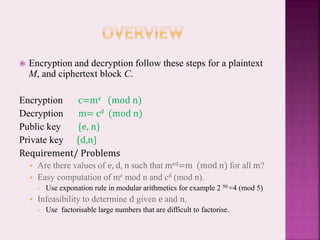
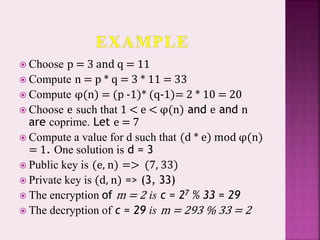
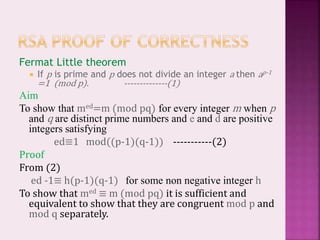
The RSA algorithm is a widely used public-key encryption technique developed in 1977. It uses a public and private key pair based on the difficulty of factoring large prime numbers. The encryption of a message m involves computing c = me mod n, where e is the public key exponent and n is the product of two large primes. Decryption gets the original message by computing m = cd mod n, where d is the private key exponent. For the encryption and decryption to be reversible, d is chosen such that ed = 1 mod φ(n), where φ is Euler's totient function.