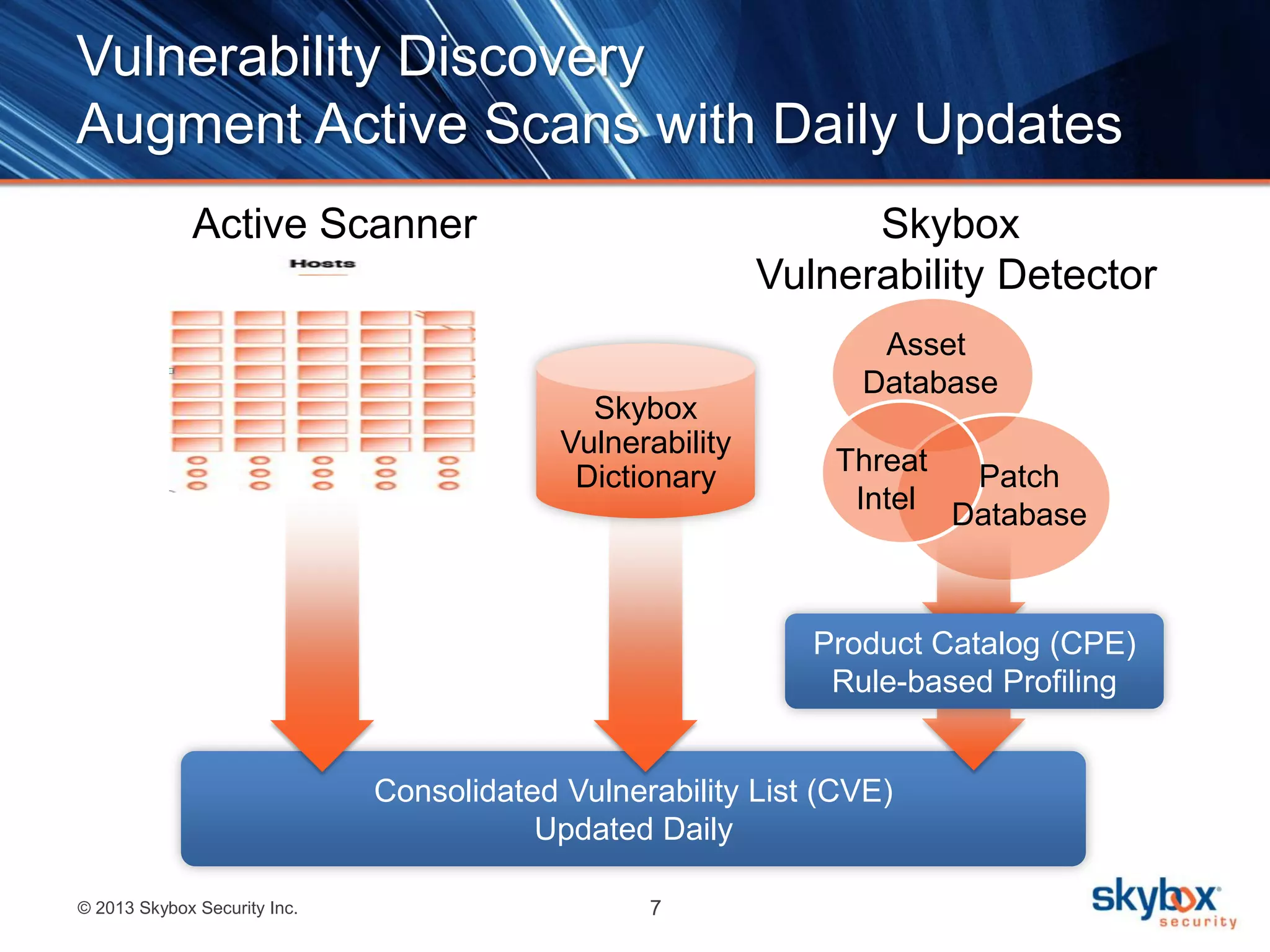
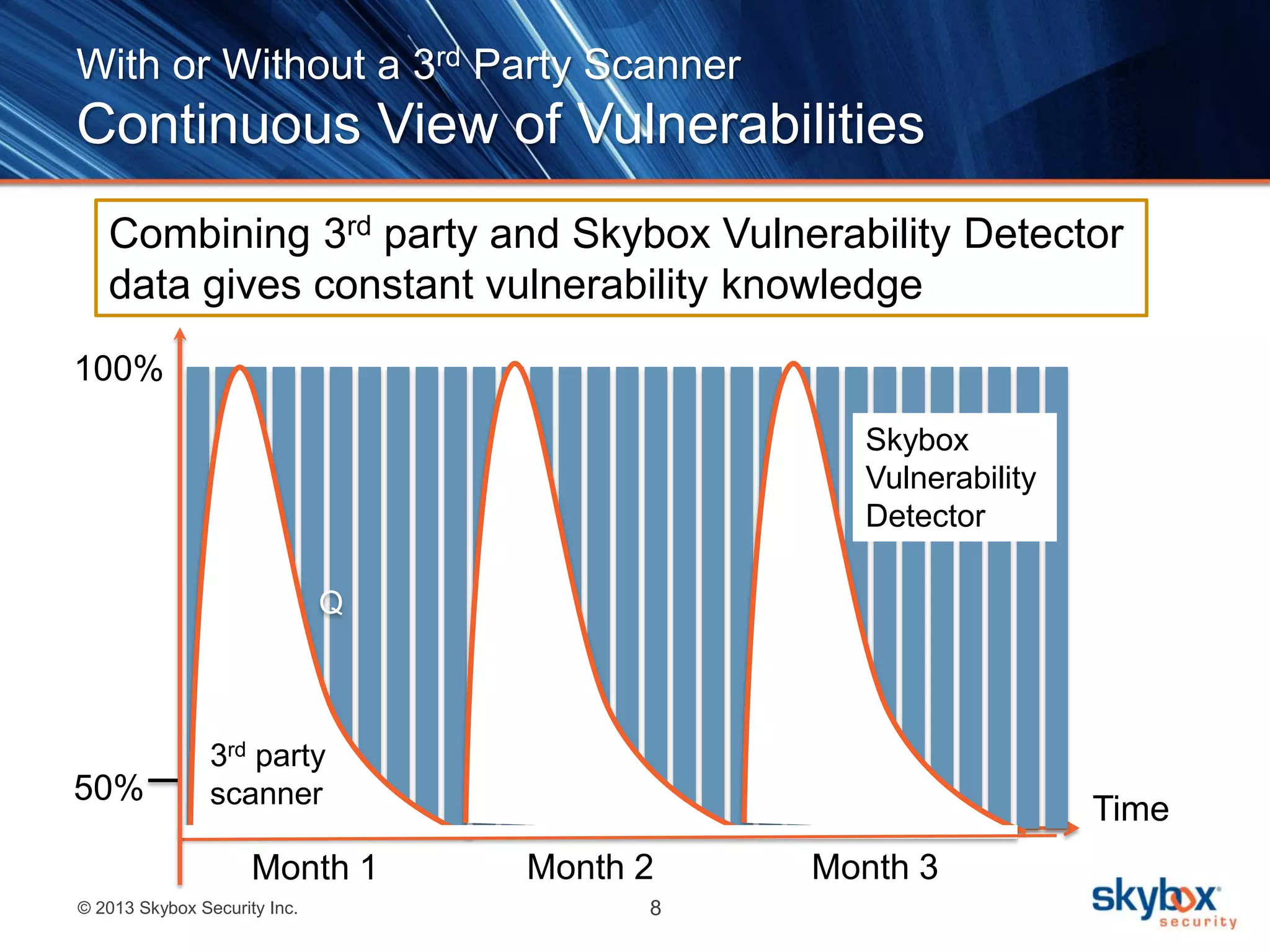
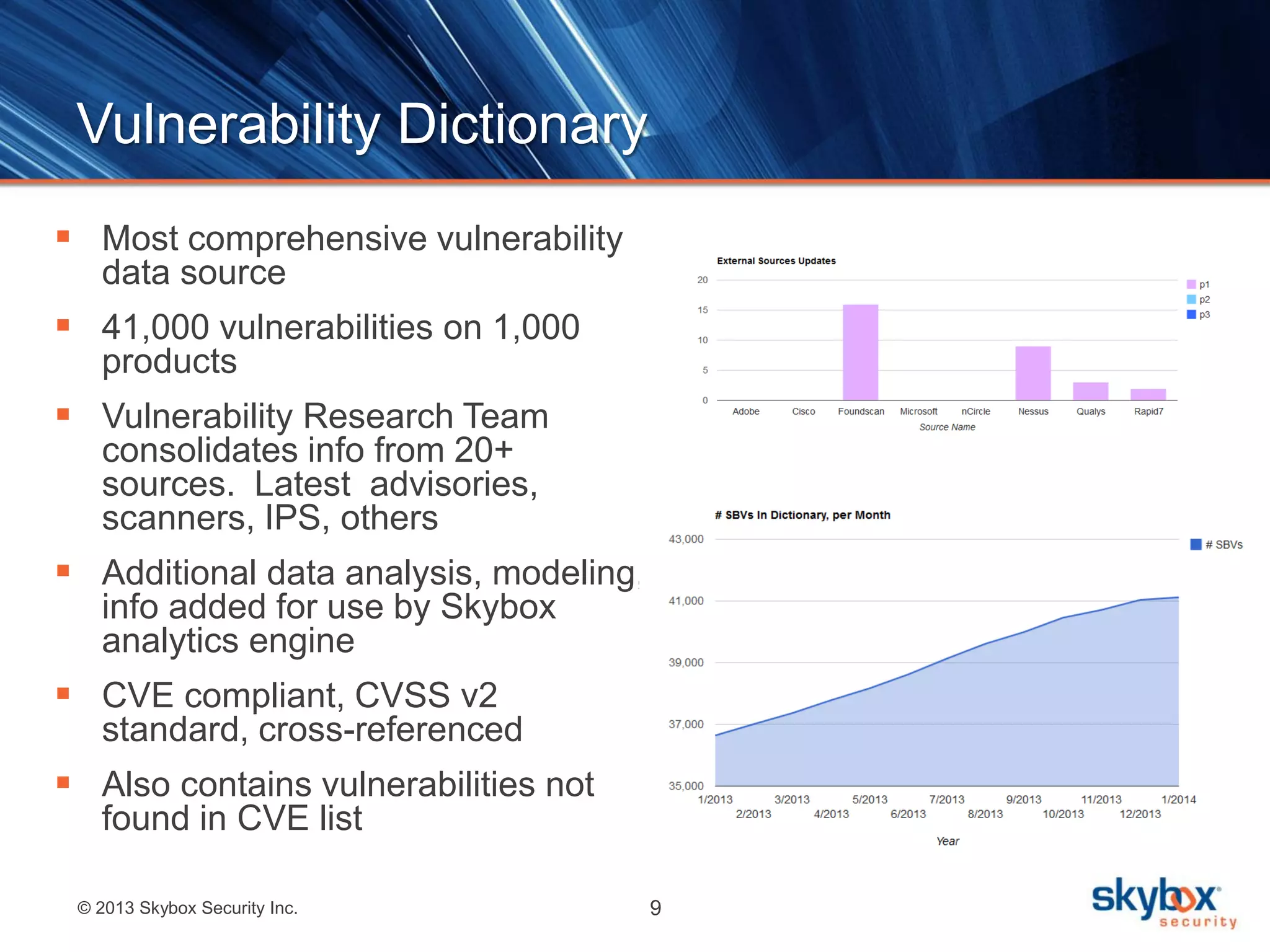
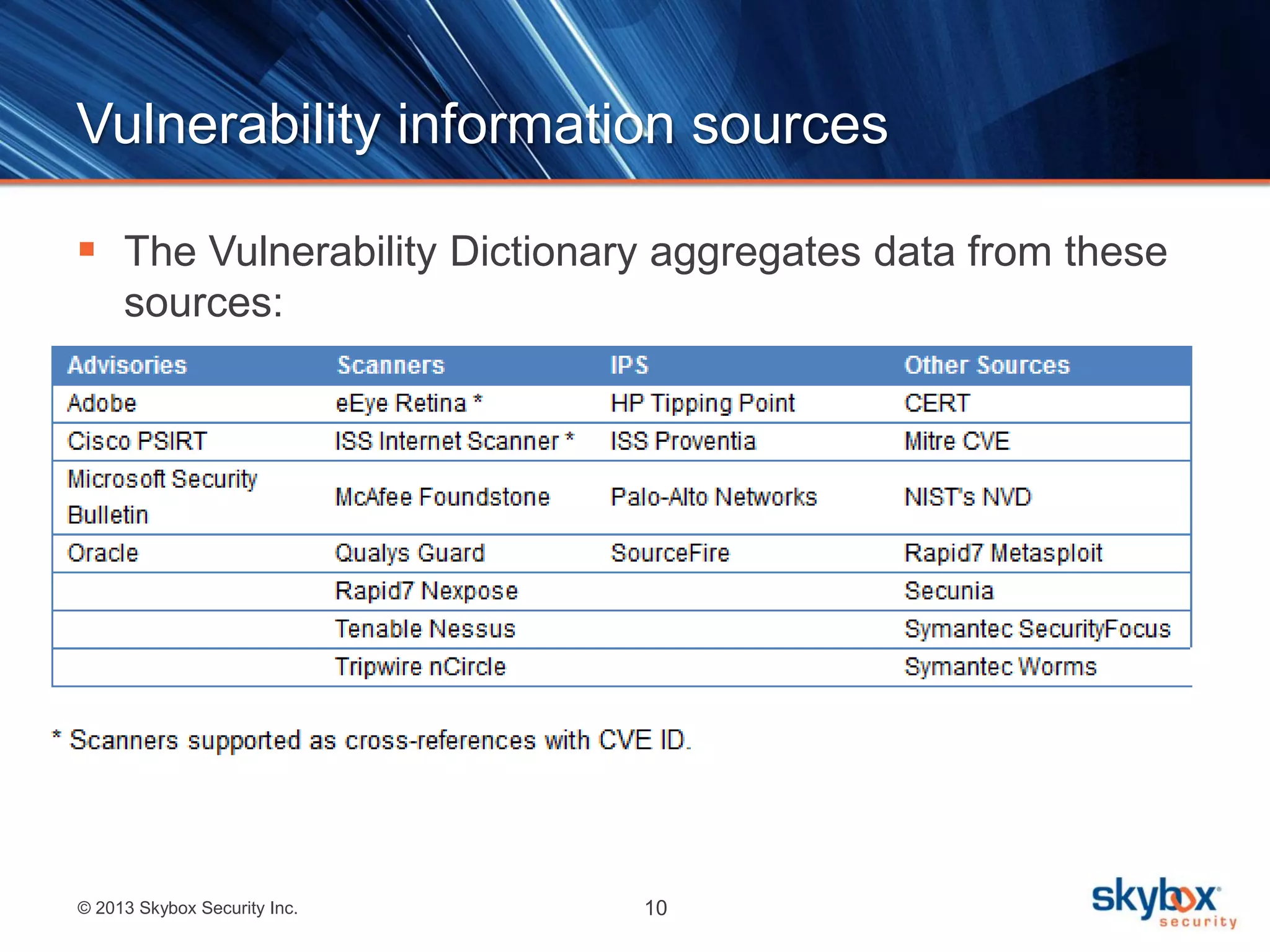
The document discusses Risk Control's vulnerability detection capabilities. It can deduce vulnerabilities without scanning by leveraging existing repositories, providing faster discovery across all systems including those that are difficult to scan. It augments traditional vulnerability scanning by continuously updating vulnerability data and detecting vulnerabilities across operating systems, network devices, applications, and client-side software.