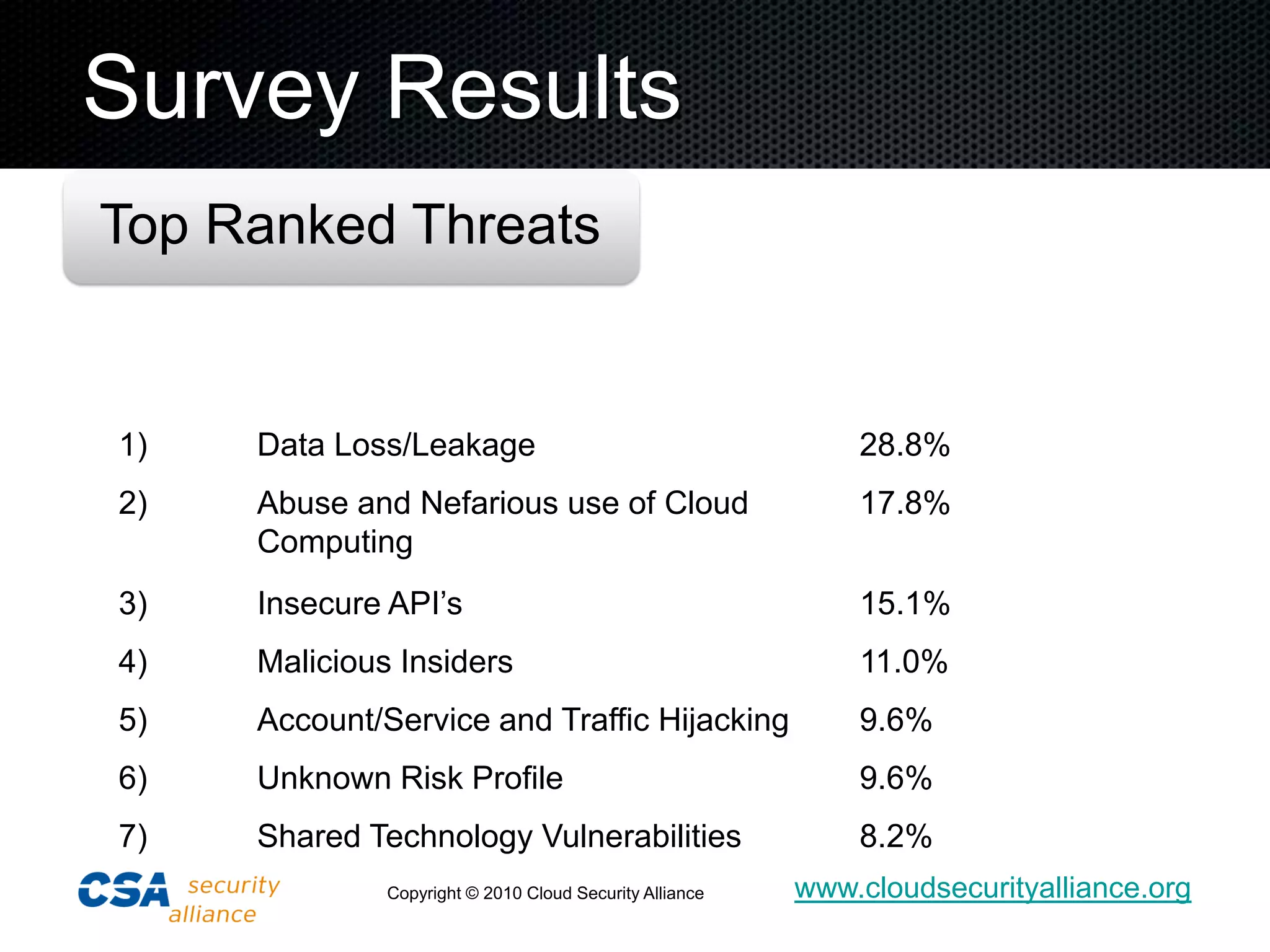
The document discusses cloud security risks and threats identified by the Cloud Security Alliance (CSA). The CSA is a non-profit organization focused on best practices for cloud security. The top 7 cloud security threats according to a CSA survey are: 1) data loss/leakage, 2) abuse and nefarious use of cloud computing, 3) insecure APIs, 4) malicious insiders, 5) account/service and traffic hijacking, 6) unknown risk profiles, and 7) shared technology vulnerabilities. The CSA guidance provides best practices to help secure cloud computing.







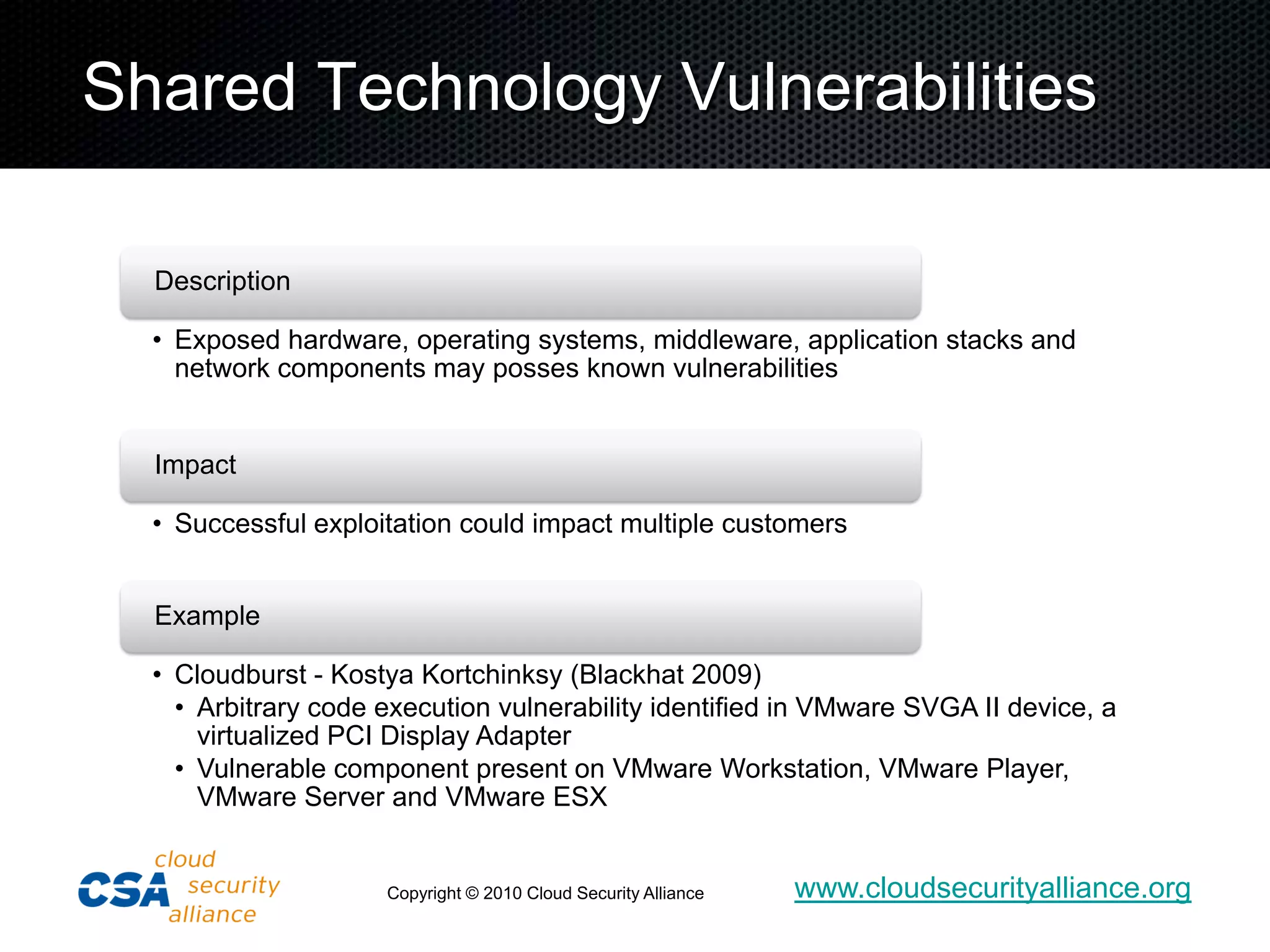


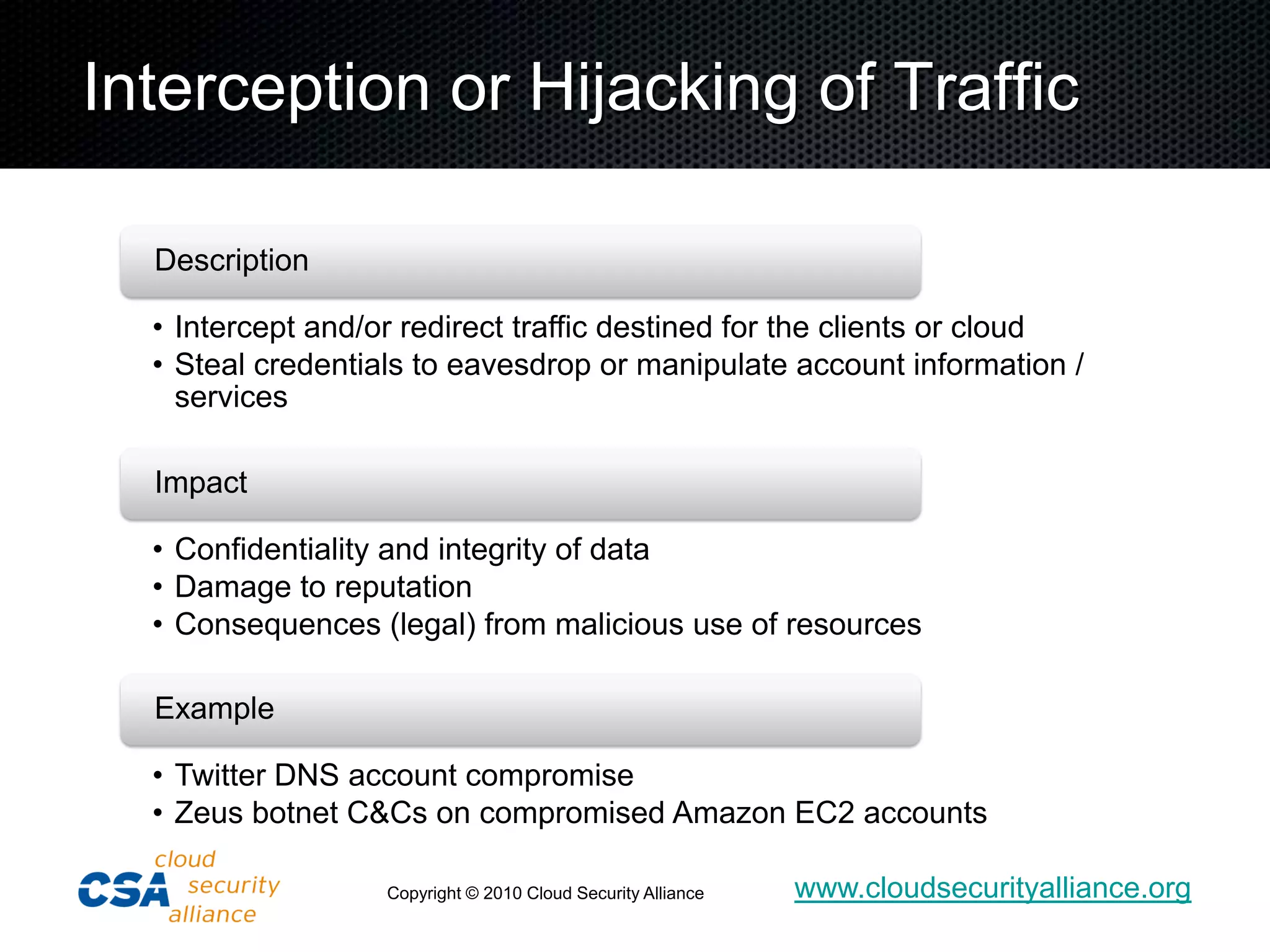

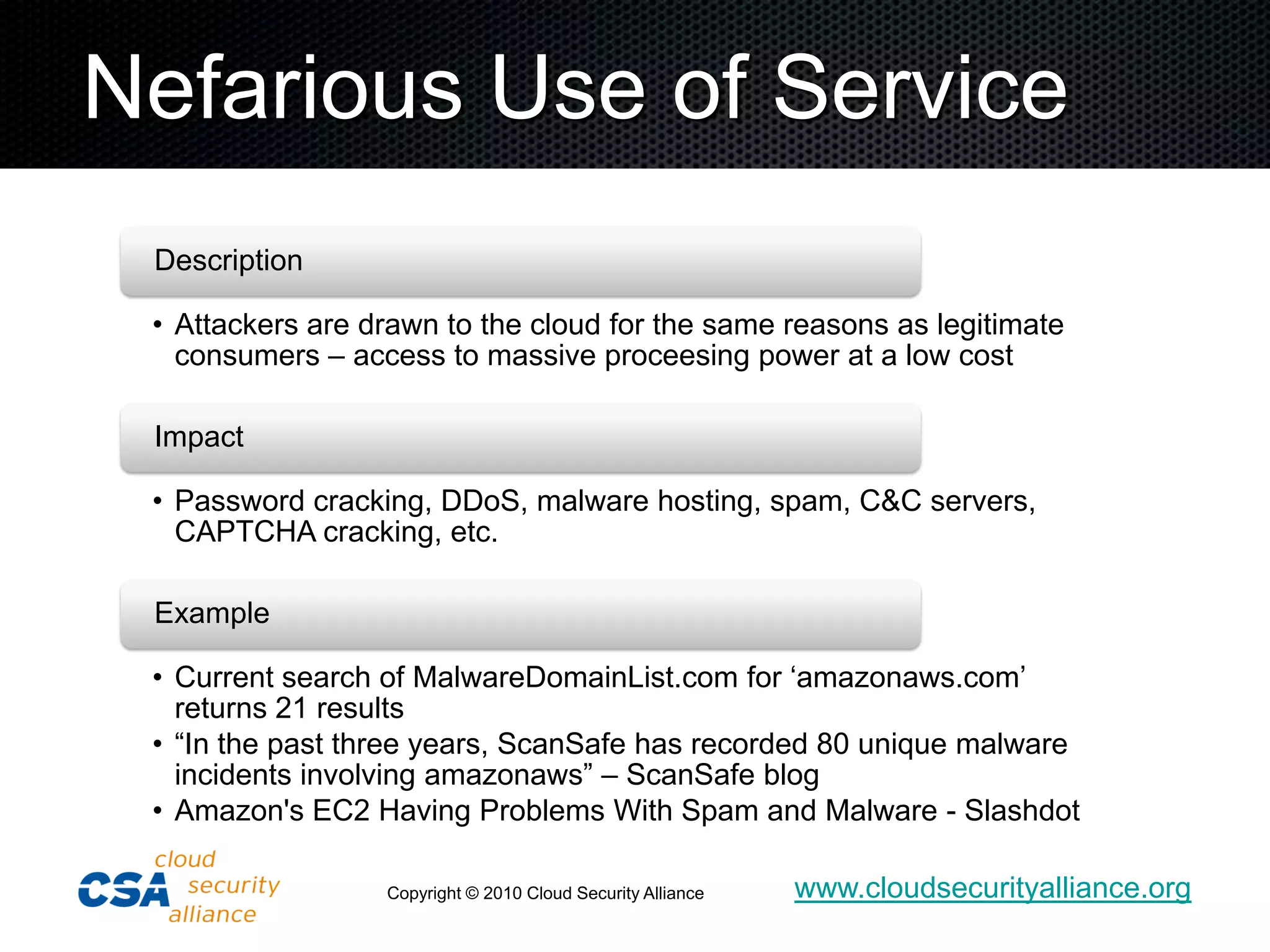
![Unknown Risk Profile
Description
• A lack of visibility into security controls could leave cloud consumers exposed to
unnecessary risk.
Impact
• Significant data breaches could occur, possibly without the knowledge of the cloud
consumer.
Example
• Heartland Payment Systems was “willing to do only the bare minimum and comply with state
laws instead of taking the extra effort to notify every single customer, regardless of law, about
whether their data [had] been stolen.”
http://www.pcworld.com/article/158038/heartland_has_no_heart_for_violated_customers.html
Copyright © 2010 Cloud Security Alliance www.cloudsecurityalliance.org](https://image.slidesharecdn.com/presd110-100601035928-phpapp02/75/Presd1-10-14-2048.jpg)