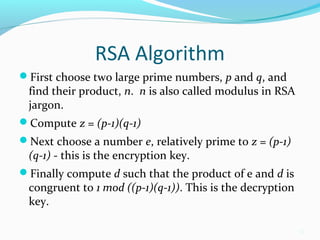
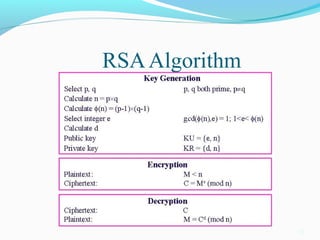
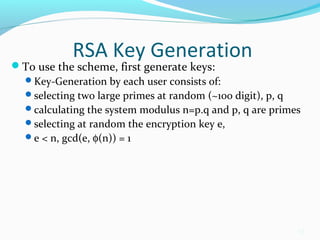
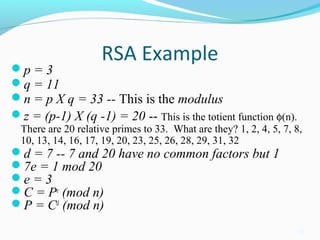
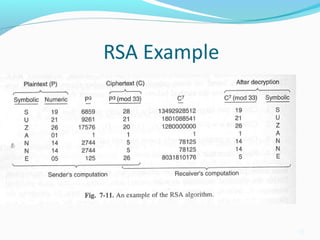
The document provides an overview of the RSA public key encryption algorithm. It discusses how RSA uses a public key and private key pair, with the public key used to encrypt messages and the private key used to decrypt them. The security of RSA relies on the difficulty of factoring the product of two large prime numbers. The document outlines the RSA algorithm steps of key generation, encryption, and decryption. It also discusses RSA applications, standardization, speed, weaknesses, and history.