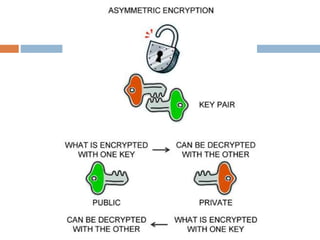
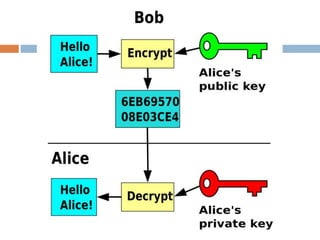
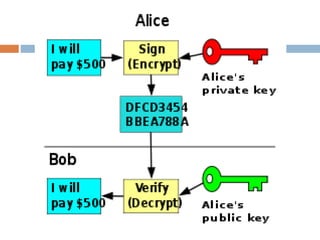
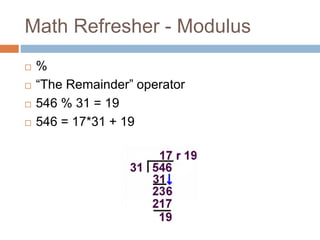
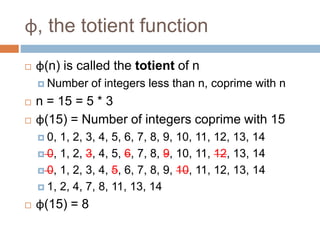
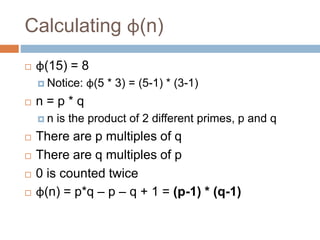
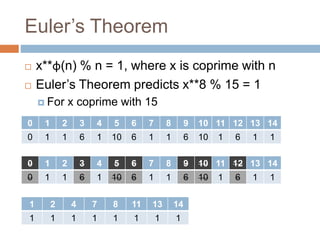
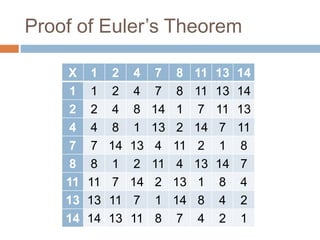
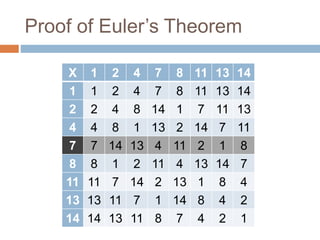
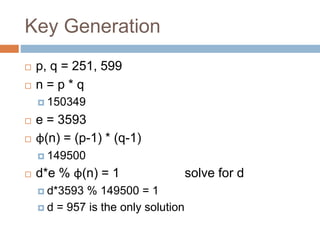
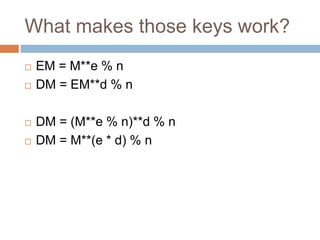
The document provides an overview of RSA encryption, explaining its functionality as a public key cryptography scheme. It delves into the mathematical principles behind RSA, such as modulus, prime factorization, Euler's theorem, and how to generate public and private keys. The document also discusses the security of RSA, emphasizing the challenges involved in deriving the private key from the public key and the difficulty of solving encrypted messages.