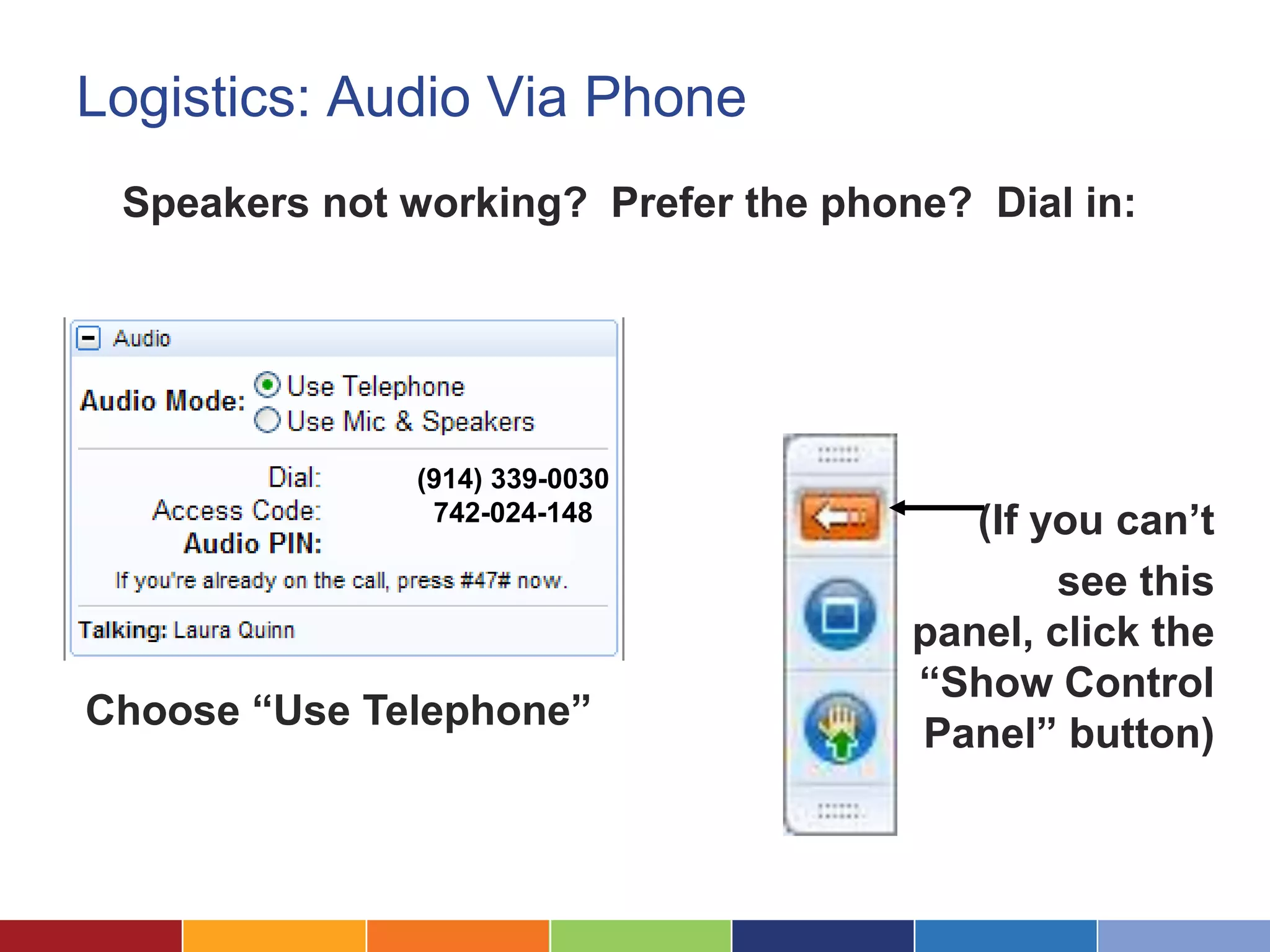
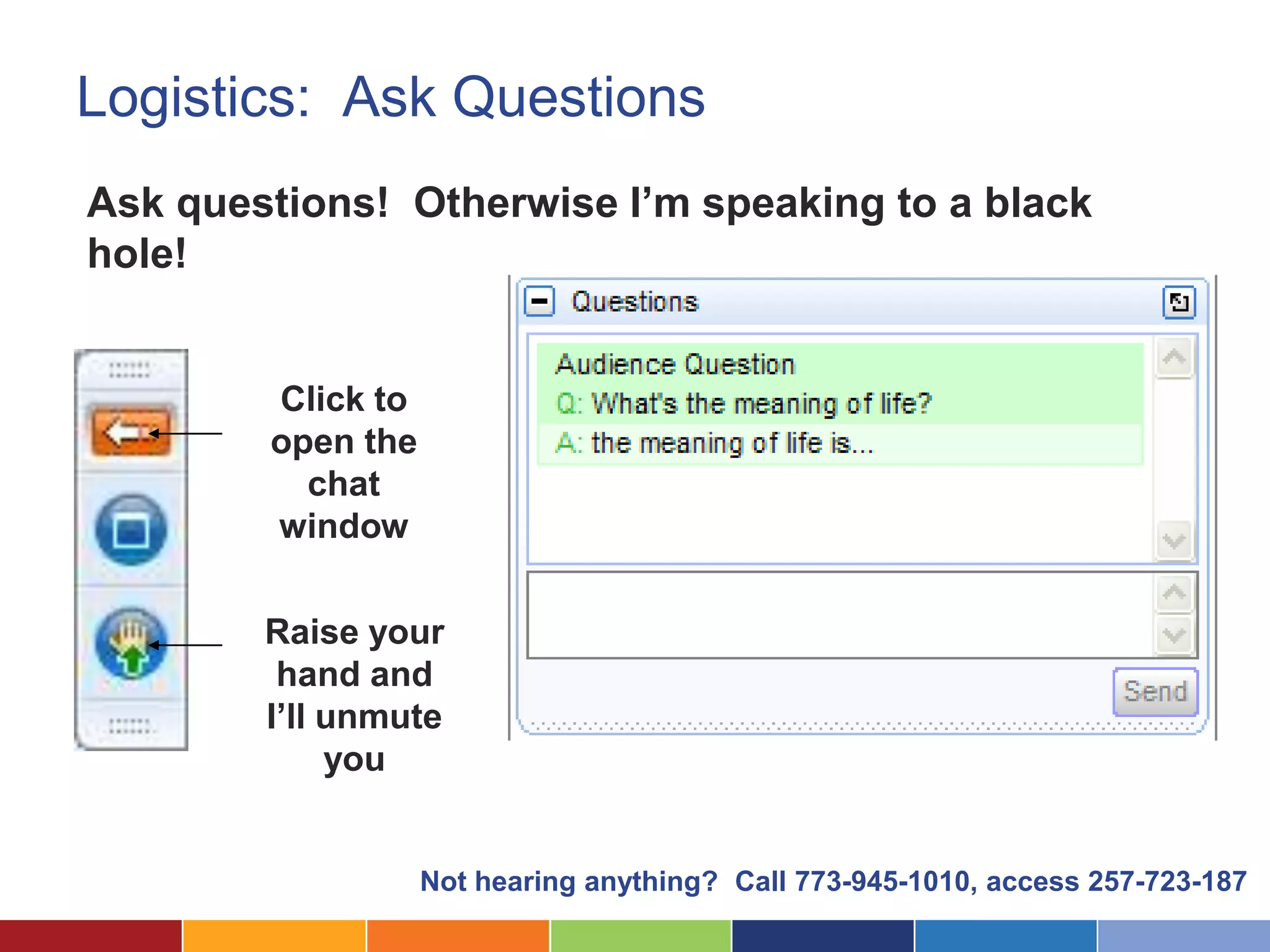
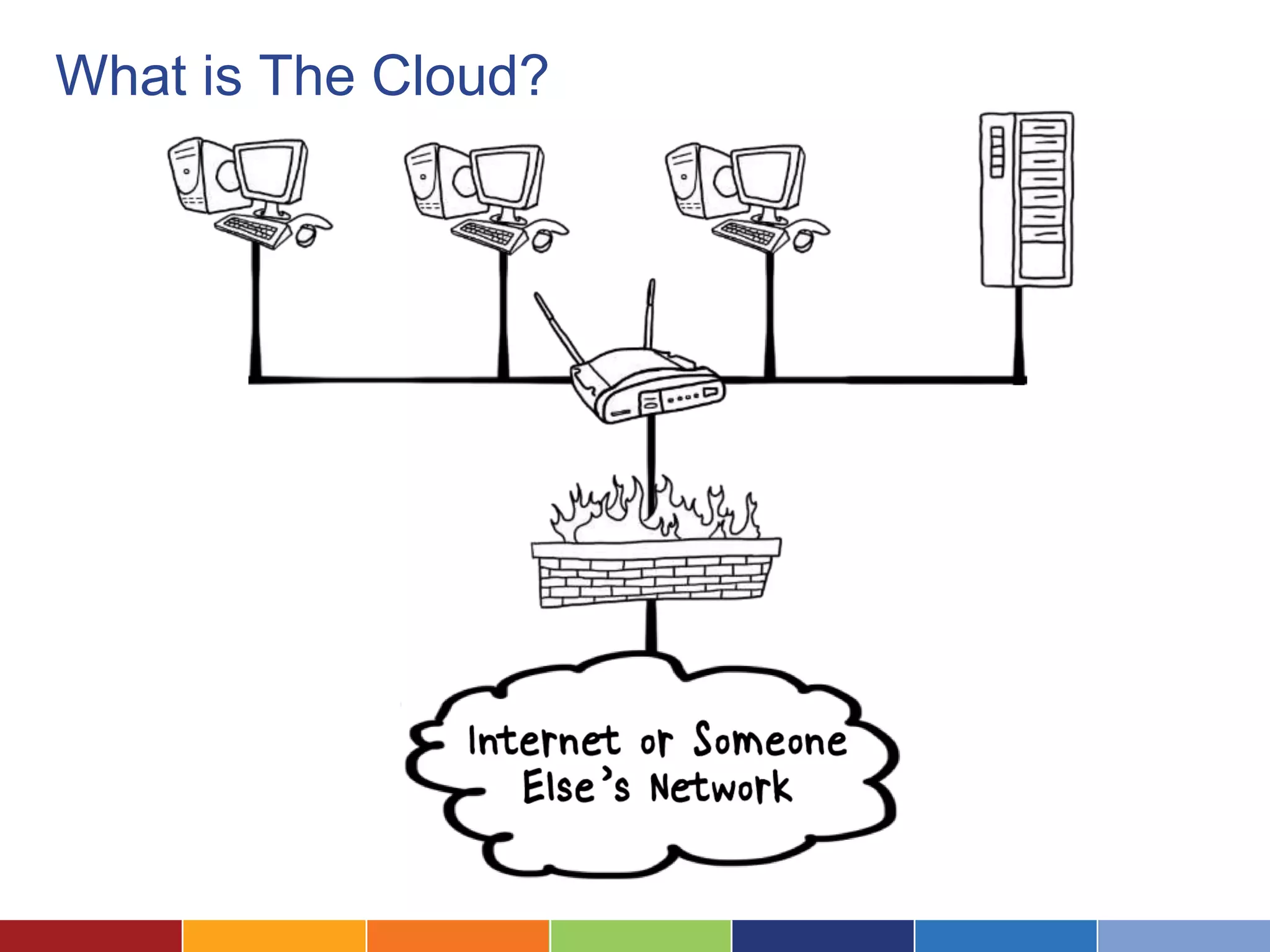
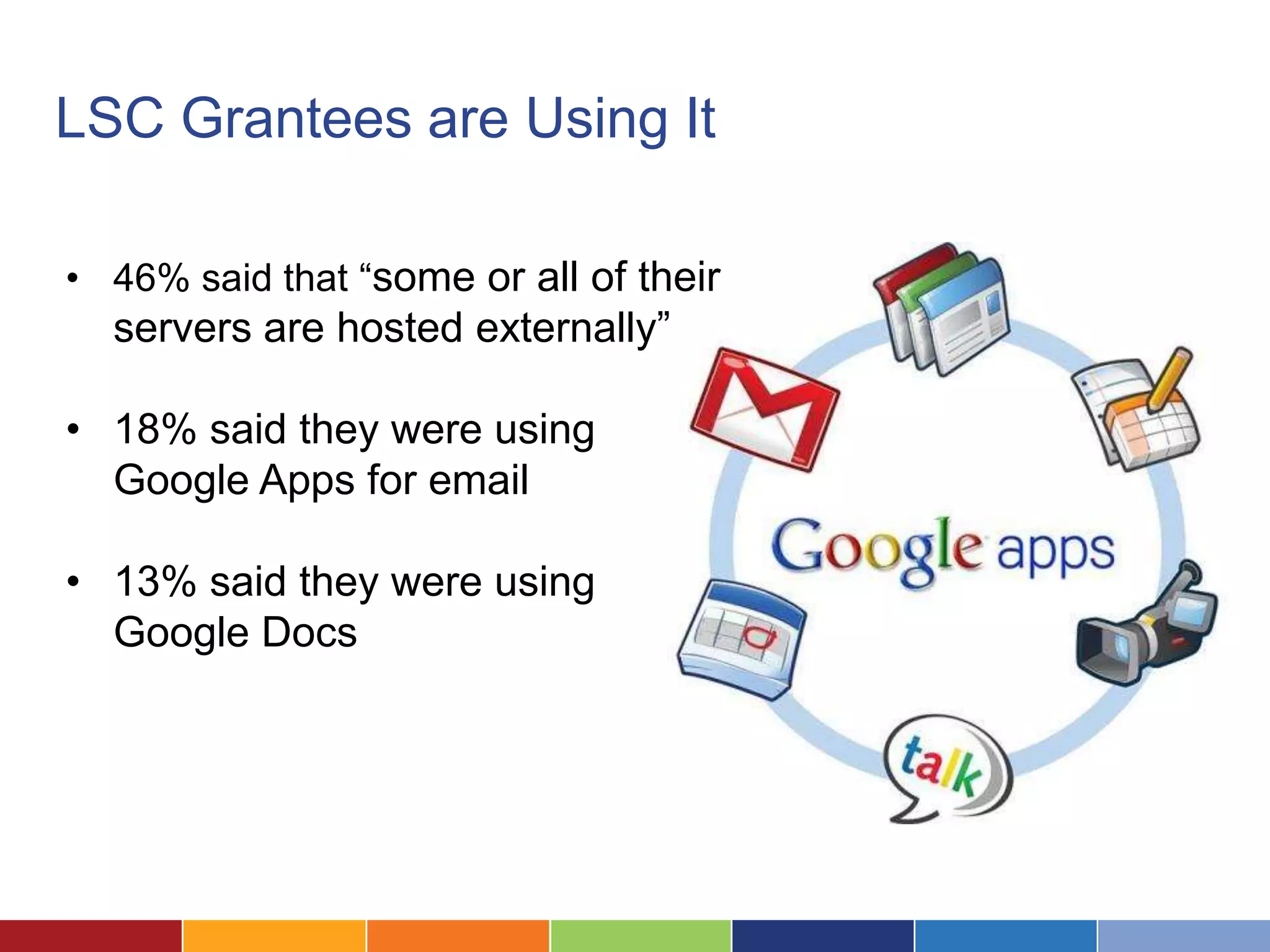
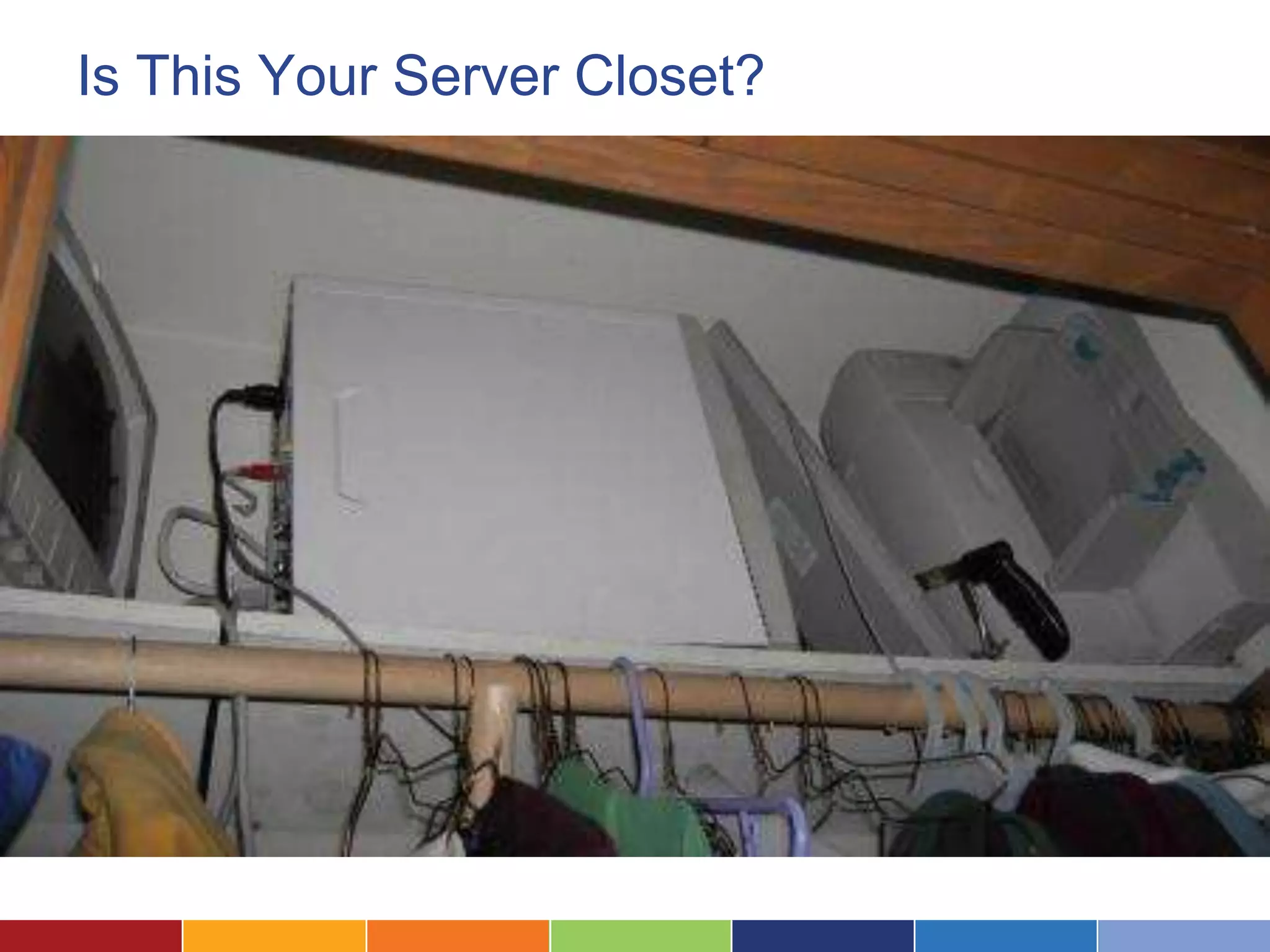
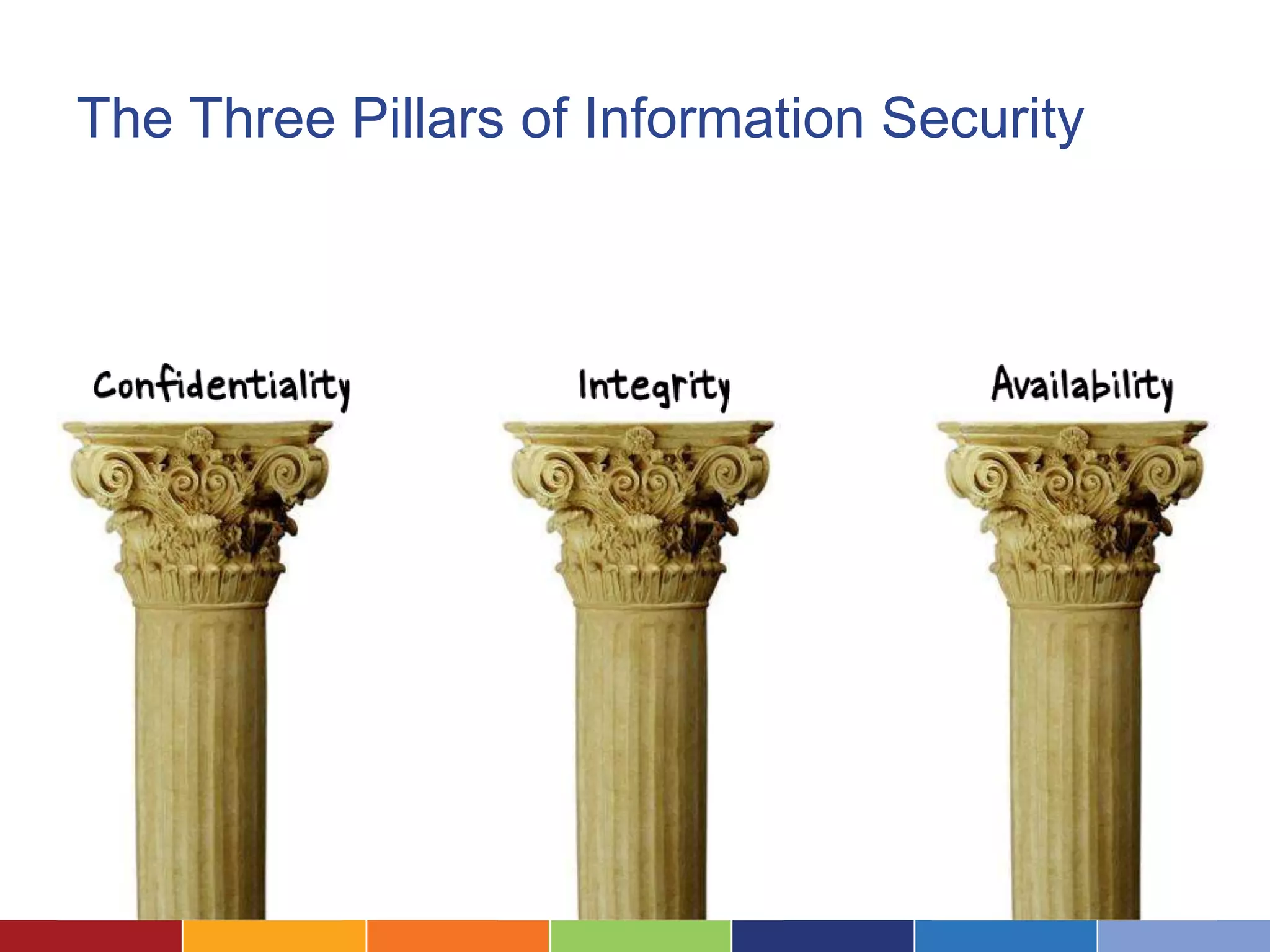
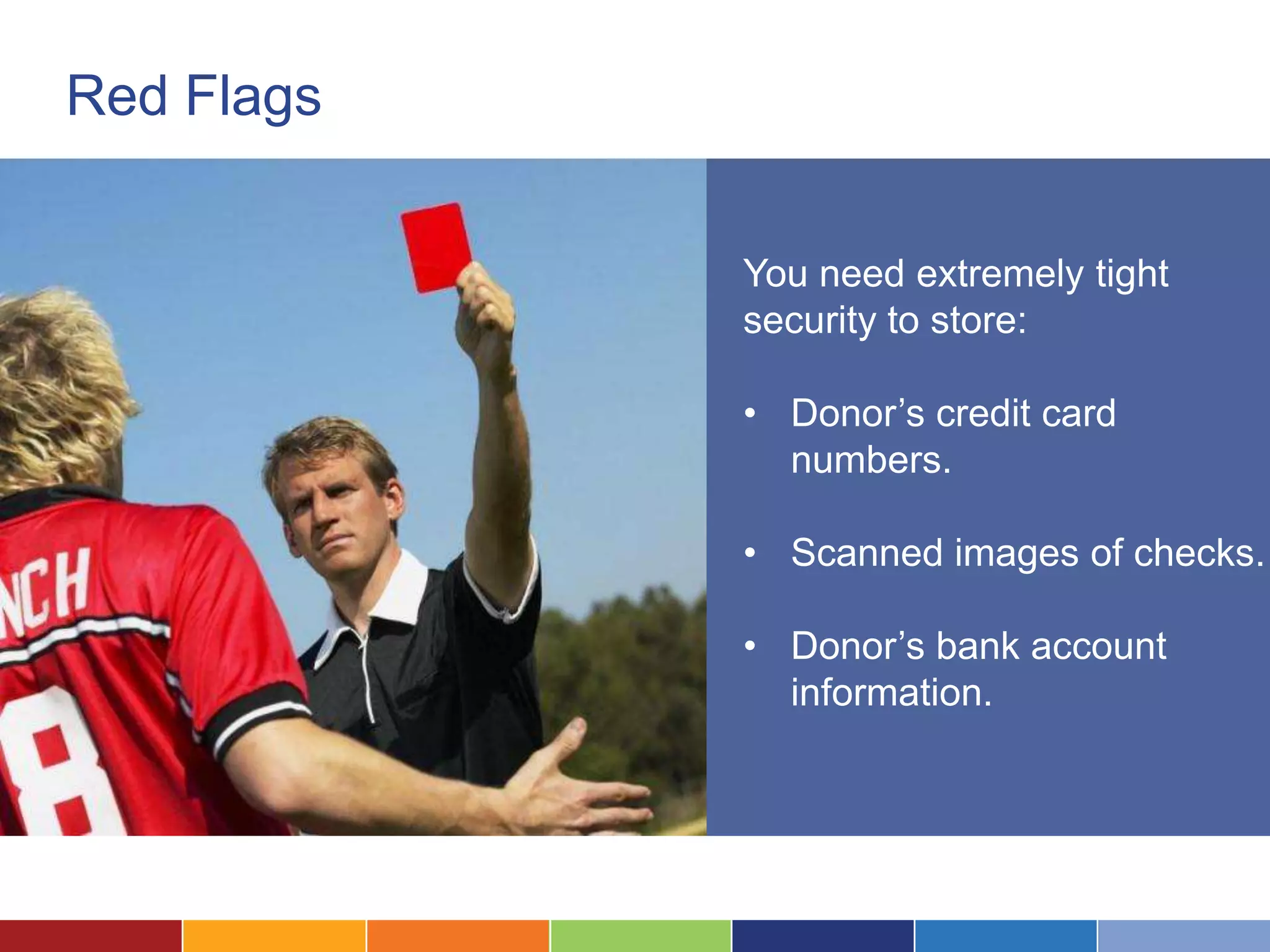
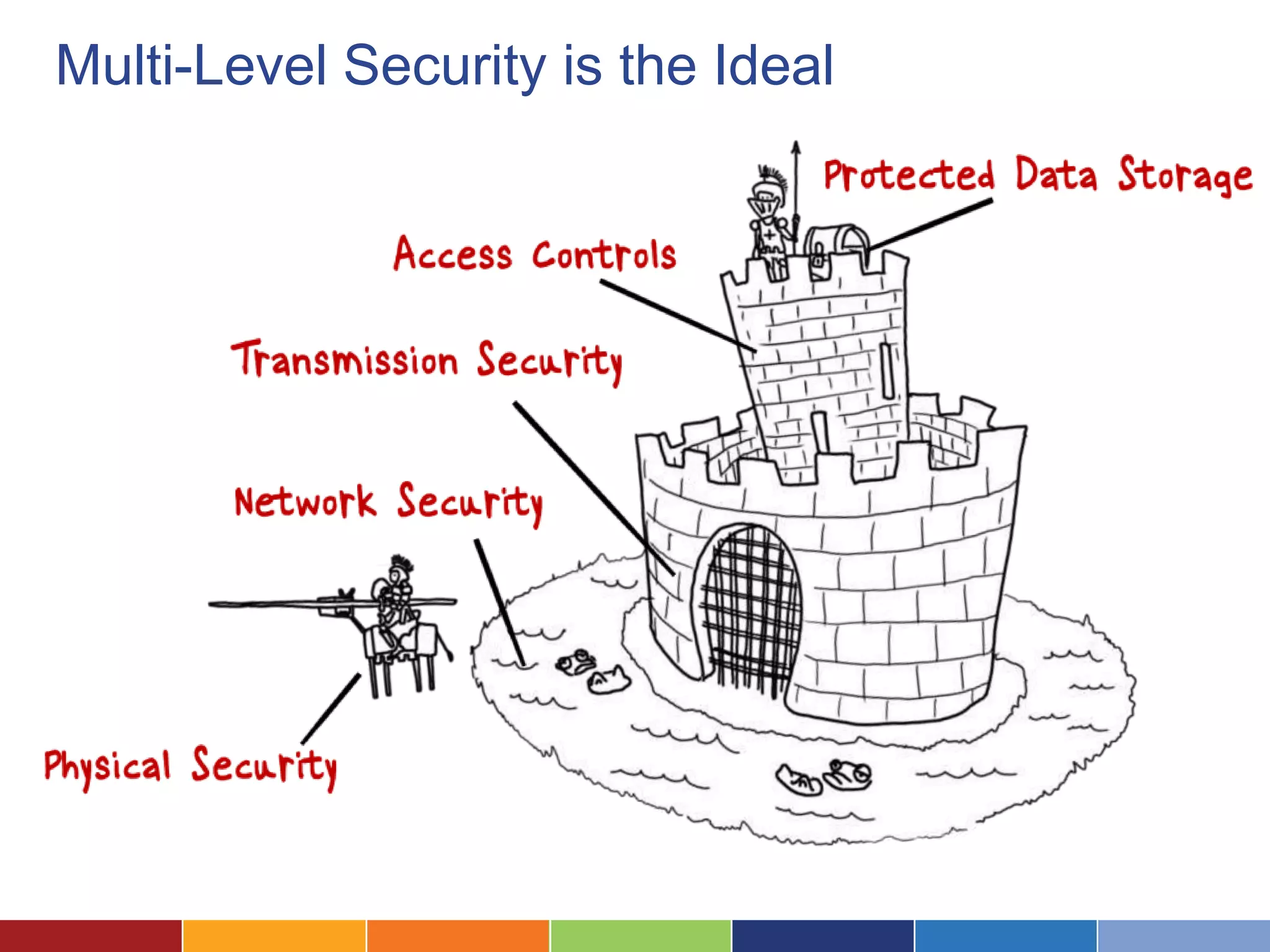
The document discusses the security considerations for organizations considering storing data in the cloud. It notes that while the cloud offers benefits like low costs and easy remote access, organizations must ensure their data is properly secured. The cloud can be secure if a vendor takes security seriously and maintains practices like strong access controls, data encryption, regular backups, and compliance with standards like SAS70, SSAE16 and PCI DSS. Overall, an organization's data is only as secure as the protections put in place, and choosing a security-focused cloud vendor can help safeguard confidential information in the cloud.