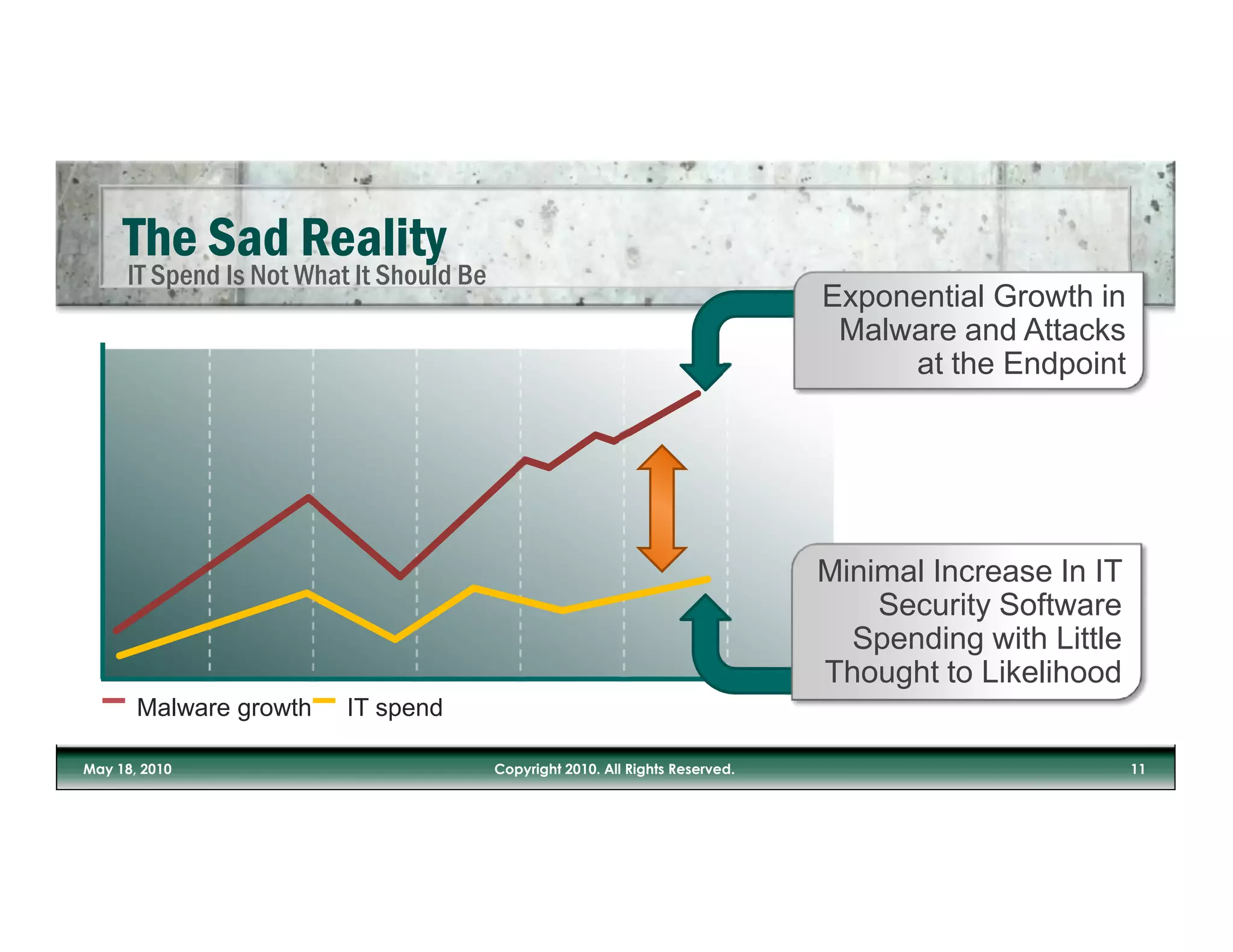
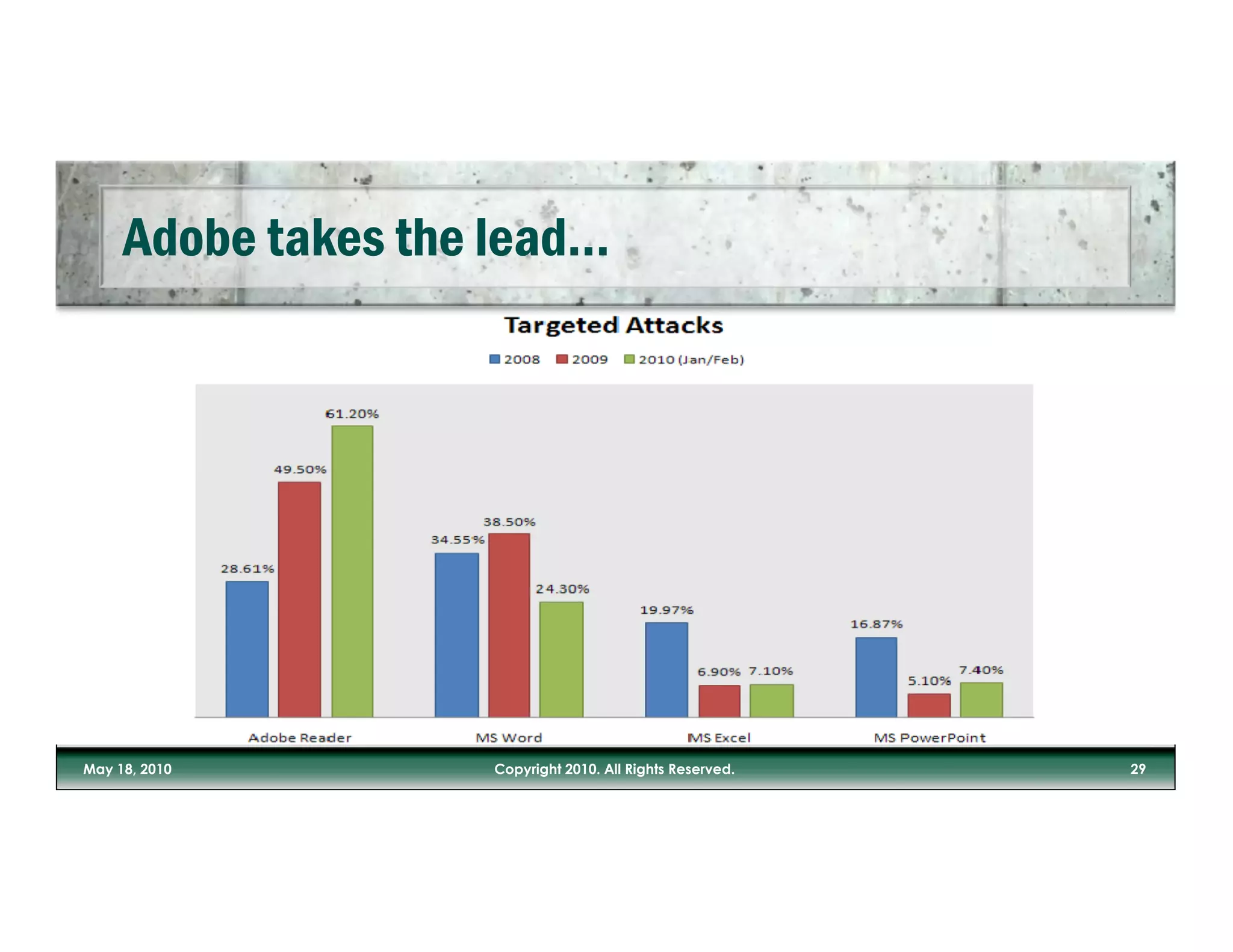
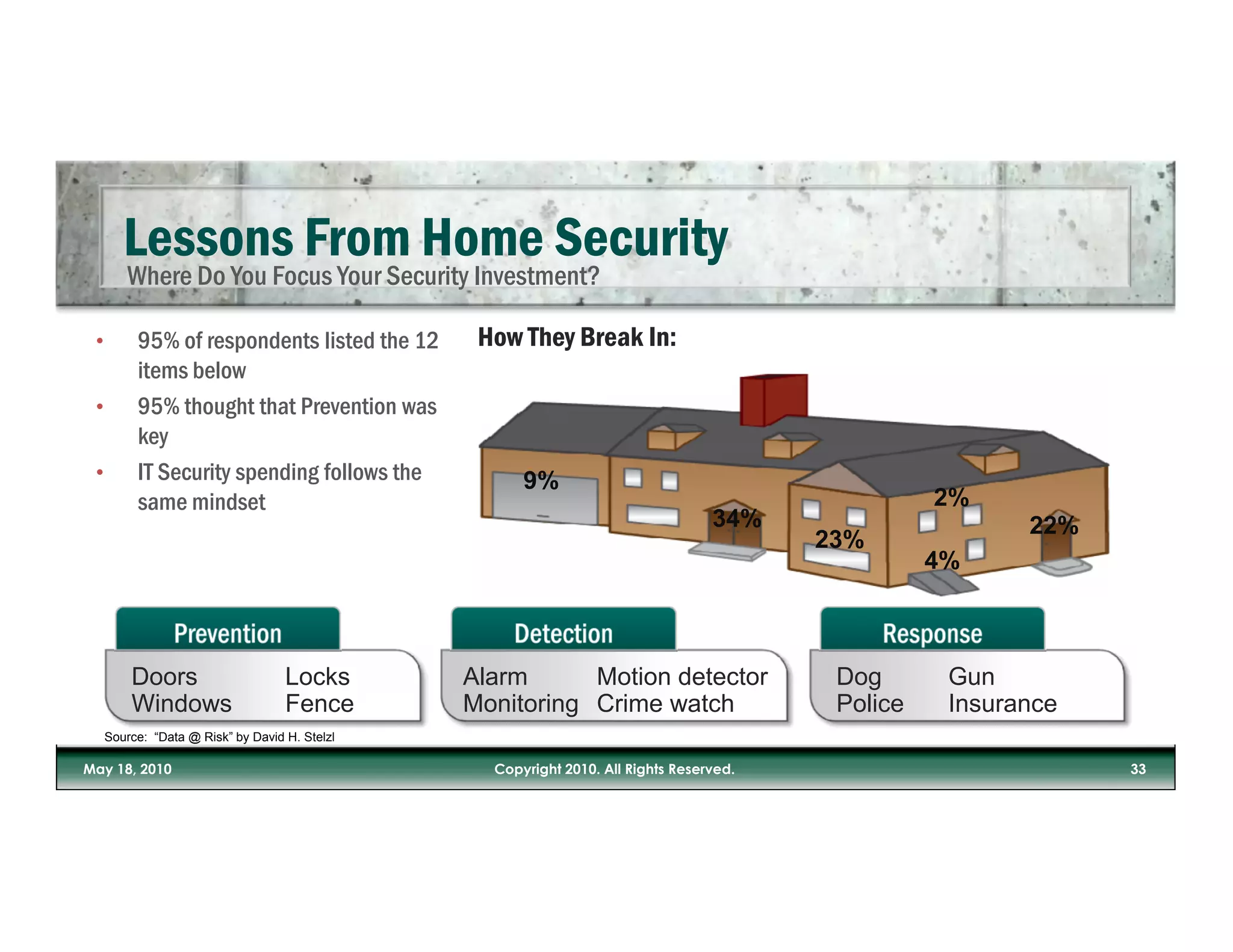
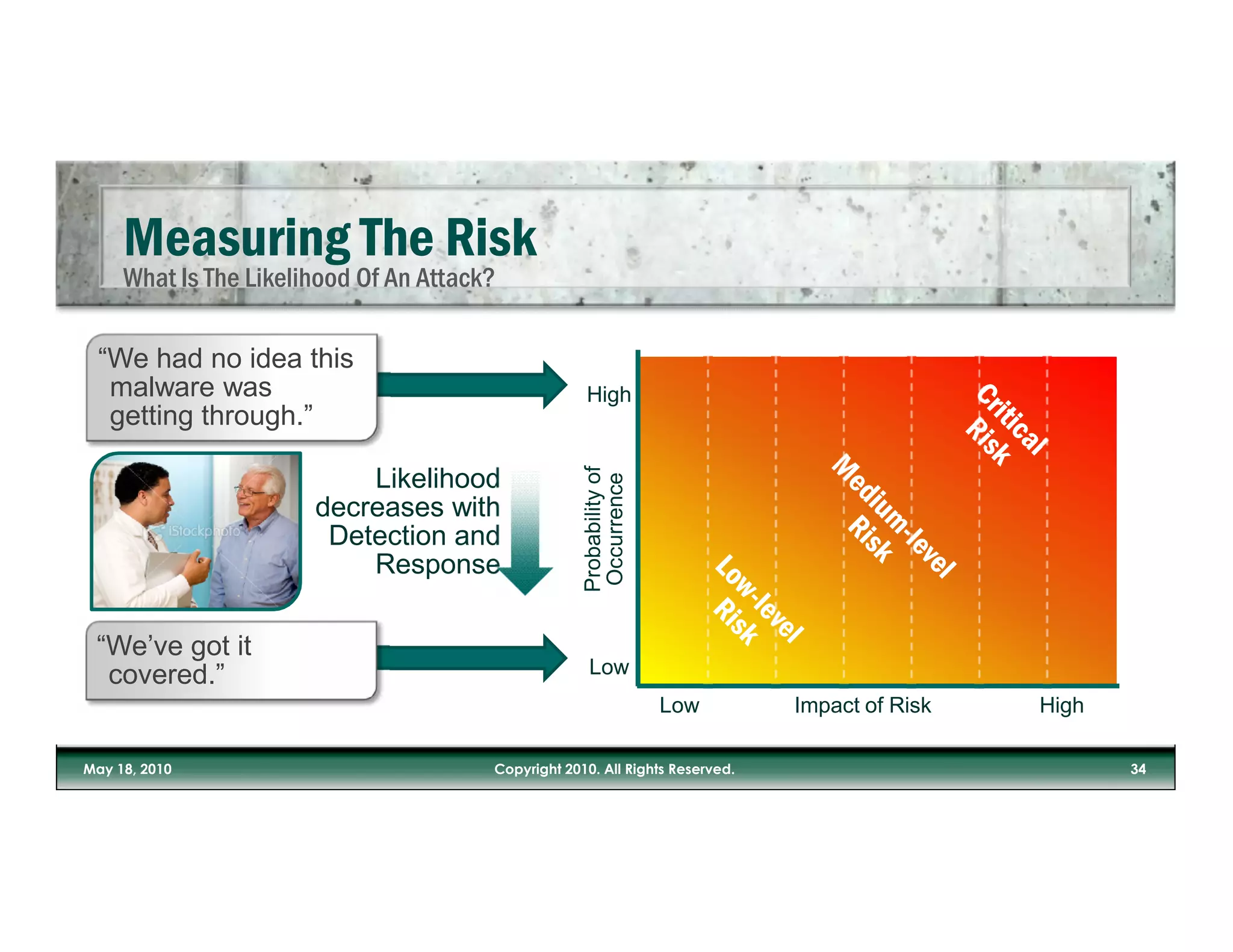
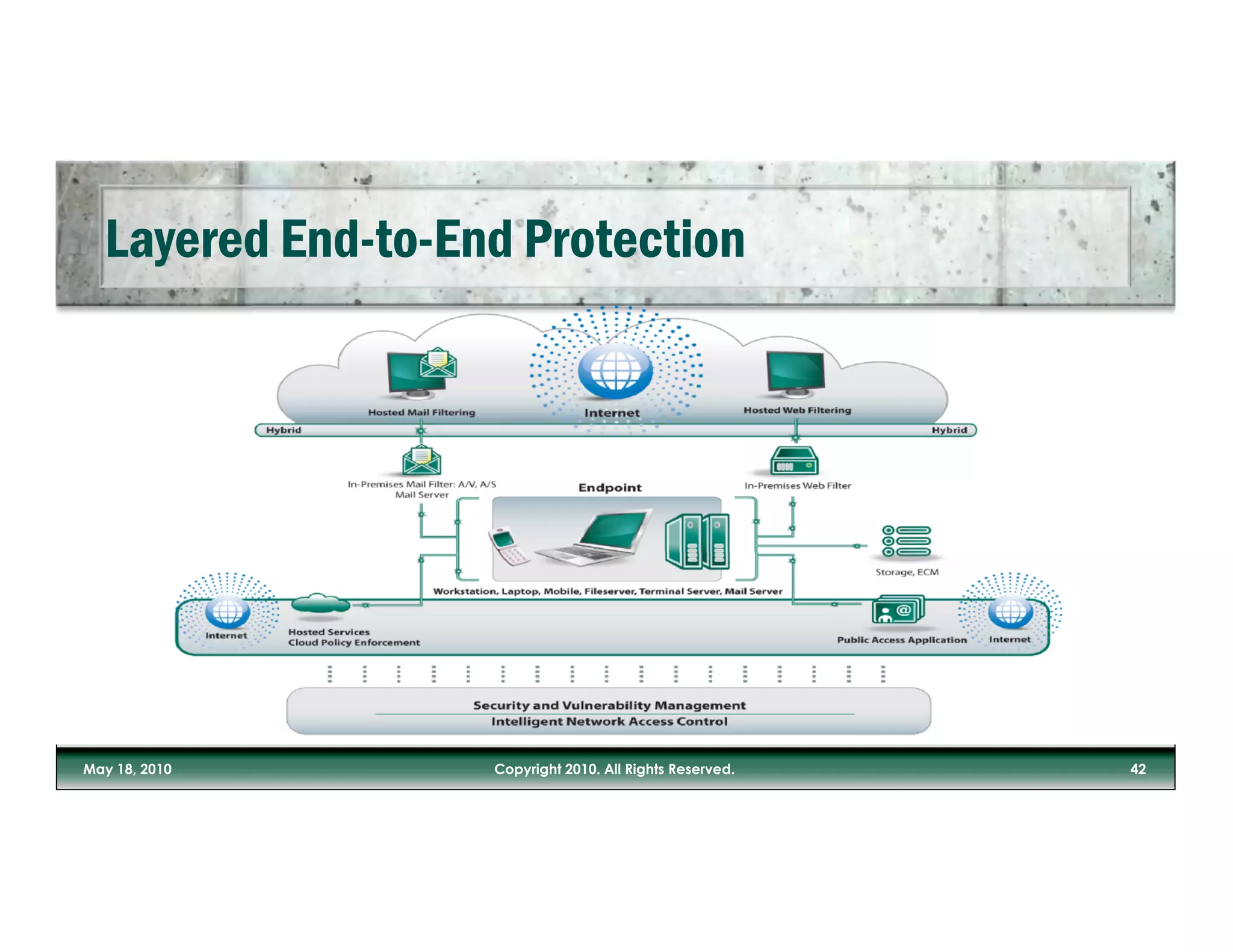
The document discusses the increasing risks posed by malware and inadequate IT security measures in light of the growing use of mobile devices and cloud applications. It emphasizes the importance of valuing data over physical assets and suggests a need for updated security approaches that account for the realities of data security in mobile and social media contexts. The author stresses the necessity of integrating security measures into business processes rather than relying solely on IT departments.