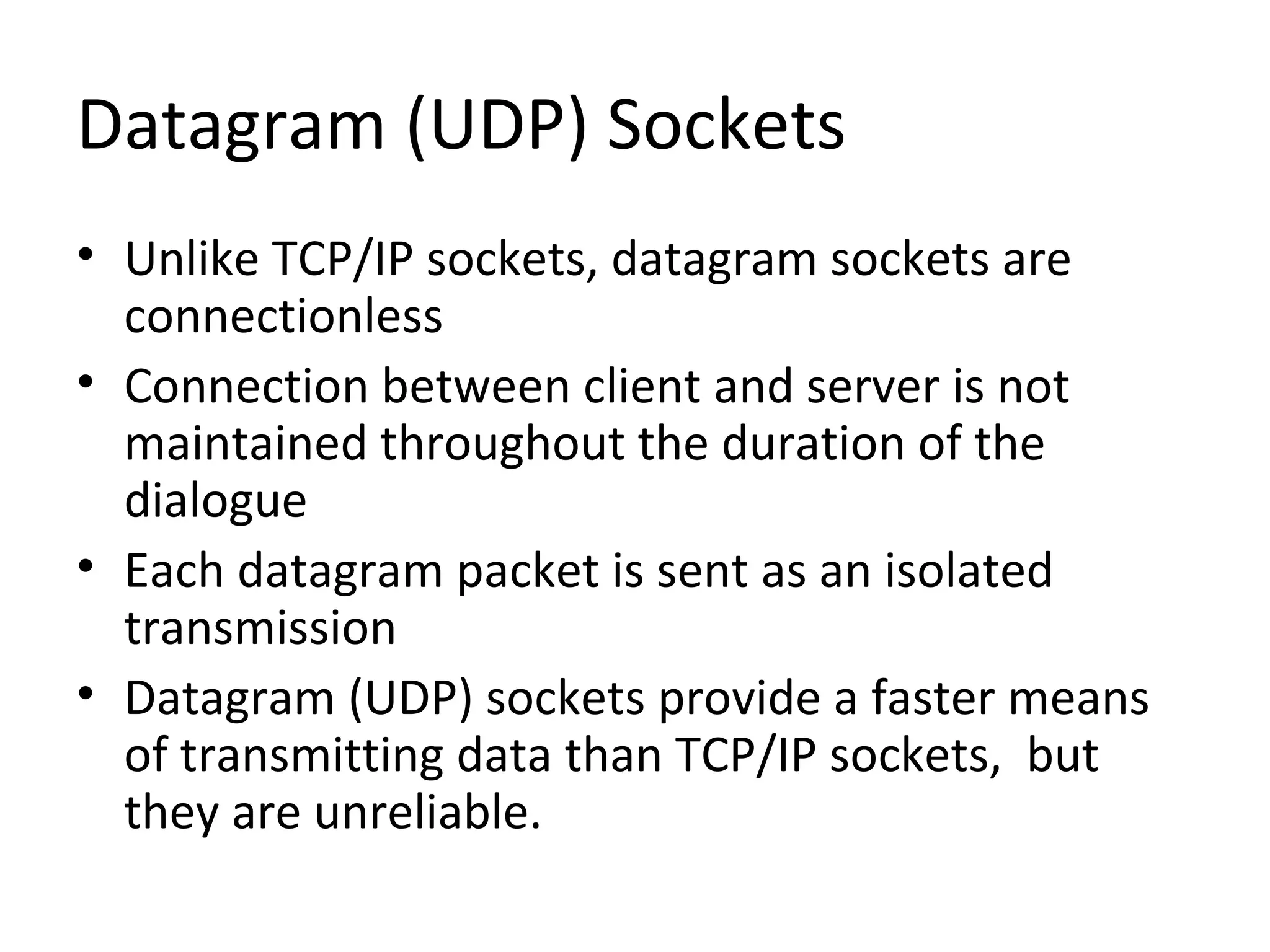
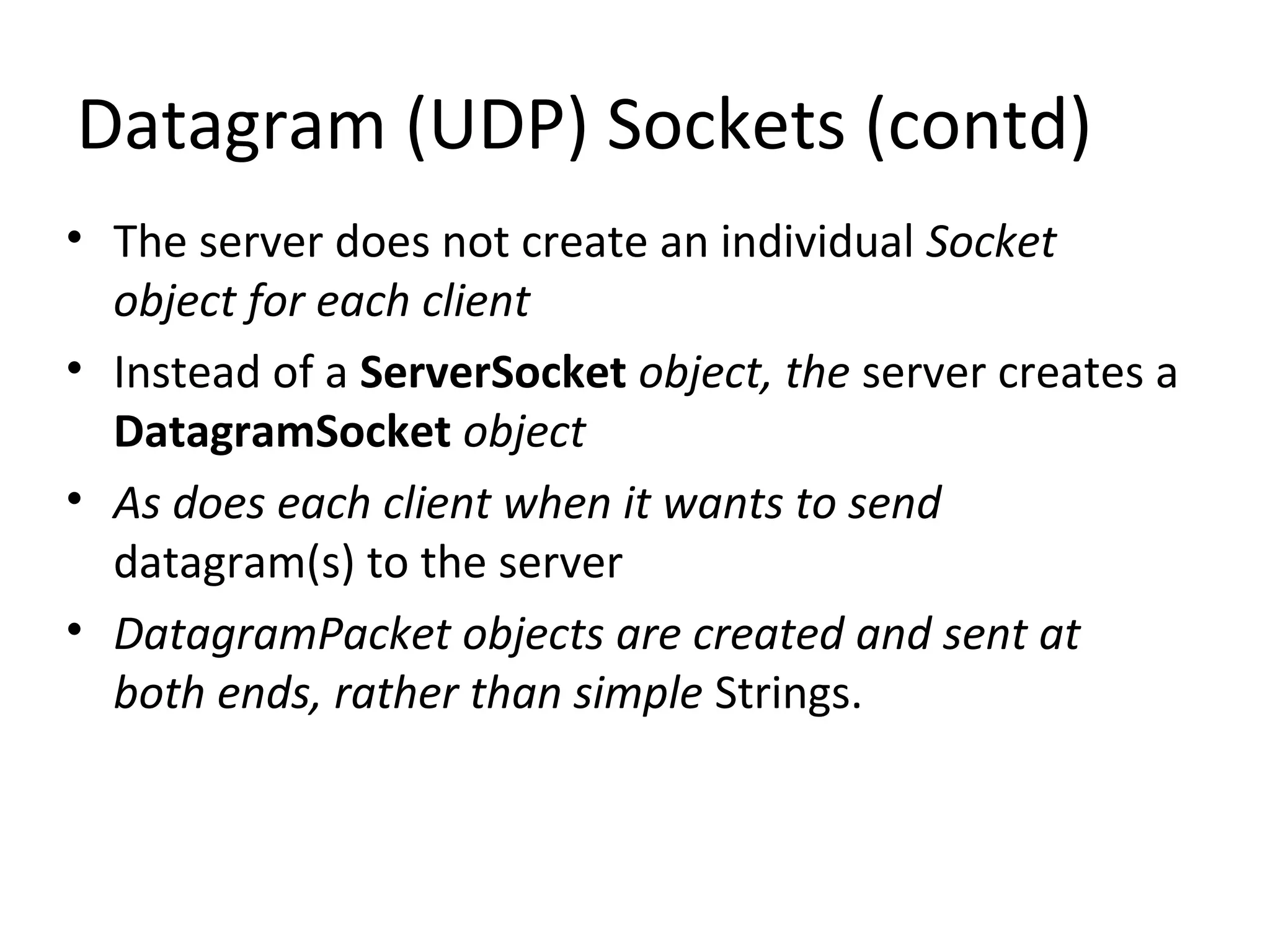
This document discusses UDP sockets and provides code examples for UDP client-server communication. UDP sockets are connectionless and unreliable compared to TCP sockets but provide faster transmission of data. The server creates a DatagramSocket and receives DatagramPacket objects without maintaining individual connections to clients. Clients also use DatagramSockets to send and receive DatagramPacket objects from the server. The code examples show the steps to create and use DatagramSockets on both the server and client sides.

![UDP Server
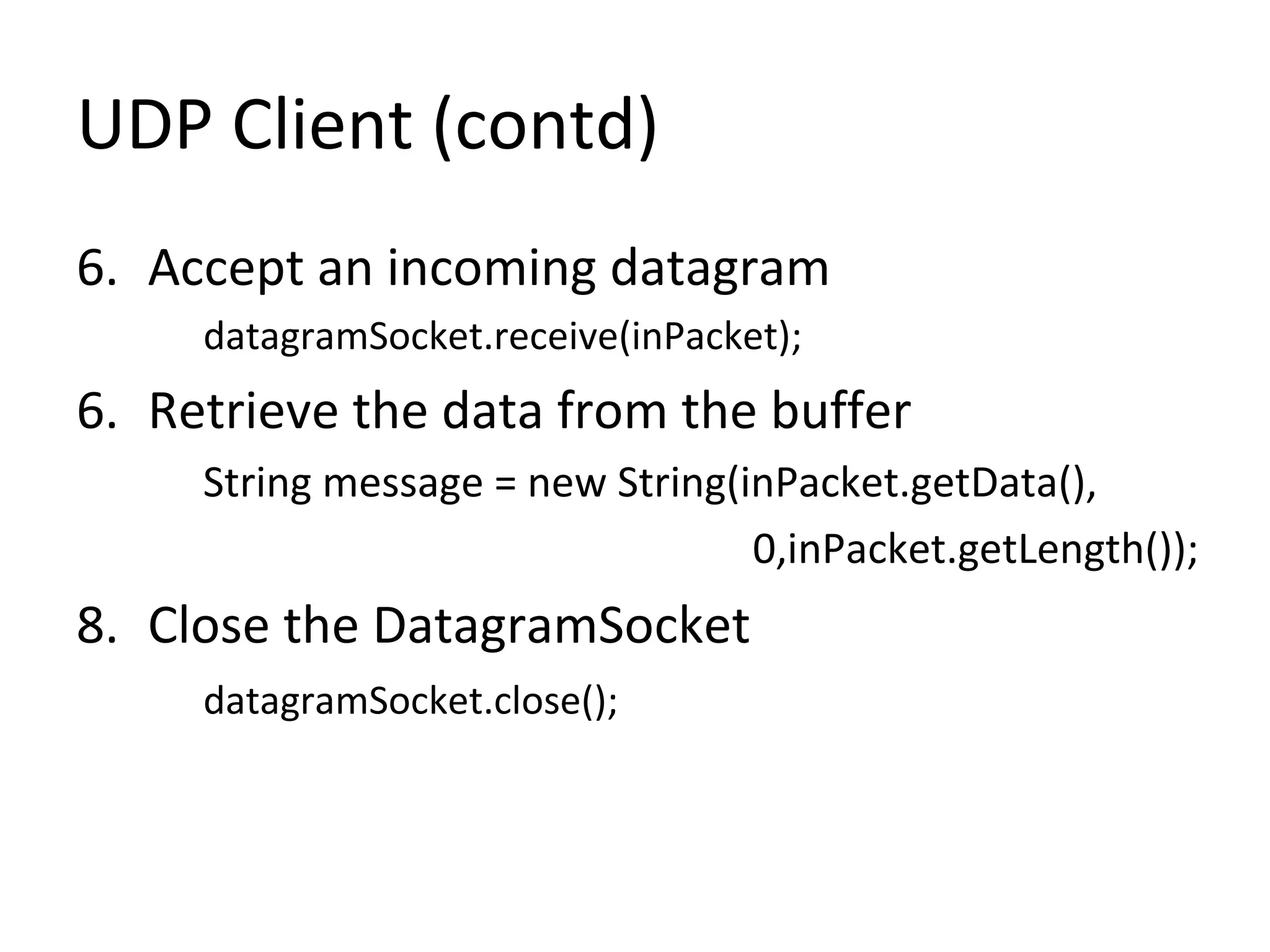
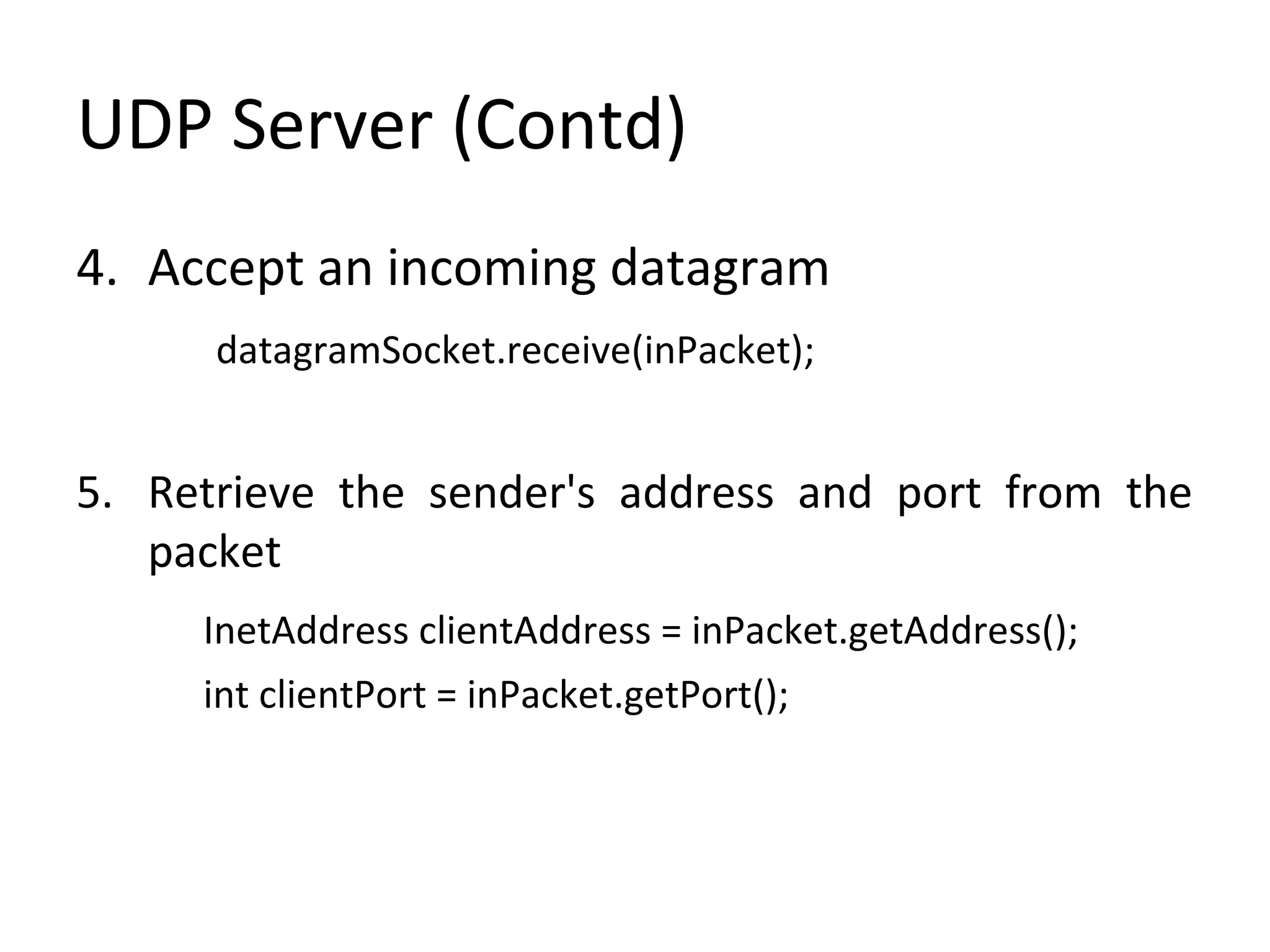
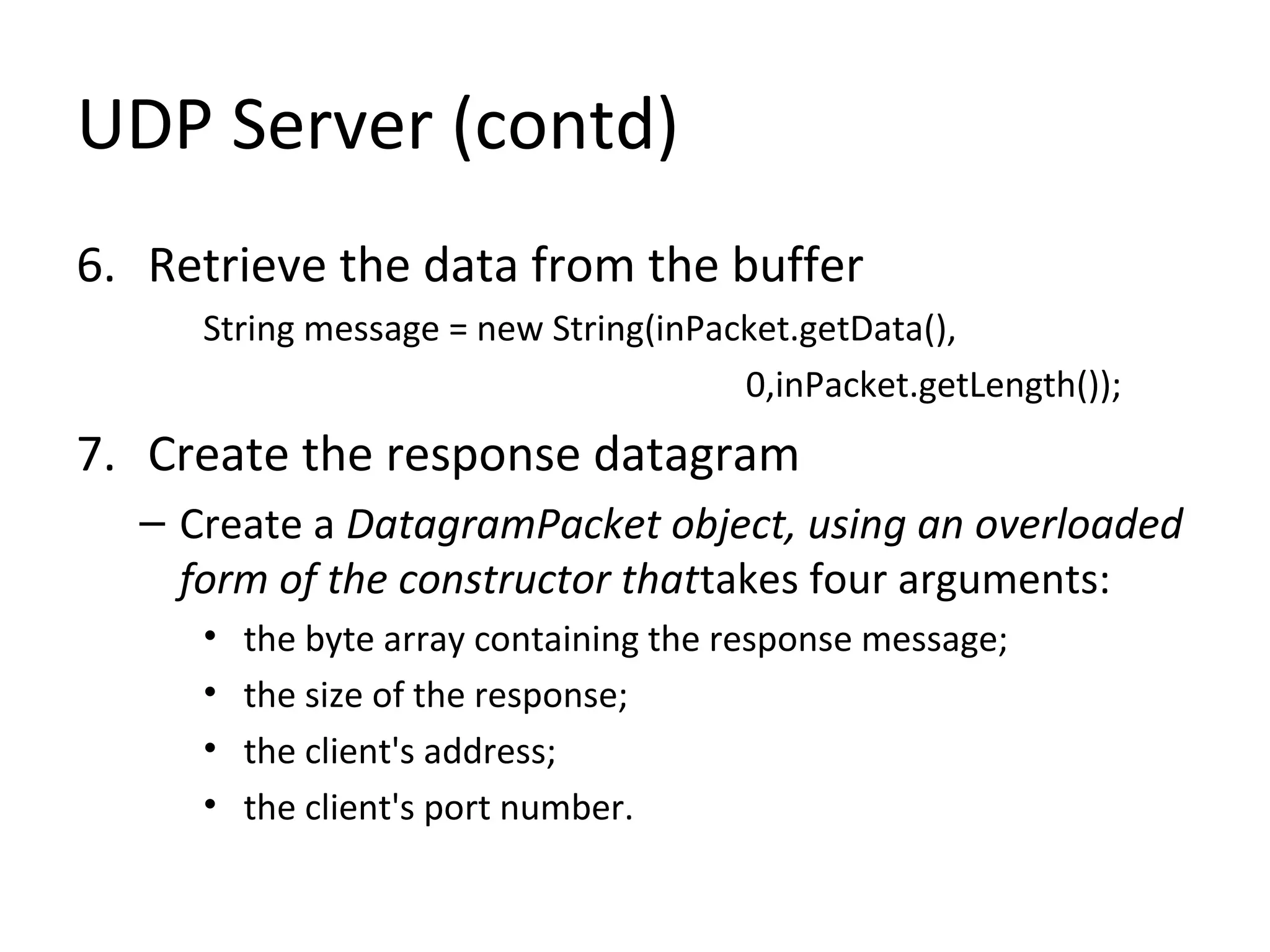
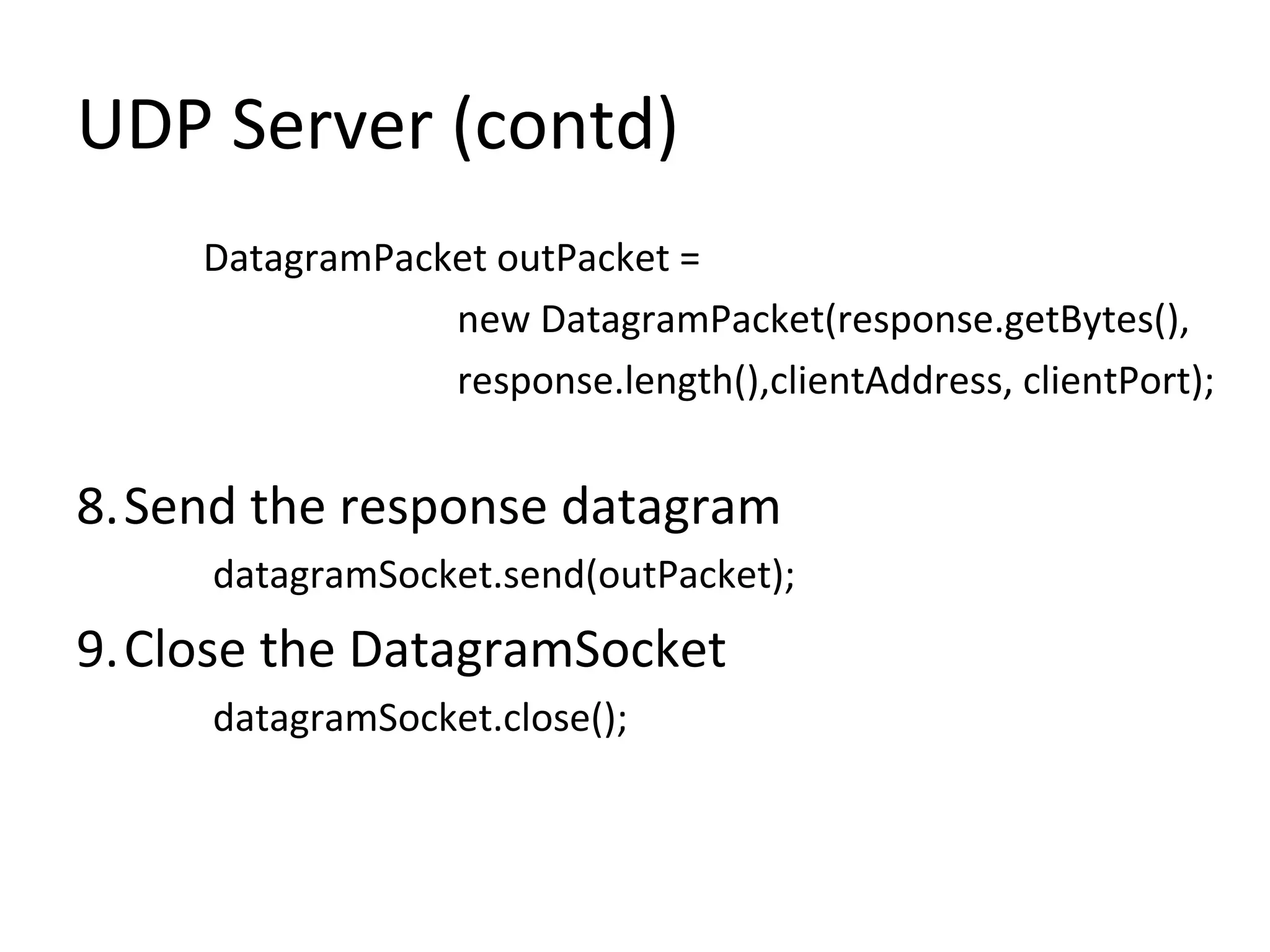
• Process involves the following nine steps
1. Create a DatagramSocket object
DatagramSocket datagramSocket =
new DatagramSocket(1234);
2.Create a buffer for incoming datagrams
byte[] buffer = new byte[256];](https://image.slidesharecdn.com/udp-140411135143-phpapp01/75/Easy-Steps-to-implement-UDP-Server-and-Client-Sockets-4-2048.jpg)

![UDP Client (contd)
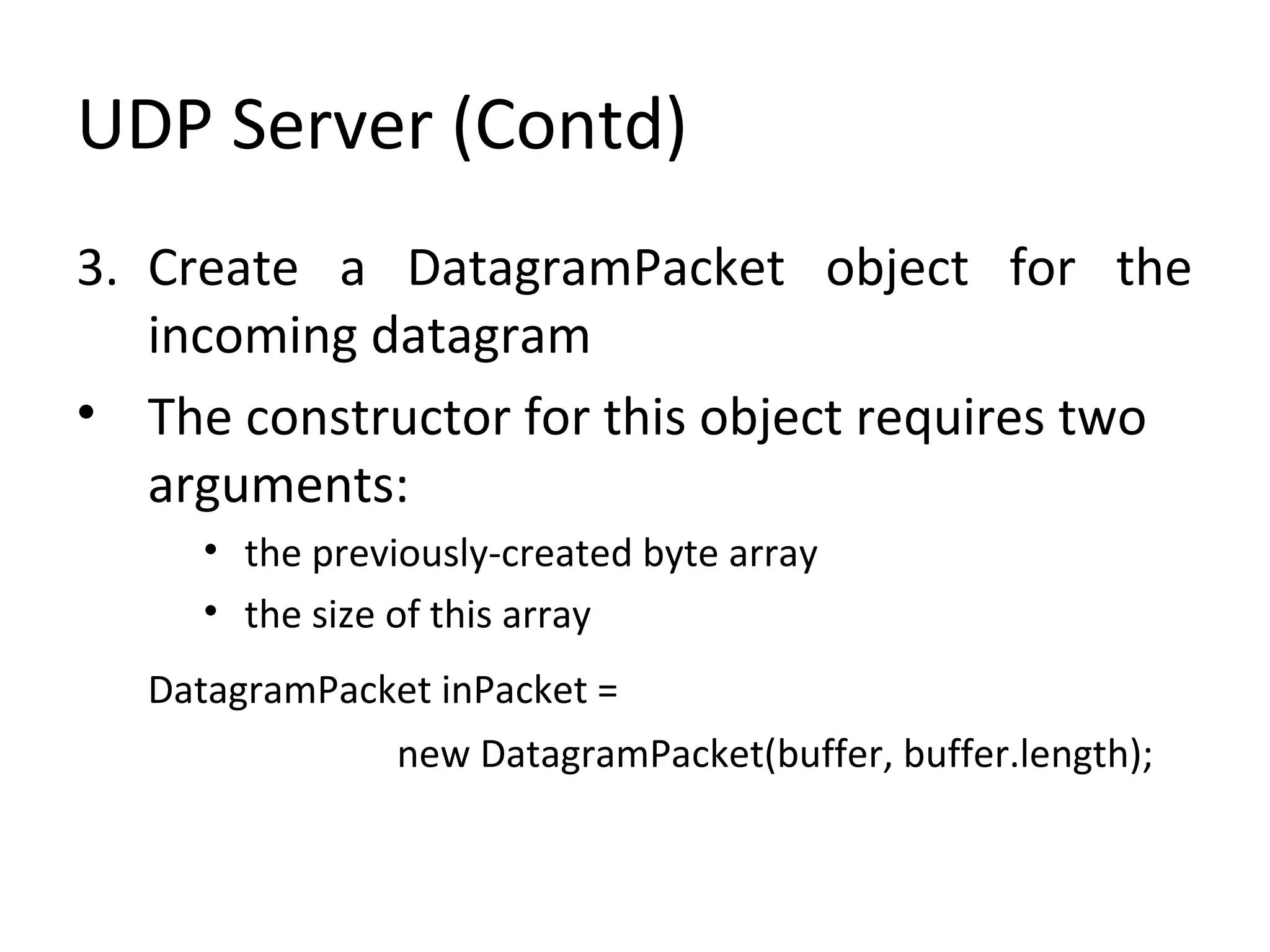
3. Send the datagram message
datagramSocket.send(outPacket);
4. Create a buffer for incoming datagrams
byte[] buffer = new byte[256];
5.Create a DatagramPacket object for the
incoming datagrams
DatagramPacket inPacket =
new DatagramPacket(buffer, buffer.length);](https://image.slidesharecdn.com/udp-140411135143-phpapp01/75/Easy-Steps-to-implement-UDP-Server-and-Client-Sockets-10-2048.jpg)