This document discusses security attacks on the RSA cryptosystem from a computational number theoretic approach. It covers factorization attacks using algorithms like Fermat's method, Euler's method, Pollard's p-1 method and Pollard's rho method. It also discusses elementary attacks like dictionary attacks and common modulus attacks. Finally, it discusses low private exponent attacks using Wiener's attack. The document analyzes the impact of these attacks on the security of RSA and explores the relationship between breaking RSA versus integer factorization.















![Introduction Factoring Attacks Elementary Attacks Low Private Exponent Attack
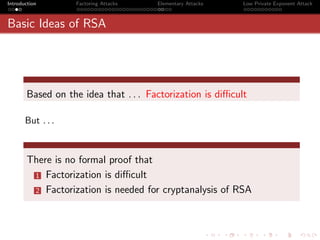
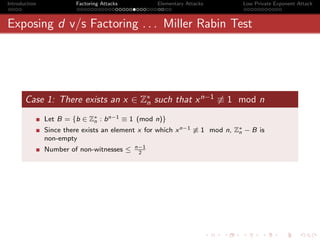
Continued Fractions
Definition
The function of n + 1 variables
1
a0 +
1
a1 +
1
a2 +
1
a3 + · · ·
an
or
[a0 , a1 , a2 , a3 · · · , an ]
is defined as a continued fraction. We consider only simple and
positive continued fractions, i.e. all ai s are integral and positive.
[a0 , a1 , a2 , a3 · · · , ai ], 0 ≤ i ≤ n are said to be the convergents of
[a0 , a1 , a2 , a3 · · · , an ].](https://image.slidesharecdn.com/seminarpres-091203014021-phpapp02/85/Security-Attacks-on-RSA-39-320.jpg)
![Introduction Factoring Attacks Elementary Attacks Low Private Exponent Attack
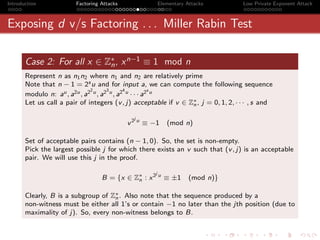
Continued Fractions · · · Theorems
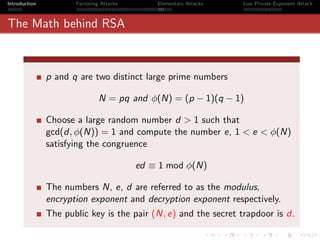
Theorem 1
The continued fraction
[a0 , a1 , a2 , · · · , an ] = [a0 , a1 , · · · , am−1 , [am , · · · an ]]
Theorem 2
The continued fraction
pm am pm−1 + pm−2
[a0 , a1 , a2 , · · · , am−1 , am ] = =
qm am qm−1 + qm−2](https://image.slidesharecdn.com/seminarpres-091203014021-phpapp02/85/Security-Attacks-on-RSA-40-320.jpg)
![Introduction Factoring Attacks Elementary Attacks Low Private Exponent Attack
Continued Fractions · · · Theorems
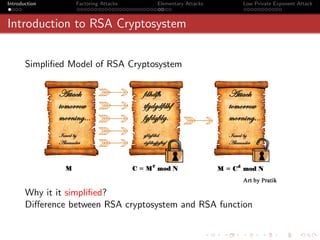
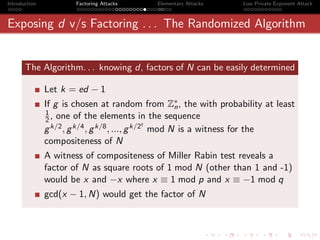
Theorem 3
Continued Fraction Algorithm: Any rational number x can be represented as a
simple finite continued fraction.
Proof
h0
x=
k0
Comparing x with [a0 , a1 , a2 , · · · , aN , aN+1 ],
x = a0 + ξ0 where ξ0 < 1 i.e. h0 = a0 k0 + ξ0 k0
If ξ0 = 0
1 k0
=
ξ0 h0 − a0 k0
Let k1 = h0 − a0 k0 , (since, k1 = ξ0 k0 , we have k1 < k0 )
k0
= a1 + ξ1 and k0 = a1 k1 + ξ1 k1
k1](https://image.slidesharecdn.com/seminarpres-091203014021-phpapp02/85/Security-Attacks-on-RSA-41-320.jpg)
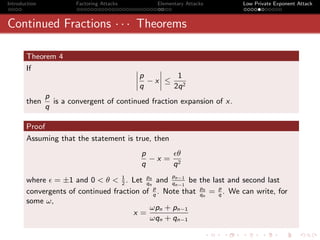
![Introduction Factoring Attacks Elementary Attacks Low Private Exponent Attack
Continued Fractions · · · Theorems
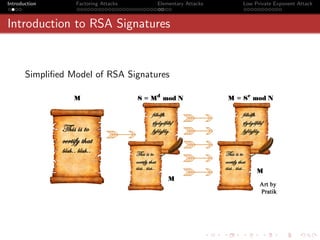
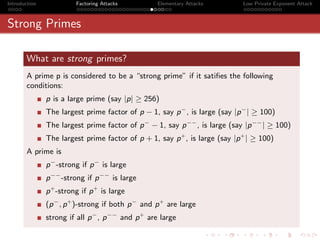
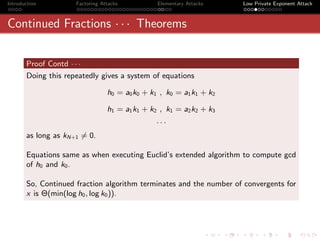
Proof Contd · · ·
qn 1 qn−1
θ= and ω = −
ωqn + qn−1 θ qn
Note that since θ < 1 , we have, ω > 1
2
p
Let = [a0 , a1 , · · · am1 ]
q
Let ω = [b0 , b1 , b2 · · · bm2 ]
[a0 , a1 , a2 · · · am1 , ω] = [a0 , a1 , a2 · · · am1 , [b0 , b1 , b2 · · · bm2 ]]
ωpm + pm−1
= =x
ωqm + qm−1
So, x = [a0 , a1 , a2 · · · am1 , b0 , b1 , · · · bm2 ].
p
So, by construction, we have proved that q
is a convergent of continued
fraction expansion of x.](https://image.slidesharecdn.com/seminarpres-091203014021-phpapp02/85/Security-Attacks-on-RSA-44-320.jpg)




