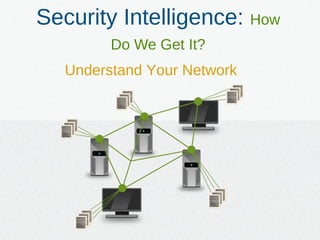
The document discusses the importance of security intelligence in identifying and addressing cyber attacks, highlighting that traditional tools are often inadequate. It emphasizes the need for a behavior-based analysis approach and increased understanding of network security, alongside the integration of non-traditional data sources. The author advocates for legitimizing and training for security intelligence roles within organizations to improve security analysis capabilities.