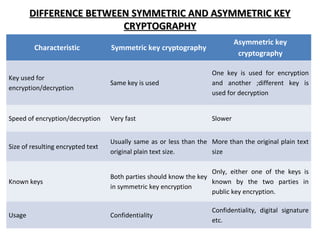
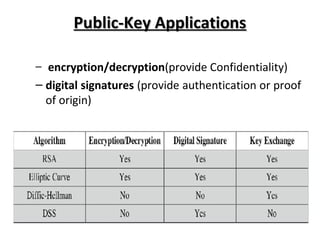
The document presents an overview of public key cryptography and the RSA algorithm, detailing the principles of encryption and decryption, the distinction between symmetric and asymmetric key cryptography, and the mathematical foundations of RSA. It describes the RSA algorithm's steps for key generation, encryption, and decryption, and discusses its practical applications in securing web traffic, emails, and remote connections. Despite RSA's popularity and advantages in security, it faces challenges such as slow key generation and decryption compared to symmetric key systems like DES.






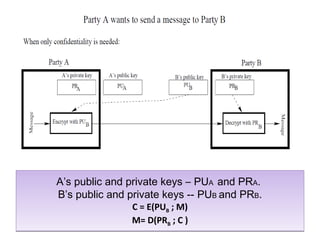

![A’s public and private keys – PUA and PRA.
B’s public and private keys - PUB and PRB.
C = E[PUB ; E(PRA ; M)]
M = D[PUA ; D(PRB ; C)]
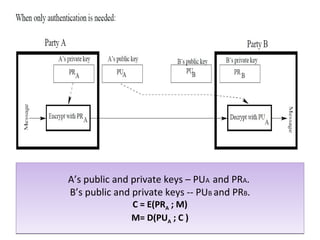
A’s public and private keys – PUA and PRA.
B’s public and private keys - PUB and PRB.
C = E[PUB ; E(PRA ; M)]
M = D[PUA ; D(PRB ; C)]](https://image.slidesharecdn.com/submittedby-2-160830042555/85/Public-Key-Cryptography-and-RSA-algorithm-11-320.jpg)


![RSA ALGORITHMRSA ALGORITHM
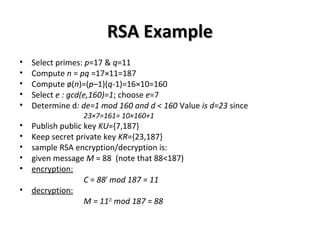
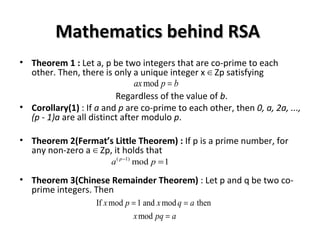
• Choose two large prime numbers p and q randomly
• Let n = pq.
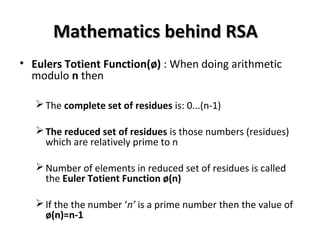
• Let (n)ɸ = (p - 1)(q - 1).
• Choose a large number e ϵ [2, -1]ɸ that is co-prime to (n)ɸ .
• Compute d [2, -1]ɸ such that
ed mod (n) = 1 or ed = k× (n)+1ɸ ɸ
There is a unique such d. Furthermore, d must be co-prime to (n)ɸ
• Announce to the whole word the pair (e; n), which is his public key.
• Keep the pair (d; n) secret to himself, which is his private key
• Sender will now use the public key to encrypt the message M as follows
C = Me
mod n. Here, C is the encrypted message.
• Receiver will use its own private key to decrypt the message by using the equation
M=Cd
mod n](https://image.slidesharecdn.com/submittedby-2-160830042555/85/Public-Key-Cryptography-and-RSA-algorithm-18-320.jpg)