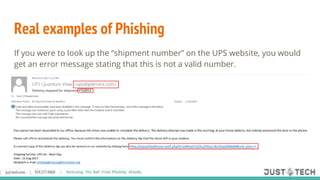
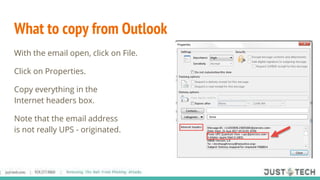
The document discusses phishing attacks, defining them as attempts to bait users into revealing sensitive information for financial gain. It outlines methods of phishing, recognition tips, and necessary prevention strategies, including technology and human-centered measures. Additionally, it emphasizes the importance of continual training for staff and provides resources for further information.