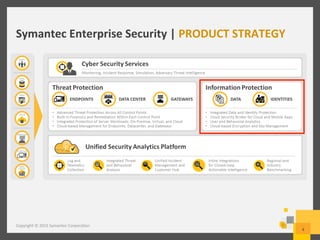
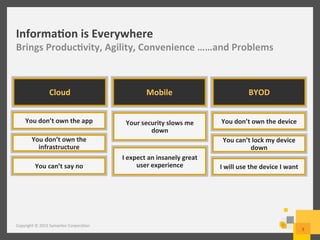
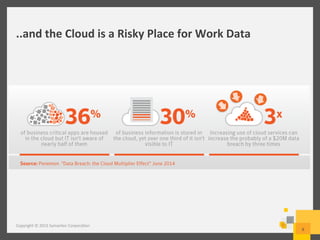
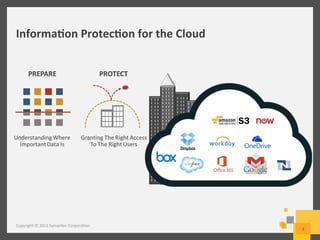
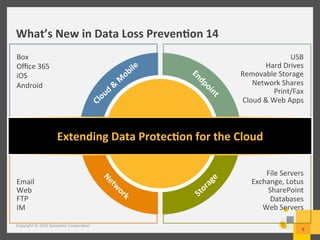
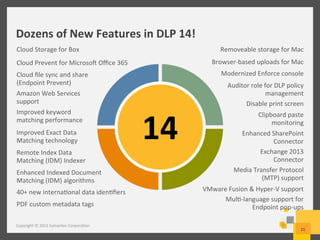
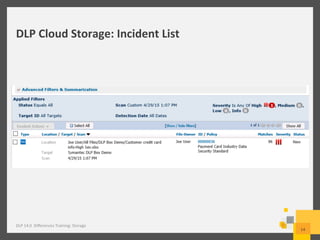
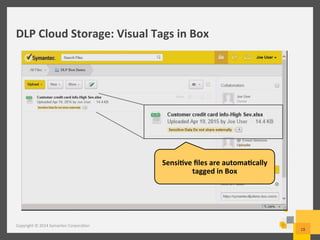
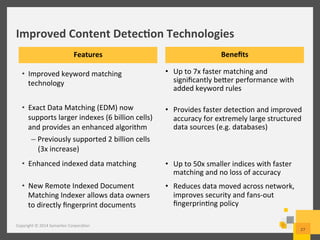
The document provides an overview of data loss prevention (DLP) challenges in the cloud and details new offerings from Symantec, including DLP for Cloud products that enhance visibility, control, and compliance for sensitive data. It discusses customer concerns regarding data security in cloud environments and outlines improvements in DLP 14 features for various applications. Additionally, the document emphasizes the opportunity for resellers to upsell DLP solutions to address cloud-related security and compliance issues.