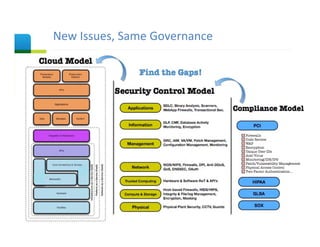
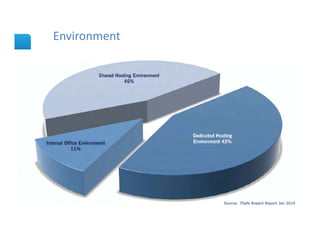
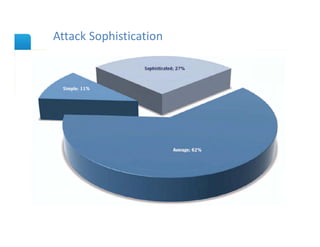
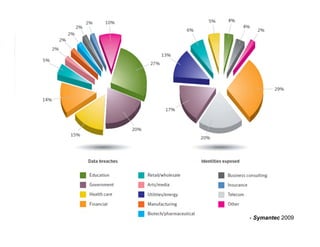
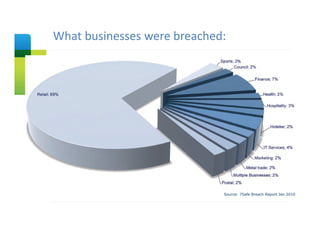
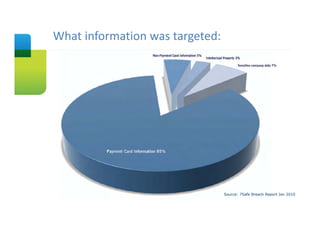
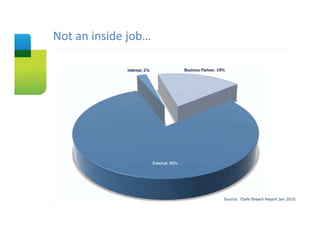
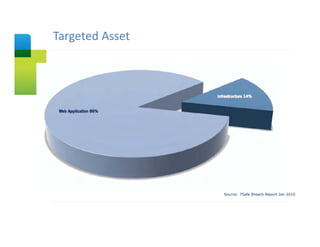
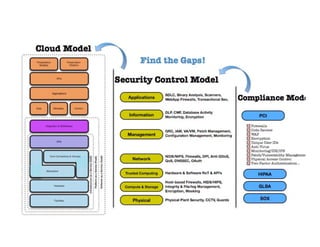
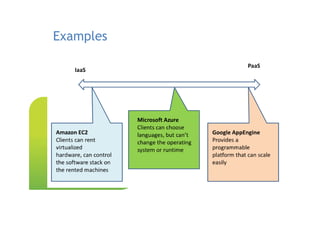
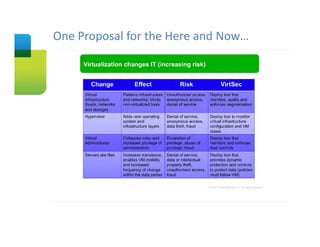
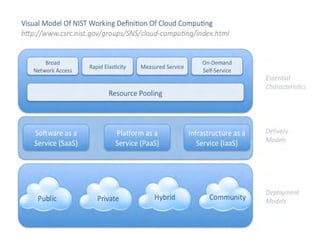
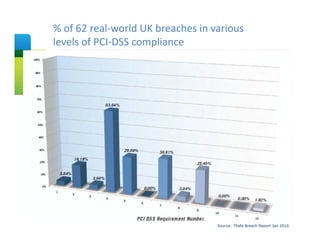
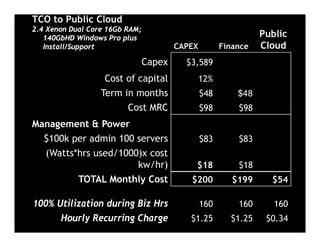
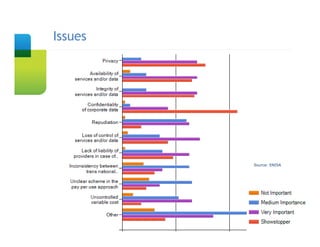
The document presents an overview of cloud security concerns and challenges discussed at Forrester's Security Forum EMEA 2010, highlighting the slow adoption of cloud technology by enterprises due to security and control issues. It emphasizes the need for adequate security measures, risk assessments, and understanding of compliance requirements in cloud computing. The document also shares real-world examples and statistics regarding breaches and the increasing sophistication of cyber threats, suggesting a proactive approach to security in cloud environments.





















![NASDAQ and the New York Times
Slide Title
• New York Times
– Didn’t coordinate with Amazon, used a credit card!
– Used EC2 and S3 to convert 15M scanned news articles to PDF (4TB data)
– Took 100 Linux computers 24 hours (would have taken months on NYT
computers
– “It was cheap experimentation, and the learning curve isn't steep.” –
Derrick Gottfrid, Nasdaq
• Nasdaq
– Uses S3 to deliver historic stock and fund information
– Millions of files showing price changes over 10 minute segments
– “The expenses of keeping all that data online [in Nasdaq servers] was too
high.” – Claude Courbois, Nasdaq VP
– Created lightweight Adobe AIR application to let users view data](https://image.slidesharecdn.com/peeringthroughthecloudforresteremea2010-120126214611-phpapp02/85/Peering-Through-the-Cloud-Forrester-EMEA-2010-31-320.jpg)