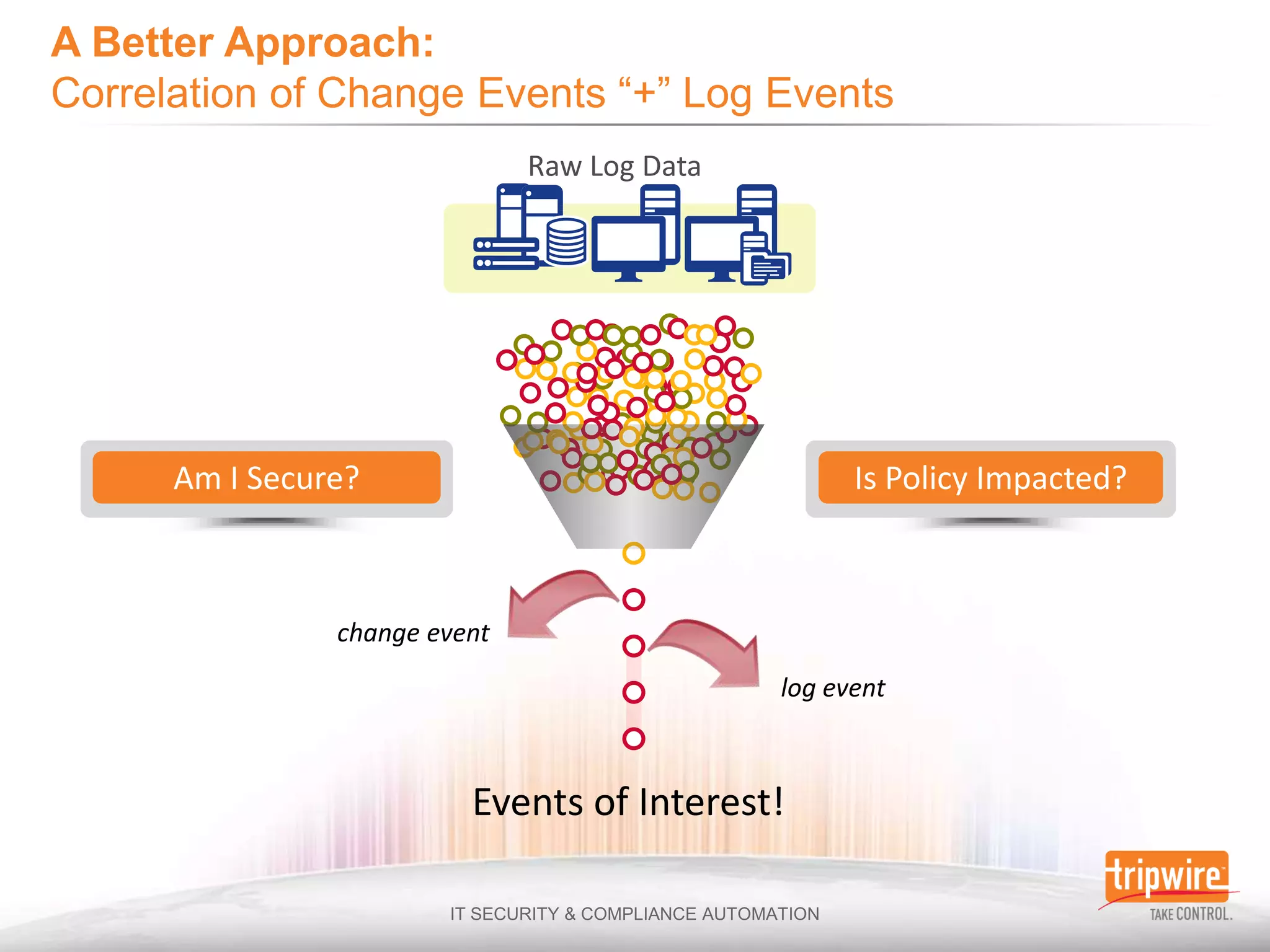
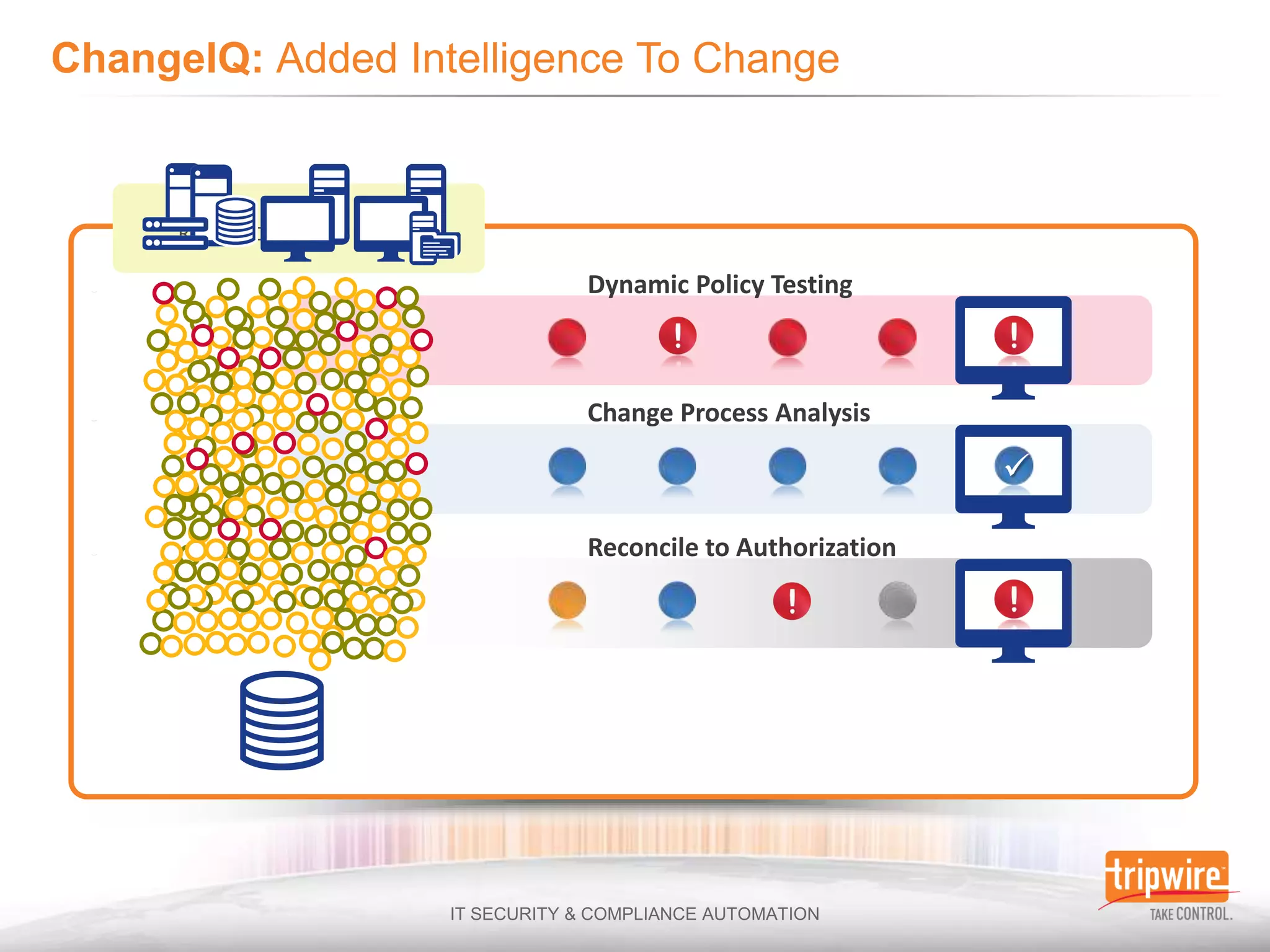
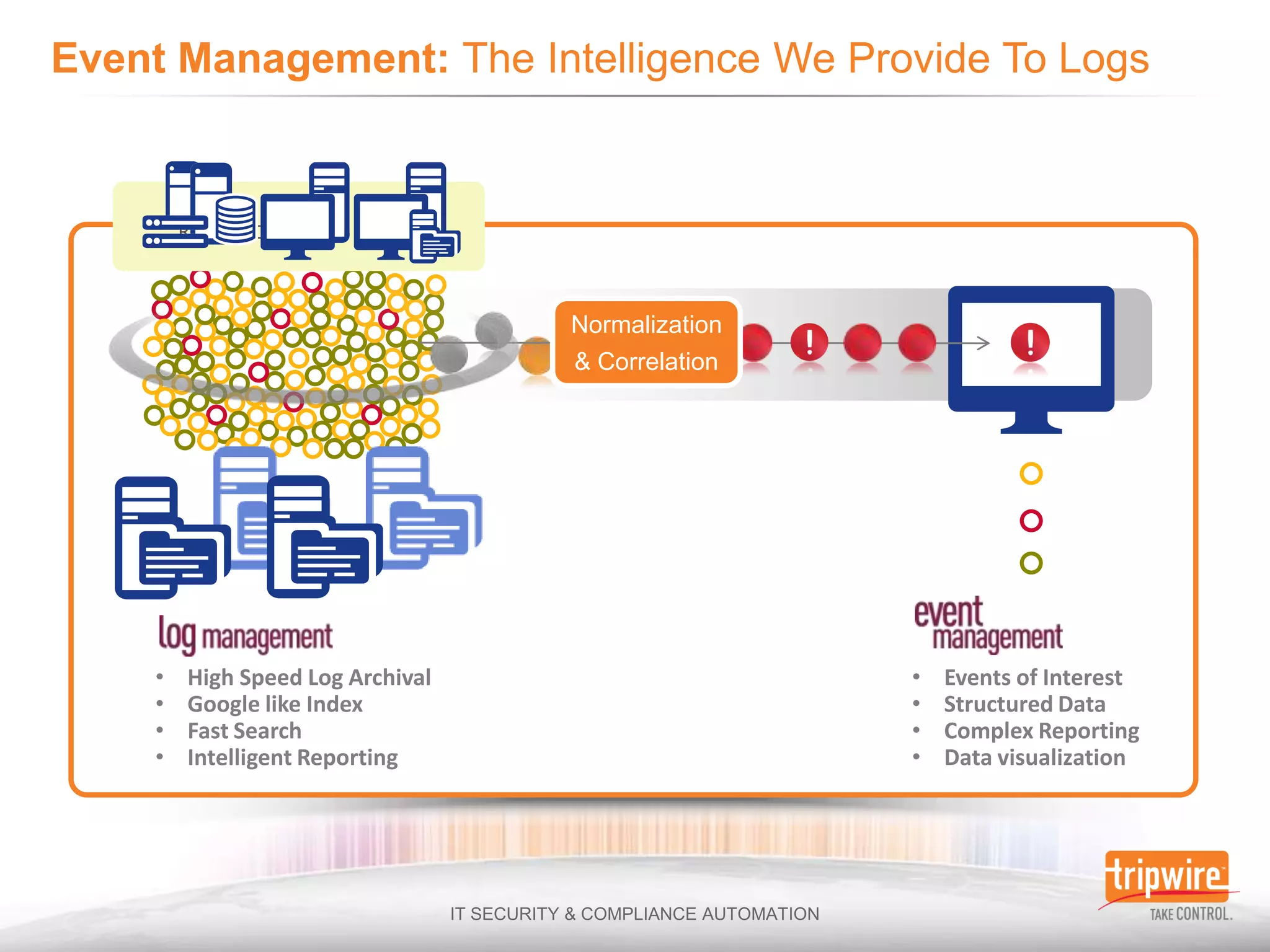
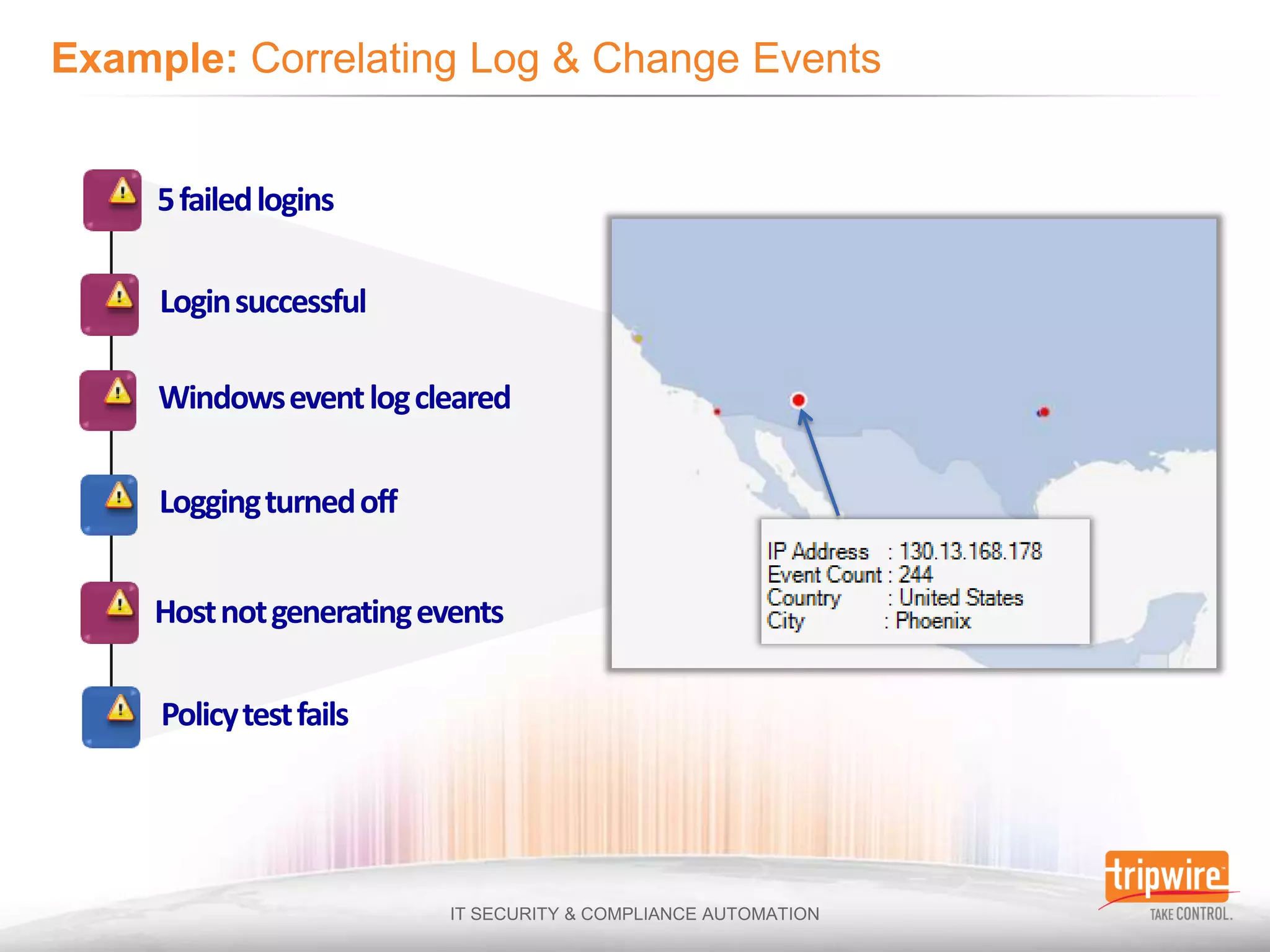
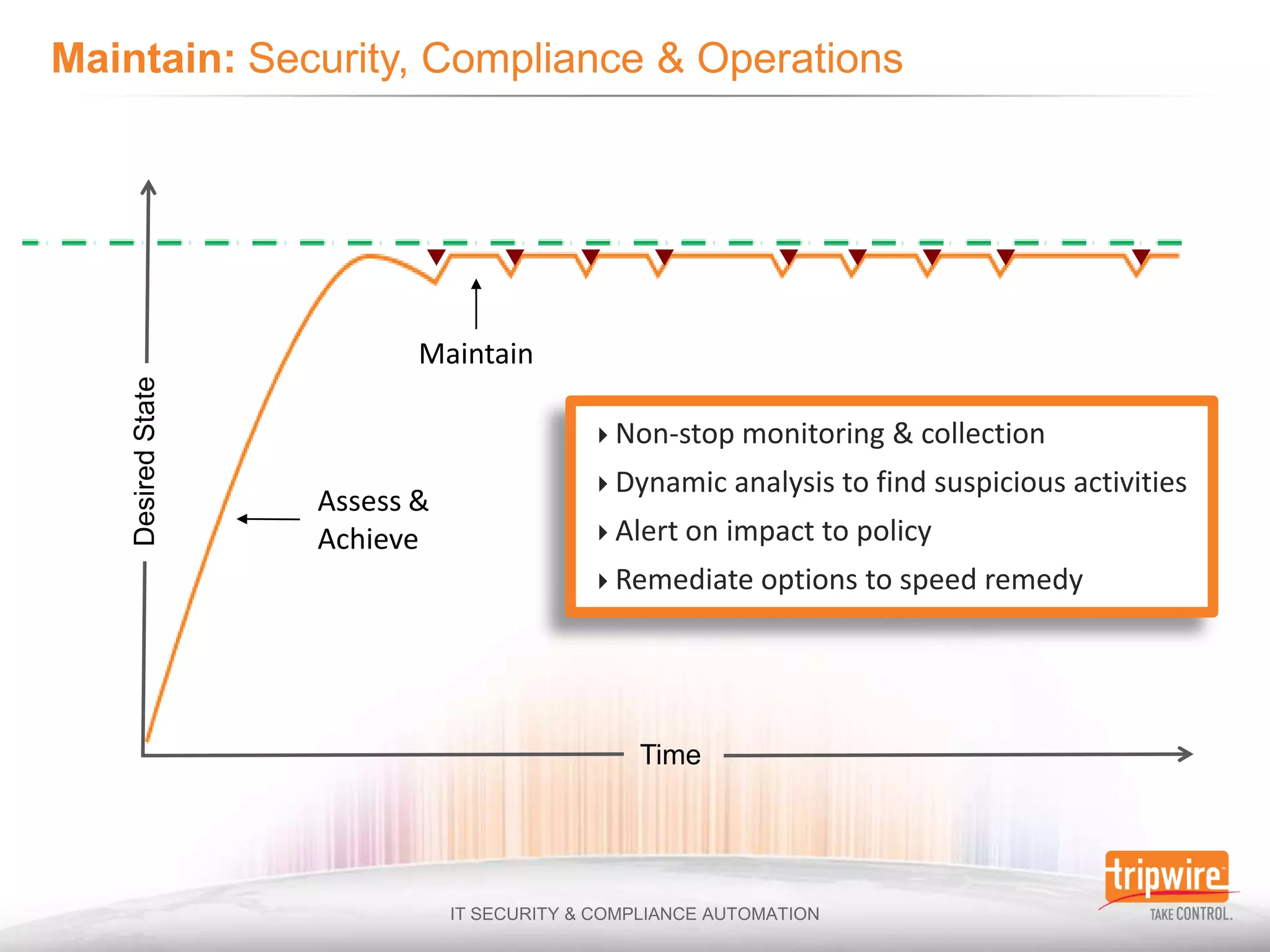
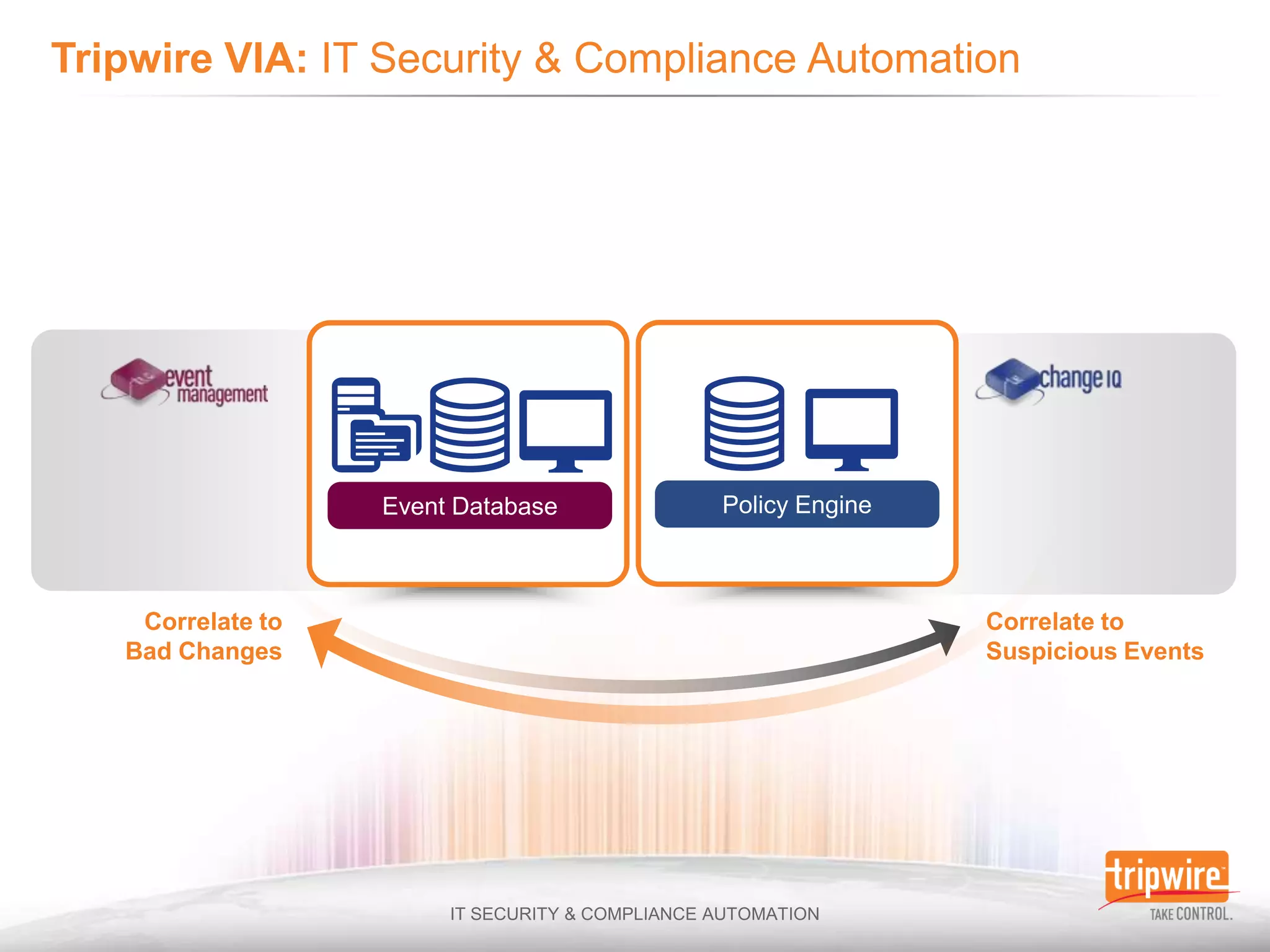
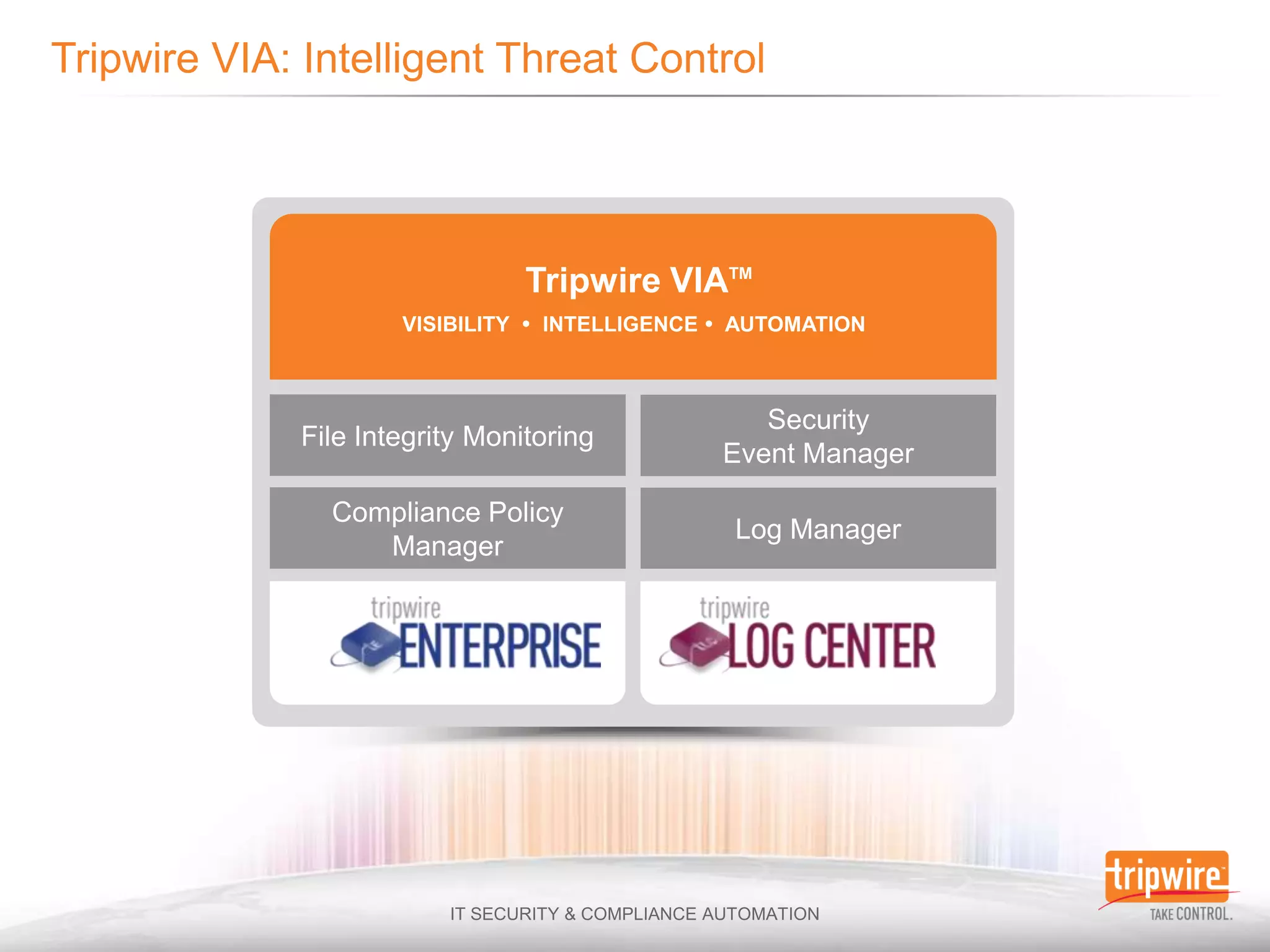
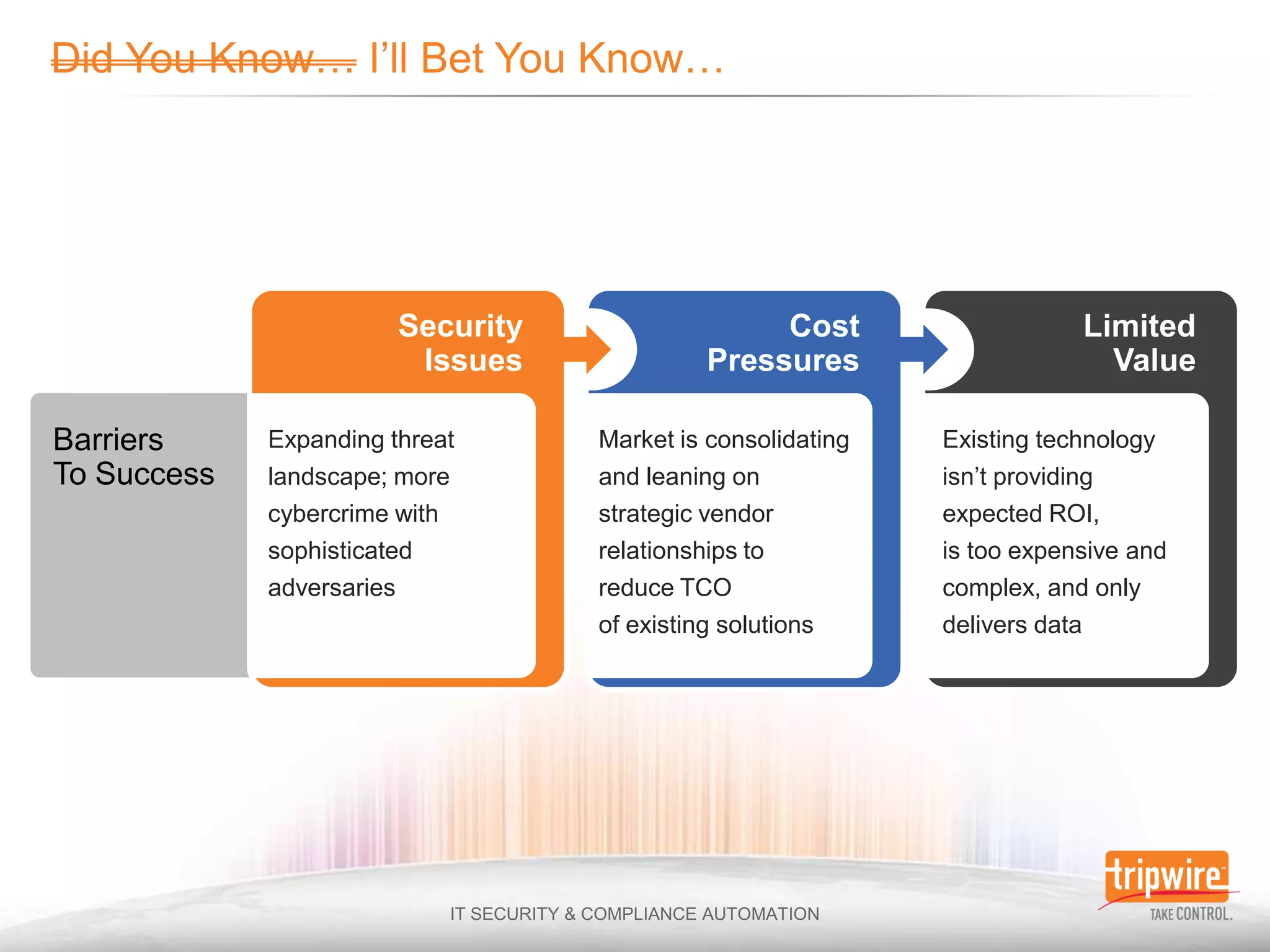
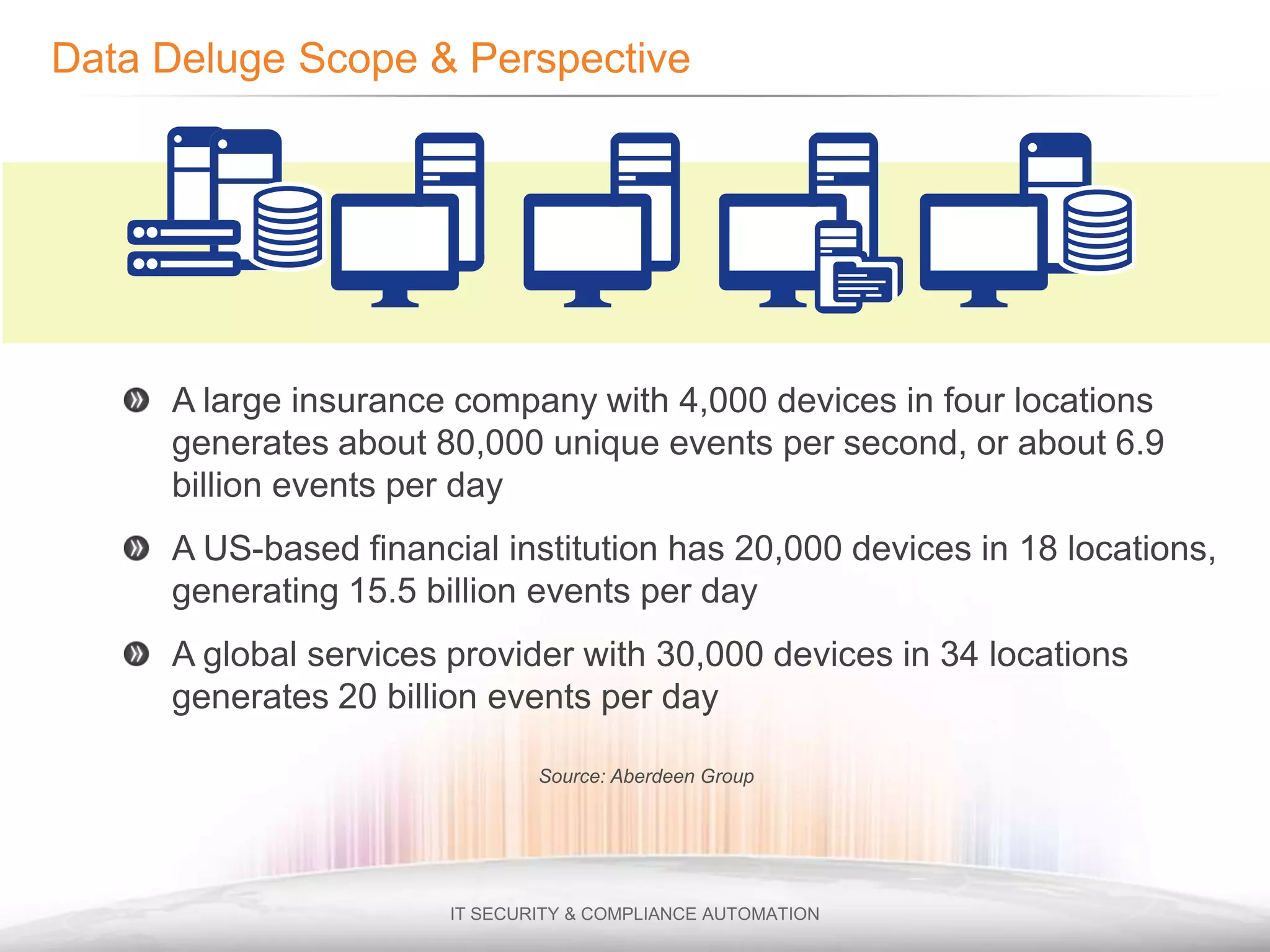
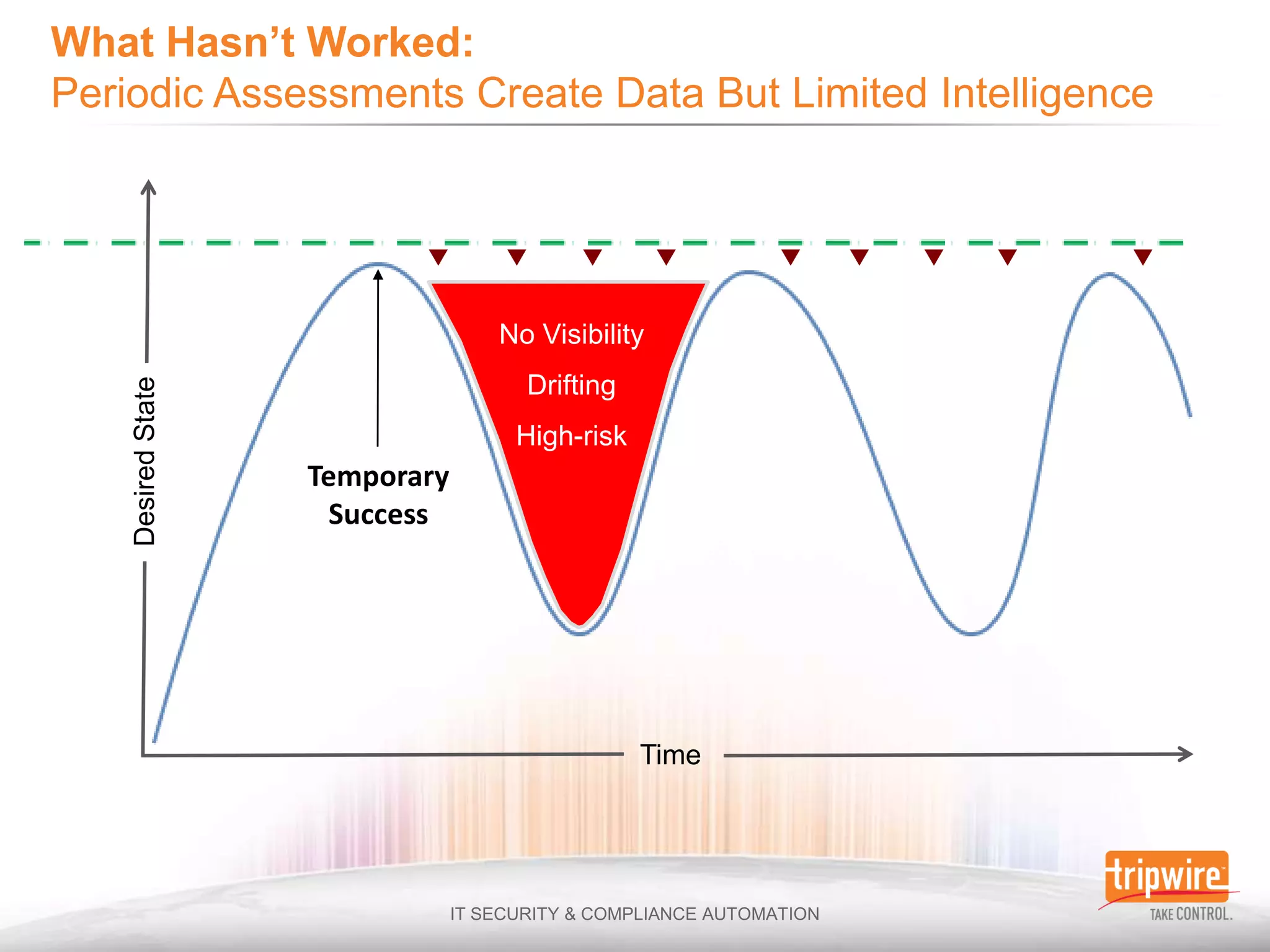
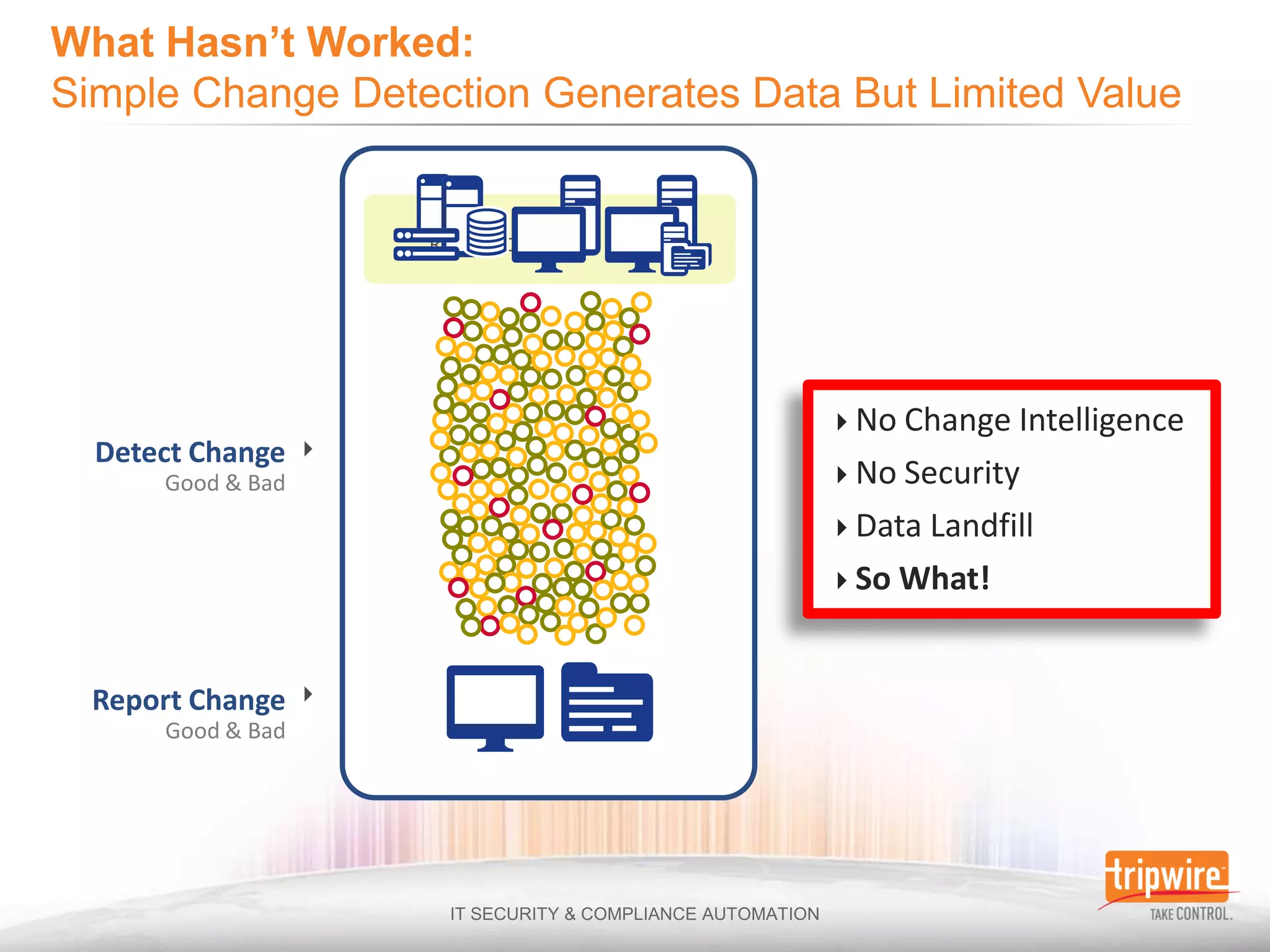
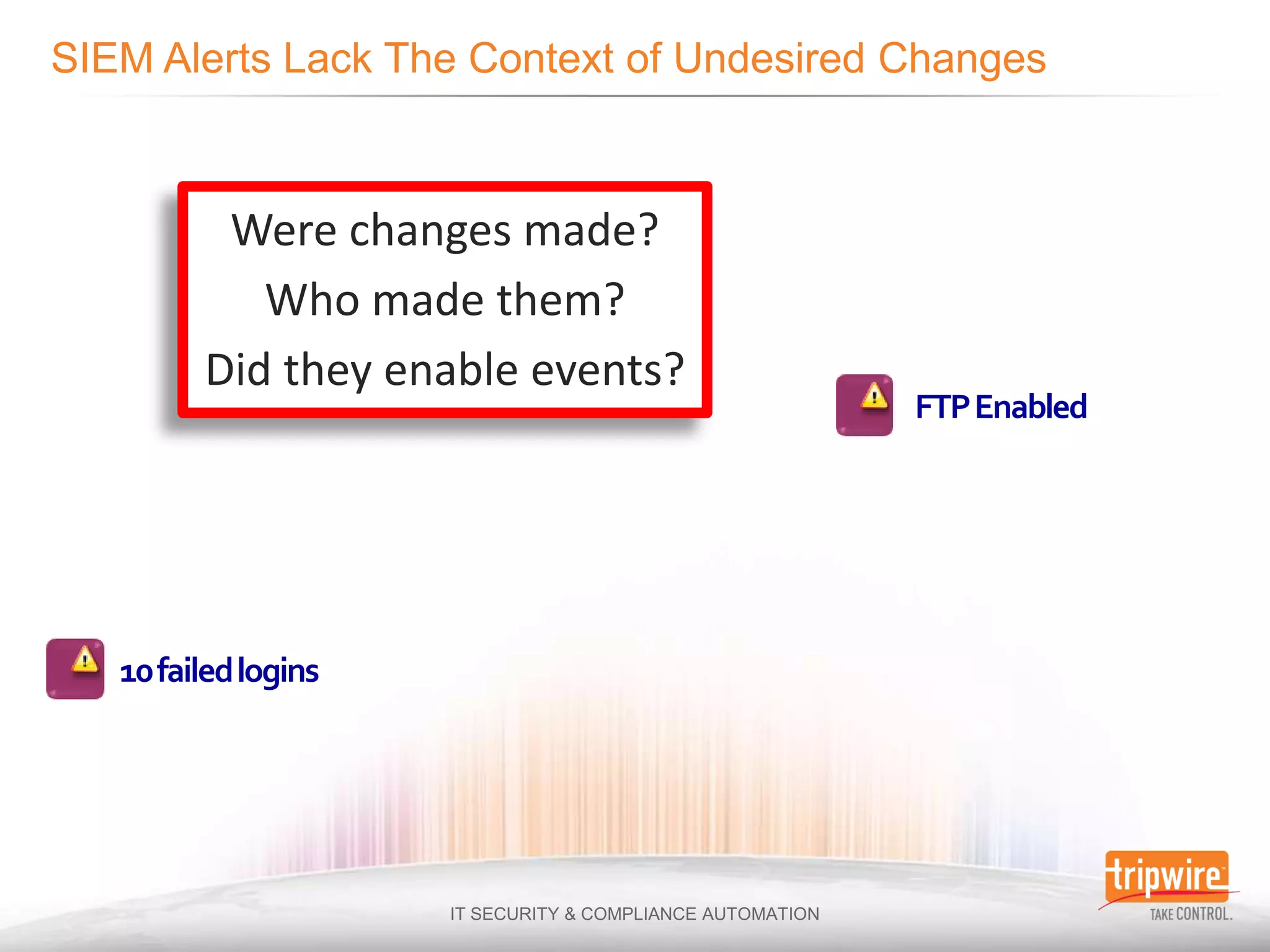
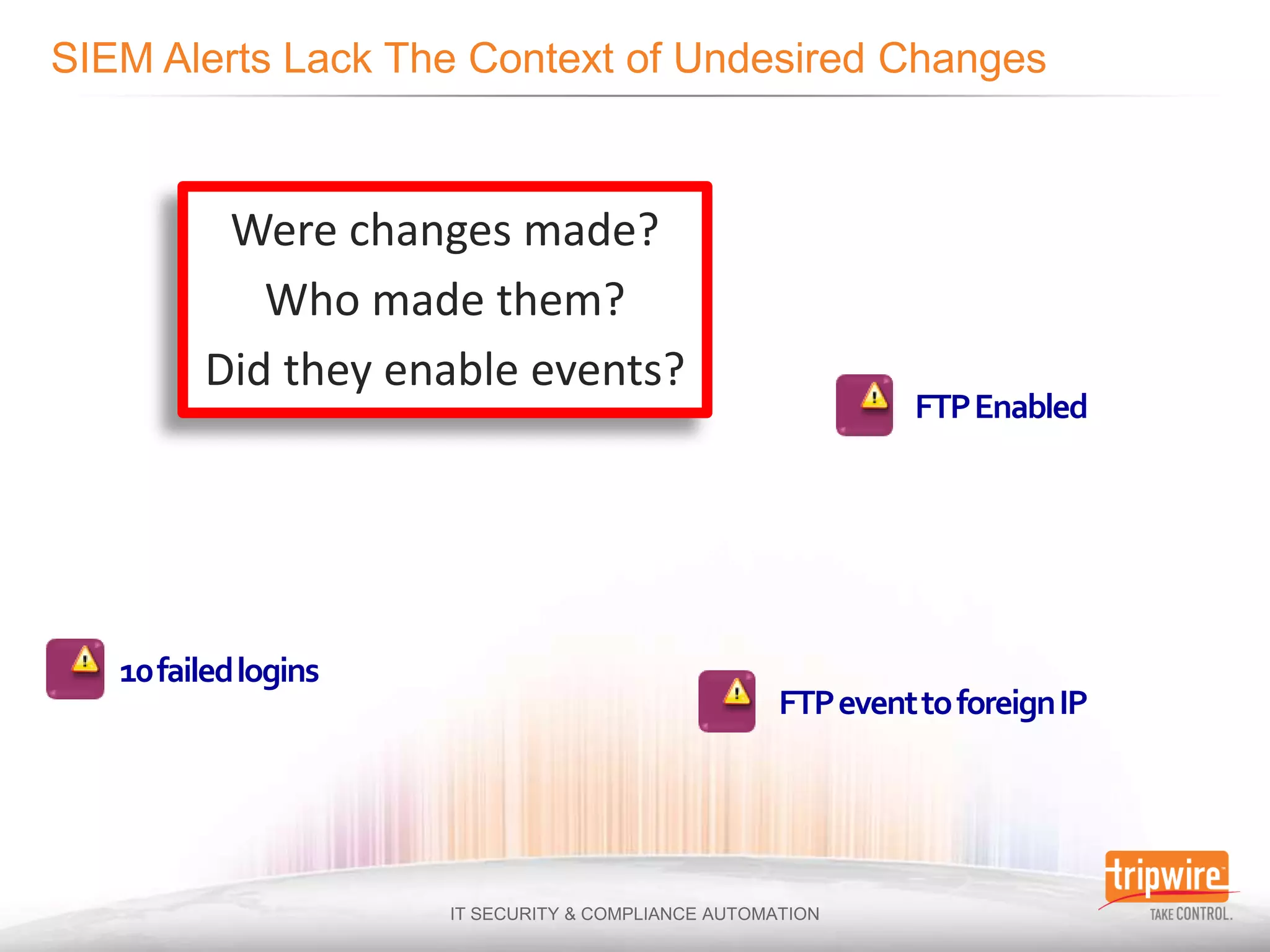
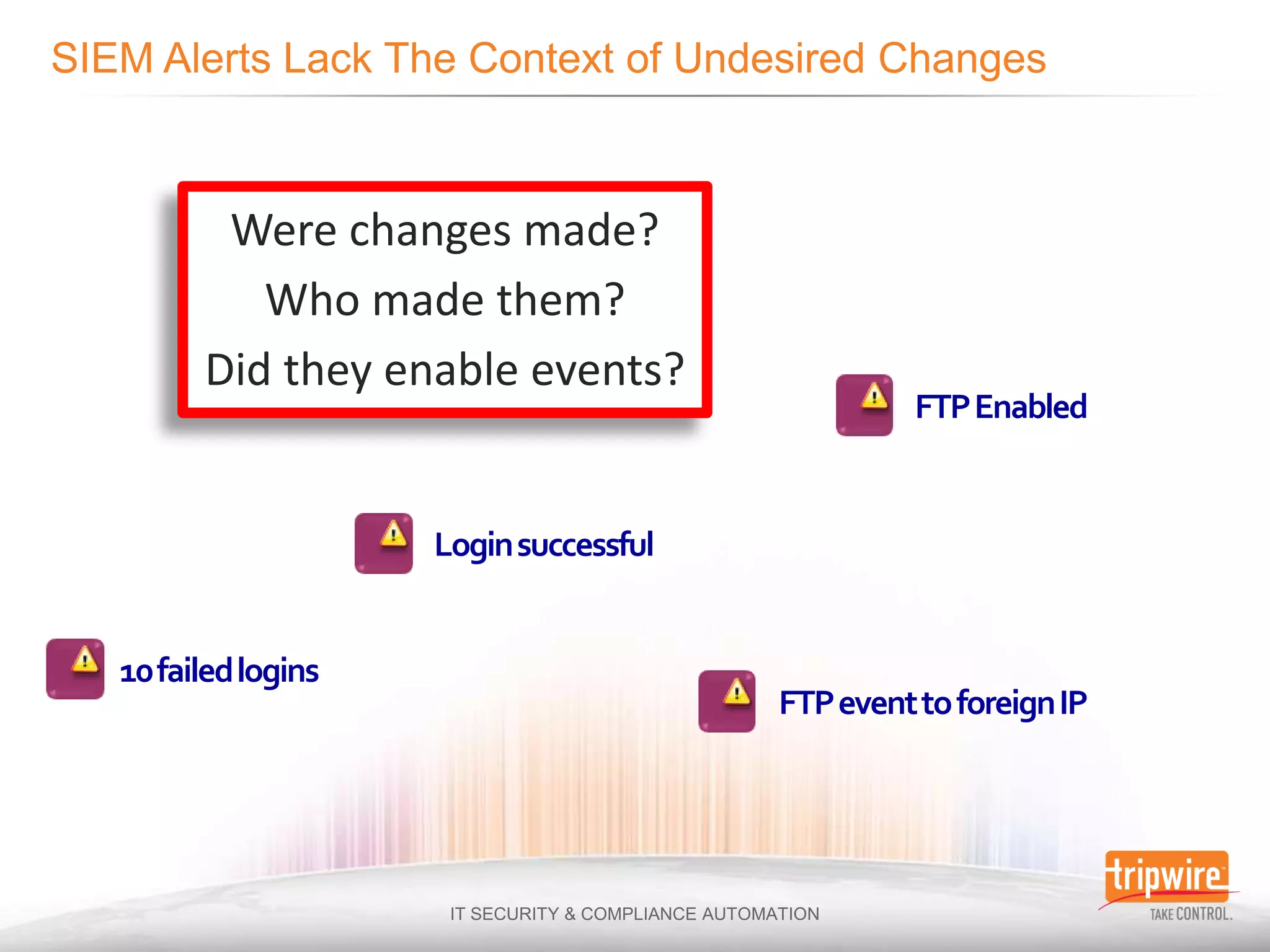
The document discusses the challenges of ensuring security and compliance in the context of increasing data complexities and cyber threats. It highlights the inefficiencies of current solutions in detecting breaches and the high costs associated with maintaining security and compliance. Tripwire is presented as a solution provider offering automation to enhance visibility, reduce manual efforts, and improve breach detection and response times.


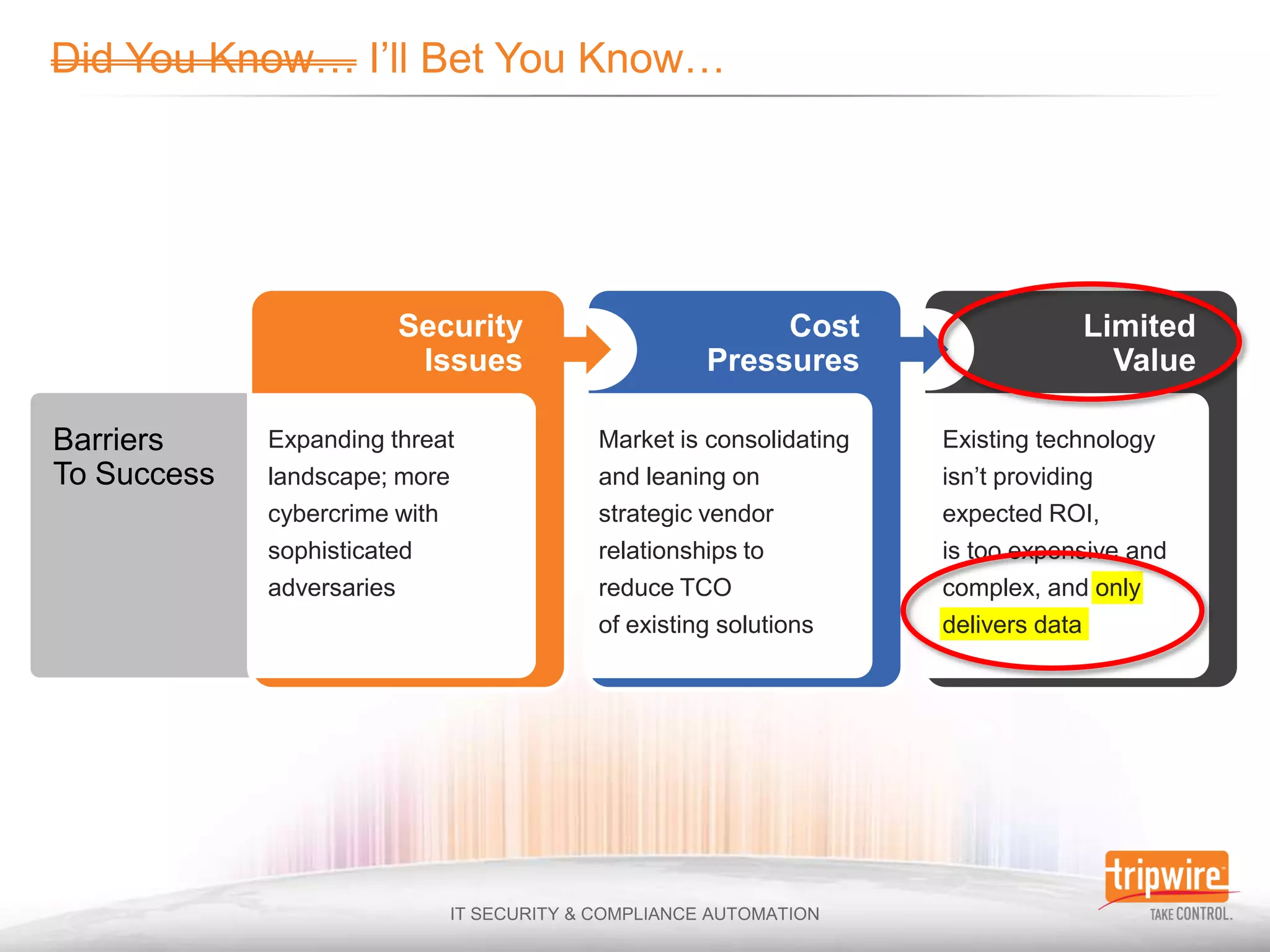






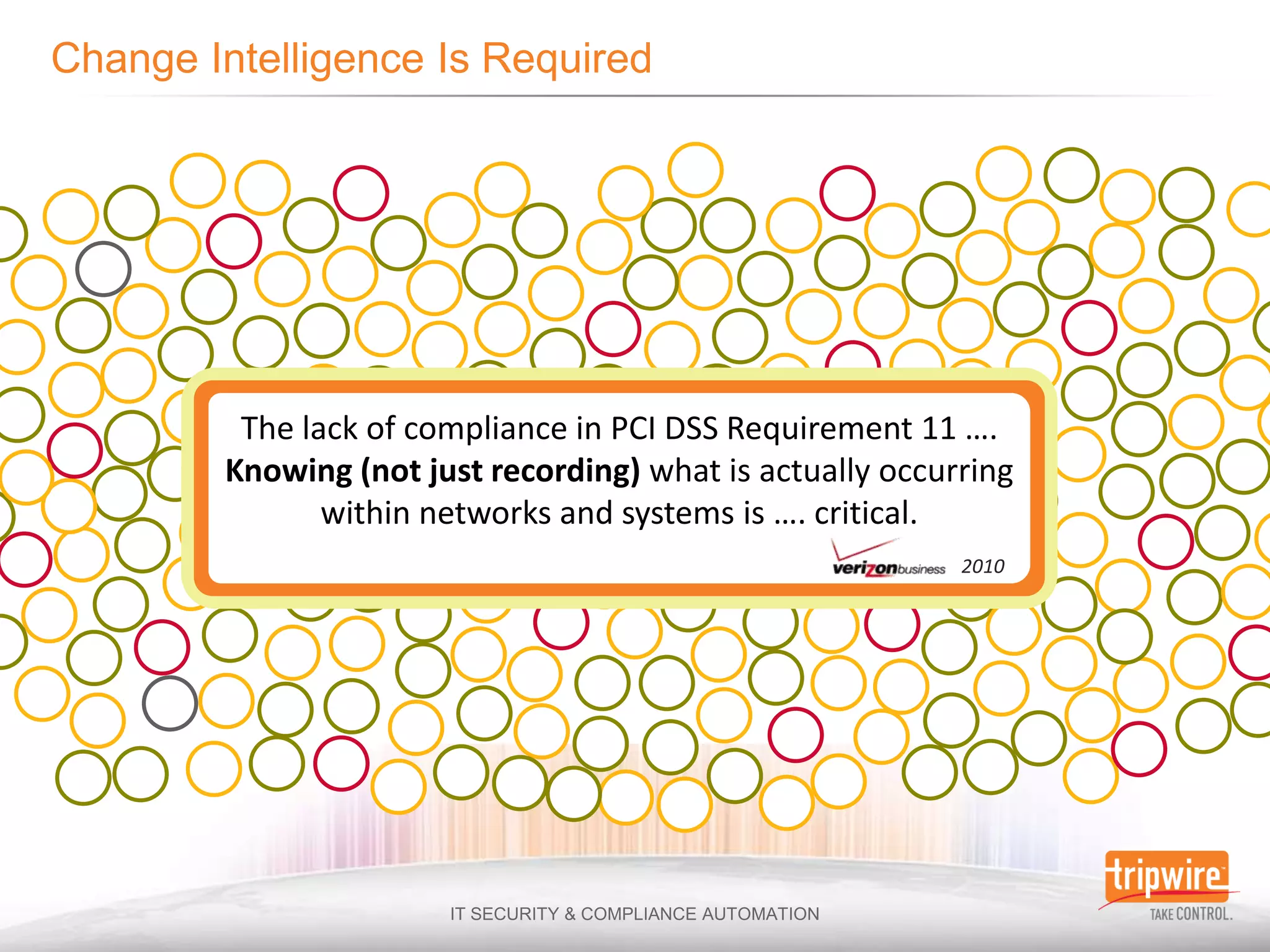




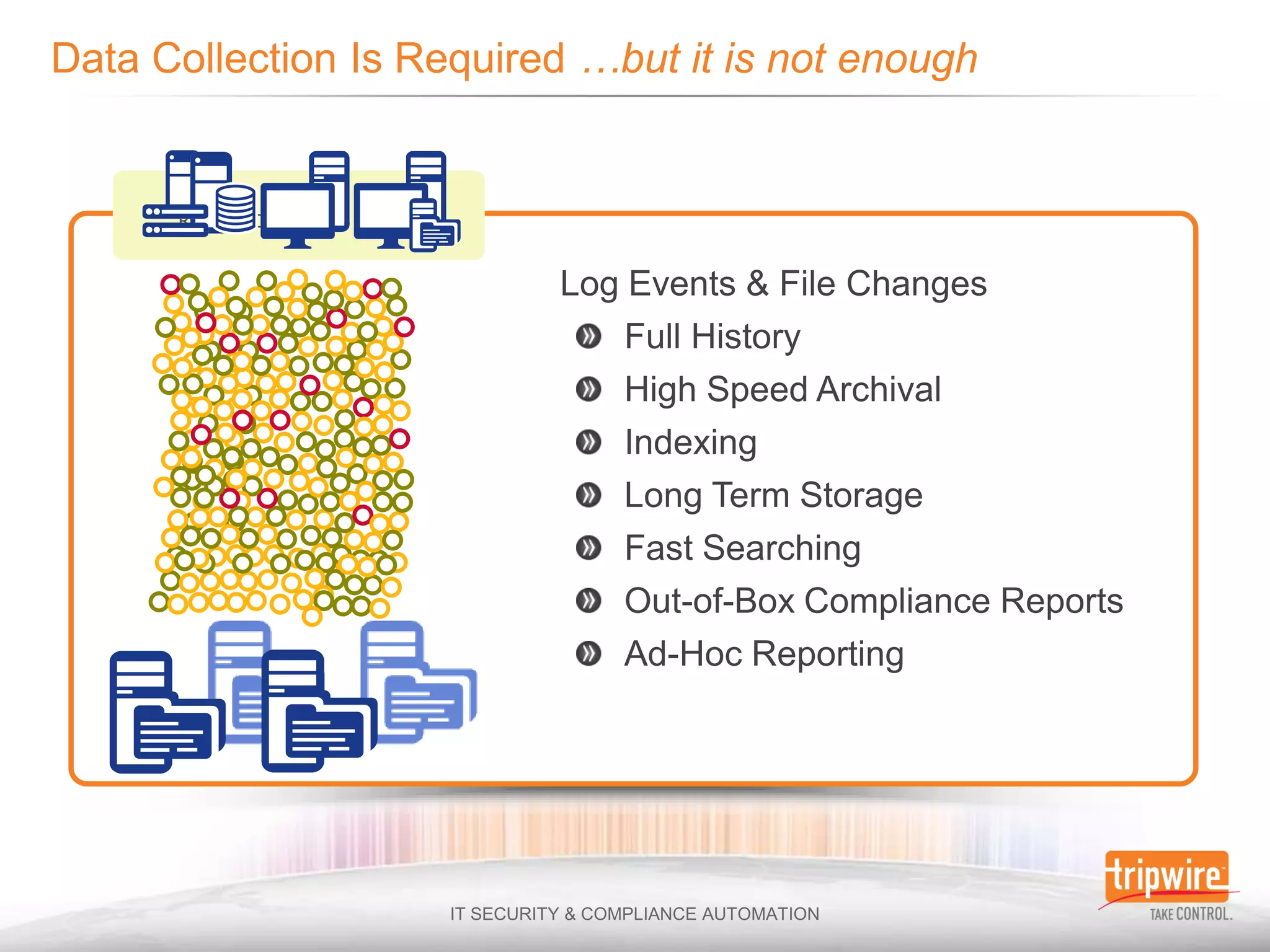
![“We consistently find that nearly 90% of
the time logs are available but discovery
[of breaches] via log analysis remains
under 5% ”
2010](https://image.slidesharecdn.com/ensuringsecurityandcomplianceinadatadeluge-110627103803-phpapp01/75/Ensuring-Security-and-Compliance-in-a-Data-Deluge-24-2048.jpg)