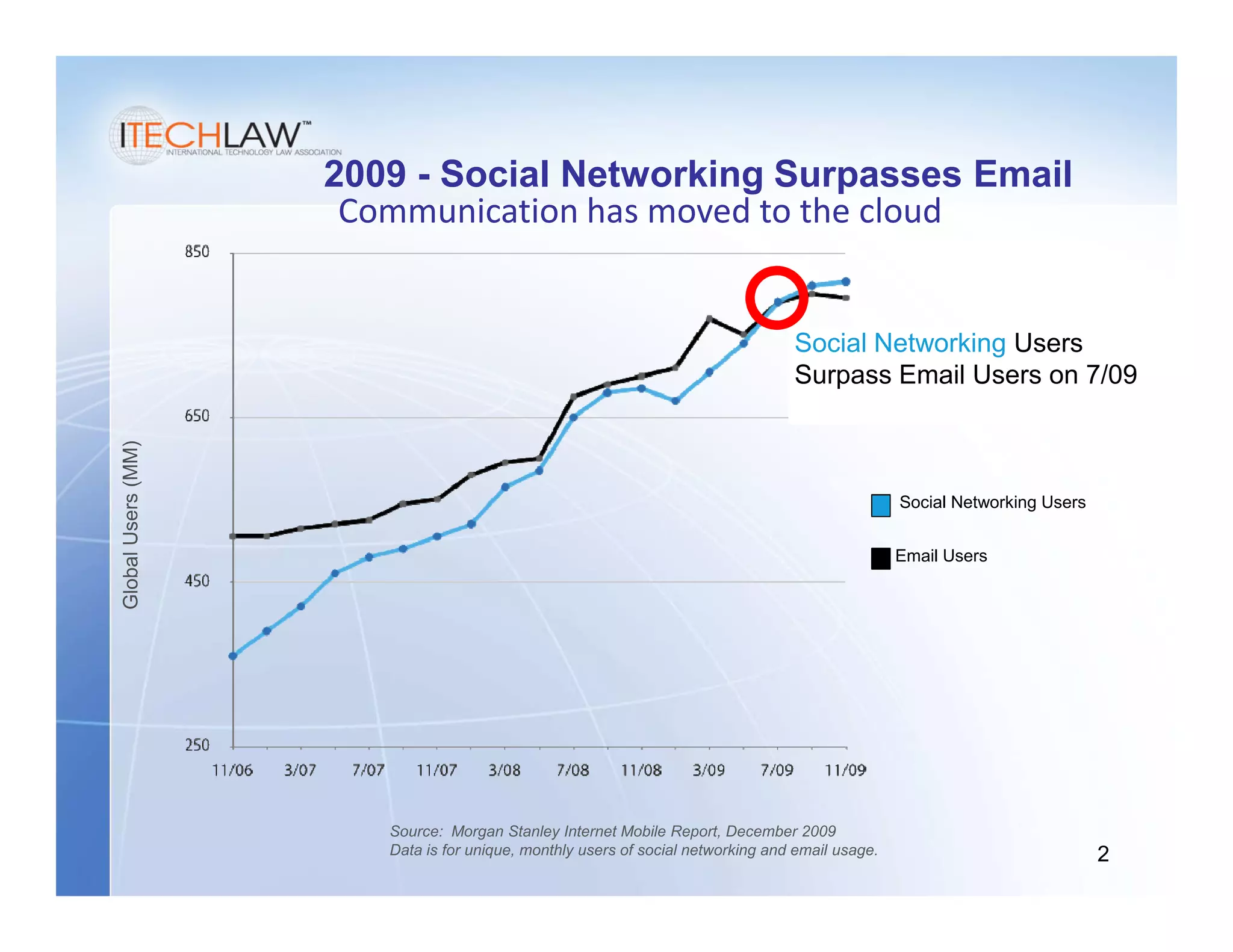
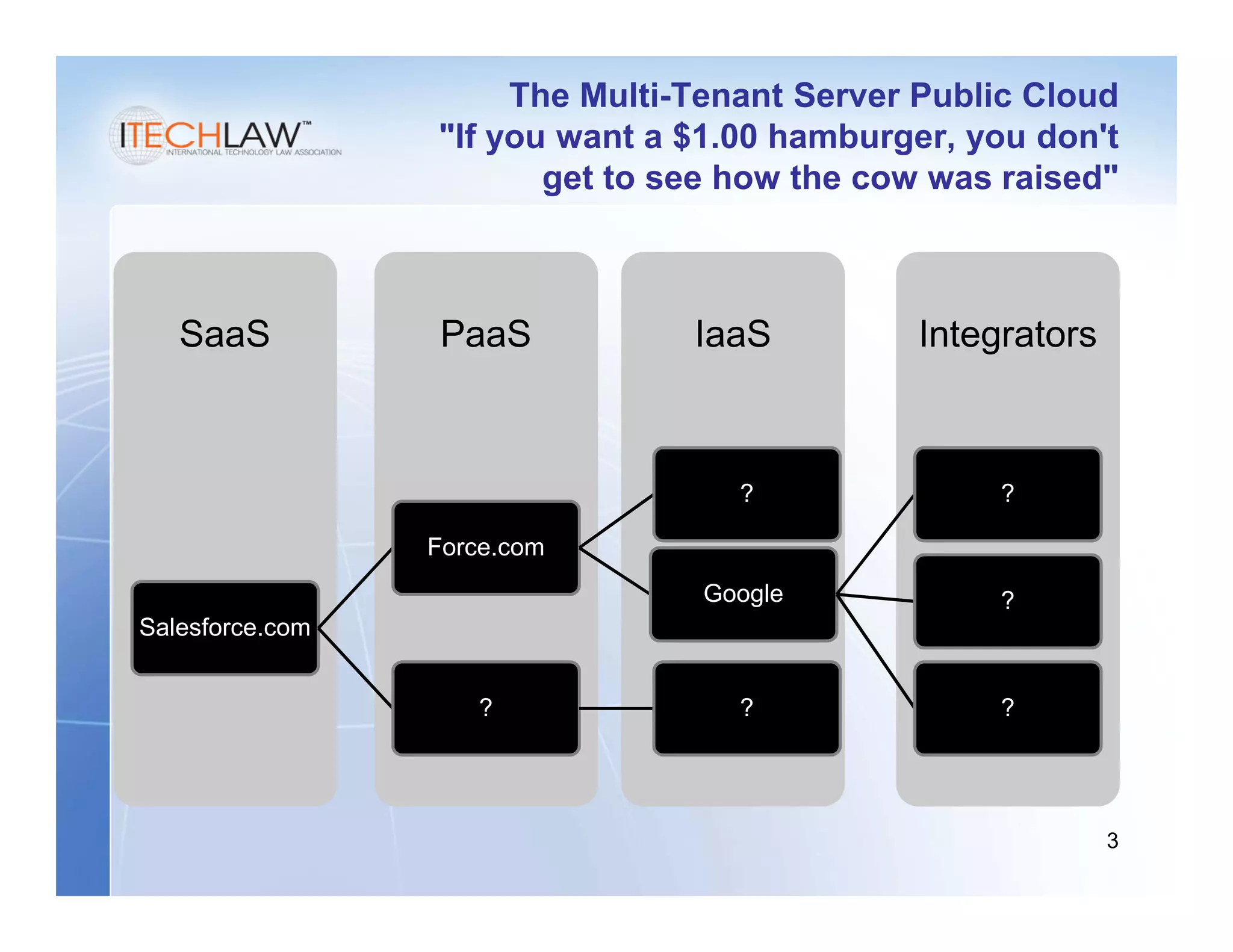
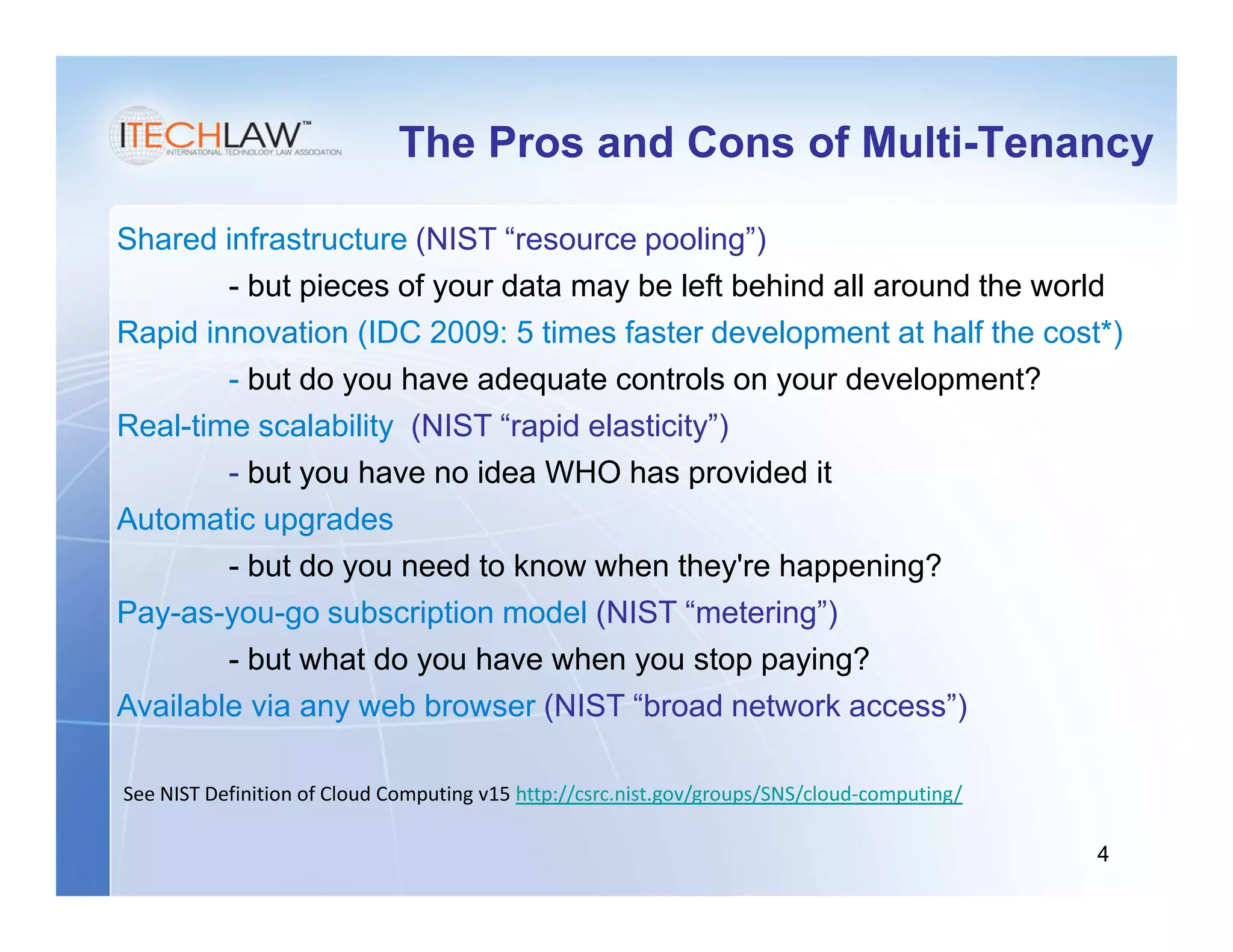
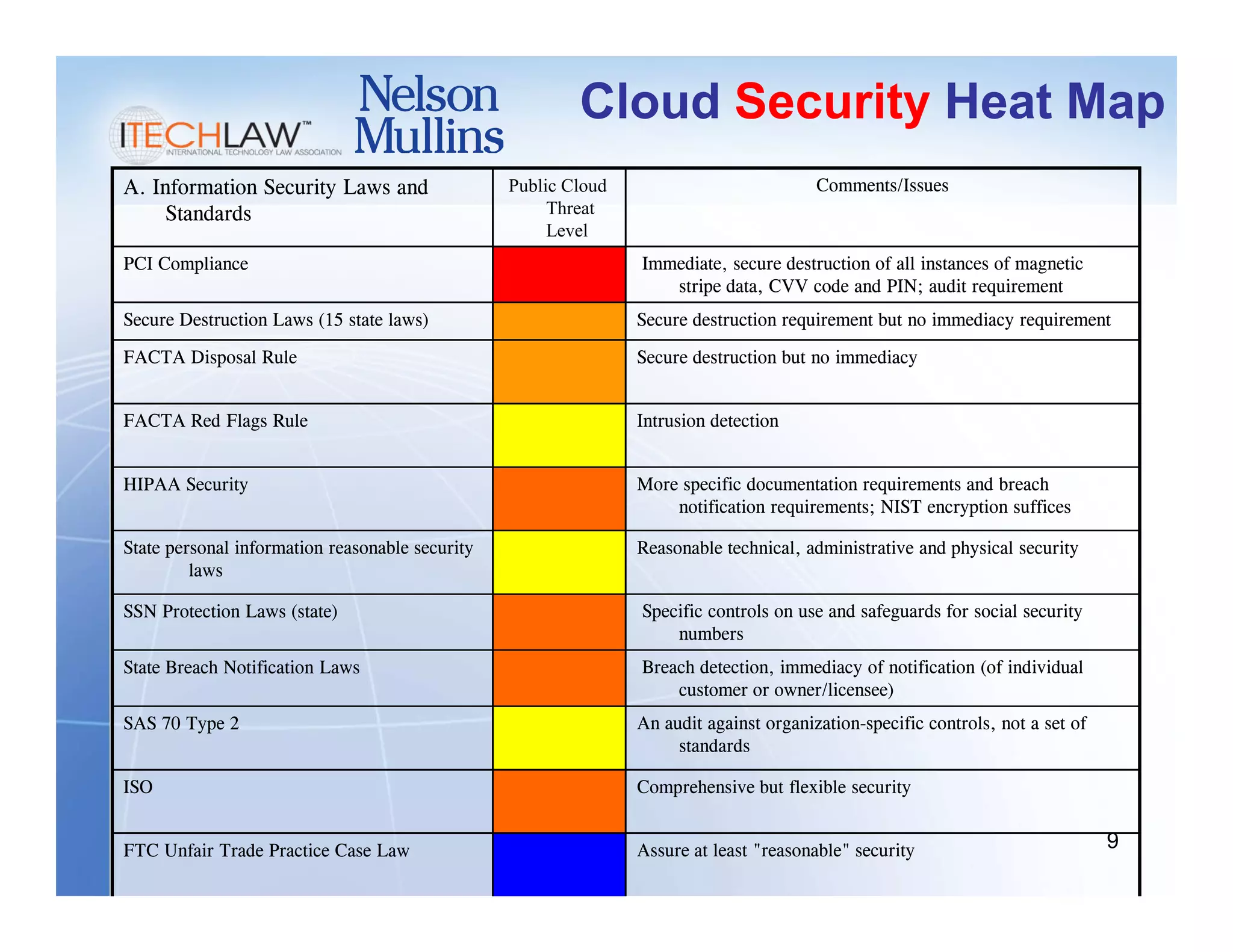
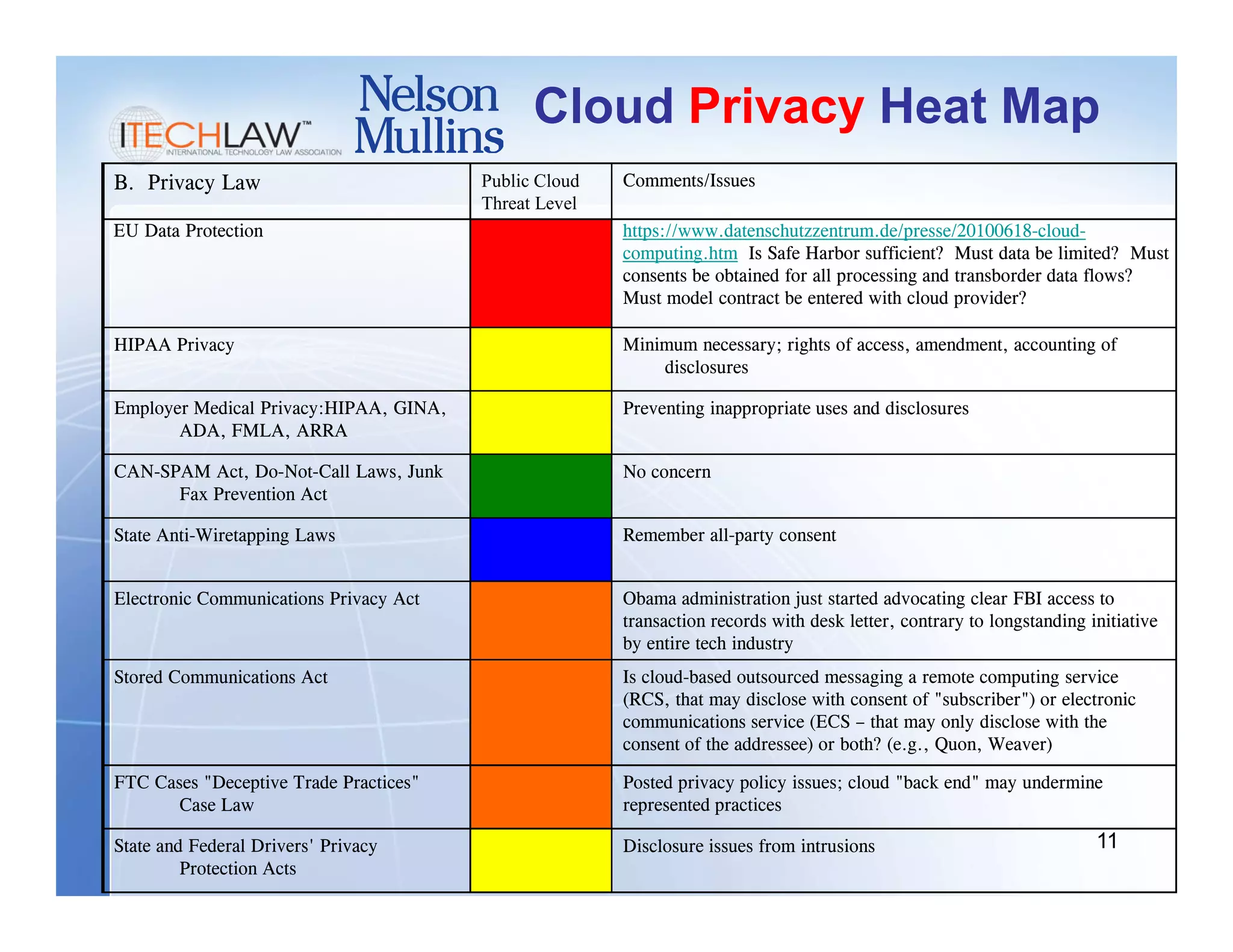
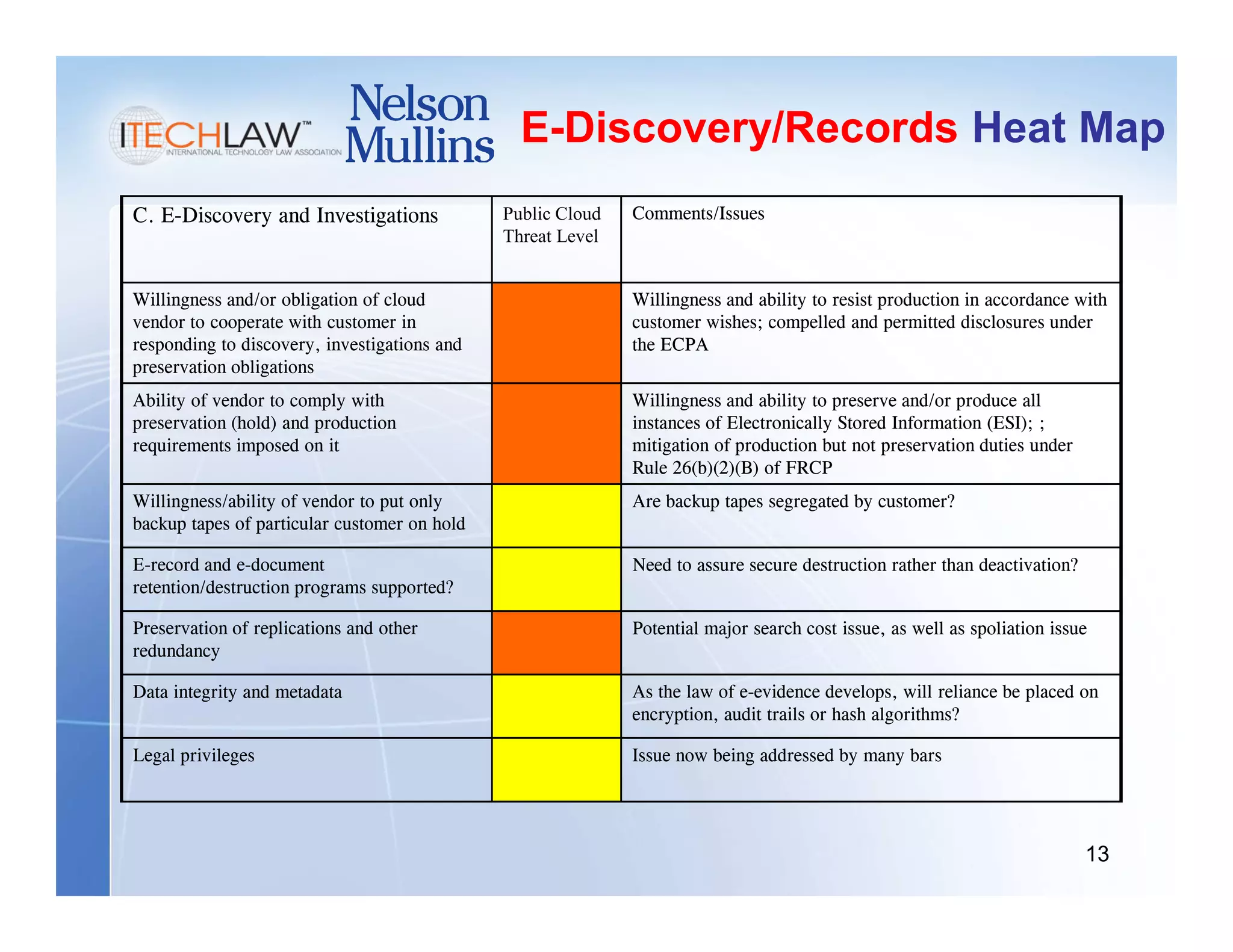
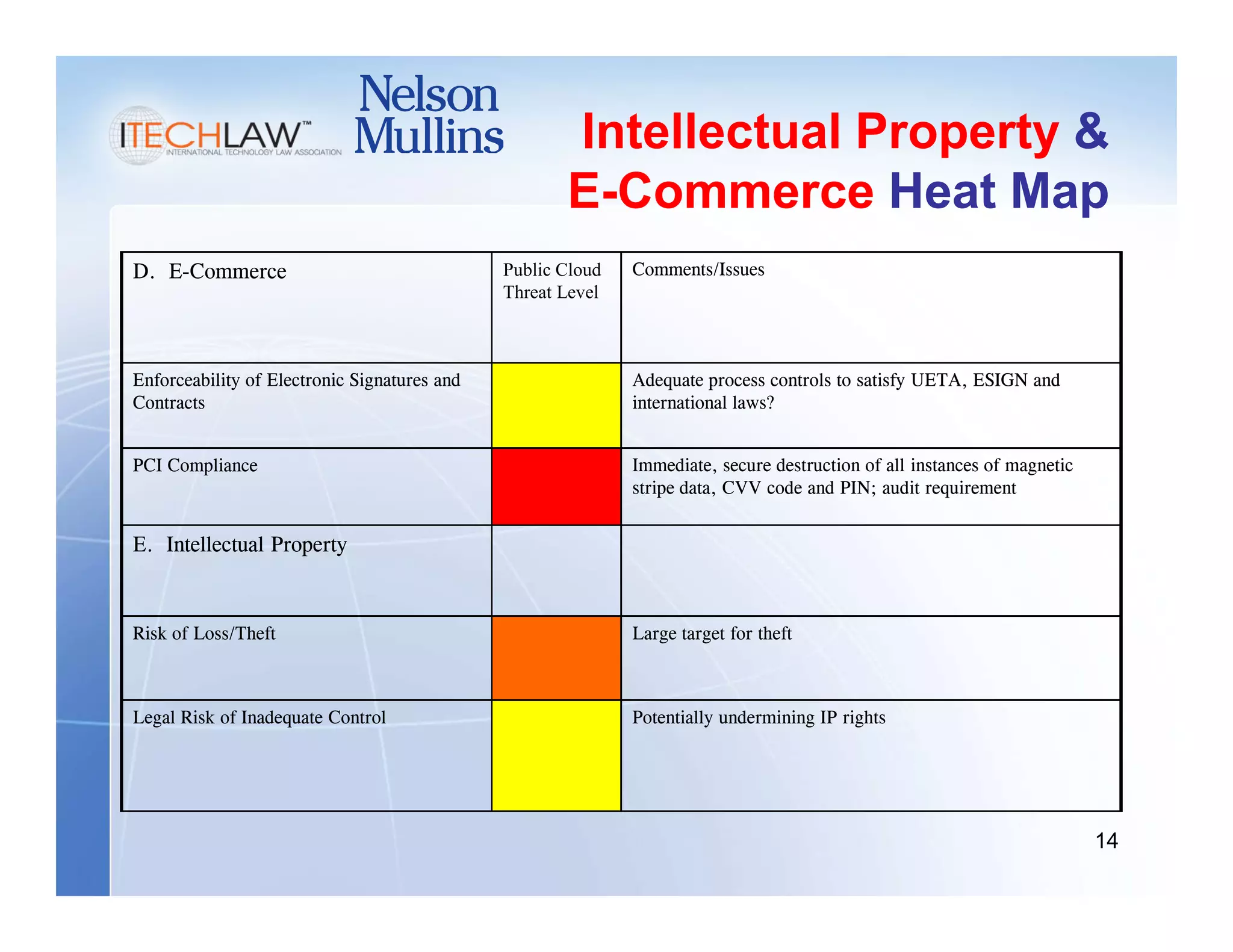
This document summarizes a presentation on managing legal and risk issues of cloud computing. It discusses key topics like social networking surpassing email, multi-tenant server models, security breach risks, encryption concerns, and e-discovery obligations in cloud environments. Overall, the presentation outlines major legal considerations and best practices for organizations adopting cloud computing.