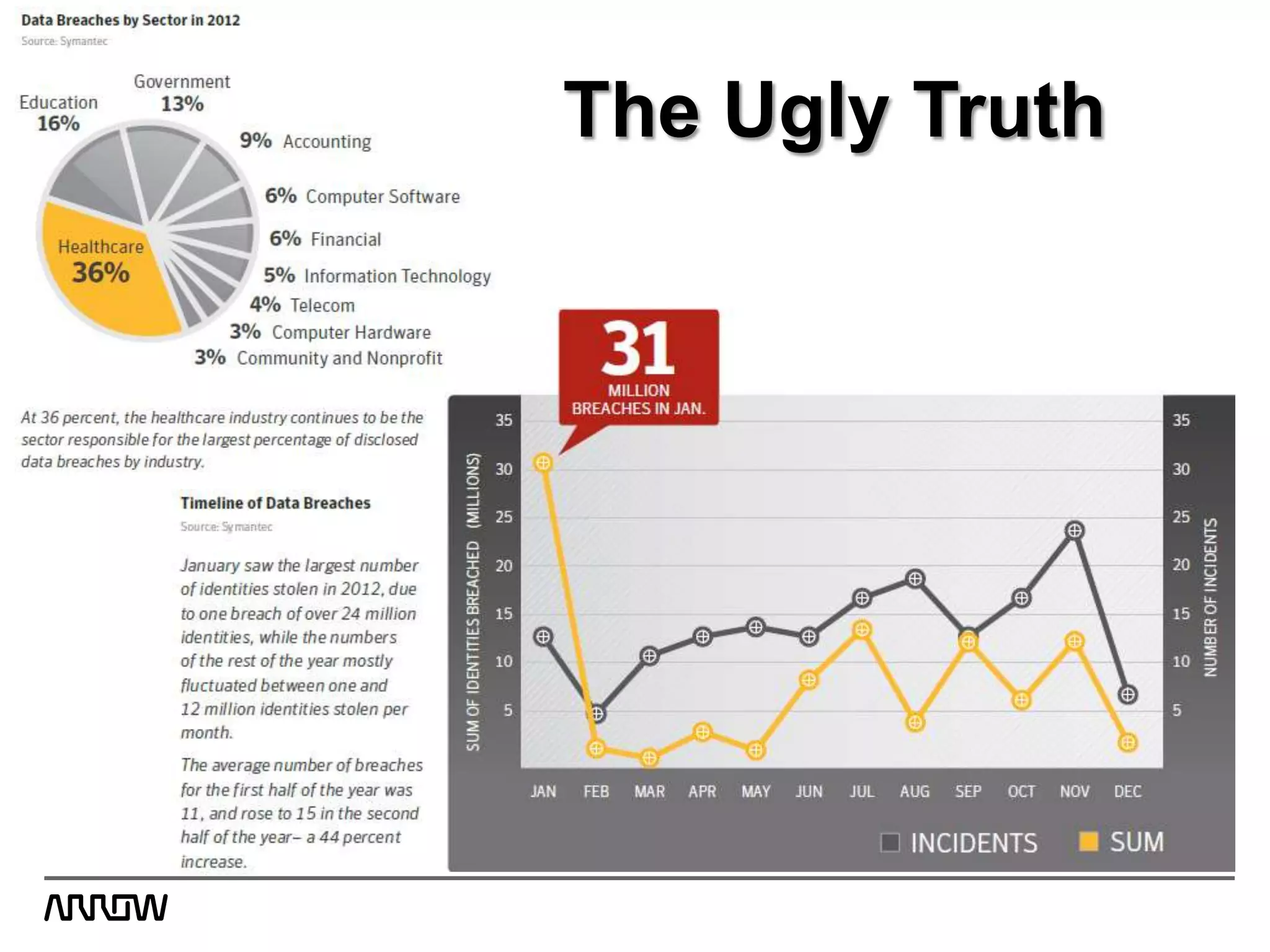
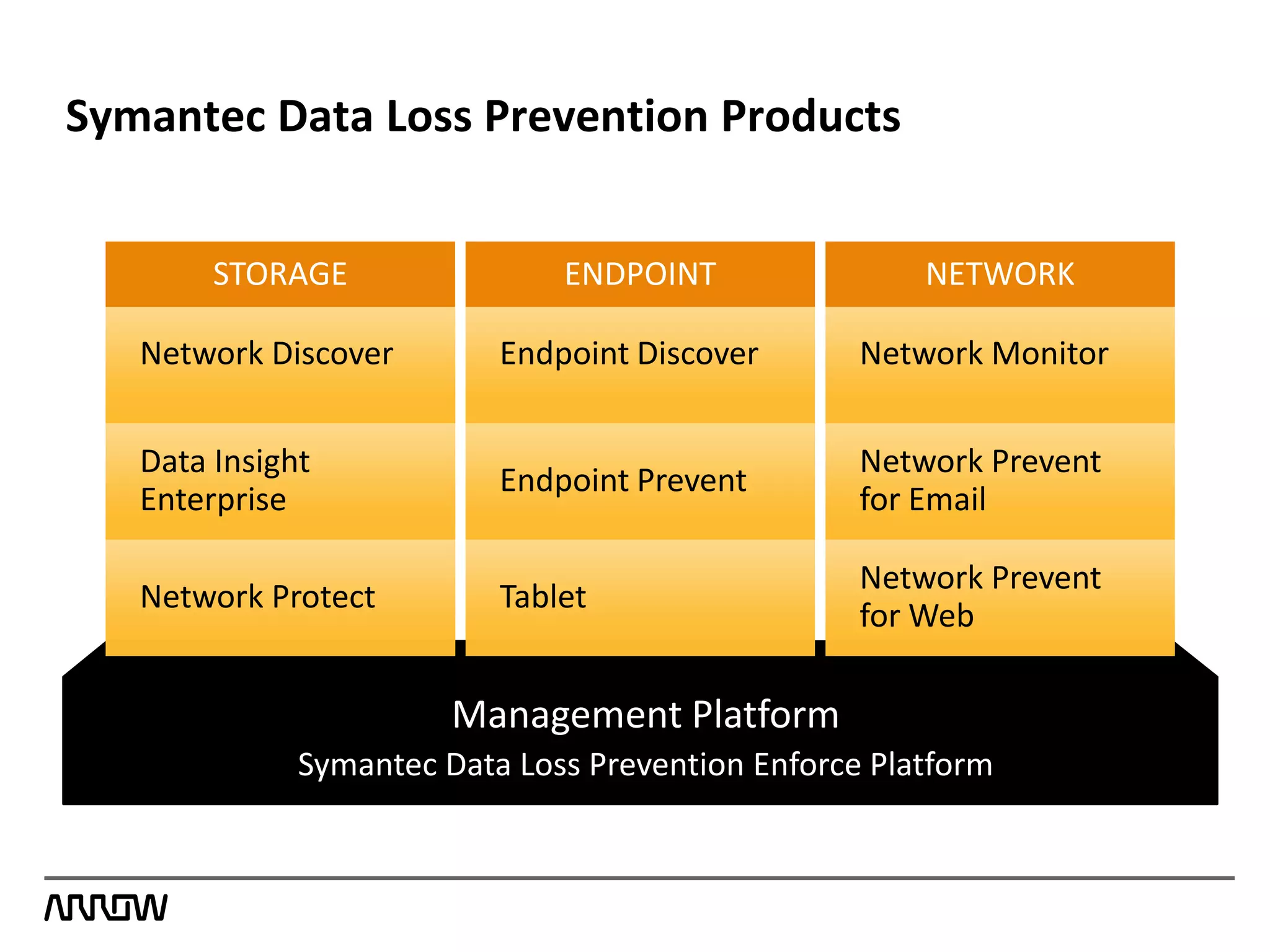
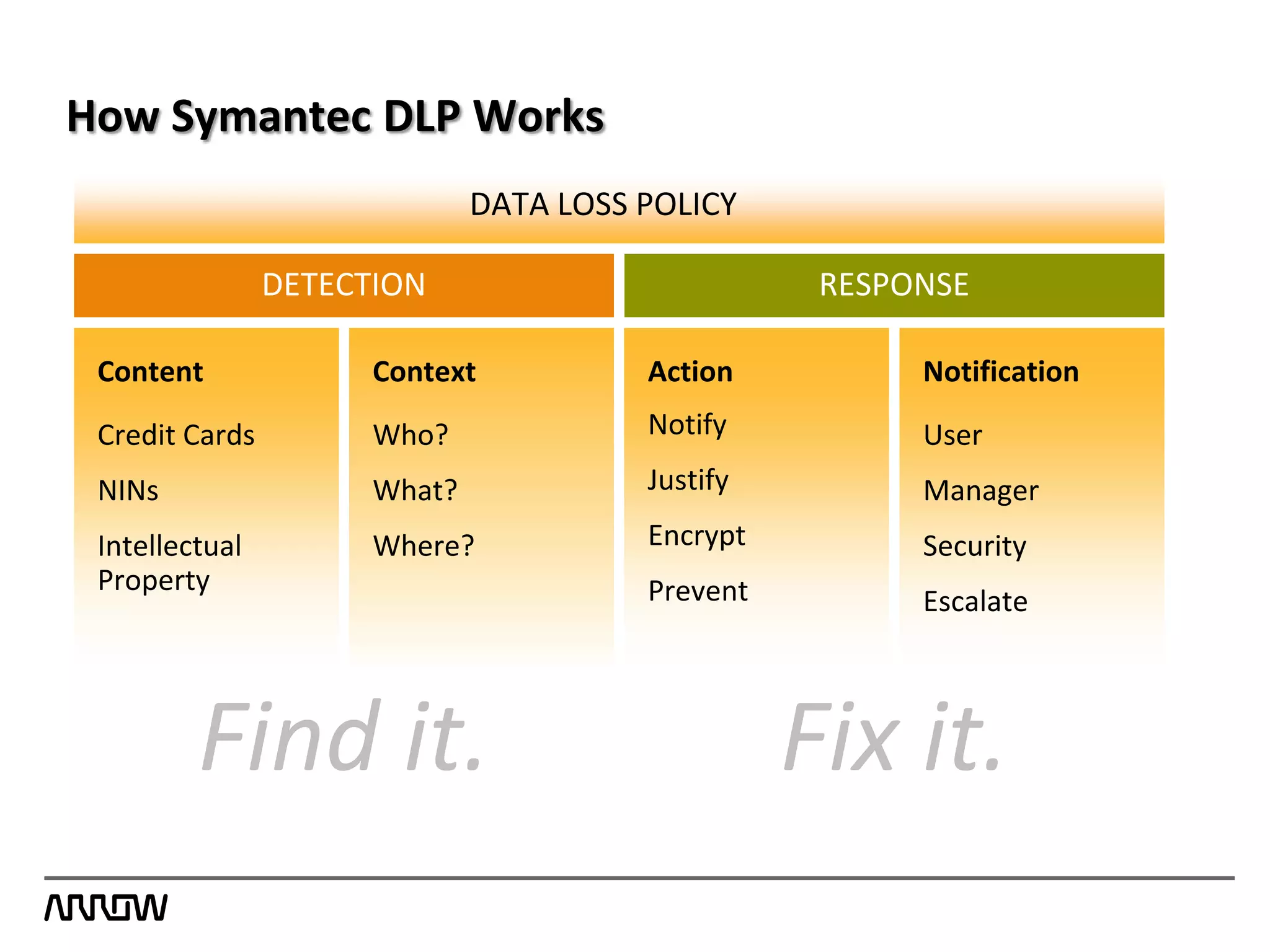
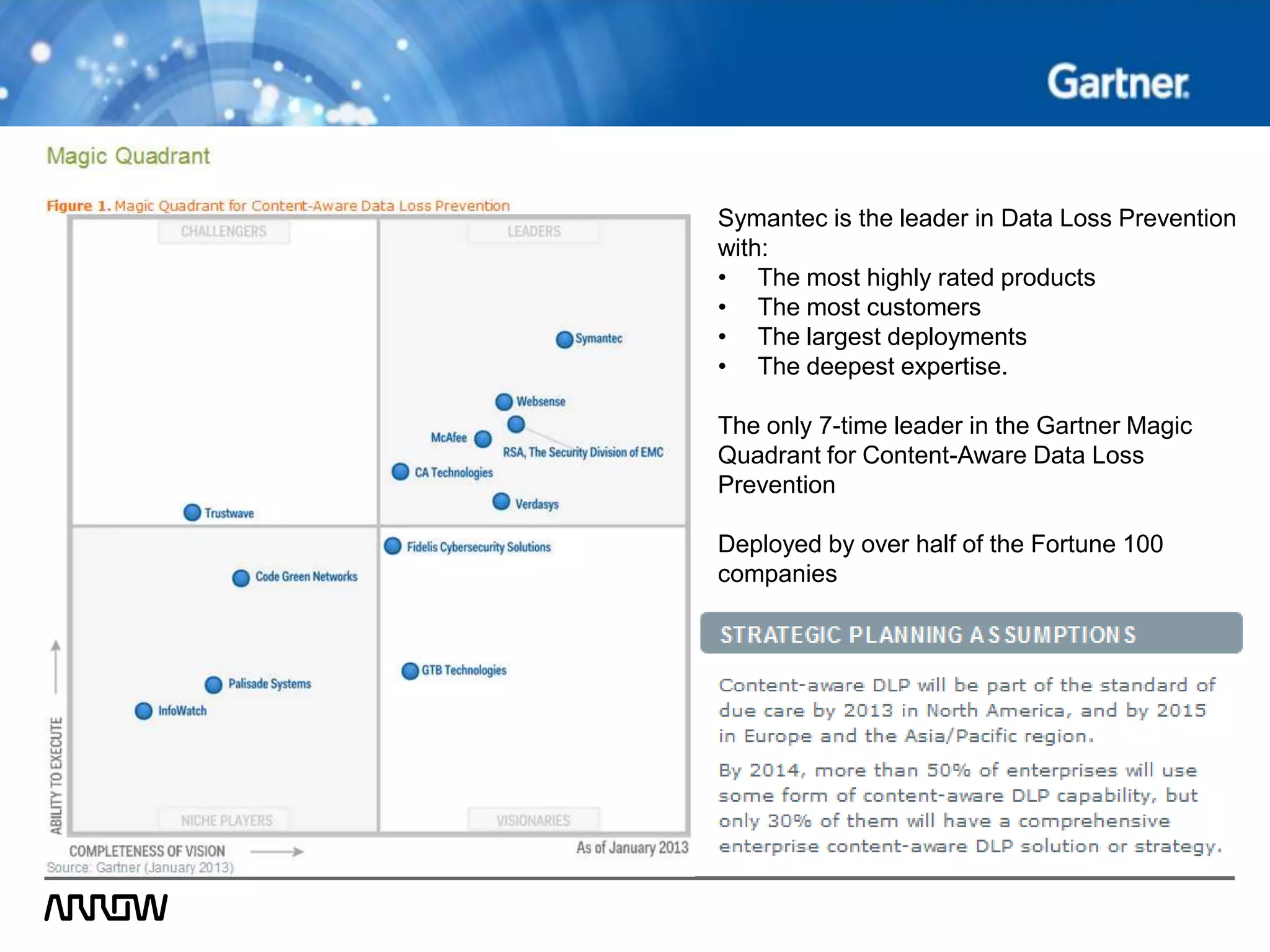
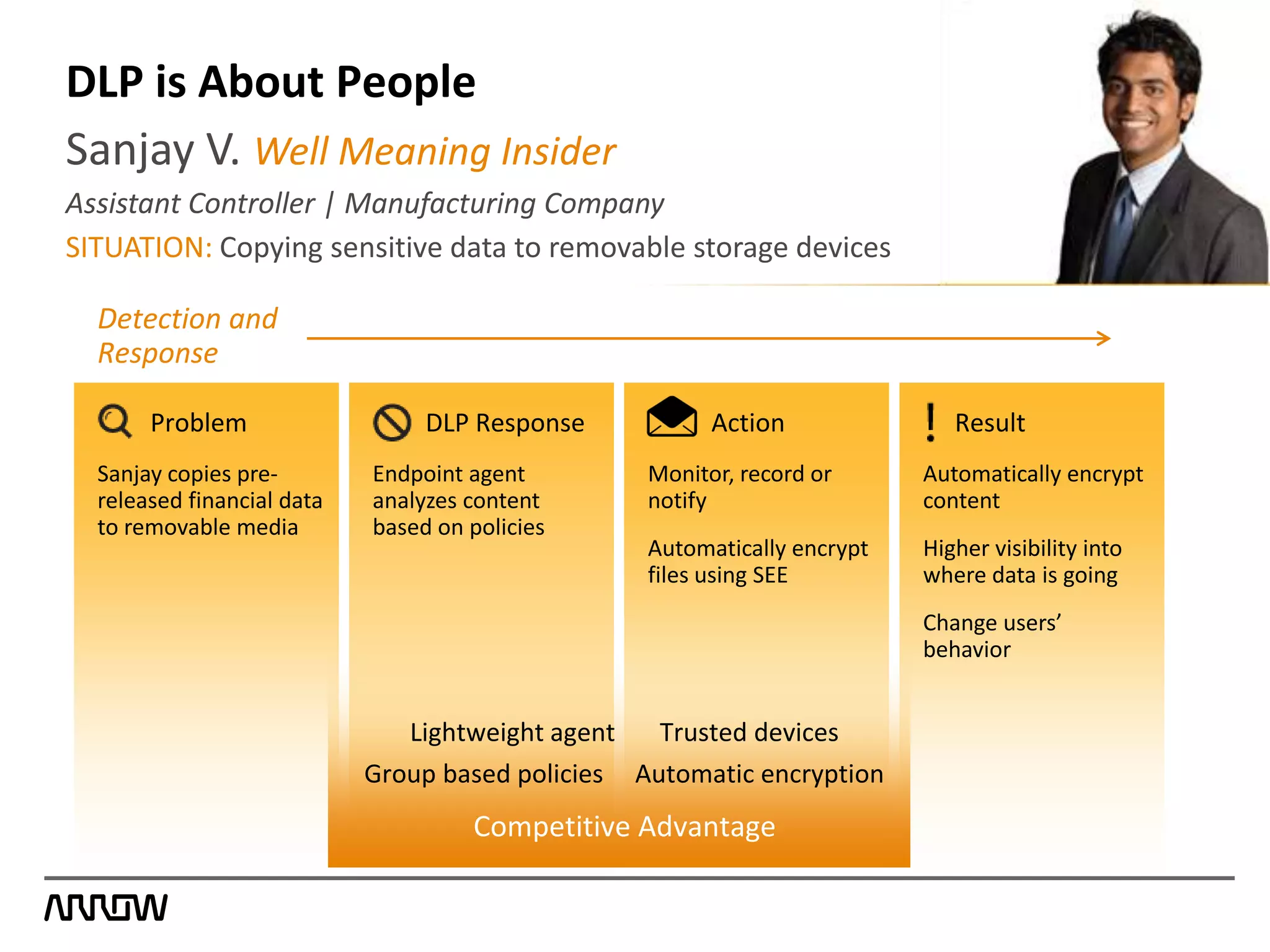
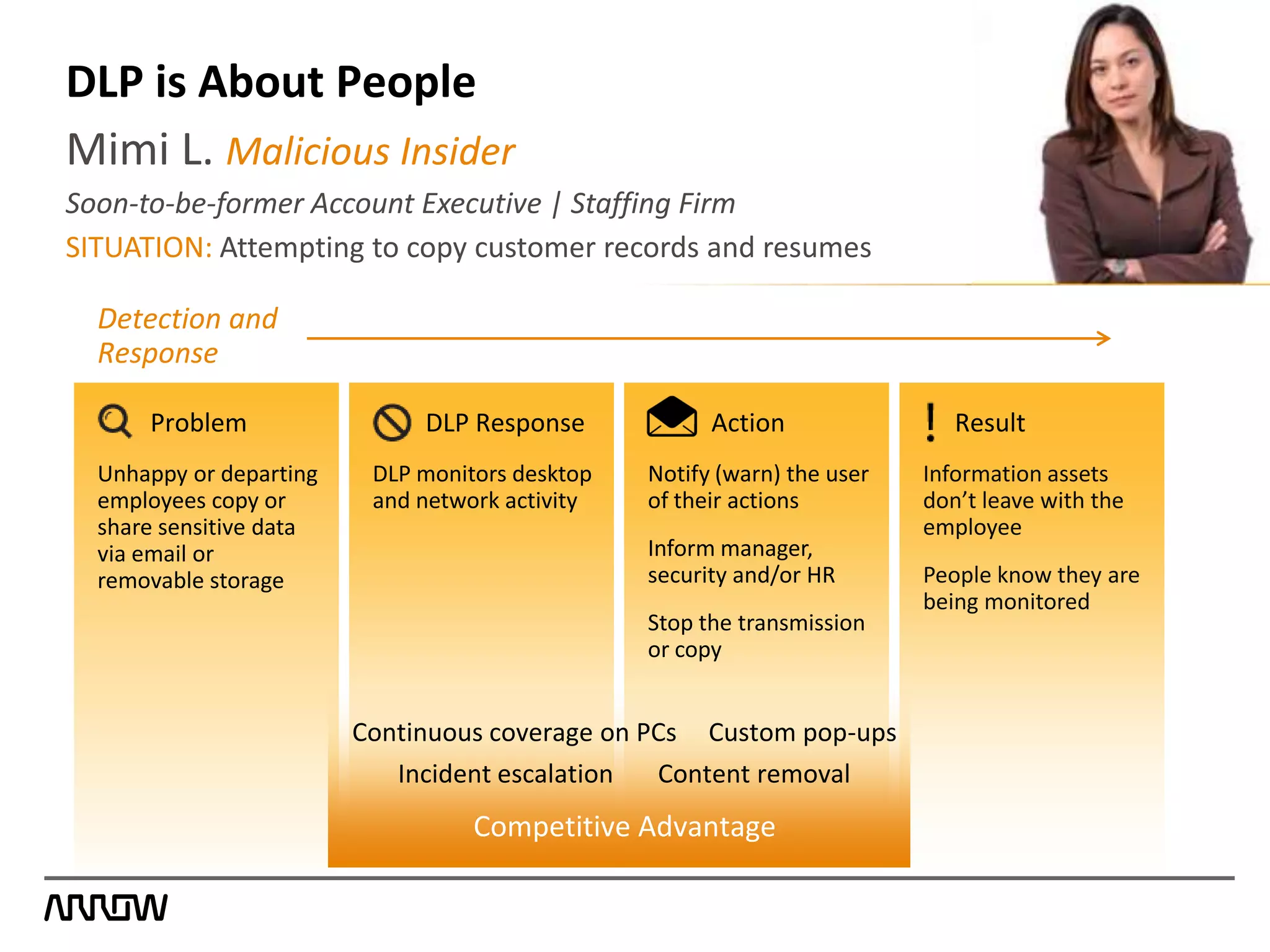
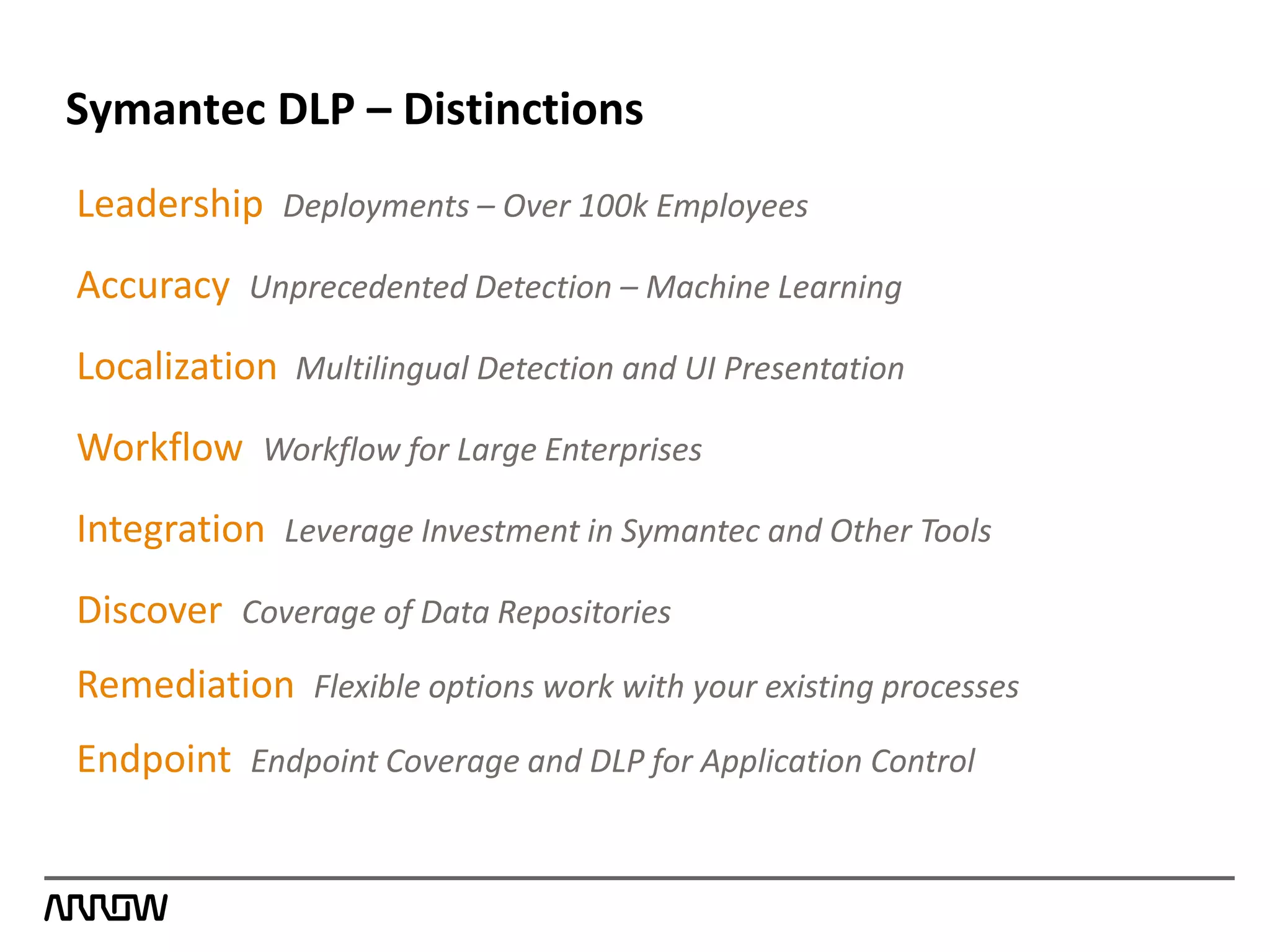
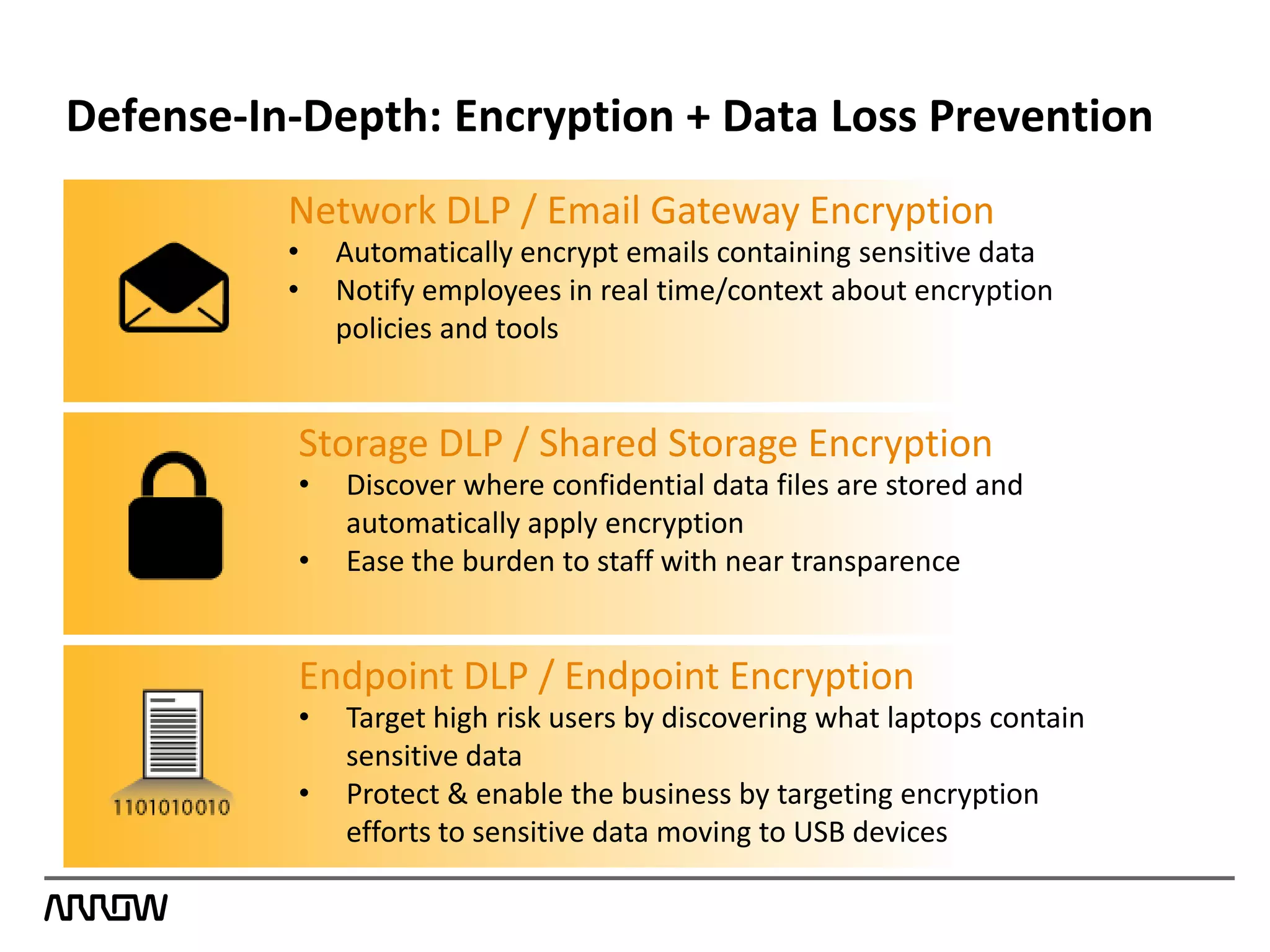
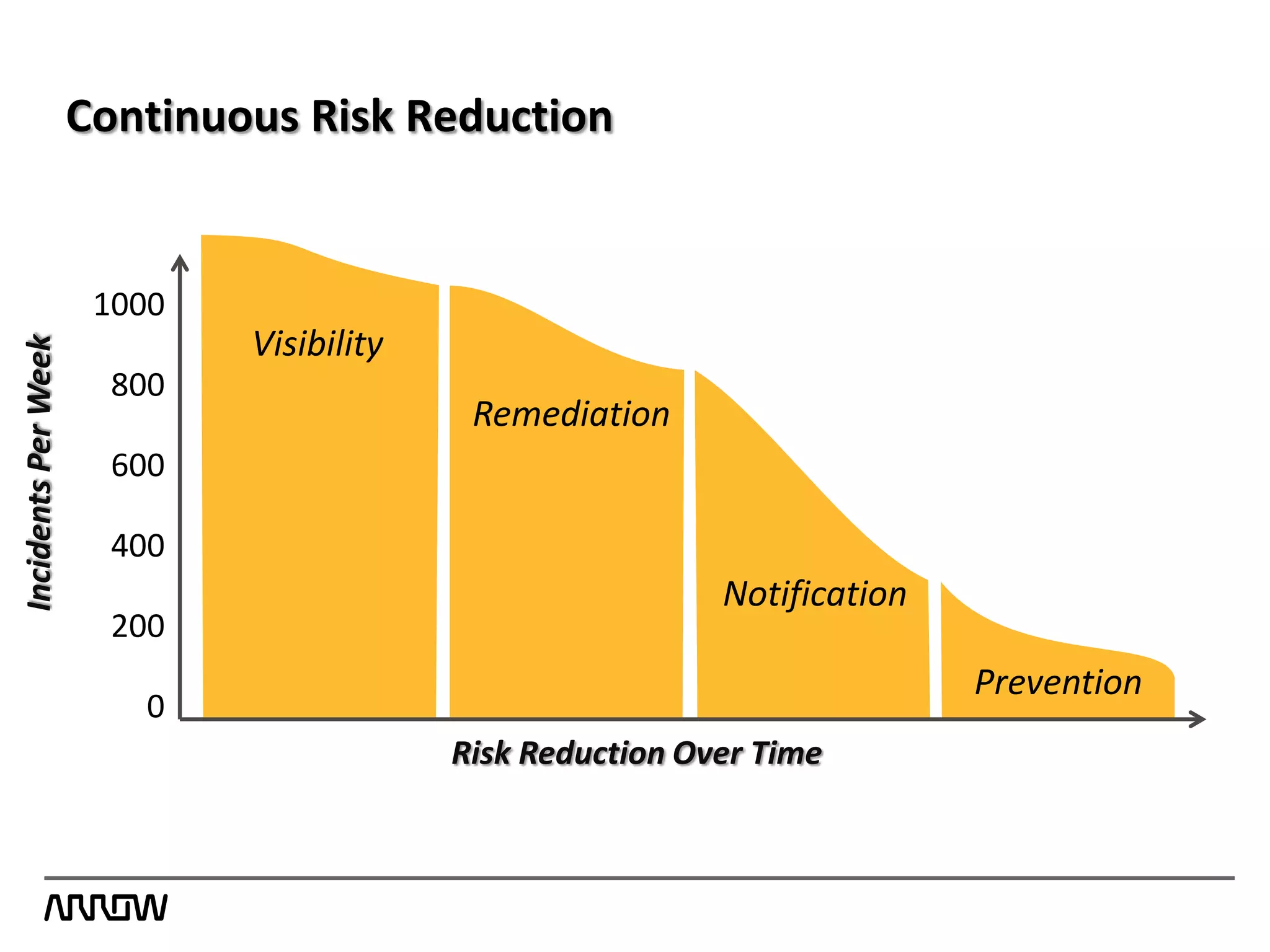
Symantec Data Loss Prevention helps organizations address the serious problem of data loss by providing visibility into where sensitive data is located and how it is being used, enabling monitoring of data movement and detection of policy violations, and offering flexible options for protecting data and educating employees to prevent accidental or intentional data loss. Symantec is a leader in this field with the most highly rated products, largest customer base, and deepest expertise in helping customers improve security, comply with regulations, and reduce the costs of data breaches.