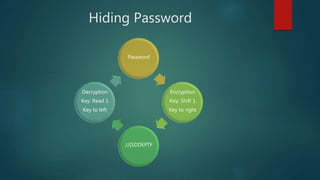
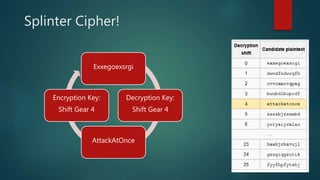
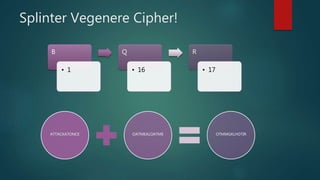
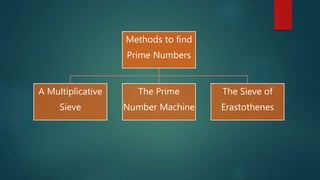
This document provides an introduction to cryptography. It discusses how cryptography is essential for secure communication on the internet. It then covers the history of cryptography from its first documented uses in ancient Egypt through its importance in World War II. It defines cryptography terms and describes encryption and decryption. It also summarizes some classical cryptography techniques like the Caesar cipher and discusses concepts like prime numbers and the RSA encryption algorithm.