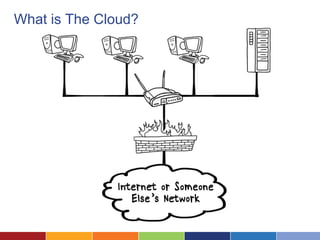
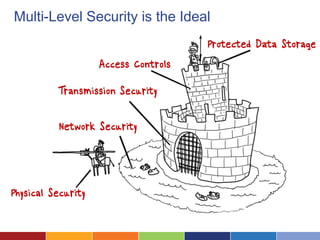
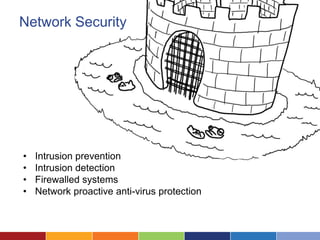
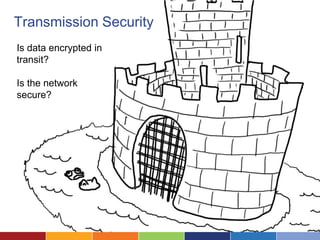
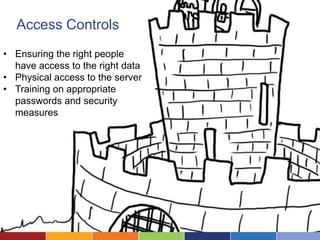
The document discusses cloud computing's advantages, such as low cost and easy access, while highlighting security concerns organizations face. It differentiates types of cloud services (SaaS, hosted private cloud, and co-located private cloud) and emphasizes the importance of understanding data sensitivity and implementing strong security practices. Ultimately, it suggests organizations assess vendor security standards and consider the true value of their data when making decisions about cloud storage.