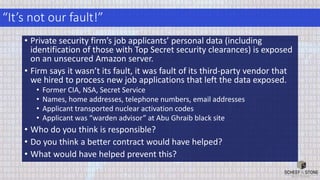
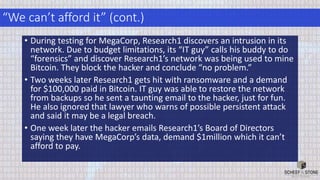
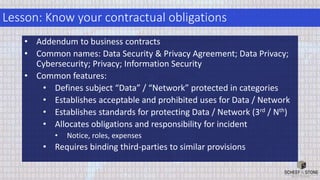
The document discusses best practices for managing cybersecurity and data privacy risks from third party vendors. It recommends (1) conducting due diligence on third parties' security practices before engaging them, (2) using contracts to obligate third parties to comply with security standards and notify clients of incidents, and (3) periodically assessing third parties' security based on risk. Following these practices can help companies minimize risks from third parties as required by laws and frameworks.










![New York Department of Financial Services Cybersecurity (NYDFS)
Requirements for Financial Services Companies + [fill in]
• All NY “financial institutions” + third party service providers.
• Third party service providers – examine, obligate, audit.
• Establish Cybersecurity Program (w/ specifics):
• Logging, Data Classification, IDS, IPS;
• Pen Testing, Vulnerability Assessments, Risk Assessment; and
• Encryption, Access Controls.
• Adopt Cybersecurity Policies.
• Designate qualified CISO to be responsible.
• Adequate cybersecurity personnel and intelligence.
• Personnel Policies & Procedures, Training, Written IRP.
• Chairman or Senior Officer Certify Compliance.](https://image.slidesharecdn.com/tuma-cybersecuritycontracts-171207072531/85/Contracting-for-Better-Cybersecurity-14-320.jpg)