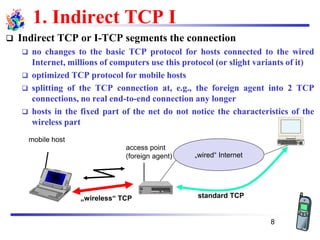
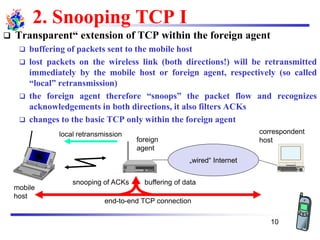
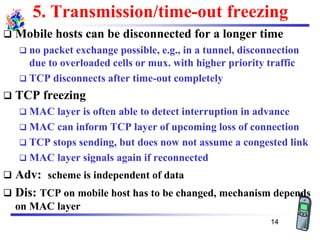
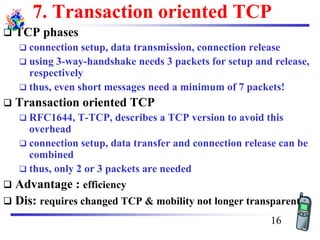
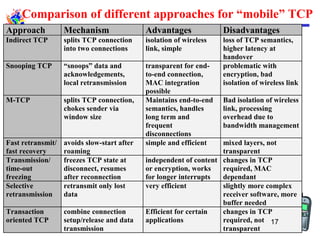
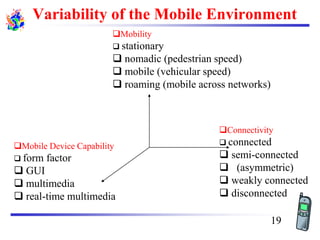
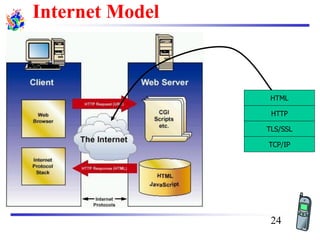
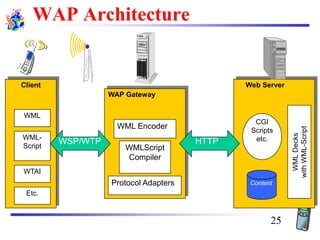
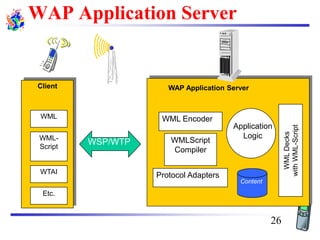
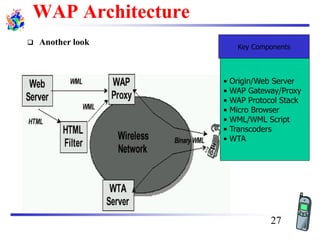
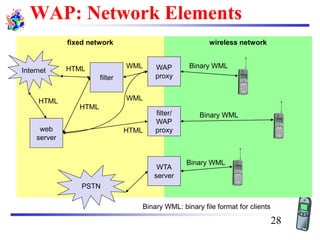
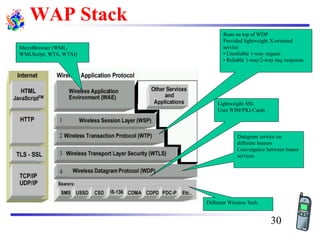
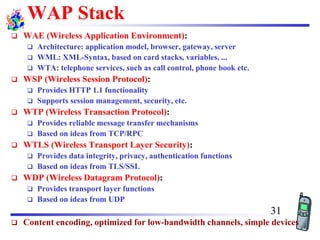
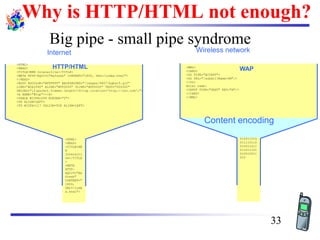
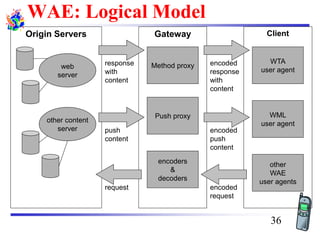
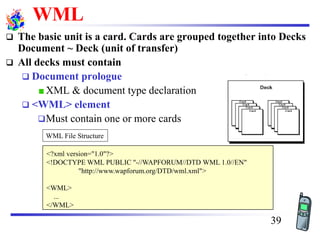
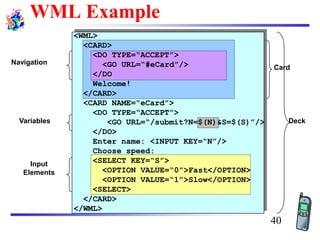
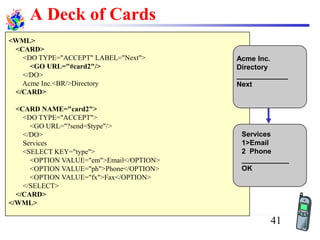
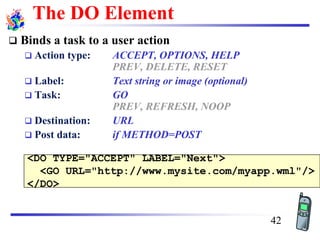
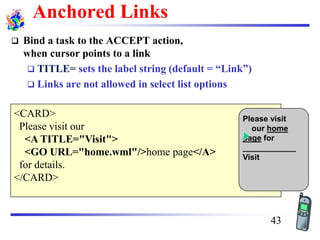
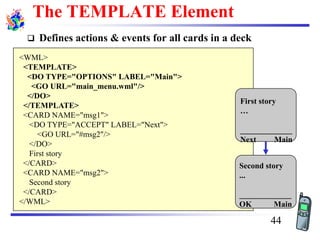
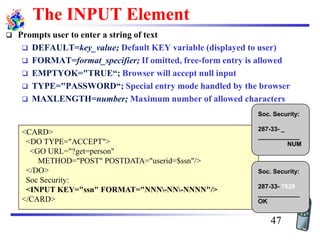
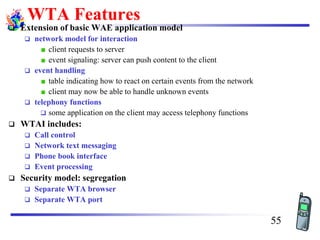
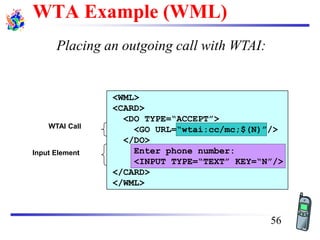
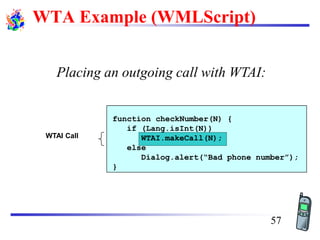
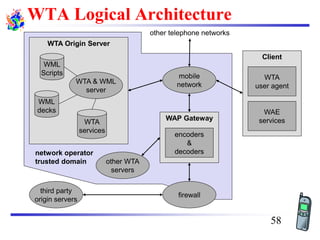
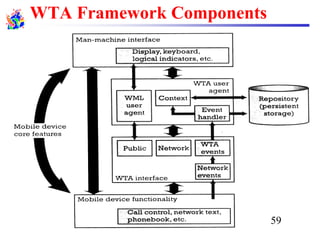
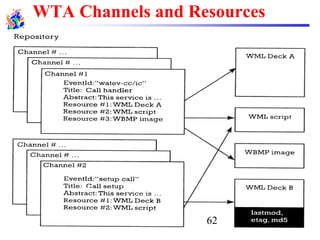
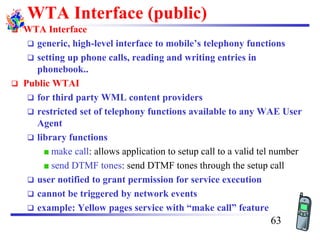
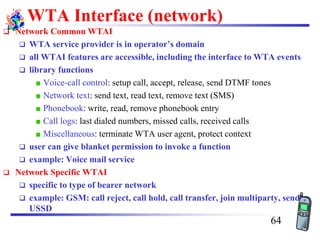
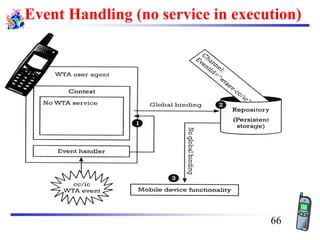
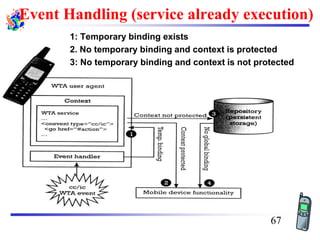
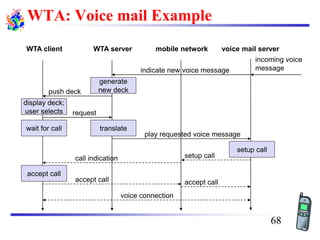
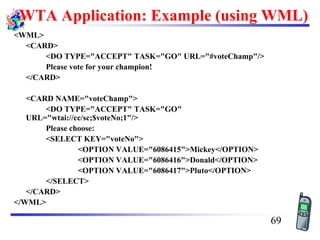
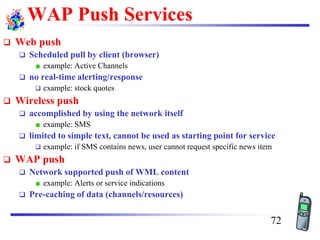
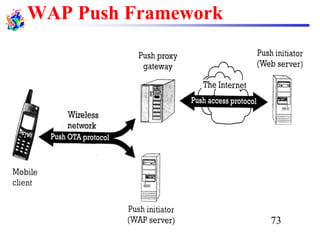
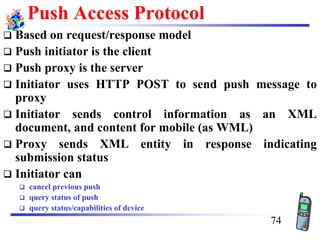
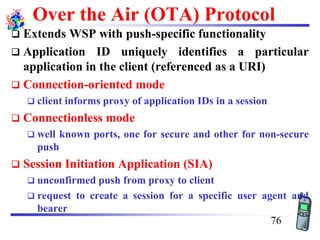
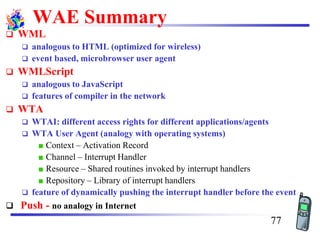
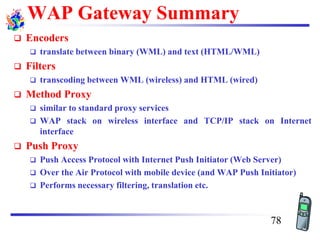
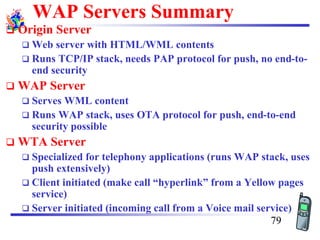
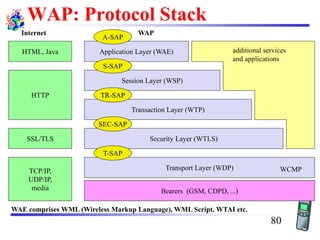
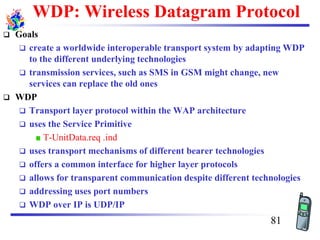
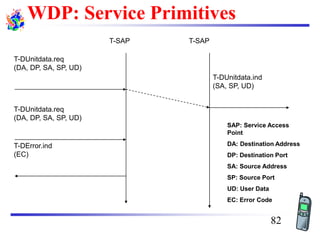
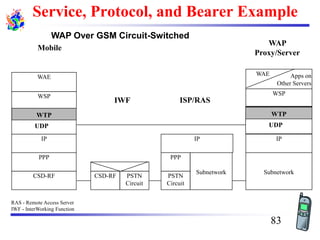
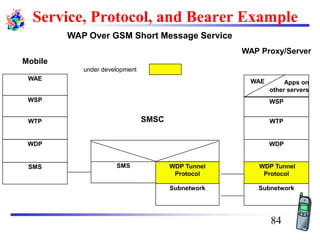
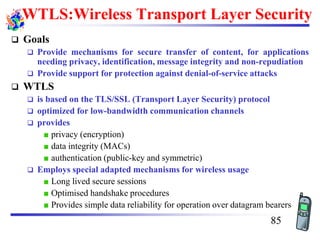
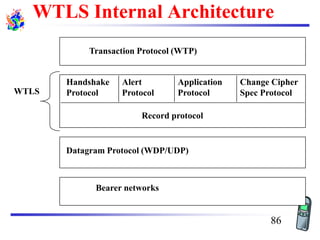
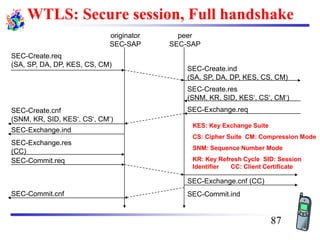
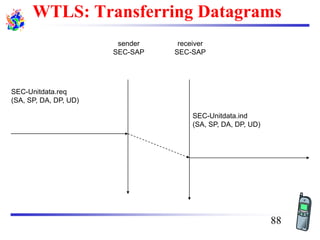
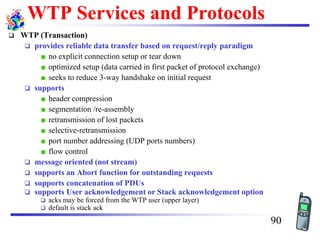
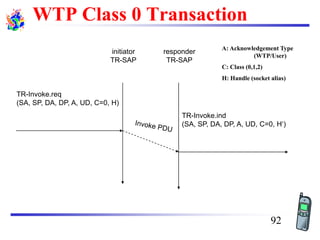
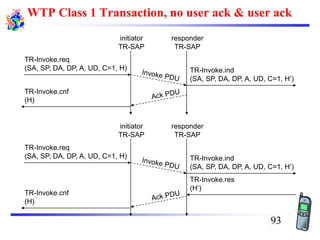
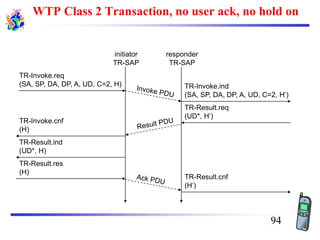
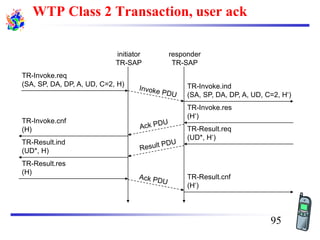
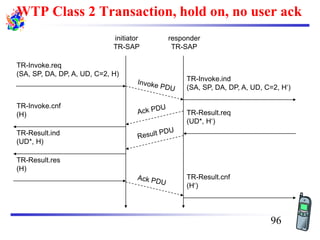
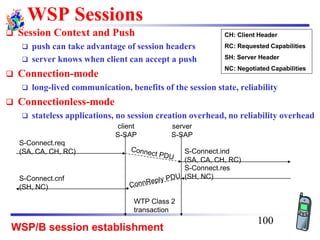
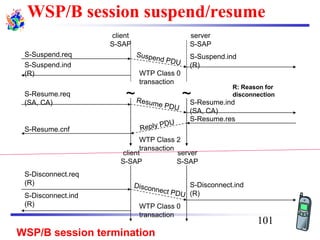
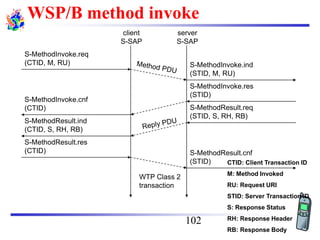
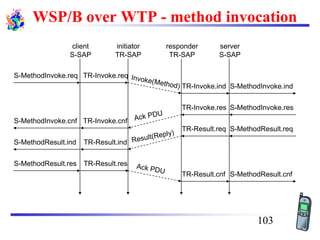
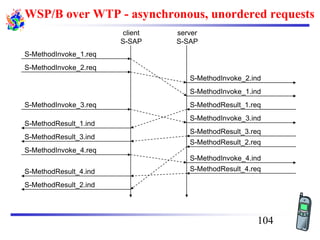
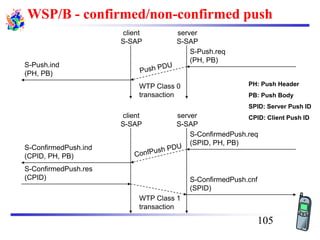
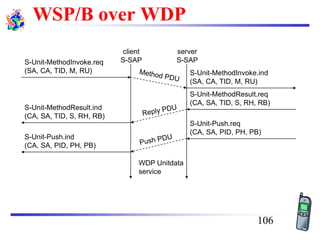
The document discusses mobile transport and application layer technologies, focusing on TCP adaptations for mobile environments, such as Indirect TCP, Snooping TCP, and Mobile TCP. It highlights challenges such as packet loss due to mobility, presenting various proposals to enhance TCP performance in mobile networks. Additionally, it covers the Wireless Application Protocol (WAP), emphasizing its role in enabling internet access from mobile devices and the architectural components necessary for its implementation.