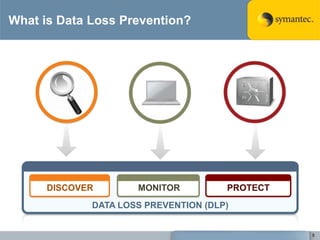
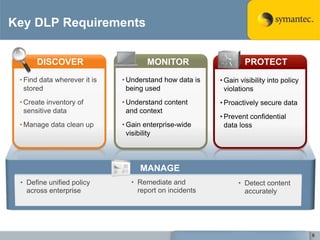
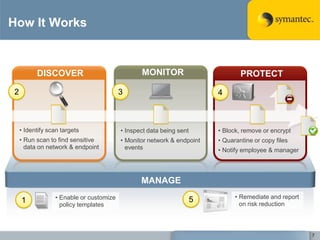
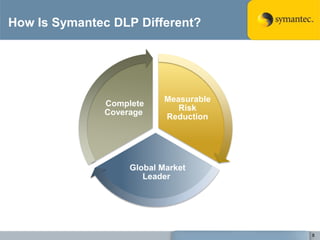
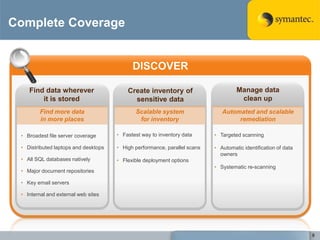
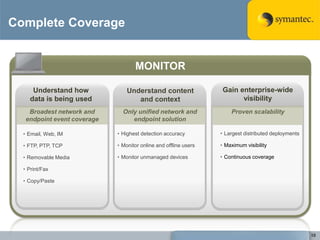
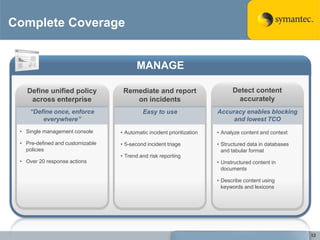
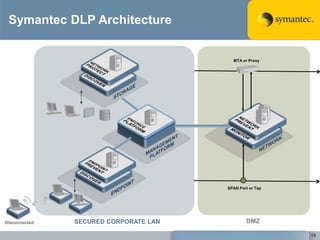
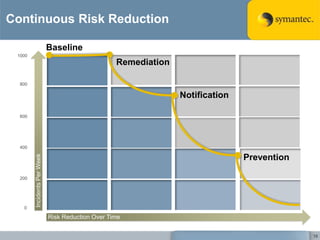
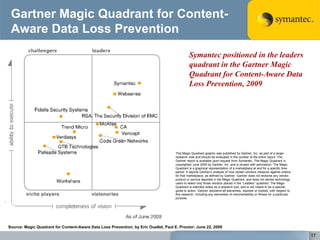
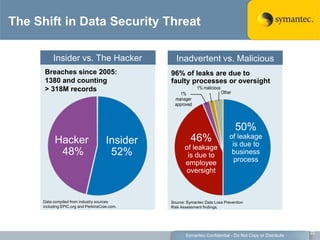
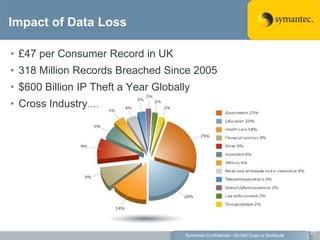
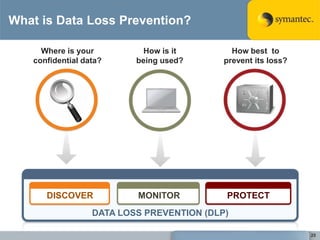
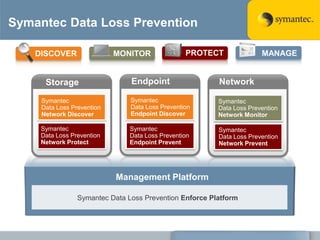
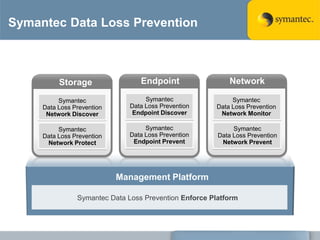
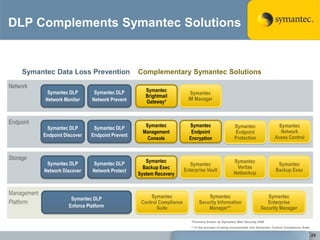
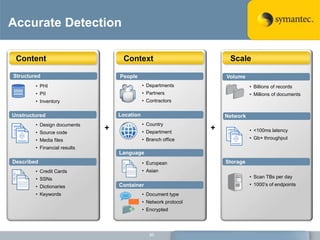
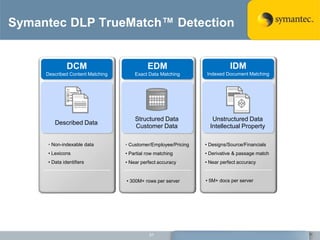
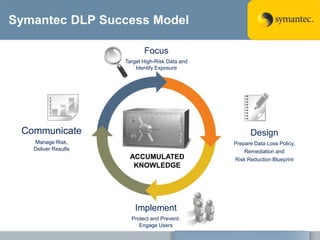
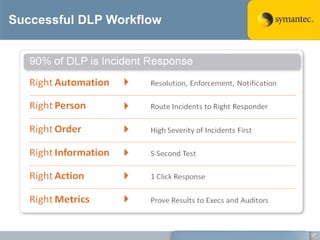
The document outlines the importance of Data Loss Prevention (DLP) by Symantec, highlighting key issues like data visibility and management errors as major causes of data loss. It details the functionalities and advantages of Symantec DLP, including enterprise-wide visibility, automated remediation, and compliance monitoring, positioning Symantec as a trusted leader in the field. The document also stresses the significant risks associated with data loss, emphasizing the necessity for effective DLP solutions in protecting sensitive information.